Identity Outliers
Identity Outliers, part of SailPoint Access Insights, enables administrators to quickly discover and remediate risky access in an organization. SailPoint discovers identities with access that is significantly different than their peers. By gathering and presenting these identity outliers in one place, admins can quickly examine and address risky access privileges in their organization.
Note
Due to limitations in AWS regional support, Identity Outliers are only available for customers in AWS regions where the AWS SageMaker LLM that SailPoint employs is supported.
The following regions are unavailable:
- Middle East (UAE): me-central-1
Prerequisites
- Your organization must have Access Insights to access Identity Outliers.
- Your organization must have Certifications to launch certification campaigns from Identity Outliers.
- Your organization must have configured a source and loaded account data.
- Your organization’s account data must be onboarded into AI-Driven Identity Security.
Process Overview
- Launch the Identity Outlier Dashboard to discover outliers.
- Review the discovered outliers.
- Remediate some or all outliers.
Each process overview step is described in detail in the sections that follow.
Discovering Outliers
Navigate to Admin > Identity Management > Outliers to display the Identity Outlier Dashboard. The dashboard presents high-level, summary information about outliers in your organization and recommended actions for remediation. SailPoint looks for new outliers regularly.
The dashboard can be accessed by Admins or users with the report admin user level.
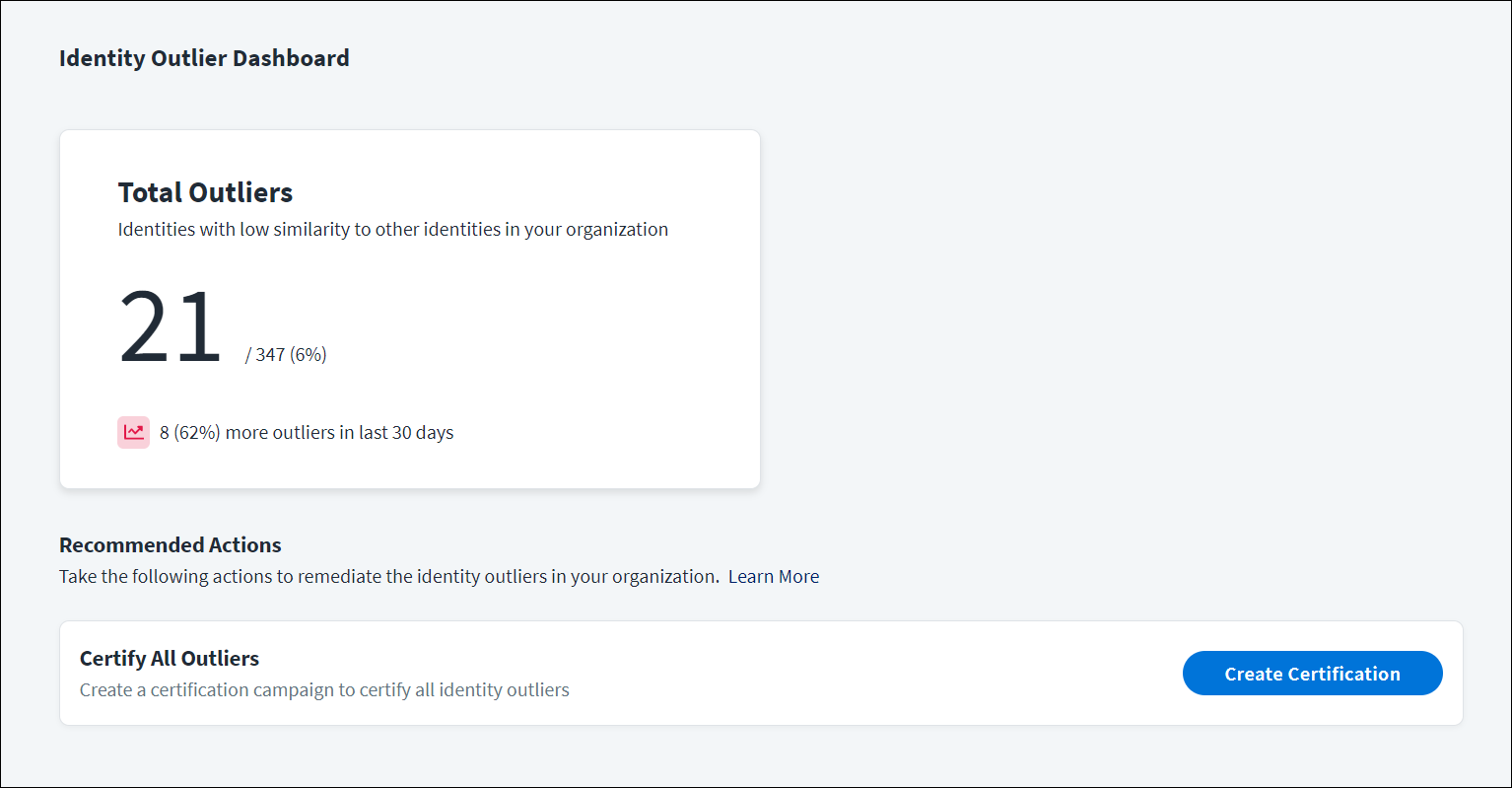
The Total Outliers card displays the following information:
- The total number of identities that have low-similarity access compared to others in the organization.
