Viewing Cloud Access
After connecting your cloud service providers and marking the cloud-enabled entitlement types, SailPoint CIEM can display the effective access that accounts associated with human identities have to your cloud infrastructure.
SailPoint CIEM data is also available in the Access Intelligence Center (AIC) and your MySailPoint dashboard, which allows you to view customized visualizations to more easily analyze and explore your identity and cloud data.
Note
Non-admin users must have the Cloud Gov User permission to view and approve SailPoint CIEM account entitlements. Refer to User Level Permissions and User Level Matrix.
Viewing Effective Access
To view the cloud resources and privileges users can access through their assigned entitlements:
- Go to Admin > Identity Management > Identities.
- Select an identity.
- Select Accounts and choose an account.
-
The entitlements assigned to the user through their account on the source are displayed in Entitlement Assignments. If the entitlements were marked as cloud enabled and grant access to cloud resources, select Yes in the Cloud Enabled column to display the effective access.
Notes
You can also access an identity's entitlement assignments by going to the source configuration and choosing their account from the Accounts section.
If you select Yes and receive a message that the user does not have effective access, this indicates the identity has an entitlement that grants cloud access, but they do not have access to any cloud resources.
-
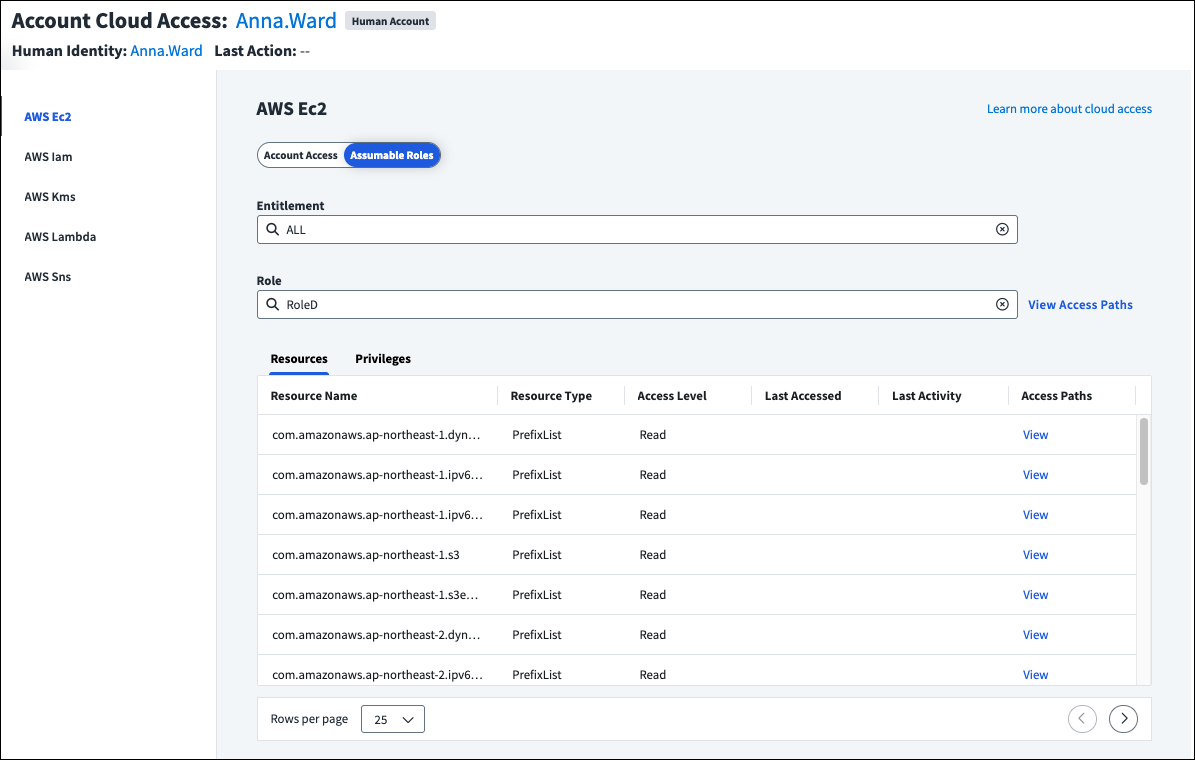
In the effective access view, select the cloud account from the left side to see the account access granted through the set entitlement. The resources and privileges the user can access are displayed, as well as their access level and history.
