Managing AWS Cloud Accounts and Entitlements
To display your AWS entitlement data, you must mark supported entitlements as cloud enabled.
Supported Entitlement Types
You can use the following AWS and AWS Identity Center entitlements:
GroupsAWSManagedPolicyCustomerManagedPolicyInlinePolicy
GroupsAccountPermissionSet
The CIEM AWS source aggregates AWS Identity Center accounts and entitlements.
Viewing Identity Center Accounts and Entitlements
After you've aggregated your source, you can view the collected Identity Center users on the Accounts tab of the CIEM AWS source.
SailPoint CIEM uses the AWS Identity Center Groups and AccountPermissionSet entitlements to identify cloud access. If you enabled native change detection, your AWS accounts will be scanned for changes made out-of-band.
Notes
-
The CIEM AWS connector supports organization instances of Identity Center. Account instances are not supported. Refer to Organization and account instances of IAM Identity Center for more information.
-
Not all fields apply to Identity Center users.
| Attribute | Type | Description |
|---|---|---|
| UserName | string | The friendly name of the user |
| UserId | string | The unique ID of the user |
| Path | string | Path to the user |
| ARN | string | Amazon Resource Name of the user |
| CreatedDate | string | User Creation date |
| ConsoleAccess | string | Password Status |
| Access Keys | string | Access keys associated with the user |
| AWS CodeCommit HTTPS Credentials | string | AWS CodeCommit HTTPS Git credentials associated with the user |
| AWS CodeCommit SSH Keys | string | AWS CodeCommit SSH public keys associated with the user |
| Signing Certificates | string | Signing Certificates associated with the user |
| AccountType | string | Account is either Federated, Local Federated or Local |
| AWSAccountSet | string (multi-valued) | AWS Accounts this User has access to |
| DisplayName | string | User friendly display name |
| string | User email |
While the schemas match, the account ID displayed on the CIEM AWS source is the account ID associated with a user's AWS Identity Center access, not their AWS IAM ARN.
Identity Store APIs
SailPoint CIEM calls the following Identity Store and Identity Store SSO APIs:
ListUsersListGroupsListGroupMemberships
ListInstancesListPermissionSetsDescribePermissionSetListAccountsForProvisionedPermissionSetListAccountAssignmentsGetInlinePolicyForPermissionSetGetPermissionsBoundaryForPermissionSetListManagedPoliciesInPermissionSetListCustomerManagedPolicyReferencesInPermissionSet
Viewing Identity Center Entitlements
After you've aggregated your source, you can view the collected Identity Center entitlements on the Entitlements tab of the CIEM AWS source.
SailPoint CIEM uses the AWS Identity Center Groups and AccountPermissionSet entitlements to identify cloud access. They are comprised of the following schemas:
Identity Center Group Schema
| Attribute | Type | Description |
|---|---|---|
| GroupId | string | The Unique Identifier for the group |
| GroupName | string | The display name of the group |
| GroupType | string | Group is either Federated, Local Federated, or Local |
AccountPermissionSet Schema
| Attribute | Type | Description |
|---|---|---|
| AWSAccountName | string | The Account Name of associated AWS account |
| AWSAccountId | string | The Account Id of the associated AWS account |
| AccountPermissionSetId | string | Unique Id for the entitlement |
| PermissionSetName | string | The Name of the Permission Set associated with this assignment |
| DisplayName | string | The Display name for the AccountPermissionSet |
| Permission Set ARN | string | The ARN of the Permission Set |
Marking AWS Cloud-Enabled Entitlement Types
When your entitlements are pulled from your AWS cloud environment, you must mark the AWS IAM entitlement types that relate to cloud access. If you use AWS Identity Center, you must also mark those entitlements as cloud enabled on the CIEM AWS source.
Identifying these entitlements as cloud enabled will display cloud access details for human identities with those entitlements. It will also allow certification campaign reviewers to view the cloud access details on cloud entitlements included in certification campaigns for AWS cloud infrastructure users.
Marking AWS IAM Entitlements
On the AWS IAM source, you must mark the supported entitlements as cloud enabled to allow SailPoint CIEM to display the cloud access granted by AWS entitlements.
To mark entitlements as cloud enabled on the AWS IAM source:
- Go to Admin > Connections > Sources.
- Select or edit the AWS SaaS or VA-based source.
- In the Entitlement Management section, select Entitlement Types and Schemas.
-
Edit the entitlement type and select the Cloud Enabled checkbox for the following entitlements:
GroupsAWSManagedPolicyCustomerManagedPolicyInlinePolicy
-
Select Update.
You can now view an identity's cloud access granted through entitlements and add cloud-based entitlement types to certification campaigns to allow certifiers to view the effective access your AWS IAM users have to your AWS resources.
Important
If you are using AWS Identity Center, you must also mark your AWS Identity Center entitlements as cloud enabled.
Marking AWS Identity Center Entitlements
If you use AWS Identity Center, you must mark the supported Identity Center entitlements as cloud enabled to allow SailPoint CIEM to display the cloud access granted by Identity Center entitlements.
To mark entitlements as cloud enabled on the CIEM AWS source:
- Go to Admin > Connections > Sources.