- Trends over the last 30 days, such as how many more or fewer outliers have been discovered, or whether the number of outliers has stayed the same.
If your organization has Certifications, the Recommended Actions section of the dashboard provides a quick remediation action to certify all outliers.
Reviewing Outliers
Before you decide what to do about the identity outliers in your organization, you might want to review who they are, their attributes, and why they are an outlier.
To review a list of all discovered identity outliers, select the Total Outliers card.
You can review outlier information for all outliers in the Identity Outliers list or explore contextual insights for each individual outlier identity.
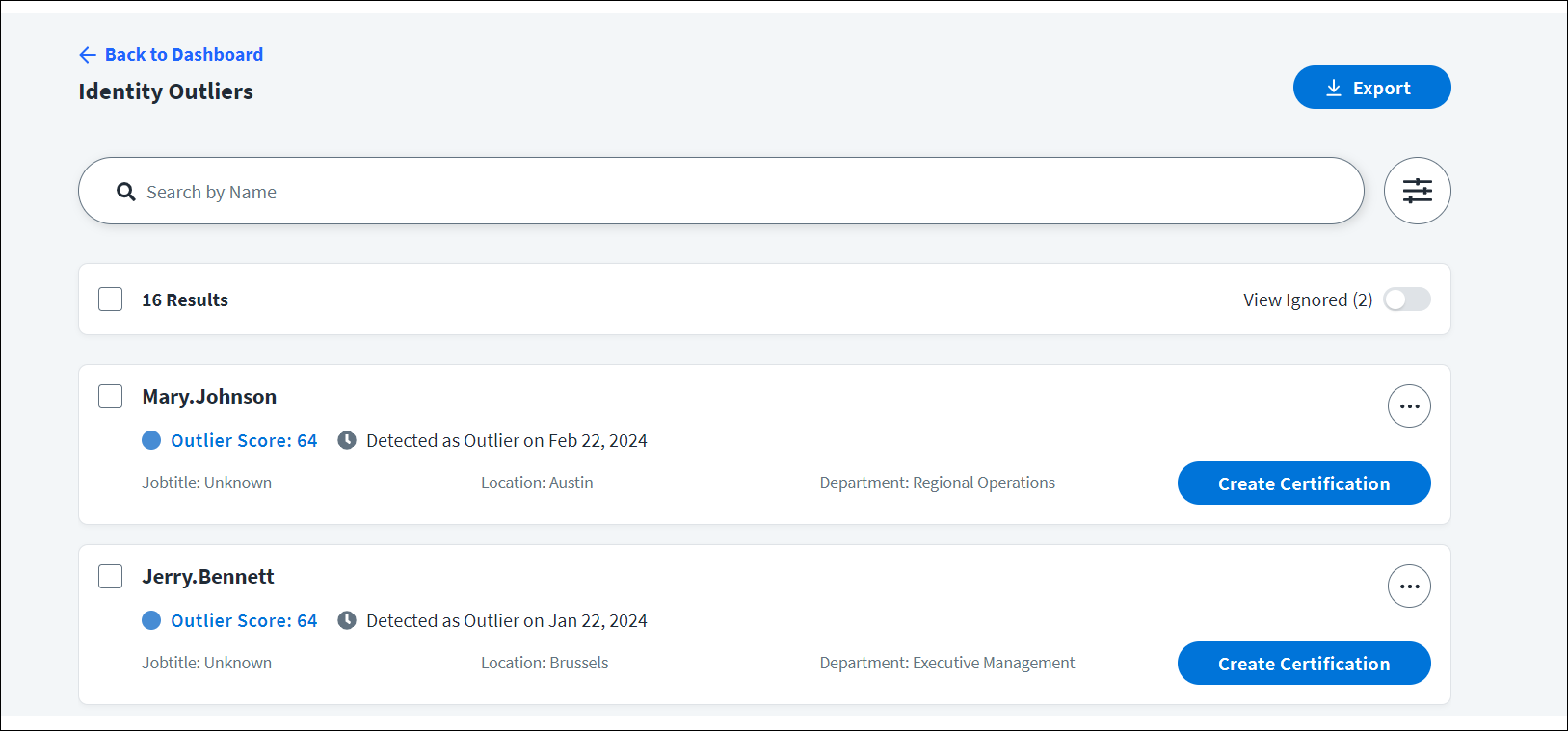
Working with the Identity Outliers List
The Identity Outliers list displays the following information for each outlier:
-
An outlier score ranging from 0-100 that indicates the potential riskiness of an identity based on their individual security factors.
-
The date they were discovered to be an outlier.
-
The AI core identity attributes that you configured after AI services setup. Any updates you make to your AI core attributes will also update the attributes displayed for each outlier.
You can work with the list of outliers as follows:
-