To view the resources associated with other entitlements, select the Entitlement field and choose a new entitlement to display.
-
If the entitlement is on an AWS source and grants access to an AWS resource, you can select Assumable Roles. If the identity can assume AWS IAM roles, including roles that can be indirectly reached through role chaining, they can be selected from the Role field to display the associated resources and privileges.
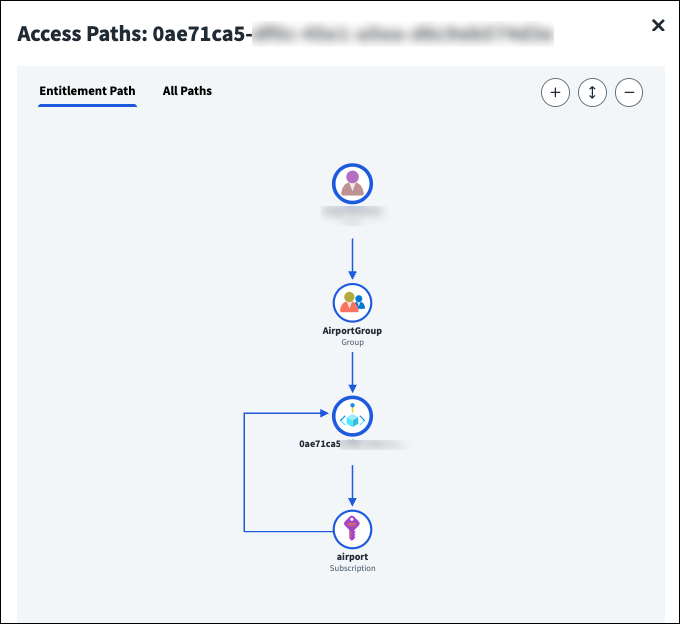
For a visual representation of how the user can access the specified role through the chosen entitlement, or all entitlements, select View Access Paths above the table. You can switch between viewing the entitlement role path or all role paths.
To see the access paths the role has to a specific resource, select View in the Access Paths column of the table.
-
For all source types, you can view a visual representation of the account access granted to each resource by selecting View Access in the Access Paths column.
When you include cloud-enabled entitlements in certification campaigns, your certifiers can view this information, as well as the access paths. Refer certifiers to Viewing Cloud Access Details in the User Help for guidance on reviewing cloud-enabled entitlements.
AWS CloudTrail Limitations
Some CloudTrail entries delivered by AWS services do not contain the Resource attribute, which is used to display the last activity on an AWS resource in a certification campaign. Your certifiers will still see how the resource was accessed, but might not have full activity data details.
Excluded GCP Asset Types
SailPoint CIEM displays the effective and last access data for supported GCP asset types except:
anthos.googleapis.com/ConnectedCluster |
dlp.googleapis.com/DlpJob |
networkconnectivity.googleapis.com/PolicyBasedRoutes |
bigquerymigration.googleapis.com/MigrationWorkflow |
firebase.googleapis.com/FirebaseAppInfo |
networkservices.googleapis.com/EdgeCacheKeyset |
compute.googleapis.com/RegionDisk |
firestore.googleapis.com/Database |
networkservices.googleapis.com/EdgeCacheOrigin |
containerregistry.googleapis.com/Image |
identity.accesscontextmanager.googleapis.com/AccessLevel |
networkservices.googleapis.com/EdgeCacheService |
dialogflow.googleapis.com/KnowledgeBase |
identity.accesscontextmanager.googleapis.com/AccessPolicy |
sqladmin.googleapis.com/Instance |
dialogflow.googleapis.com/LocationSettings |
identity.accesscontextmanager.googleapis.com/ServicePerimeter |
Viewing Access Paths
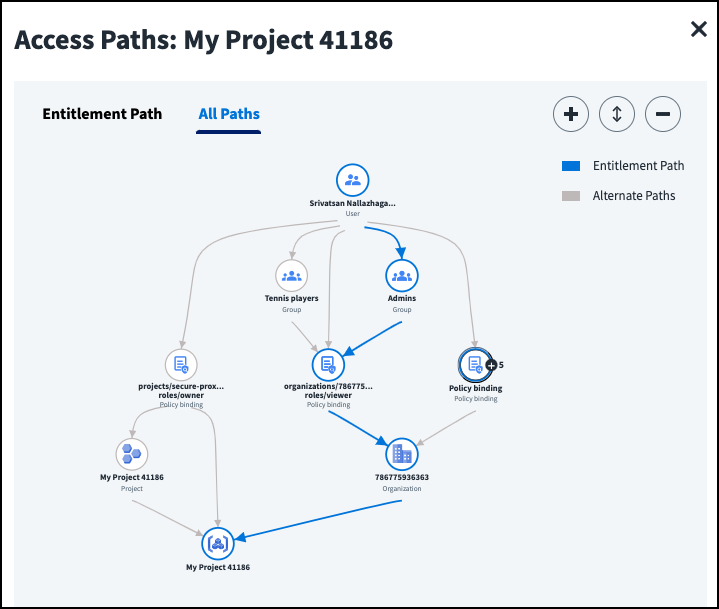
Access paths display between scoped objects like groups, policies, and projects granting the user access to the selected resource. This includes the direct access granted by the entitlement or all access paths to the resource. The access granted by the entitlement is highlighted.