- Select or edit the CIEM AWS source.
- In the Entitlement Management section, select Entitlement Types and Schemas.
-
Edit the entitlement type and select the Cloud Enabled checkbox for the following entitlements:
GroupsAccountPermissionSet
-
Select Update.
ICAccountAssignment Entitlement
SailPoint CIEM previously used the ICAccountAssignment Identity Center entitlement. That has been changed to AccountPermissionSet. You must mark AccountPermissionSet as cloud enabled to continue receiving your Identity Center cloud data.
SailPoint CIEM can now display the effective access users have to your AWS cloud resources.
Provisioning Identity Center Directory Accounts
If you are using the Identity Center directory as your identity source, as opposed to Active Directory or another external IdP, you can provision Identity Center accounts in Identity Security Cloud.
The IdentityStore API does not support updating a user's password or enabling and disabling users. Therefore, password provisioning and account enable/disable operations are not supported.
You can enable Identity Center directory account provisioning in your CIEM AWS source.
Viewing Effective Access to AWS Resources
After marking your entitlement types and gathering data from your cloud sources, you can view the effective access cloud-enabled entitlements provide to resources. This includes access provided through roles the user can assume.
You can also include cloud-enabled entitlements in certification campaigns to allow your certifiers to refer to cloud access details like the last level of access and type of action taken on the resource when making access decisions.
Note
Some CloudTrail entries delivered by AWS services do not contain the Resource attribute, which is used to display the last activity on an AWS resource. Your certifiers will still see how the resource was accessed, but might not have full activity data details.
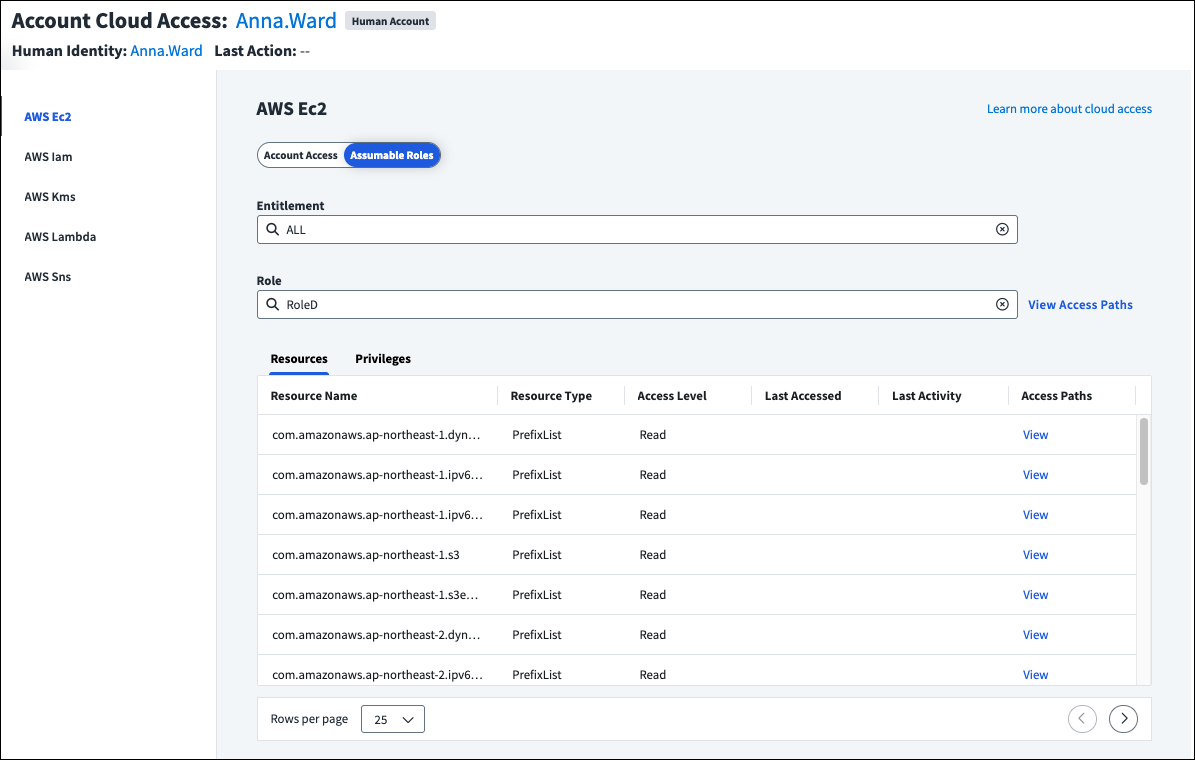
Viewing AWS Assumable Roles
If the entitlement is on an AWS source and grants access to an AWS resource, you can select Assumable Roles. If the identity can assume AWS IAM roles, including roles that can be indirectly reached through role chaining, they can be selected from the Role field to display the associated resources and privileges.
For a visual representation of how the user can access the specified role through the chosen entitlement, or all entitlements, select View Access Paths above the table. You can switch between viewing the entitlement role path or all role paths.
To see the access paths the role has to a specific resource, select View in the Access Paths column of the table.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.