On the Identity Outliers page, review the list of outliers by scrolling or searching for an identity name.
-
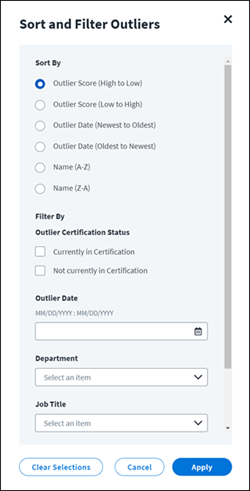
Select the Sort and Filter icon
 to sort the outliers list and filter by certification status, outlier date range, or identity attributes.
to sort the outliers list and filter by certification status, outlier date range, or identity attributes.The Outlier Certification Status checkboxes pertain only to active certifications. Staged/scheduled certifications are not considered to be active.
-
To see the access history for an outlier, select the More Options icon
 , then View Access History. You will be redirected to the Access History page for the identity.
, then View Access History. You will be redirected to the Access History page for the identity. -
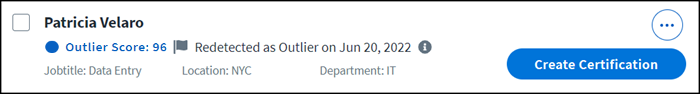
To ignore an identity outlier, select Options > Ignore. The identity will not be discovered as an outlier again unless there is a significant change in their entitlements.
If the ignored identity's entitlements change significantly, the identity will be redetected as an outlier and will reappear in the Identity Outliers list.
-
To unignore a previously ignored outlier, select the More Options icon
 , then Unignore.
, then Unignore. -
To export outlier data to a .csv file, select Export.
