Managing Access Profiles
Access profiles are bundles of entitlements representing related sets of access from a single source. For example, in an accounting system, you could have one access profile that grants transaction entry and reporting access, and another access profile that grants vendor management access.
Access profiles are used in roles and lifecycle states and can be enabled for access requests. They can be granted to identities through:
- Automated provisioning based on assigned lifecycle states or role criteria
- Access requests, directly or through a role
- Detection, when it is determined during identity processing that a user has all of the entitlements associated with an access profile and the access profile is granted automatically. At that point, they are no longer considered to have the entitlements individually, but instead have the access profile.
Creating Access Profiles
-
Go to Admin > Access Model > Access Profiles.
-
Select Create New.
-
Complete the relevant configurations.
- Configuration - Determine the access profile’s basic information.
- Manage Entitlements - Choose the entitlements to include in this access profile.
- Metadata Attributes - Add metadata attributes to the access profile.
- Access Requests - Enable access requests and set a review process for requests.
- Multiple Account Options - Set the criteria to determine which account will receive this access profile when it's provisioned through automatic assignment to a user with multiple accounts on a source.
- Select Enable Access Profile in the top right. Disabled access profiles cannot be used for access requests.
Important
New or updated access profile configurations must be applied through identity processing. Refer to Applying Changes for details.
Creating Access Profiles from Sources
You can also create access profiles within the source itself.
- Go to Admin > Connections > Sources.
- Select or edit the source you want to create access profiles in.
- In the Aggregation History and Connections section, select Access Profiles.
- Select Create Access Profile.
-
Complete the relevant configurations.
- Configuration - Determine the access profile’s basic information.
- Manage Entitlements - Choose the entitlements to include in this access profile.
- Metadata Attributes - Add metadata attributes to the access profile.
- Access Requests - Enable access requests and set a review process for requests.
- Multiple Account Options - Set the criteria to determine which account will receive this access profile when it's provisioned to a user with multiple accounts on a source.
-
If you want to use this access profile in access requests, select Enable Access Profile in the top right.
Configuration
When creating an access profile, you will define the access profile’s basic details.
-
In the Name field, enter a unique and descriptive name for your access profile. Access profile names cannot exceed 128 characters.
-
Select the Owner dropdown list to choose an identity to own this access profile. This identity can be configured as a reviewer in access requests or certifications.
To find an identity in this field, begin typing their name.
-
In the Description field, provide additional details about this access profile and the access it contains. This field allows a maximum of 2,000 characters.
Best Practice
Provide user-friendly, informative names and descriptions for your access profiles. Both are visible in certifications, access requests, and approvals. A detailed description will improve the quality and speed of reviewer decisions.
-
Select the Entitlement Source dropdown list to choose the source the entitlements in this access profile should come from. This can't be edited later.
-
Select Save.
Manage Entitlements
Access profiles must contain at least one entitlement.
- In the access profile configuration, select Manage Entitlements.
-
In the Add Entitlement field, search for an entitlement from the source you selected in the Configuration page and select + to add it to this access profile. Add more entitlements as needed.
-
To remove an entitlement from the access profile, select X in the Delete column of the entitlement row.
-
Select Save.
When this access profile is provisioned to an identity, these entitlements will be granted to that identity.
Metadata Attributes
You can add metadata attributes to an access profile to provide valuable contextual information.
To add metadata attributes:
-
In the access profile configuration, select Metadata Attributes.
-
Select Add Attributes.
-
Use the dropdown fields to select values for any listed attributes that you want to add to the access profile.
-
Select Save.
For information about adding custom metadata attributes to the list, refer to Creating Custom Metadata Attributes
Access Requests
If you have the Access Request service in your site, you can configure access profiles that users can request in the Request Center. Refer to Access Requests for details.
Note
Access profiles can only be associated to an identity one time, so users who already have an access profile cannot request it for another account. If you need to be able to assign the same access to multiple accounts for the same user, you must request the individual entitlements or bundle the access into roles.
