Managing Entitlements
Entitlements are the access rights an account has on a source. They're a key part of identity governance and an important way of quantifying access. They can be:
- Configured for direct access requests.
- Grouped with related entitlements in access profiles.
- Added directly to roles.
- Reviewed and managed in certifications.
Refer to Loading Entitlement Data for information on collecting entitlement data from sources.
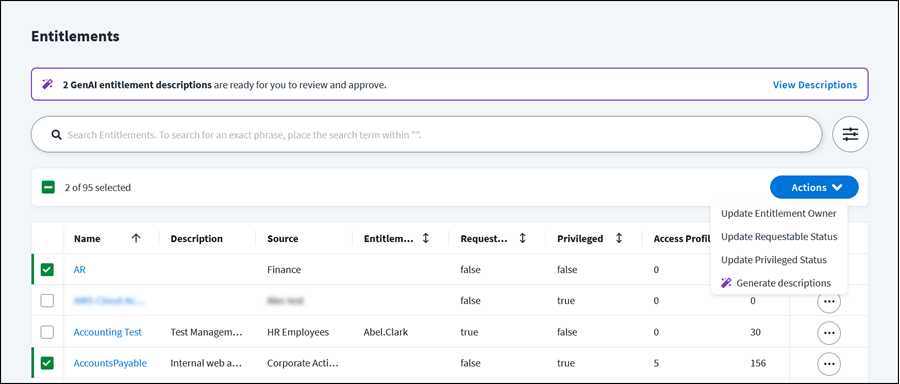
You can work with all of your organization's entitlements in one place on the Entitlements page by going to Admin > Access Model > Entitlements.
You can also work with entitlements on sources.
Viewing Entitlements
Go to Admin > Access Model > Entitlements to see a list of the entitlements in your organization. The table columns include important information for each entitlement such as:
- Source
- Owner
- Whether the entitlement is requestable or privileged
- How many access profiles include the entitlement
- How many identities have the entitlement assigned to them
If your organization has licensed SailPoint Identity Graph, you can select the View in Identity Graph icon to display a visualization of the entitlement's relationships with other access objects.
Use the Search field to look for a specific entitlement or select the Filter icon ![]() to refine the list of entitlements by specific attributes.
to refine the list of entitlements by specific attributes.
You can select an entitlement to view additional details about it, including:
- Cloud Access Details - If your site licenses a SailPoint cloud governance solution, you can view cloud access data related to entitlements on a source with cloud access. You can mark entitlements as Cloud Enabled by creating or editing cloud-enabled entitlement types.
-
Permissions - Permissions represent individual units of read/write/admin access to a system. If you have direct or indirect permissions on your supported sources, they can be aggregated. Direct permissions are aggregated as entitlements, and are displayed on the directPermissions attribute on an account. Indirect permissions appear in the attributes of an entitlement.
You can also view permissions per source. The Permissions column on an account's list of entitlements displays Yes or No to indicate whether the entitlement includes permissions.
Note
You cannot modify a permission within Identity Security Cloud.
-
Type - Some sources support multiple types of entitlements, each with a different attribute schema.
Notes
-
Not all sources support entitlement types or permissions. Refer to the source's connector documentation to find out whether it supports those attributes.
-
Newly created sources of supported types can aggregate entitlement types and permissions automatically. To configure an existing source to support this functionality, update the entitlement schema associated with the source using the Update Source Schema (Partial) API.
-
Depending on the entitlement, the following information may also display on tabs:
-
Access Profiles - Lists the access profiles that include the entitlement.
-
Identities - Lists the identities that have the entitlement assigned and provides the ability to revoke the entitlement for an identity.
-
Roles - Lists the roles that include the entitlement.
- Parent and Child Entitlements - View the parent and child relationships each entitlement has. For more information, refer to Representing Nested Entitlements.
Notes
-
Entitlements generated by a Privileged Task Automation launcher process can take up to an hour to appear in the Entitlements list. Launcher-generated entitlements will have the internal IdentityNow source. Admins can edit and set the owner for these generated entitlements.
-
Entitlements from the internal IdentityNow source cannot be deleted or overwritten on import.
Working with Entitlements
You can manage, edit, and configure access requests for entitlements across sources from the Entitlements page by going to Admin > Access Model > Entitlements.
GenAI Entitlement Descriptions
SailPoint leverages GenAI to generate descriptions for your organization’s entitlements. Admins can select specific entitlements and generate descriptions for them.
Refer to Configuring GenAI Settings for details about customizing this feature for your tenant.
Note
Due to limitations in AWS regional support, GenAI entitlement descriptions are only available for customers in AWS regions where the AWS Bedrock LLM that SailPoint employs is supported.