If you are viewing access paths for AWS assumable roles, you can switch between viewing the entitlement role path and all role paths provided by the entitlement.
If a user has multiple of the same type of access at the same scope, such as multiple role assignments that lead to the same management group, you can select the node  to display the access leading to the resource. Use the Collapse icon
to display the access leading to the resource. Use the Collapse icon to collapse all nodes.
Note
If your organization has licensed Machine Identity Security, you can also view the effective access for machine identities that use Microsoft Azure Service Principles and Google Cloud Infrastructure Service Accounts.
Viewing SailPoint CIEM Event Logs
When your cloud access data is pulled into Identity Security Cloud, you can use Search to view logs about SailPoint CIEM events. You can use these error logs to troubleshoot your GCP, AWS, Microsoft Entra ID, and Okta configurations.
-
actor.name:CIEM_SYSTEM- Allows you to view events generated by the SailPoint CIEM system. -
type:CIEM_SOURCE_MANAGEMENT- Allows you to view events related to SailPoint CIEM source management. -
type:CIEM_TEST_CONNECTION- Allows you to view logs of test connection successes and failures.
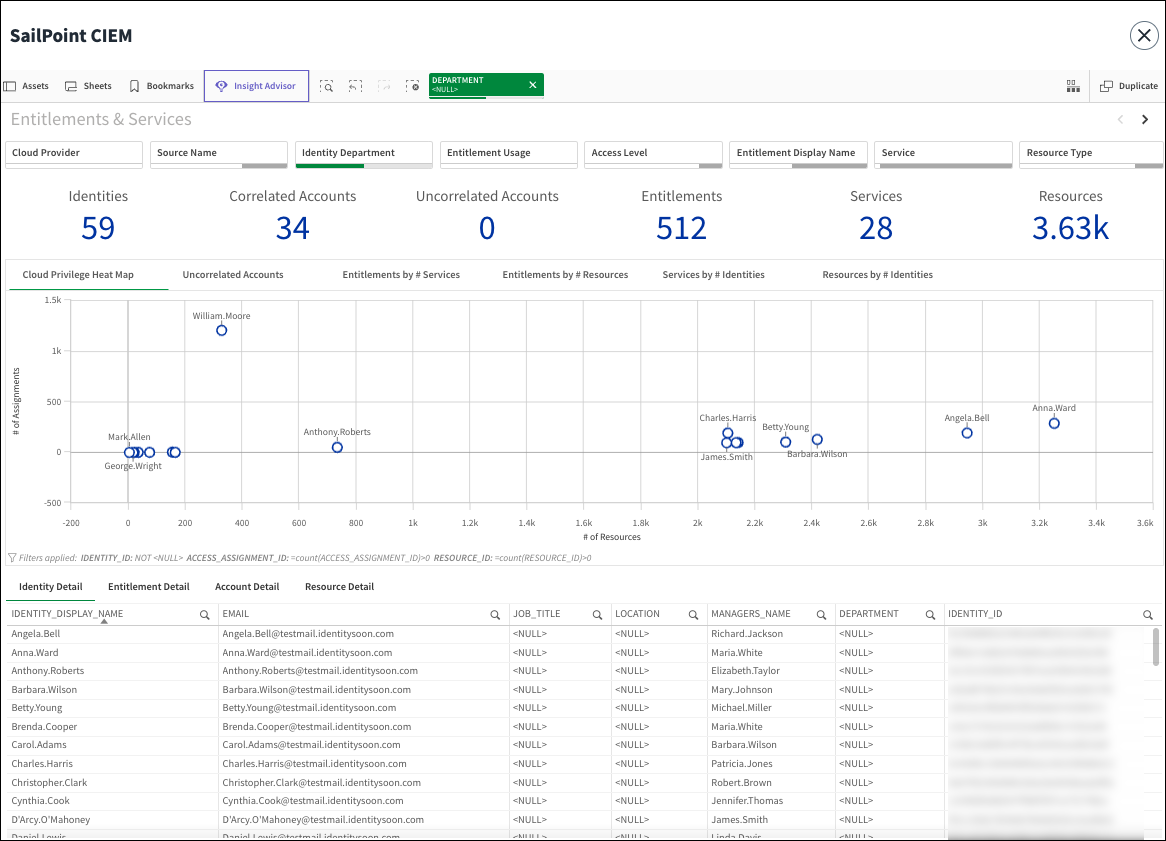
Viewing CIEM Reports in the Access Intelligence Center
If your organization has licensed the Access Intelligence Center (AIC), you can use SailPoint CIEM data to create powerful visualizations that track how human identities are using entitlements to access cloud resources and services.
