Handling Policy Violations
By creating your first separation of duties policies, you've taken some proactive steps to keeping your organization safe.
Next, you'll use those policies to track violations and prevent some violations before they occur.
Detective Separation of Duties
Detective separation of duties allows you to detect policy violations that have occurred in your org.
Download a Report of Violations to a Single Policy
-
Go to Search.
-
Select the Policies icon in the vertical toolbar.
-
Select the policy you want to view.
-
Select the menu icon and select Get Report.
You can create one subscription to each SoD policy.
Subscribing to an SoD Policy
To receive regular reports on violations to a policy you've created, configure a policy subscription. You can subscribe to a disabled policy, but subscription emails are only sent for enabled policies.
This email is sent to users who have been added as subscribers. Subscribers can:
- View the email generated by the subscription
- View the policy in the system if they have access to the admin interface
Org administrators can unsubscribe a user by using the Unsubscribe a recipient from Scheduled Search API.
Best Practices for Other Subscribers
- Let all subscribers know about the subscription in advance, including the frequency with which they'll receive emails.
- Because some subscribers might not be regular Identity Security Cloud users, it's important to make the Name and Description values for each subscription clear.
To subscribe to an SoD policy:
- Go to Search.
-
Select the Layers icon to view your SoD policies. Choose the policy you want to subscribe to.
-
Select the envelope icon to begin creating your subscription.
-
Select a time zone for this policy subscription and select Next.
-
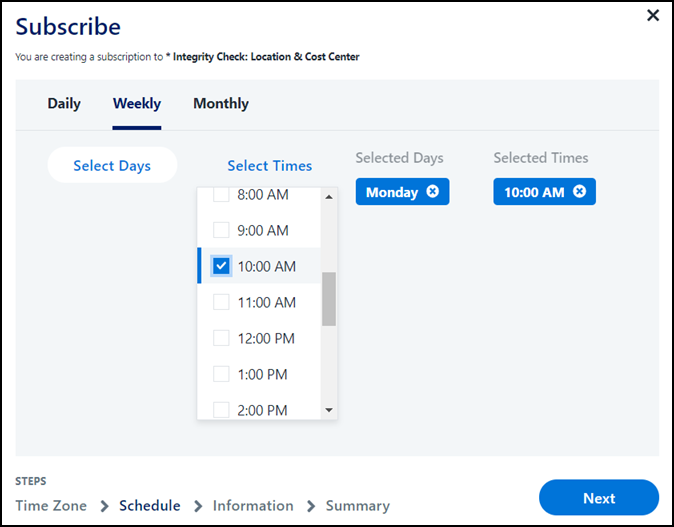
Choose a schedule for your subscription from the following options:
- Daily - Select the times of day subscribers should to receive a violation report each day. The times you select will show up on the right next to the dropdown menu. Select the x next to the time to remove it from the list. Daily is the default option.
- Weekly - Select the days of the week and times you'd like to receive a violation report. The days and times you select will show up on the right next to the dropdown menu. Select the X next to a selection to remove it from the list.
- Monthly - Select the numerical days of the month and times you'd like to receive an email about the subscription using the checkboxes. The days and times you select will show up on the right next to the dropdown menu. Select the X next to the day or time to remove it from the list.
You can use one schedule option at a time. For example, if you start with a weekly schedule but move to monthly, your weekly subscription will end.
Select Next.
-
On the Information page, define the details used to create the email subscription including Name, Description, and Subscribers who'll receive the email subscription.
Note
Typically, users need to be subscribed to an SoD policy if they will manage policy enforcement. An SoD policy's Violation Owner is always added to subscriptions to the policy and can't be removed.
You can also choose to send the report even when there are no violations.
Select Next.
-
On the Summary page, review your subscription. The first 4 lines are about the policy, and the next 4 are about the subscription.
-
Select Subscribe.
Subscribers can receive violation reports at the cadence you selected as long as the policy is enabled.
You can review and make changes to the email users receive. Refer to the SoD Policy Subscription Notification Email Template for more information.
Download a Report of All Policy Violations
- Go to Search.
- Select the Policies icon in the vertical toolbar.
- Choose the Download icon
 to the upper right of the table.
to the upper right of the table.
Policy and Violation Limits
You can have a maximum of 500 policies of any type in your org. In each access-based SoD policy, you can have a maximum of 50 entitlements in each access list.
Reports on policy violations are limited to a specific number of violations. Excessive policy violations could be indicative of a larger data problem or a sign that your policy is incorrectly constructed. Consider correcting those issues before downloading reports of your policy violations.
Preventative Separation of Duties
Preventative SoD helps you find and prevent policy violations before they occur.
Notifications During Access Requests
Access requests are analyzed for SoD policy violations after they are submitted for processing. This compares the requested access with the access the identity already has and notifies requesters and reviewers when a request would put an identity in violation of an SoD policy. Access that has been requested but is not yet provisioned is not included in the preventative SoD evaluation.
Note
This feature is available for access-based SoD policies, not for general policies.
Requester
If a user requests access that would put the recipient in violation of an SoD policy, that request will display a warning icon in their Requests tab once it has been submitted. They can review the policies they would be violating and cancel the request if needed.
Recipient
If the recipient of the access is someone other than the requester, the recipient also sees the request in their Requests tab with a warning icon.
Reviewer
SoD policy checking occurs before an access request is sent to a reviewer for approval. When SoD policy violations are detected, the reviewer sees the warning icon and Review Policy button in the request. This allows them to make an informed decision about whether to approve the access for the user.
Reviewers can see additional information about the policy, including the names of the Policy Owner, the Violation Owner, and the access included in each access list.
Notes
- SoD policies are defined at the entitlement level only. However, if a requested role or access profile includes an entitlement that causes an SoD policy violation with another entitlement for the user, this will be detected and the warning displayed for the request.
- SoD policies are not applied to the contents of a single role or access profile. If a role or access profile includes conflicting entitlements within its access list, a request for that role or access profile will not cause a policy violation to be detected.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.