Multiple Account Options
When an identity has multiple accounts on a source, you can specify the criteria for determining which of the user’s accounts should receive the access. This applies to access profiles automatically provisioned through lifecycle states or automated role assignment.
Important
- These criteria are not applied for users with only one account on the source.
- These criteria do not apply to access requests. If identities have multiple accounts on the entitlement source, the requester will select the accounts that need access in the Request Center. Options are displayed by account name and account ID.
When no account or multiple accounts match the criteria, provisioning will fail. If your organization has enabled manual account selection, the source owner can complete a form in their tasks to choose which account should receive the access. When the account is selected, a manual task might be required to add the access to the chosen account.
To configure the account selection criteria:
-
In the access profile configuration, select Multiple Account Options.
-
In the Attribute field, select the account attribute to use in this filter.
-
In the Operation dropdown list, choose an operation to compare the attribute to the value you enter.
- Equals - The attribute and value must match.
- Does Not Equal - The attribute and value cannot match.
- Contains - The specified value must exist somewhere within the attribute’s value.
-
Type a value in the Value field to compare to the attribute. This field is case insensitive.
-
If you need multiple criteria, select Add Criteria and repeat steps 2-4.
- Use the Within Groups toggle to specify whether your criteria should be combined with an AND or an OR operator.
- AND means all criteria must be met while OR means meeting any of the criteria produces a match.
- Use the Within Groups toggle to specify whether your criteria should be combined with an AND or an OR operator.
-
If your requirements are more complex, needing both AND and OR, use Add Group to add another group.
The operator not selected for Within Groups will automatically apply between groups.
When an automated provisioning action takes place that would grant this access profile to an identity with multiple accounts on the source, the criteria on this page will be used to determine which account should receive the access.
Account Selection Criteria Examples
Your configuration to choose the correct account could range from simple to very complex.
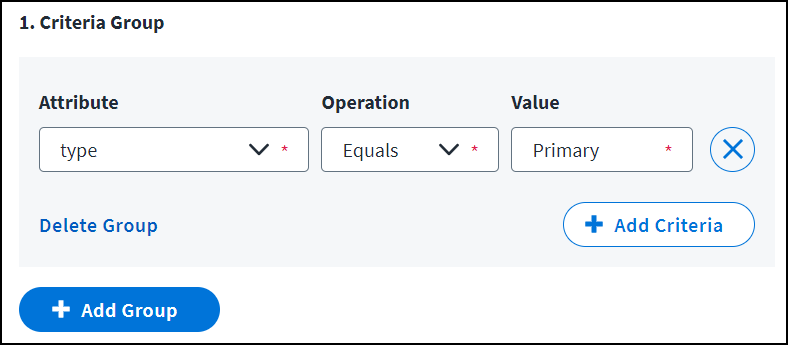
Simple selection criteria don’t use any AND/OR operators. To provision the access to the identity's account that has the Primary value in the type attribute, specify attribute type, the operator Equals, and value Primary.
