Configuring Security Integrations
You can use third-party security integrations for password reset and account unlock options.
Important
DUO instructions apply to both IdentityNow and Identity Security Cloud.
Okta Verify
You can configure Okta Verify to integrate with Identity Security Cloud to use it as a password reset method for your identity profiles.
You must first create an API token. Refer to the Okta API token management documentation for more information.
Notes
- Okta recommends generating API tokens from a service account with permissions that do not change.
- Tokens are only valid if the user who created the token is also active.
To integrate Okta Verify with Identity Security Cloud:
-
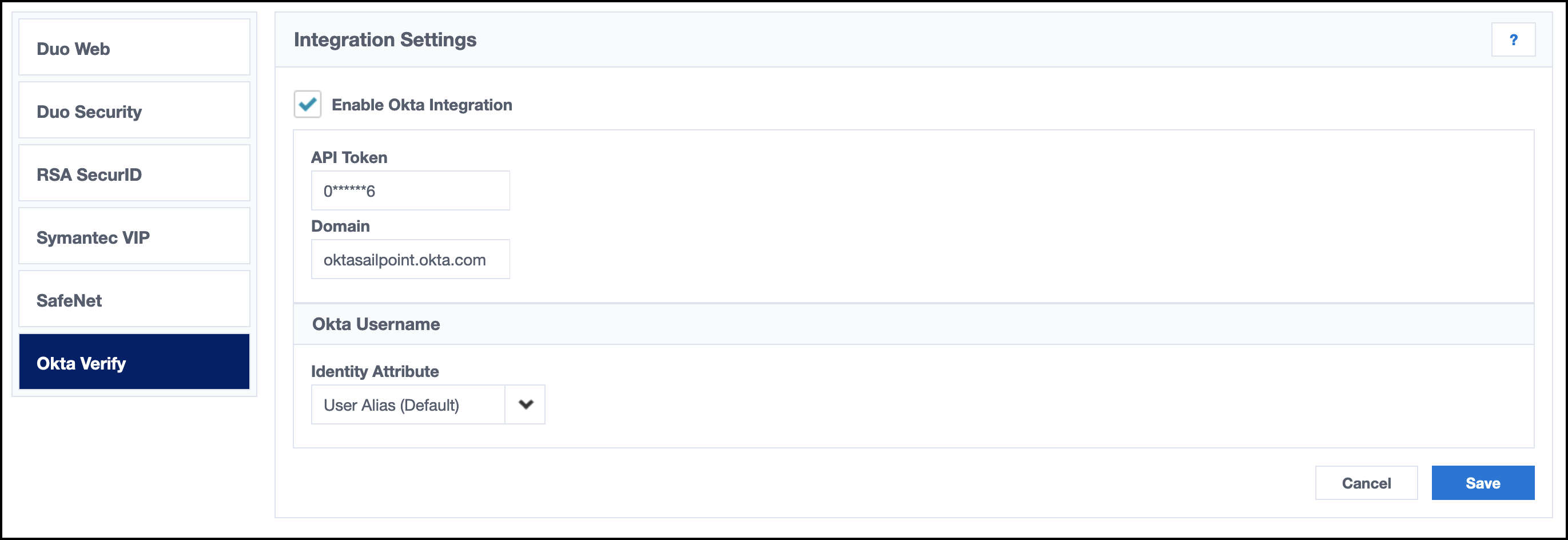
Go to Admin > Connections > Integrations > Okta Verify.
-
Select the checkbox to Enable Okta Verify Integration.
-
Enter the API token you generated in Okta.
- Enter the domain.
- Under Okta Username, use the dropdown menu to select the Identity Attribute. The default is Work Email, or you can select other options that match the username in Okta.
- Select Save.
- Select Test Connection to verify that the connection is working.
- Configure Okta Verify as an available password reset method.
Duo Web
You can use Duo Web to embed iFrames and provide an improved user experience for password resets and account unlocks. Refer to Duo’s recommended best practices for Identity Security Cloud Password Resets.
Note
The Identity Security Cloud mobile app does not support password reset or unlocks for end users authenticating via Duo Web. You can use the mobile browser instead.
You must first configure and then integrate Duo Web with Identity Security Cloud.
Configuring Duo Web
- Follow the Duo 2FA for SailPoint Identity Security Cloud configuration directions.
