Connecting AWS and SailPoint CIEM
Once you have configured your Amazon Web Services (AWS) account, you will enter that configuration information in Identity Security Cloud to enable SailPoint CIEM to display the effective access users have on collected AWS cloud resources.
Depending on your implementation, you will use one or more connectors to allow SailPoint to connect to your AWS data.
After you've connected and aggregated your cloud accounts and entitlements, you will mark your IAM and/or AWS Identity Center entitlements as cloud enabled. This will allow you to view the cloud access granted through entitlements and include those entitlements in certification campaigns.
Select your implementation type:
Implementation Options
You can use SailPoint CIEM and Identity Security Cloud to AWS to manage your IAM and Identity Center users.
| Implementation Option | AWS Connector | CIEM AWS Connector |
|---|---|---|
| Govern both IAM and Identity Center users | Select a connector to govern IAM users: - SaaS-based connector (recommended) - VA-based connector |
Connect CIEM AWS to manage Identity Center users. |
| Govern IAM users without Identity Center | Select a connector to govern IAM users: - SaaS-based connector (recommended) - VA-based connector (requires CIEM AWS connector as well) |
If you use a VA-based connection, you must also connect CIEM AWS. |
| Manage Identity Center users only | N/A | Connect CIEM AWS |
Important
You cannot enable CIEM in the AWS SaaS connector if you are also using the CIEM connector for the same management account. The CIEM connector will still collect data for AWS SaaS accounts and entitlements as long as they are marked as cloud enabled.
You may connect your AWS and CIEM AWS sources in any order.
Governing Both IAM and Identity Center Users
To use Identity Security Cloud and SailPoint CIEM to govern both your AWS IAM and Identity Center identities, you must configure two connectors.
-
Select a SaaS or VA-based connector to govern IAM users:
-
Connect CIEM AWS to include Identity Center accounts.
- (Optional) Set source scope for SailPoint CIEM.
- (Optional) Edit the regions CIEM collects data from.
-
Mark the entitlements (required).
- Aggregate the SaaS or VA-based IAM source you configured in step 1.
- Aggregate the CIEM AWS source you configured in step 2.
Governing IAM Users Without Identity Center
If you are not using AWS Identity Center, you can govern IAM users using one or more connectors, depending on your connection type.
-
Configure the SaaS or VA-based connector to govern IAM users:
-
SaaS-based connector (recommended)
- (Optional) Set source scope for IAM accounts.
-
VA-based connector (requires CIEM AWS connector as well)
-
-
If you selected the VA-based connector, configure the CIEM AWS connector as well.
- (Optional) Edit the regions CIEM collects data from.
- (Optional) Set the scopes for cloud data collected by the CIEM AWS connector.
-
Mark the entitlements (required).
- Aggregate the SaaS or VA-based IAM source you configured in step 1.
- If you chose the VA-based connector, aggregate the CIEM AWS source you configured in step 2.
Using AWS Identity Center Without IAM
If you are using SailPoint CIEM for Identity Center management, and not IAM user management, you only need to configure the CIEM AWS connector.
-
Configure the CIEM AWS connector.
-
Mark the entitlements (required).
- Aggregate the CIEM AWS connector.
Connector Options
Depending on your implementation, you might need to provide your AWS configuration information in one or more connectors for Identity Security Cloud.
| AWS connector | Allows you to manage your AWS IAM users and groups in Identity Security Cloud. If your organization has licensed a SailPoint cloud management solution, it will also gather data about the cloud access granted to users through policies, roles, organization unit, and AWS accounts. You can use the SaaS-based (recommended) or VA-based AWS connector. |
| SailPoint CIEM AWS connector | Works with your AWS connector to collect cloud resource data and display the total access an identity has to your cloud systems. This connector is required to manage your Identity Center users and groups. |
Using the SailPoint CIEM AWS Connector
The SailPoint CIEM AWS source pulls daily data about the cloud resources users can access. Users can be IAM, AWS Identity Center, Entra IDP, or Okta IDP. Depending on your implementation, you might also need the AWS connector.
Note
The CIEM AWS connector supports organization instances of Identity Center. Account instances are not supported. Refer to Organization and account instances of IAM Identity Center for more information.
You can use the information from verifying your configuration to register SailPoint CIEM:
- Go to Admin > Connections > Sources > Create New.
- Find the CIEM AWS source type and select Configure.
- Enter a source name.