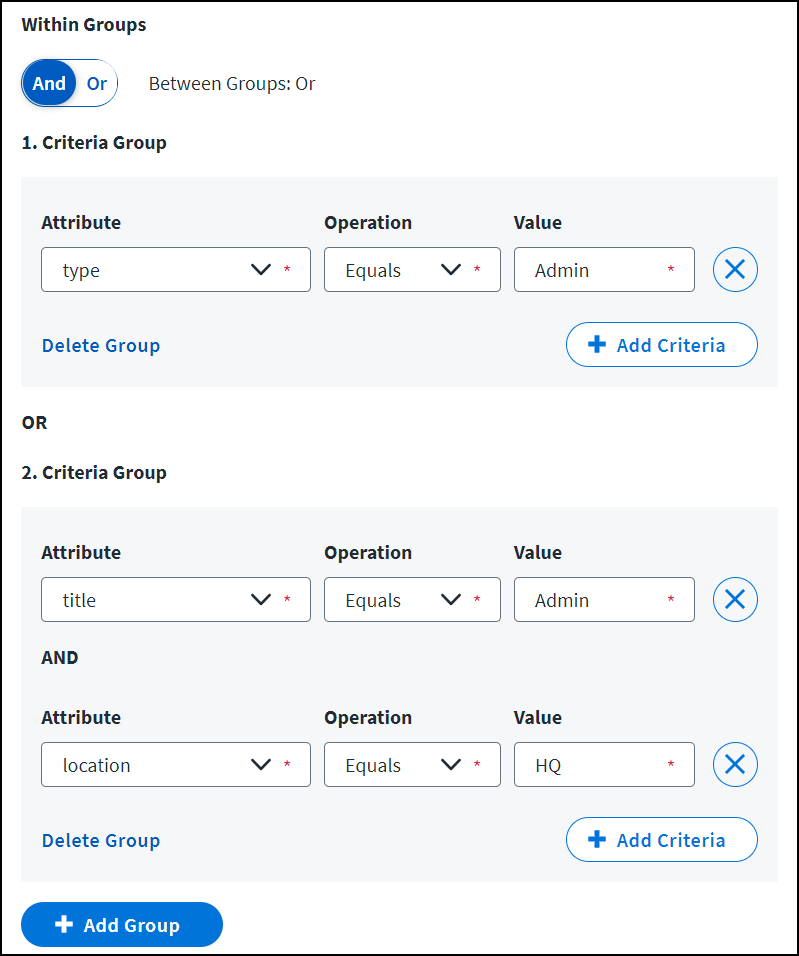
Very complex criteria might include both AND and OR. To provision the access profile to the user's account where the type equals Admin, or to the user's account with a title of Admin and a location of HQ, you must specify the title and location requirements together with AND while including the type in an OR branch, as shown here:
Editing Access Profiles
You can change most of the access profile attributes defined when creating an access profile.
If your organization has licensed SailPoint Identity Graph, you can select the View in Identity Graph icon for an existing access profile. A visualization is displayed showing the access profile's relationships with other access objects.
To edit an existing access profile:
-
Go to Admin > Access Model > Access Profiles.
-
Select Actions
 > Edit on the access profile you want to edit.
> Edit on the access profile you want to edit. -
Make changes to the access profile’s configuration, entitlements, access request configurations, or account selection logic. Select Save on each page you change.
- You cannot change the Entitlement Source. To change your source, create a new access profile and delete the unneeded one.
- Refer to Changing Access Profile Entitlements for the impact of editing the entitlements in an access profile.
Best Practice
When you have completed a set of access profile and role changes, select Apply Changes to apply the new configurations to all identities through identity processing.
Changing Access Profile Entitlements
When an access profile's entitlements are edited, users that had the access profile already might gain new entitlements, but they won't lose any.
When entitlements are removed from an access profile:
- Those entitlements are not removed from identities that currently have the access profile.
- The removed entitlements become independent entitlements for the identity, detached from the access profile.
When entitlements are added to an access profile:
- For identities that have the access profile due to a role or lifecycle state assignment, the added entitlements are provisioned to their accounts to enforce the role or lifecycle state’s requirements.
- For identities that have the access profile due to detection or based on a previous access request for the access profile itself, the additional entitlements are not provisioned.
- The user’s entitlements do not change.
- The user only retains the access profile if they already have all of the entitlements in the new list.
These changes take place the next time the identity is evaluated in identity processing.
Applying Changes
Access Profile configuration changes are not immediately applied to identities. You must select Apply Changes on the access profile list page to initiate identity processing for all identities in your organization, to recalculate users’ access based on your changes.
For best system performance, wait to select Apply Changes until you are ready to apply the whole set of configuration changes to your whole set of identities. Selecting it for roles, access profiles, or applications automatically processes all three.
Deprovisioning with Access Profiles
You can revoke access profiles from users through various provisioning actions such as access removal requests and lifecycle state changes.
The following are the limitations and behavior of access profile deprovisioning:
- Roles supersede access profiles.