- In the Duo Admin Panel, go to Applications > Protect an Application and select SailPoint Web. Refer to Duo - Protecting Applications for more information.
-
For strong, two-factor authentication:
-
(Optional) Change the integration name to a custom name configured for your organization. The integration name is important because it shows up in the Duo Push request sent when a user authenticates with Duo.
-
Do not apply a Remembered Devices policy to the SailPoint Web application.
-
Do not apply a New Users policy, Authentication policy, Authorized Networks, or User Location policy that allows access without two-factor authentication to the SailPoint Web application.
-
Never set the Authentication policy to Bypass 2FA.
-
Set username normalization to None.
Important
Failure to follow these best practices can result in users bypassing Duo security. To ensure proper configuration, test Password Reset with a test user account, then immediately repeat the reset action by the same user. Duo should prompt the user to authenticate their identity every time.
For information about Duo's policy and user administration settings, refer to Duo Policy & Control and Duo Admin - Managing Users.
-
-
Select Protect this Application, and save the following information in the Duo Web application:
-
Integration key
-
Secret key
-
API hostname
You will need these keys and API hostname when integrating Duo Web with Identity Security Cloud. The key is autogenerated.
-
Notes
-
Disabling a user in Duo causes the Duo authentication options to be disabled in Identity Security Cloud for the user.
-
Your users must register at least one device in Duo to use these features.
-
If a user has not enrolled in Duo or has not registered a device, the Duo password reset methods will not be displayed. For security purposes, the user does not have the opportunity to enroll in Duo during password resets.
You are now ready to integrate Duo Web.
Integrating Duo Web
-
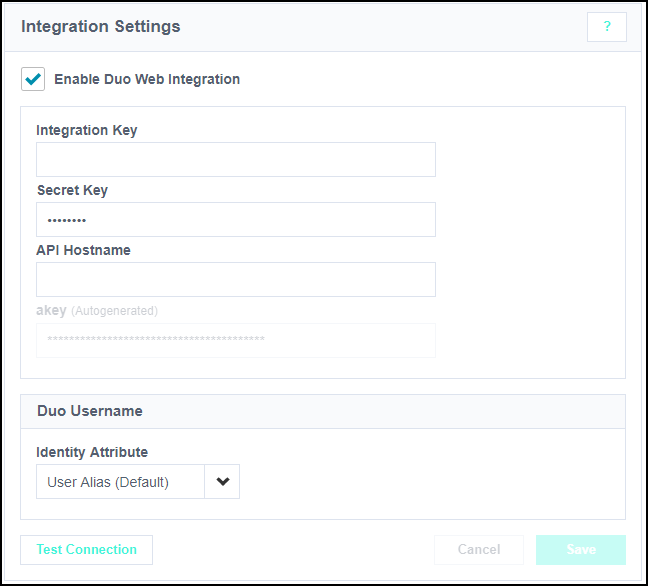
Go to Admin > Connections > Integrations > Duo Web.
-
Select Enable Duo Web Integration.
-
Complete all the available fields based on the information provided by Duo when you created the required integration. Identity Security Cloud masks your Secret Key and autogenerates and masks the key.
-
Under Duo Username, select the identity attribute that corresponds with users' Duo Security user names. By default, this is set to User Alias.
Note
If you choose an identity attribute that isn't populated for all of your identities, identities that don't have a value for that attribute cannot use Duo Web as an authentication method.
-
Select Save.
-
Select Test Connection to verify that the integration is working.
-
Configure Duo Web as an available password reset method for your identity profiles.
Note
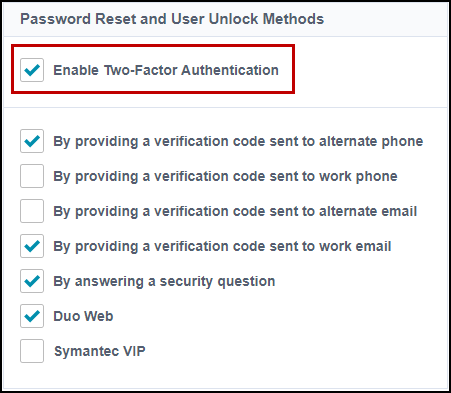
To align with Duo’s best practices, ensure that Enable Two-Factor Authentication is selected. Then select additional methods. These additional methods will be presented first. Once end users satisfy these methods, Duo Web will be presented.