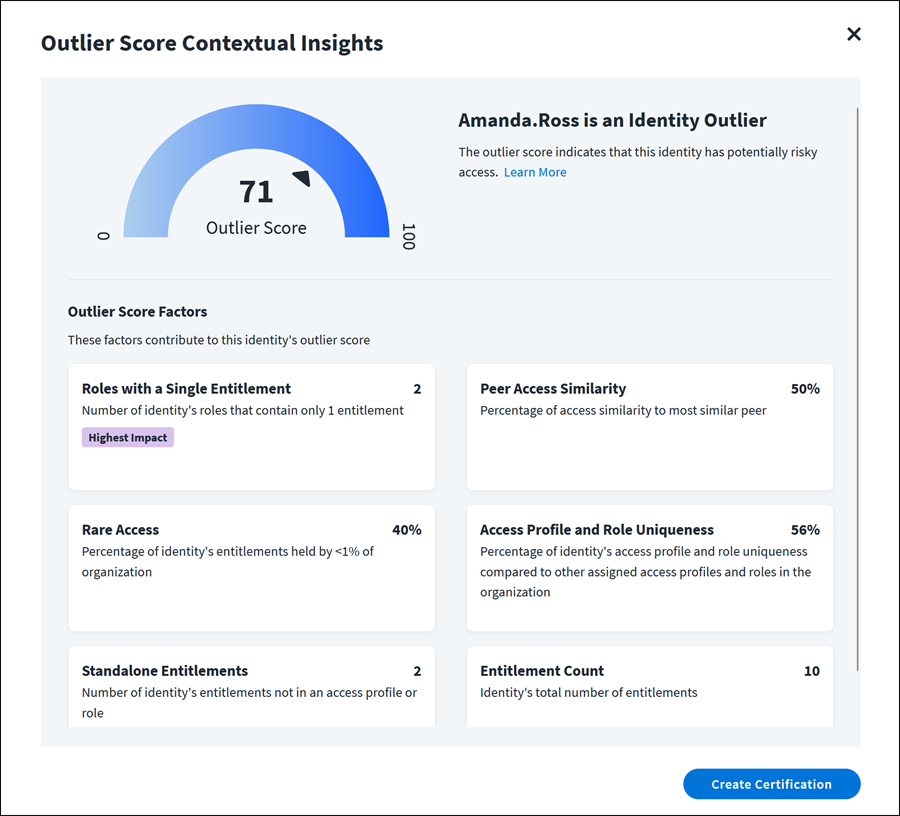
Viewing Outlier Score Contextual Insights
On the Identity Outliers page, select an outlier from the list to see the contextual insights for the outlier score.
Several outlier score factors contribute to an identity’s outlier score.
The factors displayed depend on the data available for the outlier identity. So the factors displayed might be different from one identity to another. Any of the following factors may be displayed:
-
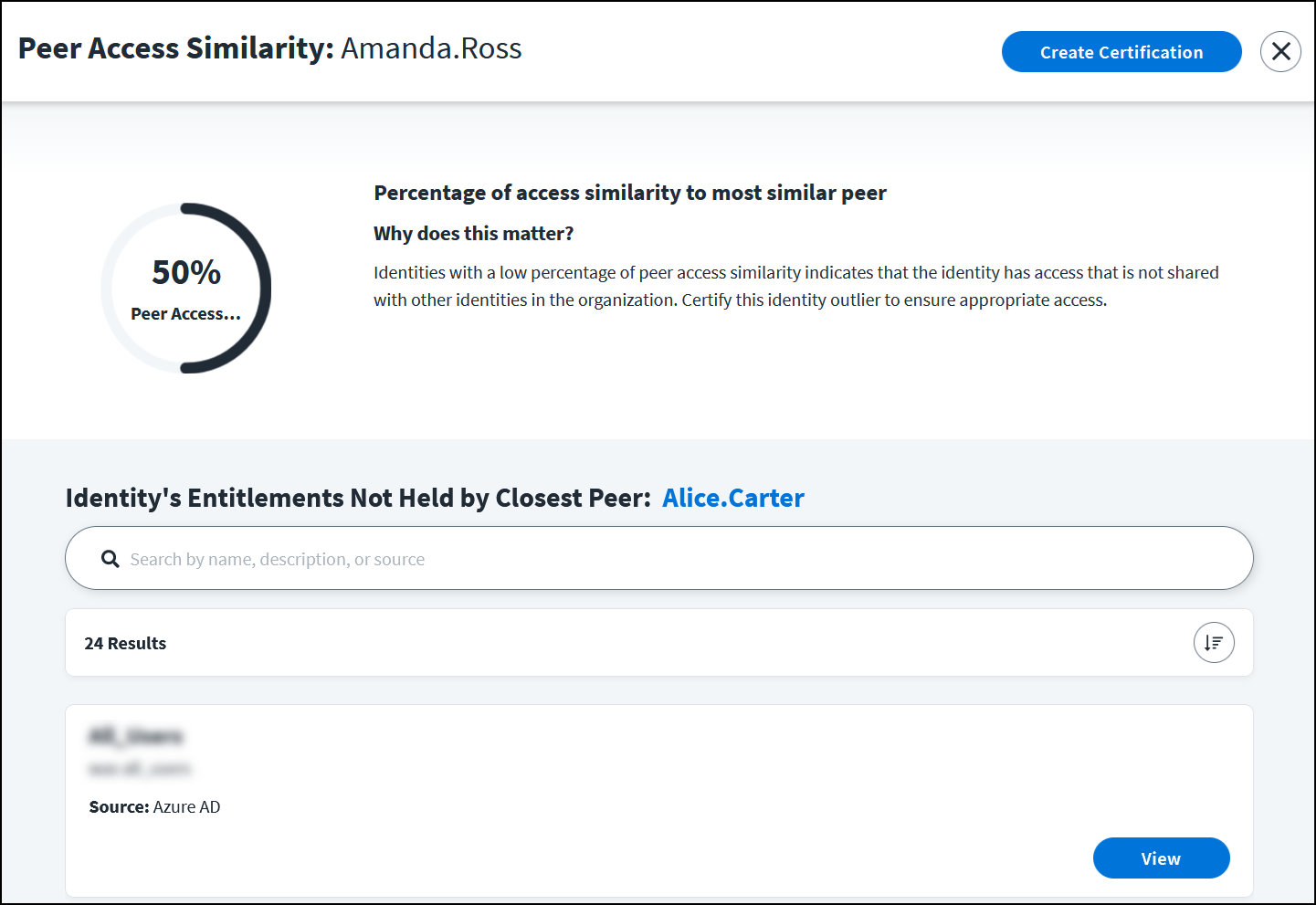
Peer Access Similarity - A percentage showing how similar the outlier's access is to the access of their closest peer.
-
Standalone Entitlements - The number of the outlier's entitlements that are not bundled in an access profiles or role. Higher counts are potentially riskier.
-
Rare Access - The percentage of the outlier’s entitlements that are held by less than 1% of all identities in the organization. Higher percentages represent greater risk.
-
Roles with a Single Entitlement - The number of the outlier's roles that contain only 1 entitlement. Higher numbers suggest closer attention to the role definitions may be warranted.
-
Entitlement Count - The outlier’s total number of entitlements. This warrants attention when the number is much higher or much lower than the average count across your identities.
-
Access Profile and Role Uniqueness - The uniqueness of the identity's roles compared to other roles in the organization.
You can select outlier score factor cards to view details about the factor.
Viewing Outlier Score Factor Details
On the Outlier Score Contextual Insights page, select an outlier score factor card to launch a factor details page that includes information about why this factor matters in your access model.
Depending on the factor, a percentage or peer average comparison visualization based on peer group analysis quickly demonstrates why this factor contributed to the score.
These factors provide a comparison of the identity outlier's access items to the peer average:
- Entitlement Count
- Standalone Entitlements
- Roles with a Single Entitlement