- If the identity was granted an access profile based on their membership in a role, the access profile can't be deprovisioned directly. The identity must be removed from the role, which also deprovisions its access profiles and their entitlements.
- If a role assignment contains overlapping access with an access profile, the user will retain the role's required access when the access profile is revoked.
- Overlapping entitlements between access profiles are revoked.
- When a user has two access profiles (not through roles) with overlapping entitlements, revoking one of those access profiles removes all of its entitlements.
- The user will lose the second access profile because they do not have its required entitlements. However, any other entitlements granted to the user by the second access profile are retained as individual entitlements.
- This is true whether the access profile was detected for the user or granted to them through provisioning processes.
Revoking Access Profiles
Admins and Access Revokers can submit requests to revoke an identity’s access profiles.
Note
You can also revoke users' access to access profiles through lifecycle states.
- Go to Admin > Identity Management > Identities.
- Locate the identity that you need and select it.
- From the left navigation, select Access.
- Select the Access Profiles tab.
- Select the access profile name that you want to revoke.
- On the access profile’s Details tab, you'll see whether the access profile is revocable or not. If it is, you can select Revoke Access Profile to request revocation.
- In the Request Revocation dialog, enter comments.
- Select Revoke.
- A success message confirms that your revocation request was submitted.
If the request doesn't require approval, the identity’s access removal will be triggered. If the request is configured to require approval, it is sent to approvers before the access is deprovisioned.
Adding or Editing an Access End Date
To add or change an end date for an access profile, locate the access item, and select Add End Date or Edit in the End Date column. Select a date in the Access End Date and Time field, add comments (optional for some requests), then select Save.
If you begin editing an access end date and change your mind, select Cancel, then confirm that you want to discard changes.
When you change an access end date, any configured maximum duration for the item will be enforced, even if the current end date (before edits) is beyond the maximum duration because it was originally assigned before the requirement was in place. The last possible new end date is calculated by adding the maximum duration to the current date.
Disabling an Access Profile
You can disable access profiles if you need to pause their usage.
To disable an access profile:
-
Go to Admin > Access Model > Access Profiles.
-
Select Actions
 > Disable on the access profile you want to disable.
> Disable on the access profile you want to disable.Disabling an access profile has these implications:
- Removes the access profile from the Request Center (if previously enabled for requests).
- Removes the access profile from your identities the next time they are examined in identity processing.
- Does not deprovision its entitlements from identities who previously held the access profile. Identities will keep the entitlements; they will just no longer be associated with the access profile.
- The access profile will still appear in existing certifications, and any revocation decisions will still be able to be enforced.
The access profile will still appear in any roles or lifecycle states that previously included it to facilitate reenabling and applying it again later.
Important
If all the entitlements in an access profile are deleted, the access profile is automatically disabled. This can occur when entitlements from the source are aggregated and the access profile's entitlements are no longer present.
This can also occur if an access profile's entitlements are renamed or changed. Aggregation deletes the old entitlement and the new, renamed entitlement is not associated with the access profile.
Information about deleted entitlements' connection to access profiles is not retained, so if they are later recreated in the source and readded, the access profile will need to be rebuilt.
Deleting an Access Profile
You can delete access profiles if you no longer need them.
Important
You cannot delete an access profile that is currently included in any provisioning configuration. You must first remove it from all lifecycle states and roles.
To delete an access profile:
-
Go to Admin > Access Model > Access Profiles.
-
Select Actions
 > Delete on the access profile you want to remove.
> Delete on the access profile you want to remove.You can also select the checkbox beside the name of each access profile you want to delete and select the Delete button.
-
A warning appears, reminding you to remove the access profiles from provisioning configurations. Select Continue.
Deleting an access profile has these implications:
- Removes the access profile from the Request Center (if it was previously enabled for requests).
- Removes the access profile from roles or lifecycle states that previously included it.
- Does not deprovision its entitlements from identities who previously held the access profile. Identities will keep the entitlements, but they will no longer be associated with the access profile.
- The access profile will still appear in existing certifications, and any revocation decisions will still be able to be enforced.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.