- Enter a description for your source.
- In the Source Owner field, begin typing the name of an owner. Matches appear after you type two letters.
- (Optional) Select a governance group for source management.
- Select Connection Settings.
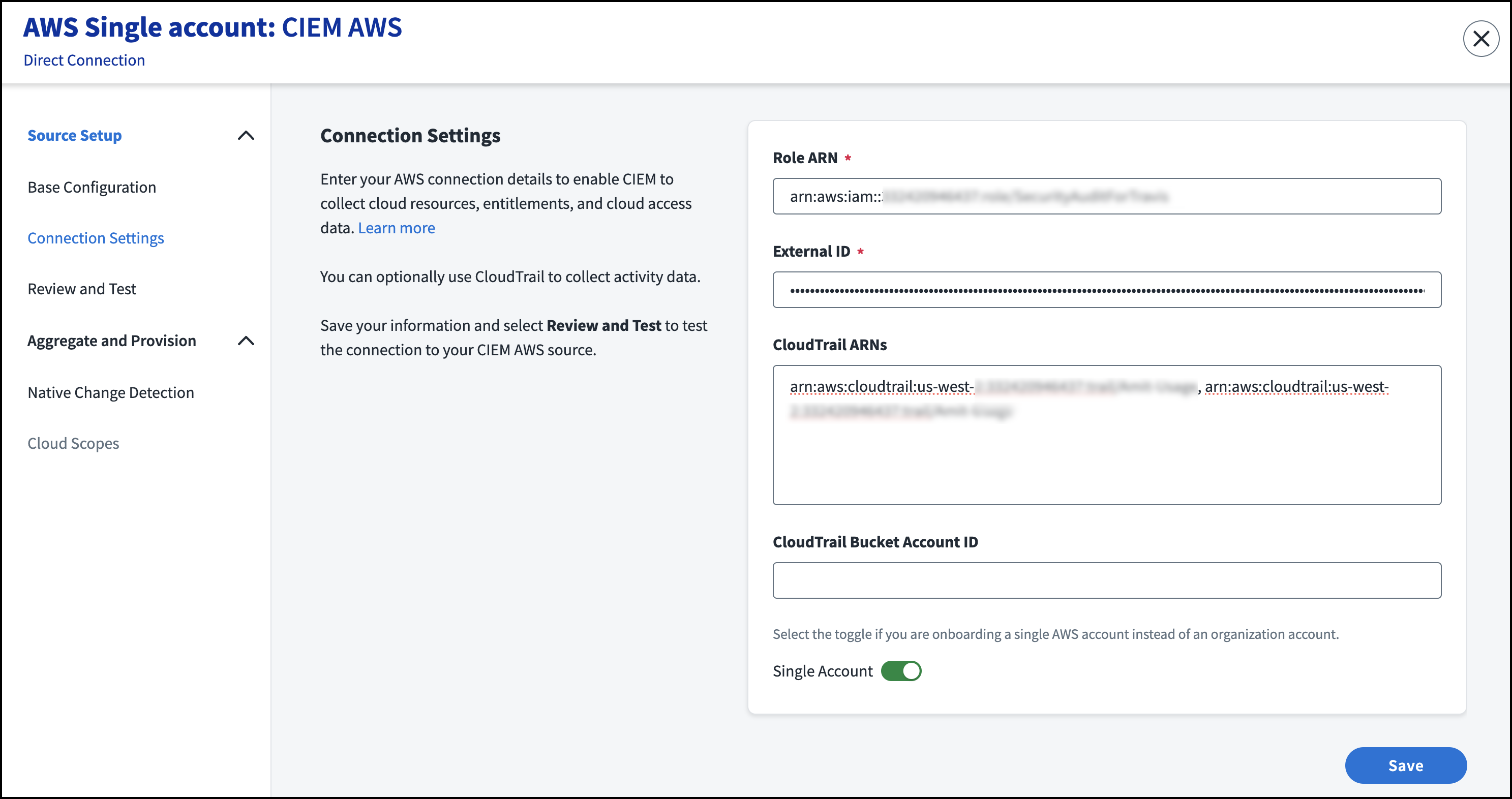
- Enter the Role ARN for the role generated when creating an IAM role. If you are using AWS Organizations, the role ARN should correspond to the management account’s role ARN.
- The External ID field is autopopulated. You will copy the external ID to use when configuring AWS.
