Configuring Okta for SailPoint CIEM
You can use Okta with SailPoint CIEM to identify cloud access by roles federated with an identity provider. CIEM supports direct AWS role assignments on Okta user-scoped/group-scoped account management in addition to the existing regex-based group role mapping. You can have multiple instances of the Okta app with different names.
To configure Okta to work with SailPoint CIEM, you must:
- Configure the AWS Account Federation app in Okta.
- Create an application token.
- Find and save your application ID.
Note
Identity Security Cloud does not support AWS roles as supported entitlements with Okta user-scoped account management.
Finding Your Application ID
To find an application ID of the Okta instance you want to onboard:
-
Log in to Okta and go to the admin portal.
-
Select Applications.
-
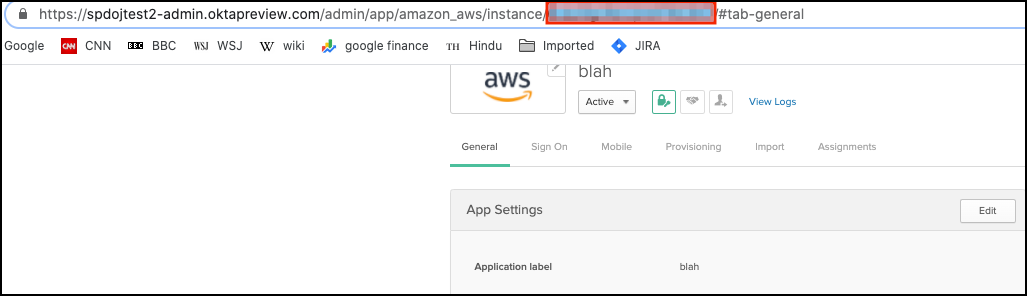
Search for the name of the AWS instance you want to onboard and select it.
-
Once you have selected the application, copy and save the application ID embedded in the URL.
-
Repeat this process for the instances you want to include. You'll enter these in the Application ID field when you connect Okta and SailPoint CIEM.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.