Connecting GCP and CIEM
Once you have configured your GCP account, you can connect it to CIEM using a SaaS connector or VA-based connector:
Choose your next step based on your configuration
When you have completed the steps for your connection type, you can aggregate and mark the entitlement types that grant cloud access. You can then view the effective access those entitlements grant on aggregated Google Cloud Platform resources and include cloud entitlements in certification campaigns.
Using the Google Workspace SaaS Connector
If you are using Google Workspace SaaS, follow the SailPoint Connector guide to enable SailPoint CIEM.
Important
In the Connection Settings, select Service Account from the Grant Type dropdown list. CIEM does not support the Client Credential grant type.
After a successful test connection, you can optionally set the source scope before aggregating accounts and marking the entitlement types that grant cloud access.
Note
If you have previously configured both the Google Workspace SaaS and SailPoint CIEM GCP connectors, you do not need to take additional action to continue receiving your data.
Setting Source Scope for SaaS-Based Connections
By default, SailPoint CIEM reads and automatically discovers changes to your cloud infrastructure. You can choose to exclude scopes to prevent SailPoint CIEM from including data for those accounts.
When you exclude scopes, SailPoint CIEM will only read and include data from selected scopes. When Auto-Include Scopes is disabled, new and deleted folders and projects in your cloud system will be detected, but SailPoint CIEM will not automatically include data from new scopes until you select the folders and projects individually or reenable Auto-Include Scopes.
Scope Limits
There are limits to the number of scopes you can select based on whether you are gathering inventory data to view effective access, activity data to view last access, or both. To gather both inventory and activity data, you must adhere to the smaller of the two limits.
- Inventory Data (Effective Access) - 30,000 projects
- Activity Data (Last Access) - 5,300 projects
- Both - 5,300 projects
To change the scope of your included source data when using a SaaS-based connector:
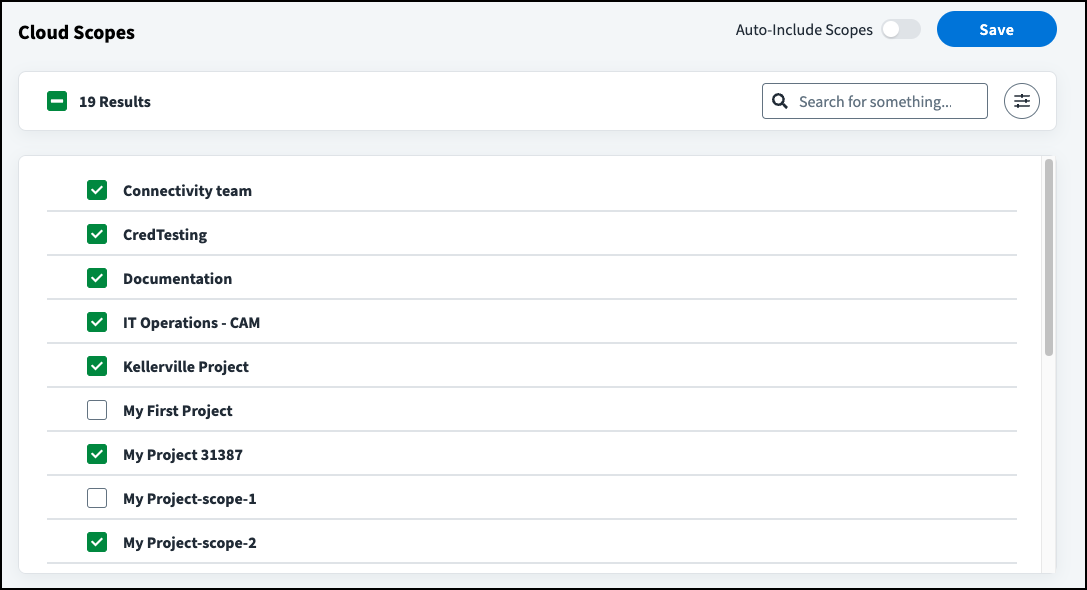
- In the Google Workspace SaaS source, select Cloud Scopes under Additional Settings.
-
Select which cloud scopes to include:
- To automatically include data from all projects, enable Auto-Include Scopes. Deselecting a scope disables Auto-Include Scopes.
- To include a subset of projects, use the checkboxes to change which scopes are included.