-
(Optional) Enter the CloudTrail ARN for an organization or individual member account. You can add up to 150 CloudTrail ARNs, separated by commas.
- Enter the AWS Account ID where the CloudTrail bucket is hosted.
-
If the source uses a single account (as opposed to the organization account) select the Single Account toggle.
Note
Identity Center accounts cannot be aggregated using a single account. To aggregate identity center users, ensure Single Account is not selected.
-
If you are using the Identity Center directory as your identity source, as opposed to Active Directory or another external IdP, select the Provision Identity Center toggle to enable provisioning of Identity Center accounts.
Important
- It is not recommended to enable both Single Account and Provision Identity Center because identity center accounts won't be aggregated or have entitlements provisioned.
- Due to limitations with the IdentityStore API, password provisioning and enabling and disabling accounts are not supported.
Required Provisioning String
To use Identity Store provisioning, ensure the CIEM AWS connector has the
PROVISIONINGfeature string. You can check if provisioning is enabled using the Developer Tools or GET the source's endpoint to find:If it is not enabled, you can use the update-source API to set and validate this using the following payload:
-
Select Save.
- Select Review and Test.
-
Review the configuration details and select Test Connection. A successful test is required for SailPoint CIEM to gather data for this source.
Notes
-
CloudTrail ARNs are tested asynchronously. If a CloudTrail cannot be connected, an error will display in the event logs.
-
If the test connection fails, you can use the Search query
name:“Test_connection Source Failed”for more information.
-
-
(Optional) Enable native change detection. You can monitor your AWS Identity Center Groups and AccountPermissionSet entitlement attributes for changes made outside of Identity Security Cloud, as well as non-entitlement attributes.
- Select Save.
After a successful test connection, you can optionally edit which regions CIEM collects data from or change the source scope. When you complete your configurations, you will aggregate and mark the entitlements.
Choose your next step based on your implementation
- Edit which regions CIEM collects data from (optional)
- Set source scope (optional)
- Aggregate and mark the entitlements (required)
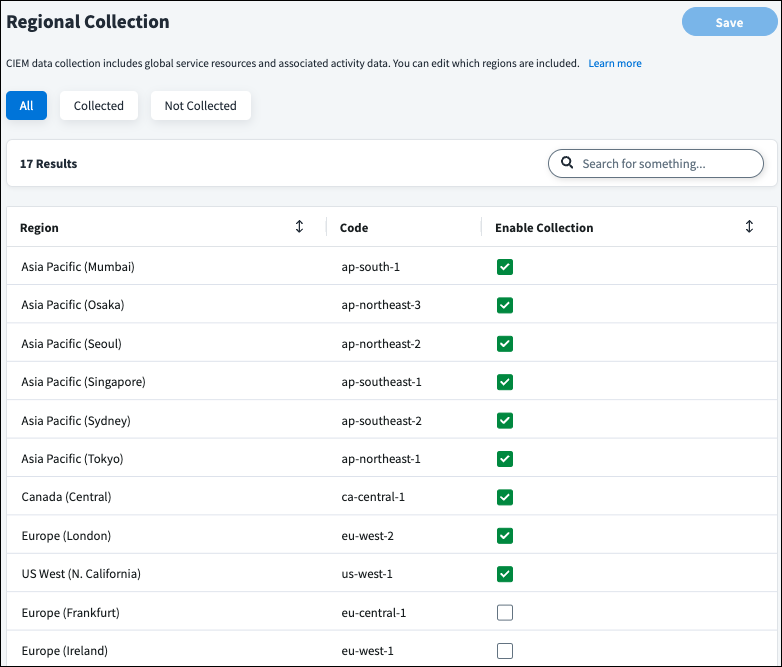
Configuring Regional Collection
CIEM data collection includes global service resources and associated activity data. You can edit which AWS regions are included.
Note
Regional collection is not available for the SailPoint VA-based connector.
-
In the CIEM AWS or AWS SaaS source, select Regional Collection under Additional Settings.
Important
The regional collection on the AWS SaaS source only controls SailPoint CIEM and not the regular IAM account and entitlement aggregation.
-
Use the checkboxes in the Enable Collection column to choose which regions CIEM collects data from.
-
Select Save.
Setting Source Scope
By default, SailPoint CIEM reads and automatically discovers changes to your cloud infrastructure. You can choose to exclude scopes to prevent SailPoint CIEM from including data for those accounts.