The following regions are unavailable:
- FedRamp Gov Cloud: us-gov-west-1
- South America (São Paulo): sa-east-1
- Middle East (UAE): me-central-1
Generating Entitlement Descriptions
To generate descriptions:
-
Select entitlements and start description generation in one of the following ways:
- Multiple Entitlements - Select multiple checkboxes for multiple entitlements, and then select Actions > Generate descriptions.
- All Filtered Entitlements - Apply one or more filters, select the Results checkbox, select Select all, and then select Actions > Generate descriptions.
- One Individual Entitlement - Select the Actions icon
 > Generate descriptions for an individual entitlement.
> Generate descriptions for an individual entitlement.
-
Progress is displayed in the Generating Descriptions bar at the top of the GenAI Entitlement Descriptions page.
-
Once completed, newly generated entitlement descriptions are listed.
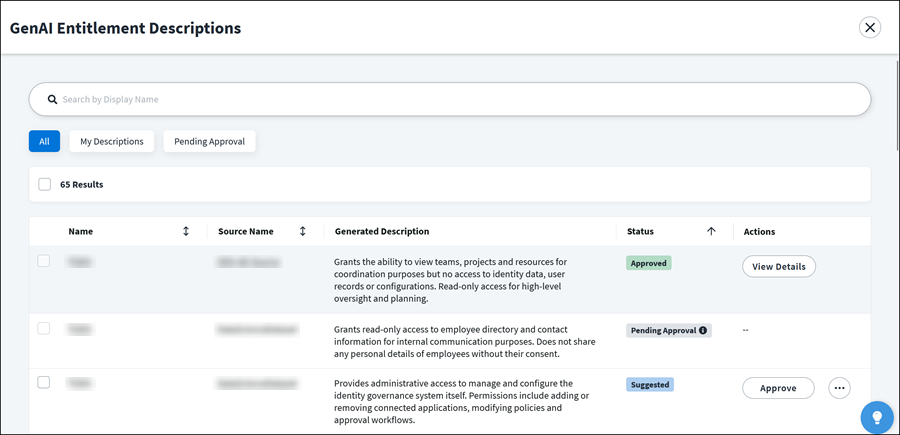
Viewing Generated Entitlement Descriptions
If there are GenAI entitlement descriptions to review and approve, a banner displays at the top of the Entitlements page. Select View Descriptions to view generated descriptions and their status.
To refine the list by source and status, select the Filter icon ![]() .
.
To display approver details for descriptions that are pending approval, select the description's Pending Approval status badge.
Reviewing and Approving GenAI Entitlement Descriptions
A generated entitlement description must be approved before it can be updated in the entitlement. On the GenAI Entitlement Descriptions page, select Approve to update the description. Use the checkboxes to select and approve several at once.
To make changes to the generated description:
-
Select the Actions icon
 > Edit.
> Edit. -
Make edits to the generated description.
-
Select Approve.
If the entitlement description should be approved by someone else in the organization, you can send it to another reviewer as follows:
-
Select the Actions icon
 > Send to Reviewer.
> Send to Reviewer. -
Select an identity or governance group to review and approve the entitlement description.
-
Select Send.
-
The entitlement description shows up in the reviewer’s Approvals page and an email notification lets them know they have been assigned an approval.
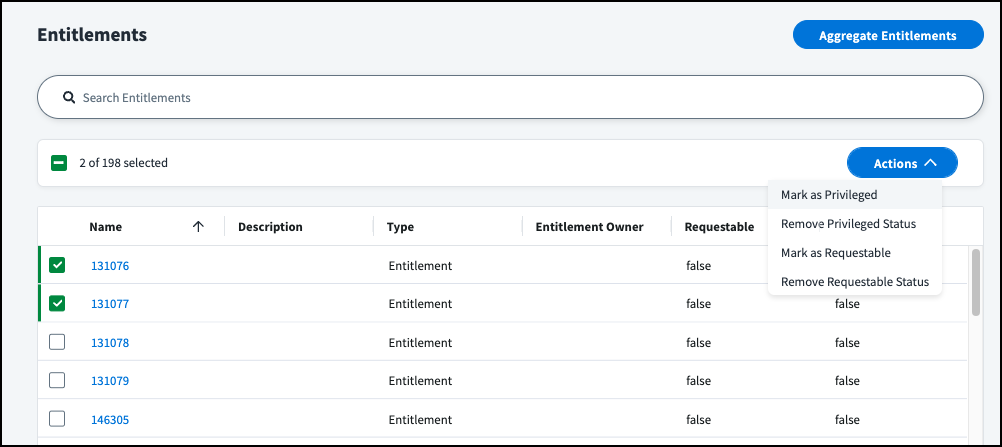
Bulk Entitlement Updates
You can perform the following actions on multiple entitlements at once:
- Update entitlement owner
- Update requestable status
- Update privileged status
- Update metadata attributes
Entitlement updates that do not impact identities and their access can take up to 24 hours to appear in Search results because those updates are added to Search during a nightly synchronization job.