-
Select Save.
Notes
- You can search for scopes as well as filter by excluded scopes and scopes with errors.
- The Discovered by CIEM column displays when changes to your source inventory were last detected by SailPoint CIEM. This is separate from aggregation.
You will next aggregate accounts and mark the entitlement types that grant cloud access.
Using the Google Workspace VA-Based Connector
If you are onboarding SailPoint CIEM using a VA-based connector instead of SaaS, you must configure both the Google Workspace VA-based connector and the SailPoint CIEM GCP connector.
| Google Workspace (formerly G Suite) VA-based connector | Allows you to manage your GCP accounts, groups, and roles in Identity Security Cloud on virtual appliances. If your organization has licensed a SailPoint cloud management solution, it will also gather data on the cloud resources users are granted through your GCP organization, projects, accounts, and role assignments. |
| SailPoint CIEM GCP connector | Works with the Google Workspace VA-based connector to collect cloud resource data and display the total access an identity has on aggregated resources from your GCP cloud systems. |
You may connect your Google Workspace VA-based and SailPoint CIEM GCP sources in any order.
Connecting the Google Workspace VA-Based Connector
- Follow the SailPoint Connector guide to configure or edit the Google Workspace connector.
- Select Connection Settings.
- In Cloud Resources Management Settings, enable Manage Cloud Resources.
You must then use the SailPoint CIEM GCP connector to display all access users have to your cloud resources.
Connecting SailPoint CIEM GCP
The SailPoint CIEM GCP source pulls data daily about the cloud resources your GCP IaaS users can access.
To register SailPoint CIEM GCP:
- Go to Admin > Connections > Sources > Create New.
- Find the CIEM GCP source type and select Configure.
- Enter a source name.
- Enter a description for your source.
- In the Source Owner field, begin typing the name of an owner. Matches appear after you type two letters.
- (Optional) Select a governance group for source management.
- Select Save.
-
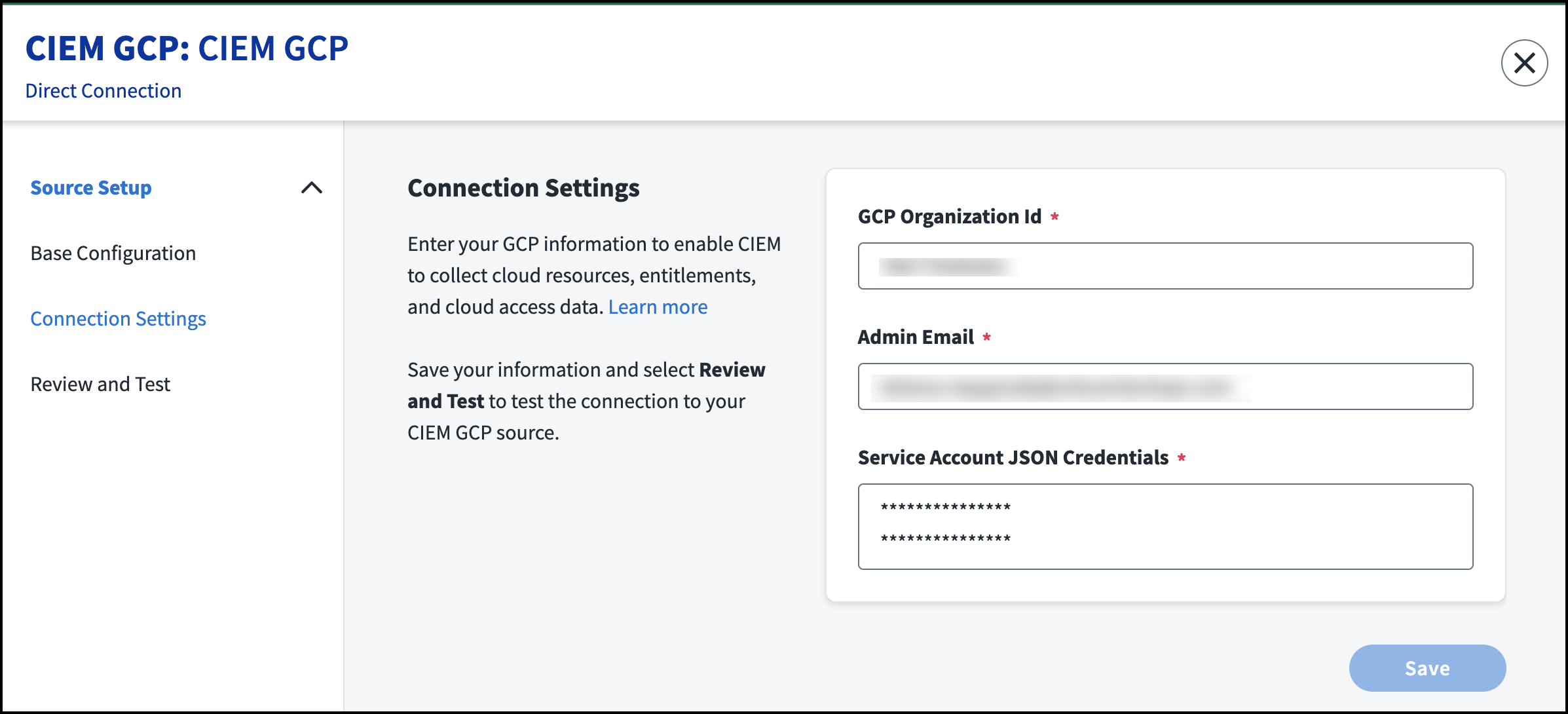
Select Connection Settings in the left panel.
-
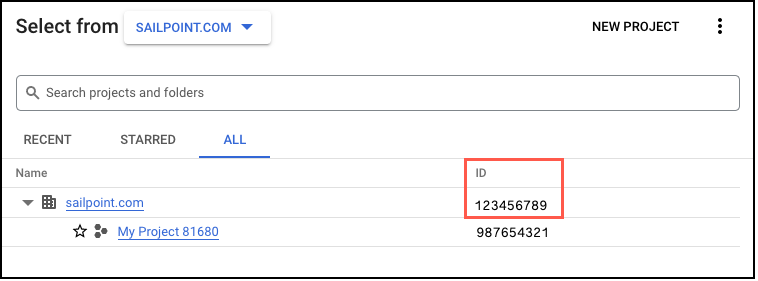
In the GCP Organization ID field, enter the 10-digit organization ID. You can find this in the Google Cloud Platform console by selecting the dropdown list with your project or organization name. Select the All tab and copy the organization ID.