RSA SecurID
You can configure RSA SecurID to integrate with Identity Security Cloud and give your users additional authentication options. Users of RSA SecurID must be correlated to an existing identity.
Configuring RSA SecurID
-
Set up an on-premise RSA 8.1 server and roll out RSA SecurID to your users.
Note
To use RSA strong authentication in Identity Security Cloud, your users must complete their RSA accounts. This includes setting up a PIN and being able to receive an RSA token.
-
Configure RSA to accept a SecurID from your users in a format Identity Security Cloud supports.
-
Create and aggregate an RSA source.
Refer to the RSA SecurID documentation for configuration guidance.
You are now ready to integrate RSA SecurID.
Integrating RSA SecurID Integration
-
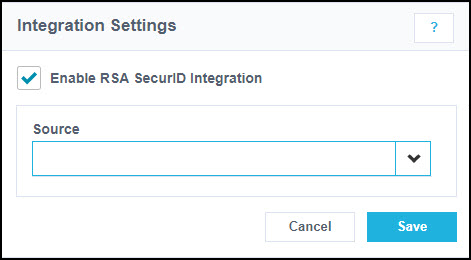
Go to Admin > Connections > Integrations > RSA SecurID.
-
Select Enable RSA SecurID Integration.
-
For Source, select the RSA Authentication Manager source.
Because only one RSA source can be configured for the integration, only users from this RSA source will be able to use RSA strong authentication methods.
-
Select Save.
-
If you have not already aggregated accounts from your RSA source, aggregate those accounts.
-
Configure RSA SecurID as an available password reset method for your identity profiles.
Symantec VIP
You can configure Symantec VIP to integrate with Identity Security Cloud for additional account unlock and password reset methods for your identity profiles.
Notes
-
If a user's account is disabled within Symantec VIP, they will not see options to use Symantec VIP.
-
If a user has not enrolled in Symantec VIP or has not registered an Access Credential, the Symantec VIP password reset options do not appear.
Configuring Symantec VIP
-
Roll out Symantec VIP to your users.
-
In Symantec VIP, request a new VIP Certificate in PKCS#12 format.
-
Complete the other required fields in the Symantec interface and note the certificate password. You will need this later..
-
Download the certificate to a known location. You will need this later.
-
To allow your users to use Symantec VIP Push notifications for strong authentication, the Enable Mobile Push option must be globally enabled on the VIP Policy Configuration page within Symantec VIP.
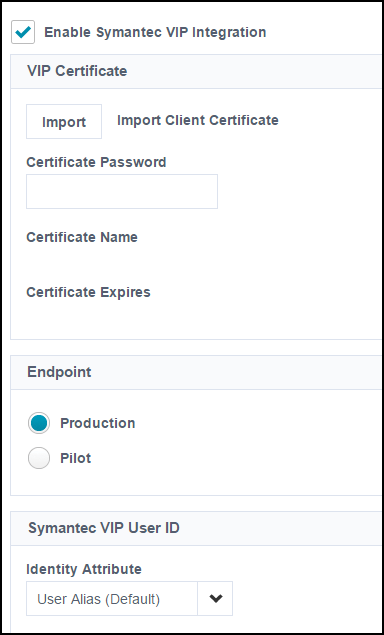
Integrating Symantec VIP
-
Go to Admin > Connections > Integrations > Symantec VIP.
-
Under Integration Settings, select Enable Symantec VIP Integration.
-
Select Import to upload the Client Certificate you created within Symantec VIP.
-
Enter the Certificate Password you configured when you generated the certificate.
-
Under Endpoint, choose the type of endpoint you are pointing to. In most cases, you will select Production.
-
Under Symantec VIP User ID, select the identity attribute that represents the users' User ID in Symantec VIP. By default, this is set to User Alias.
Important
If you choose an identity attribute that isn't populated for all of your identities, identities that don't have a value for that attribute will not be able to use Duo Web as an authentication method.
-
Select Save. The Certificate Name and Certificate Expires fields are populated automatically.
-
Select Test Connection to verify that the integration is working.
-
Configure Symantec VIP as an available password reset method for your identity profiles.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.