These factors provide a percentage comparison of the identity outlier to their peers or the overall organization:
- Peer Access Similarity
- Rare Access
- Access Profile and Role Uniqueness
The Peer Access Similarity page also includes the identity of the outlier's closest peer.
Each outlier factor details page also provides a searchable list of access items contributing to the outlier score. Select any access item in the list to learn more about its access.
Some entitlements in the access item list may have an Extremely Rare label. Extremely rare entitlements are the 10 rarest entitlements in your organization. The label may appear in lists for each outlier score factor if those entitlements are assigned to an identity outlier. You may see more than 10 entitlements labeled Extremely Rare. This occurs when the tenth item’s counts are the same for multiple entitlements, so everything with that count is tagged Extremely Rare.
Remediating Outliers
You can remediate your organization’s identity outliers by starting a certification campaign to have their access reviewed and approved. Certifications help organizations reduce the risk of inappropriate access, satisfy audit requirements, and meet regulatory standards.
Note
Certification is limited to 1,000 identity outliers per campaign.
You can create outlier certification campaigns from the Identity Outlier Dashboard or from the Identity Outliers page:
-
On the Identity Outlier Dashboard, select Create Certification to start a certification campaign for all discovered outliers.
-
On the Identity Outliers page:
-
Select Create Certification for a single outlier.
-
Select checkboxes for multiple outliers, and then select any Create Certification button to certify several outliers in one campaign.
-
Identity Outliers will automatically pre-fill a new certification campaign with the identities and entitlements. You can review them and input an appropriate certification name and campaign details to confirm the campaign.
Best Practice
We recommend you include the text "Identity Outliers" in the certification name or description to capture the source of the campaign.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.