To update multiple entitlements:
-
Go to Admin > Access Model > Entitlements.
-
Select the checkboxes for the entitlements you want to update. Once you select more than one entitlement, the Actions button appears.
-
Select the Actions button.
-
From the dropdown list, select the update you want to make for the selected entitlements.
Refer to Updating a Metadata Attribute for Multiple Entitlements for details on the Update Metadata Attributes option.
-
Make your updates in the Update panel, and select Update.
Updating a Metadata Attribute for Multiple Entitlements
Metadata attributes are used to assign additional information to entitlements, so that entitlements with similar purposes can be easily associated with each other. There are additional steps to edit a metadata attribute on multiple entitlements.
To update a metadata attribute on entitlements in bulk:
-
Select the checkboxes for the entitlements you want to update or select the Results checkbox then Select all to update all entitlements.
-
Select Actions > Update Metadata Attributes.
-
In the Metadata Attribute field, choose the metadata attribute you want to update.
-
In the Operation field, choose the type of action you want to take on this metadata attribute for the selected entitlements.
-
If applicable, enter a value for the attribute in the Values field.
-
Select Update.
You can also update the metadata attributes on an individual entitlement.
Individual Entitlement Updates
You can perform the following actions on individual entitlements:
- Edit entitlement details
- Update entitlement status
- Add and update metadata attributes on an entitlement
- Revoke an entitlement from an identity
Entitlement updates that do not impact identities and their access can take up to 24 hours to appear in Search results because those updates are added to Search during a nightly synchronization job.
Editing Entitlement Details
To edit details for an entitlement:
-
Go to Admin > Access Model > Entitlements and find the entitlement you want to update.
Tip
To search for a specific entitlement, place the search term in
"". -
Select the Actions icon
 > Edit for the entitlement.
> Edit for the entitlement. -
In the Configuration panel, update the entitlement’s display name, description, or owner. Select Save to save your changes.
Best Practice
Ensure the entitlement’s display name and description are easy to understand as the entitlement may appear in access requests and certifications. This will improve the accuracy, quality, and speed of requests and review decisions.
Notes
- Changes to the display name and description are not sent to the source.
- You can also assign an entitlement owner by submitting an API call with the Patch an entitlement endpoint.
-
In the Access Request panel, set your access request configurations and select Save to save your changes.
Your changes will take effect immediately but may take a moment to display on the Entitlement Management page.
Updating Entitlement Status
To update the privileged or requestable status for an entitlement:
- Select the Actions icon
 for the entitlement you want to update.
for the entitlement you want to update. - Select the status update you want to make from the dropdown menu.
Your changes will take effect immediately but may take a moment to display on the Entitlement Management page.
Updating Metadata Attributes on Individual Entitlements
To add metadata attributes to an individual entitlement:
-
Go to Admin > Access Model > Entitlements.
-
Select the entitlement you want to edit.
-
Under Governance Metadata, select Edit.
-
Select Metadata Attributes.
-
Select Add Attributes.
-
Enter a value in the fields for any metadata attributes you want to configure for this entitlement.
-
Select Save.
The metadata attributes that were given values on this page are added to this entitlement.
To edit metadata attributes on an entitlement:
-
Go to the Metadata Attributes page on the entitlement you want to edit using the steps for adding a metadata attribute.
-
Select the checkboxes beside the metadata attributes you want to edit.
-
Select Actions > Update Metadata Attributes to update multiple attributes at once.
You can also select an entitlement's name or the Actions icon
 to edit an entitlement's metadata attribute values individually.
to edit an entitlement's metadata attribute values individually.Select Clear Attribute Value on the edit screen to remove all values for an attribute from the entitlement.
Revoking Entitlements
Admins and Access Revokers can submit requests to revoke an identity's entitlements.
- On the Admin > Access Model > Entitlements page, select the entitlement you want to revoke.
- On the Entitlement Details page, select the Identities tab.
- Locate the identity you want to remove the entitlement from and select View Assignments.
- On the Assignment page, you can select the option to Revoke Assignment. If a user has more than one assignment, verify the account target details first to make sure you revoke the access you intend to.
- In the Request Revocation dialog, enter comments.
- Select Revoke.
- A success message confirms that your revocation request was submitted.
Adding or Editing an Access End Date
You can change the end date for an access assignment.
- On the Admin > Identity Management > Identities page, select an identity.
- Select Access from the left navigation, then select an access item.
- Go to the Assignment page and select Add or Edit in the end date field.
-
In the End Date and Time field, select a date.
Note
The End Date and Time field is required for access items with a maximum duration. Maximum duration is calculated by adding the last possible new end date to the current date, even when the current end date (before edits) is beyond the maximum duration. When you change an end date, the new date needs to be within the allowed duration.
-
If required, add comments.
- Select Save.
