Access Recommendations
SailPoint Access Recommendations empowers users and certifiers in your organization to make more informed access decisions. It uses peer group analysis and identity attributes to recommend access to your users and help certifiers decide whether access requests should be approved or denied.
Identity Security Cloud customers with Access Recommendations receive recommendations related to access requests and certifications when they are available.
Understanding Peer Group Analysis
Peer group analysis is a machine learning model that analyzes user data and calculates similarity based on identities and their access. A network graph representation of identity-to-identity, entitlement-based similarity is used to identify densely connected communities of identities.
SailPoint AI-Driven Identity Security uses peer group analysis to organize your identities into peer groups based on common entitlements, and simplify the creation and maintenance of a dynamic identity governance program.
Peer groups are constantly evolving with your data and are updated regularly.
Access Request Recommendations
Access request recommendations guide end users to request appropriate access items in the Request Center, based on an analysis of access held by other similar users. Each user is presented with their top 15 access request recommendations, enabling them to confidently request access.
Note
Due to limitations in AWS regional support, entitlement recommendations are only available for customers in AWS regions where the AWS SageMaker LLM that SailPoint employs is supported.
The following regions are unavailable:
- Middle East (UAE): me-central-1
Access request recommendations are generated based on combinations of the following:
- Peer group analysis
- Dense clustering based on the “Manager” identity attribute
- Users who share the same AI core identity attributes
- Recommendation threshold calculation
- Configurable access request recommendation attributes
Note
The system may evaluate the elements above and not find any recommendations for a user.
Access request recommendations filter out access that is too common, rare across the whole organization, or not requestable.
-
Common access is access that is widespread across the organization. If users do not have this common access, it will not be recommended to them unless they are designated as a Joiner new to the organization.
-
Access that is rare across the whole organization is filtered out. For example, if there are a small number of users with manager-only roles within the organization, that access will not be recommended even if those roles are common with their team.
- Access that is marked as non-requestable is excluded from recommendations.
Note
There may be a delay in recalculating recommendations based on a change in the requestable status of an access item. If it is changed from requestable to not requestable, the item may still show up as recommended until overnight processing takes place. If a user tries to request the item during this time, the request will be blocked and an error message will display.
Viewing Access Request Recommendations
Users can view their access request recommendations in the following ways:
- By selecting View Access Recommendations on the banner that's displayed after logging in
- On the Request Center's Recommended tab
At Log In
When access request recommendations are available for a user, a banner is displayed to notify them when they log in. Select View Access Recommendations to open the Recommended tab in the Request Center.
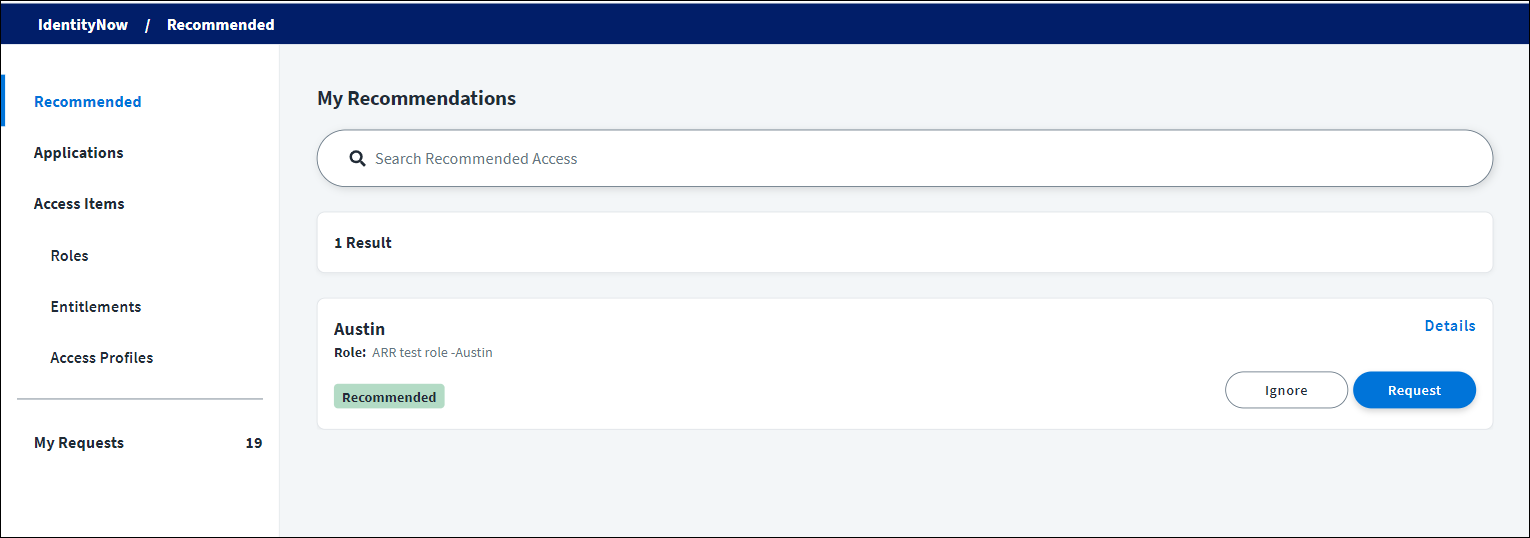
Recommended tab
The Recommended tab lists the user's top 15 recommended entitlements, access profiles, and roles. Depending on the type of access item, recommendations may include information about why this access is recommended to you.