For example, you can view cloud resources with large numbers of entitlements or entitlements with large numbers of resources to right-size your access model. Or you can discover departments with administrative cloud access that might be candidates for least privilege adjustments.
Go to Admin > Dashboard > Access Intelligence Center and select SailPoint CIEM. You can filter your view to focus on specific cloud providers, departments, entitlements, resource type, and more.
Notes
- To view CIEM reports in AIC, you must be assigned either the Admin or Report Admin user level with the Access Intelligence Center Reader or Author user level.
- Due to data sizing concerns, machine identities are not displayed in AIC reports.
If your organization has not licensed Access Intelligence Center, you can view SailPoint CIEM data in deprecated reports.
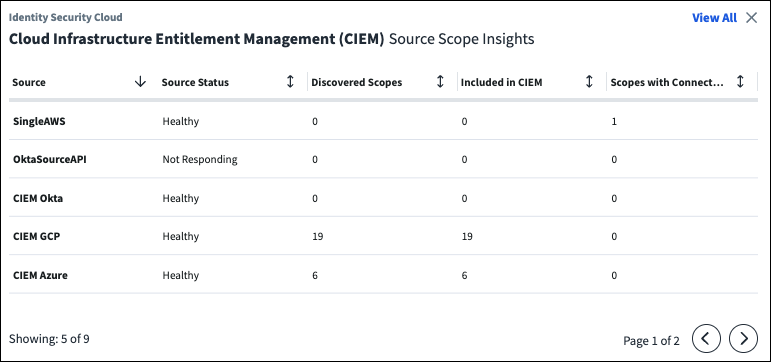
Viewing Cloud Scope Status
The Cloud Infrastructure Entitlement Management (CIEM) Source Scope Insights widget on your MySailPoint home page provides high-level information about the status of your sources and associated scopes, the number of discovered and included scopes, and scopes with connection errors.
Viewing Deprecated Reports
SailPoint CIEM recommends using Access Intelligence Center or MySailPoint to visualize your data.
You might still be able to download deprecated reports that present data in .csv format.
Note
Deprecated reports display human identity data and do not include information about machine identities.
Using the Cloud Scope Status Report
The Cloud Scope Status Report displays detailed information about errors encountered in your selected cloud scopes. Reports are divided by cloud source type and cloud source native ID. They are updated once per day on an asynchronous schedule.
To download the report:
- Go to Search.
- Select the Reports icon
 in the toolbar.
in the toolbar. - Select Cloud Source Scope Status Report to generate the report.
- Select Download at the bottom of the browser to download the .zip file.
Note
Report downloads require a high-speed internet connection (100 Mbps or higher).
When you extract the .zip file, you can view reports of the authentication and authorization errors found in cloud scopes. If no authorization or authentication errors were encountered, the .csv will be empty.