Based on your implementation, you can choose to edit the scope of IAM accounts gathered by the AWS SaaS connector and/or the scope of the cloud data gathered by SailPoint CIEM in the CIEM AWS connector.
Notes
- You can search for scopes as well as filter by selected and unselected scopes.
- The Last Refreshed time is when changes to your source inventory were last detected by SailPoint CIEM. This is separate from aggregation.
Scope Limits
There are limits to the number of scopes you can select based on whether you are gathering inventory data to view effective access, activity data to view last access, or both. To gather both inventory and activity data, you must adhere to the smaller of the two limits.
- Inventory Data (Effective Access) - 9,000 accounts
- Activity Data (Last Access) - 3,000 accounts
- Both - 3,000 accounts
Setting Source Scope in the AWS SaaS Connector
Selecting the source scope in the AWS SaaS source controls the data that is gathered for IAM management.
If you are using SailPoint to govern both IAM users and Identity Center users, you can choose to set cloud scopes in the AWS SaaS connector to govern IAM accounts and configure the scopes of cloud data gathered by the CIEM AWS connector, including Identity Center accounts.
To change the scope of your included source data in the AWS Source, refer to AWS Account Settings.
Setting Source Scope in the CIEM AWS Connector
You can change the scope for cloud data gathered by the CIEM AWS connector. This is separate from the cloud scopes for IAM users in the AWS SaaS source.
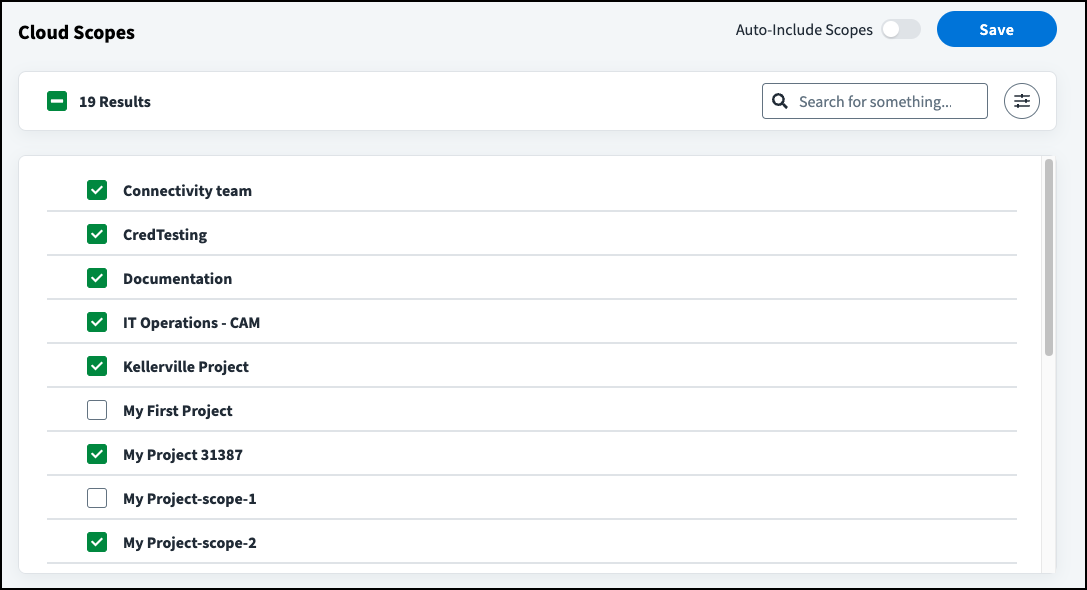
- In the CIEM AWS source, select Cloud Scopes under Additional Settings.
-
Select which cloud scopes to include:
- To automatically include data from all cloud accounts, enable Auto-Include Scopes. Deselecting a scope disables Auto-Include Scopes.
- To include a subset of accounts, use the checkboxes to change which scopes are included.
-
Select Save.
SailPoint CIEM will now only read and include cloud data from your selected scopes. When Auto-Include Scopes is disabled, new and deleted accounts in your cloud system will be detected, but SailPoint CIEM will not automatically include data from new scopes until you select the accounts individually or reenable Auto-Include Scopes.
Notes
- You can search for scopes as well as filter by excluded scopes and scopes with errors.
- The Discovered by CIEM column displays when changes to your source inventory were last detected by SailPoint CIEM. This is separate from aggregation.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.