-
Enter an email with admin access to the Google Admin Console.
Note
The domain must be the same as the organization name. For example, if the organization name is "testorg.com", then the admin email will need to be formatted like "smith@testorg.com".
-
Paste the JSON you received when creating the key for the service account.
- Select Save.
- Select Review and Test.
-
Review the configuration details and select Test Connection. A successful test is required for SailPoint CIEM to gather data for this source.
After a successful test connection, you can set the source scope or move on to marking the entitlement types that grant cloud access.
Setting Source Scope for VA-Based Connections
By default, SailPoint CIEM reads and automatically discovers changes to your cloud infrastructure. If you are using a VA, you can choose to exclude scopes to prevent SailPoint CIEM from including data for those accounts.
When you exclude scopes, SailPoint CIEM will only read and include data from selected scopes. When Auto-Include Scopes is disabled, new and deleted folders and projects in your cloud system will be detected, but they will not be automatically included in your SailPoint CIEM data until you select them individually or reenable Auto-Include Scopes.
Scope Limits
There are limits to the number of scopes you can select based on whether you are gathering inventory data to view effective access, activity data to view last access, or both. To gather both inventory and activity data, you must adhere to the smaller of the two limits.
- Inventory Data (Effective Access) - 30,000 projects
- Activity Data (Last Access) - 5,300 projects
- Both - 5,300 projects
To change the scope of your included source data when using a VA-based connector:
- In the CIEM GCP source, select Cloud Scopes under Additional Settings.
-
Select which cloud scopes to include:
- To automatically include data from all projects, enable Auto-Include Scopes. Deselecting a scope disables Auto-Include Scopes.
- To include a subset of projects, use the checkboxes to change which scopes are included.
-
Select Save.
Notes
- You can search for scopes as well as filter by excluded scopes and scopes with errors.
- The Discovered by CIEM column displays when changes to your source inventory were last detected by SailPoint CIEM. This is separate from aggregation.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.