Reading Cloud Scope Status Reports
Each Cloud Scope Status report includes the following fields:
| Field | Description |
|---|---|
| Api | The API invoked by SailPoint CIEM while running into authentication or authorization errors. If the error is an ActivityCollectionError, it will display the activity. If the ErrorType is InventoryCollectionError, it will display the service type or resource type, unless the error context is unaware of the resource, such as authorization errors during the initialization phase, then it will show the service name. |
| CloudSourceType | The cloud service provider where the account originated from (Azure, Okta, GCP, AWS) |
| CloudSourceNativeId | The native ID of the CSP parent source where the resource exists. AWS - ManagementAccountId Azure - AzureTenantId GCP - OrganizationId Okta - OrgUrl |
| CloudSubSourceNativeId | The subsource where the resource is. This value will be N/A for Azure and GCP resources that are at the AzureTenantId or OrganizationId levels. AWS - AccountId Azure - Subscription Id GCP - ProjectId Okta - N/A |
| Service | The service the resource belongs to. |
| ResourceRegion | The AWS region where the resource is located. This value will be N/A for Azure, GCP, and Okta resources. AWS resources that are not region-specific will also display N/A. |
| ResourceType | Type of the resource the API tries to collect, such as a policy. Populated only for InventoryCollectionError and when the error context is aware of the resource type. |
| ErrorType | ActivityCollectionError or InventoryCollectionError. |
| ErrorStatusCode | HTTP status code of the error, like 400, 401, and 403. |
| ErrorCount | The number of times the error record was seen in the last 24 hours. |
| LastTimestamp | The last time the error record was seen. |
| LastErrorMessage | The last error message received by the API. |
| LastTraceId | The trace ID of the last error received by the API. |
Note
API errors are deduplicated and aggregated, but the daily count and last seen timestamp, error messages, and trace IDs are preserved to track the error frequency and context.
Unused Cloud Management Activity
You can download the Unused Cloud Management Activity report to view information from the past 90 days about the unused actions, entitlements, and services of human identities in your AWS, Azure, and GCP cloud environments. IAM admins can use this report to optimize entitlements and collaborate with cloud admins to refine cloud policies.
To download the report:
- Go to Search.
- Select the Reports icon
 in the toolbar.
in the toolbar. - Select Unused Cloud Management Activity to generate the report.
- Select Download at the bottom of the browser to download the .zip file.
Note
Report downloads require a high-speed internet connection (100Mbps or higher).
When you extract the .zip file, you can view reports for each CSP listing the unused actions, services, and entitlements.
Tip
View this data dynamically in the Access Intelligence Center.
Reading Unused Management Activity Reports
The Unused Cloud Management Activity report includes 9 CSVs detailing the unused actions, services, and entitlements for each CSP. Data covers the past 90 days, or activity since the onboarding to SailPoint CIEM if added fewer than 90 days ago.
Data-plane and read actions are not included. Reports are overwritten with new data daily on an asynchronous schedule.
Report Limitations
To account for limitations in creating a list of management actions from cloud audits, SailPoint CIEM excludes AWS
data plane and GCP Read actions from the report. This might result in some data access actions being marked as unused. Before making decisions based on the report, verify the unused access action is not a data action.
Each report includes the following fields:
| Field | Description |
|---|---|
| AccountCloudName | The cloud service provider the identity came from (Azure, AWS, GCP, Okta). AWS Identity Center accounts are listed under the AWS AccountCloudName as N/A. |
| AccessCloudName | The cloud service provider where the access is granted. |
| AccountId | The ID associated with the identity in their cloud service provider. This includes all human identities in SailPoint CIEM with unused access. Users from the AWS Identity Center directory are identified with a UUID. AWS IAM users are identified with an AWS ARN. |
| The email associated with the identity. Users created in AWS will have blank email fields as they are not required to add email addresses. |
|
| AccountDisplayName | The human readable name associated with the account. |
Each report contains additional fields:
Action Report
Management-plane permissions for an identity that have not been used according to SailPoint CIEM activity processing.
| Field | Description |
|---|---|
| Action | The permission unused by the identity based on the last 90 days of activity, or activity since the time of onboarding to SailPoint CIEM if added less than 90 days ago. |
| Service | The CSP service associated with the unused action. |
Service Report
Services where all management-plane permissions associated with the service were unused by the identity. Services where some access is used by the identity are not included, even if some actions were left unused.
| Field | Description |
|---|---|
| Service | The cloud service provider service associated with the unused action. |
| CloudSourceNativeId | The ID used by the CSP parent source where the resource exists. AWS - ManagementAccountId Azure - AzureTenantId GCP - OrganizationId |
| CloudSubSourceNativeId | The subsource where the resource is. AWS - AccountId Azure - N/A GCP - N/A |
| CloudSourceDisplayName | The source display name of the CSP associated with the account. AWS - Management Account Name, N/A for non-organizational accounts Azure - Azure Tenant Name GCP - GCP Tenant Name |
| CloudSubSourceDisplayName | The subsource display name. AWS - Account name will be N/A for non-organizational accounts. Azure - N/A GCP - N/A |
Entitlement Report
Entitlements that contained one or more unused services. This can help identify entitlements that are too broad and can be revised to craft smaller least-privilege entitlements.