Note
The Recommended tab does not appear when you have no recommendations. This may happen when a set of recommendations has been requested, approved, and assigned, and no further recommendations are available. It could also happen if the attributes needed for making recommendations are not mapped for the tenant or set for the identity.
Select Details on an access item to display additional information about the access.
Users can select Request to request the access or select Ignore to dismiss the recommendation. Dismissed recommendations will not be shown again.
Using Attributes with Access Request Recommendations
You can use the following attributes to fine-tune your organization's access request recommendations. Contact Professional Services to enable, disable, or change your access request recommendation attributes as needed.
Restriction Attribute
By default, the access request recommendations that users see for roles and profiles are restricted based on the location identity attribute. For example, imagine an organization has identities with location attributes of "Austin" and "Remote." If the team members look very similar according to peer group analysis, but the recommendations are restricted by location, "Austin Facilities Access" would be recommended only to identities with the location identity attribute set to "Austin."
The recommendation restriction attribute can be disabled or set to a different identity attribute that makes sense for your organization.
Joiner and Start Date Attributes
Role and access profile recommendations are broader for someone who is a new joiner than for existing members of a team. A joiner may be identified by either the created date, joiner attribute, or start date attribute.
By default, recommendations are based on the created date - an identity is considered a joiner for 45 days after the date they were added to the system. You can override that default by using a joiner attribute or a start date attribute.
If your organization already has an identity attribute that is used to designate identities as new, such as “joiner,” “newHire,” or “isNew,” a recommendation joiner attribute can be set to this existing identity attribute instead of created date. SailPoint will not try to infer if an identity is new and will trust the organization's designation. If a joiner attribute has been created but the value is null, then the start date attribute is assessed.
If identities in an organization do not have new/joiner identity attributes, a different identity attribute can be designated as a start date attribute. This enables SailPoint to infer whether the identity has recently joined. The identity will be considered a joiner for 45 days after the start date.
If the identity does not have a joiner or start date attribute, the date the identity was created will be used.
Job Title, Location, Department, and Manager Attributes
Entitlement recommendations are made based on the access held by users who share a job title, location, department, or manager attribute. It's important that identities have those attributes mapped.
Role and access profile recommendations also rely on the manager attribute.
Using Recommendations to Make Access Decisions
Certification recommendations make the access reviewers in an organization more efficient and confident when approving, revoking, or denying access.
Certification recommendations are generated based on the following:
- Peer group analysis
- The organization’s identity attributes
- Users who share the same AI core identity attributes
- Recommendation threshold calculation
Access reviewers receive certification recommendations for entitlements, roles, and access profiles. Recommendations are not available for role composition or uncorrelated accounts certifications. Certification recommendations are enabled by default.
Admins and Certification Admins can control whether or not access reviewers see certification recommendations as follows:
- For campaigns from Search, disable or enable the Include Recommendations in your campaign toggle when creating a campaign.
- For manager or source owner campaigns, go to Admin > Global > System Settings > Feature Settings, select Other Features and clear or select the Enable Certification Recommendations checkbox.
When reviewers and approvers are evaluating access decisions, they will see recommendation icons to help guide their decision-making process. These recommendations leverage statistical methods to automatically determine the best combination of identity attributes and machine learning outputs to inform a decision threshold for making intelligent access recommendations.
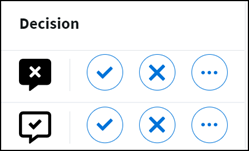
Recommendation icons appear as follows:
Recommendation icons are used to communicate the following information:
-
 - More than 70% of the identities in the peer group have the access.
- More than 70% of the identities in the peer group have the access. -
 - The access is unique within the identity's peer group, or 70% or less of the identities in the peer group have the access.
- The access is unique within the identity's peer group, or 70% or less of the identities in the peer group have the access.
Selecting an icon displays more information about the recommendation.
If no icon is displayed, it means the identity is unique, and does not have a group of peers with similar access.
Important
Recommendations are provided only as guidance. Reviewers and approvers are still ultimately responsible for making access decisions.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.