When you edit an end date to extend access time, the request goes through the Add Access approval process. If you edit an end date to remove access early, the request goes through the Remove Access approval process, which may be configured to not require approval. Refer to Configuring Access Requests for more information on the approval process. When requests to modify access end dates are shown to approvers, they are clearly labeled so approvers understand what they are being asked to review.
Viewing Entitlements with Critical Data
If your organization has SailPoint Data Access Security, you can view the classifications, policies, and data categories for the critical data that an entitlement grants access to.
- Go to Admin > Access Model > Entitlements.
- Find an entitlement with the critical data access flag
 .
. - Select Actions
 > View Details.
> View Details. - Select the Data Access tab to view the data’s classifications, policies, and categories.
For more information about critical data, refer to the Data Access Security documentation.
Working with Entitlements on Sources
Some information about entitlements can be modified on its source. This includes marking entitlements as privileged or requestable and updating multiple attributes like display names and descriptions at once.
Marking Privileged Entitlements on a Source
You can mark an entitlement as privileged to draw attention to it during certification campaigns. This flag appears everywhere the entitlement is displayed, including search and certifications.
To mark entitlements as privileged:
- Go to Admin > Connections > Sources.
- Select or edit the source that contains the entitlements you want to edit.
- In the Entitlement Management section, select Entitlements.
- Select the checkbox next to the entitlements you want to mark as privileged.
-
Select the Actions dropdown list and choose Mark as Privileged.
Performing Bulk Entitlement Updates on a Source
Entitlement aggregation can read display names and descriptions from the source. If these are missing or insufficient, you can change those values through a manual bulk edit.
- Go to Admin > Connections > Sources.
- Select or edit the source you want to update.
- In the Entitlement Management section, select Entitlements.
- Select
 to download a comma separated values (.csv) list of the entitlements.
to download a comma separated values (.csv) list of the entitlements. - Edit the file to fix any incorrect or incomplete entitlement data.
- Select
 to upload your changes.
to upload your changes.
Notes
- Subsequent aggregations can replace blank display names or descriptions but will not overwrite existing values. This ensures your manual edits do not get overwritten.
- Entitlement descriptions can be up to 2000 characters. An error will occur if you attempt to upload a file containing descriptions that exceed that limit.
Representing Nested Entitlements
Hierarchical relationships between entitlements for source types are supported where it applies. To configure parent and child relationships between entitlements in a .csv file, use the hierarchyAttribute of the Update Source Schema API.
Ways to Revoke Entitlements
You can revoke entitlements in the following ways:
- Using the Entitlements page
- Creating certifications
- Configuring a lifecycle state to remove all access.
- Submitting an API call with the Submit Access Request endpoint
Note
You can only submit revoke requests for one entitlement at a time through the Submit Access Request endpoint.
Deleting Entitlements
Entitlements can't be deleted directly in Identity Security Cloud. To remove an entitlement, delete it from the source itself and run an entitlement aggregation.
Account aggregations never delete entitlements from Identity Security Cloud, including source entitlements created solely through account aggregation. This is because an entitlement could still exist even if no accounts currently hold it.
Troubleshooting Entitlement Issues
The following list describes common entitlement issues their solutions:
Entitlement names and descriptions are not aggregating from the source system.
Perform an entitlement aggregation for your source to pull in the display names and descriptions for all entitlements.
This will only replace values that have not been updated manually in Identity Security Cloud. This is to protect and preserve any updates you make through the Entitlement Administration page, the API, or by using the .csv download/upload option. Once a value has been updated manually, an aggregation will not replace it.
If the aggregation doesn't update the entitlement description, the following may have occurred:
-
The entitlement description may have been manually updated in Identity Security Cloud. You can check whether the description has been manually updated by using the Get an entitlement endpoint. The
manually_updated_fieldsproperty should be marked as false, meaning this property has not been manually updated since the first aggregation or on subsequent aggregations. You can override the value for this property through the Patch an entitlement endpoint. -
The description isn't mapped correctly in the source schema. To view your current mapping, submit an API call using Lists Schemas on Source. If the mapping is incorrect, you can submit an API call using the Update Source Schema (Partial) endpoint to alter the group schema’s description attribute.
Caution
This endpoint allows you to change your schema definitions, which can change the data SailPoint stores for the source’s accounts and entitlements.
The wrong attribute has been used as the entitlement's display name.
Your entitlement schema defines which attribute is used as the display name. Use the Update Source Schema API to modify the display attribute designation.
If the entitlement schema for the source is editable in the user interface, you can also change it there:
- Go to Admin > Connections > Sources.
- Select or edit the source with the display name you want to change.
- In the Entitlement Management section, select Entitlement Types and Schemas.
- Select the entitlement type you want to edit.
- Change the attribute designated as the Entitlement Name to the desired display attribute.
- Run an entitlement aggregation.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.