| Field | Description |
|---|---|
| EntitlementId | The ID used by the CSP for the SailPoint CIEM entitlement the identity has been granted. AWS - The AWS ARN of the policy granted to the identity and the relevant statement ID within that policy in the format <policy arn>|<statement id> Azure - The RoleAssignment, RoleAssignmentScheduleInstance (PIM) or RoleEligibilityScheduleInstance (PIM) ID that has mapped the permissions to the given identity. GCP - The policy (scope of the entitlement) and Role that grant permissions in the format <policy id>:<role id> |
| CloudSourceNativeId | The ID of the CSP parent source where the account exists. AWS - ManagementAccountId Azure - AzureTenantId GCP - OrganizationId |
| CloudSubSourceNativeId | The subsource where the resource is. AWS - AccountId Azure - N/A GCP - N/A |
| CloudSourceDisplayName | The source display name of the CSP associated with the account. AWS - Management Account Name, N/A for non-organizational accounts Azure - Azure Tenant Name GCP - GCP Tenant Name |
| CloudSubSourceDisplayName | The subsource display name. AWS - Account name will be N/A for non-organizational accounts. Azure - N/A GCP - N/A |
Viewing Cloud Resource Access
You can download the Cloud Resource Access report to view the services and resources that human identities can access in each of your connected SailPoint CIEM sources. Reports are divided by service and are updated once per day on an asynchronous schedule.
To download the report:
- Go to Search.
- Select the Reports icon
 in the toolbar.
in the toolbar. - Select Cloud Resource Access to generate the report.
- Select Download at the bottom of the browser to download the .zip file.
Note
Report downloads require a high-speed internet connection (100Mbps or higher).
When you extract the .zip file, you can view reports of the access that human identities have to your cloud resources.
Reading Cloud Resource Access Reports
Each Cloud Resource Access report includes the following fields about the resources the identity can access.
Note
The Email, DisplayName, AccountStatus, Manager, and Department columns might be empty if there is an uncorrelated account that can access resources or if those values are not set for an identity (correlated or uncorrelated).
| Field | Description |
|---|---|
| ResourceId | The ID associated with the resource in the cloud service provider. |
| ResourceType | The type of resource. |
| ResourceName | The name of the resource. |
| The email of the correlated identity who can access the resource. | |
| DisplayName | The human readable name associated with the correlated identity. |
| AccessLevel | The level of access, Read, Write, or Admin, the identity has to that resource. |
| AccountSourceType | The cloud service provider the account originated from. SailPoint CIEM supports federated AWS access from Okta and Azure accounts. AWS Identity Center users are identified with a UUID. AWS IAM users are identified with an AWS ARN. |
| AccountStatus | The status of the account at the last time of processing. Enabled - The account is enabled and the user can access it. Disabled - The account is disabled, and the user cannot access it, but the identity is not disabled in Identity Security Cloud. This can occur when an administrator disables the account or when the user's lifecycle state changes. Locked - The account is locked. This might occur when someone has entered an incorrect password for the account too many times. Pending - The account is updating. |
| AccountId | The account ID from the cloud service provider for a given account. Resource access reports lists all known accounts in SailPoint CIEM that have resource access even if the account is not correlated to an identity. |
| Service | The service the resource belongs to. |
| ResourceAccountName | The sub source where the resource belongs. This value will be N/A for Azure and GCP resources that are directly at the AzureTenantId or OrganizationId level. AWS - AccountId Azure - SubscriptionId GCP - ProjectId |
| CloudSourceNativeId | The ID of the CSP parent source where the resource exists. AWS - ManagementAccountId Azure - AzureTenantId GCP - OrganizationId |
| CloudSubSourceNativeId | The subsource where the resource is. This value will be N/A for Azure and GCP resources that are at the AzureTenantId or OrganizationId levels. AWS - AccountId Azure - Subscription Id GCP - ProjectId |
| Manager | The manager of the identity with resource access. |
| Department | The department of the identity with resource access. |
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.