Search Overview
Search allows you to find information about almost anything in your site. For example, you can find:
- Users who have something in common, such as privileged access, or accounts on a particular source.
- Users with specific access, such as two related entitlements.
- Details about user access, such as all access profiles a specific user has.
Note
Identity Security Cloud is SailPoint’s next-generation identity security solution. It encompasses and builds on features and functions from IdentityNow. The product documentation covers both Identity Security Cloud and IdentityNow features.
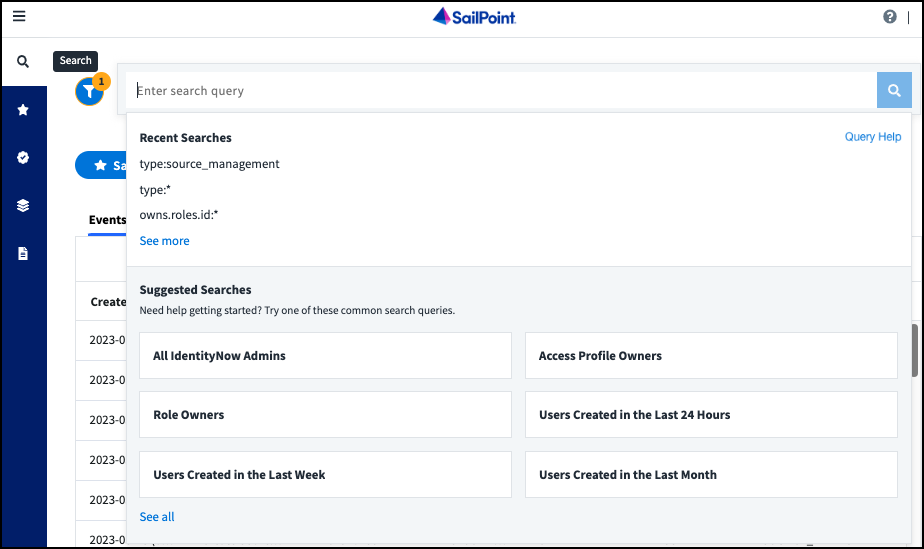
To start searching your data, select Search. Selecting the search bar displays recent and suggested searches. As you enter a query, a list of fields displays.
In addition to finding information about your environment, you can also use Search to:
- View and subscribe to saved search queries
- View, schedule, and manage certification campaigns
- Manage policies
- View and download audit reports
Select the Filter icon ![]() to filter your results by Identities, Entitlements, Events, and other Search categories. You can use the Column Chooser icon
to filter your results by Identities, Entitlements, Events, and other Search categories. You can use the Column Chooser icon  to refine your view.
to refine your view.
Using Natural Language Search to Start Queries
You can enable natural language search to use AI to help you form search queries using natural language.
Due to limitations in AWS regional support, natural language queries are only available for customers in AWS regions where the AWS Bedrock LLM that SailPoint employs is supported.
The following regions are unavailable:
- FedRamp Gov Cloud: us-gov-west-1
- South America (São Paulo): sa-east-1
- Middle East (UAE): me-central-1
Important
Natural language queries are experimental and can make mistakes. Always review the queries it provides.
Natural language queries are only supported in English.
To enable natural language queries:
-
Go to Admin > Global > System Settings.
-
Select Feature Settings.
-
Under Feature Settings, select GenAI, and select the checkbox next to Enable Natural Language Search.
-
Review the AI terms.
-
Select Enable Natural Language Search.
-
Select Save.
-
Select Search.
-
In the search bar, select AI.
-
Enter your search using natural language.
Search will generate a query based on the text you entered. Always verify the fields and construction of search queries generated by an AI tool.
You can change back to using SailPoint's domain-specific query language by selecting Query in the search bar. The query generated by your natural language entry will be added to the search bar, where it can be modified.
Natural language queries can be used alongside other search features, such as saved searches and separation of duties policies. The generated query will be saved as part of the saved search or policy.
Using Harbor Pilot to Start Queries
If your organization has licensed Harbor Pilot ![]() , you can use it to begin creating search queries.
, you can use it to begin creating search queries.
Be sure to verify the fields and construction of each search query.
Important
Harbor Pilot is experimental and can make mistakes. Always review the queries it provides.
Refer to Tips for Crafting Effective Prompts.
Tagging Items in Search
Tagging items that can be searched helps you retrieve them more easily. For example, you can tag highly privileged roles, access profiles, and entitlements to make them easier to find and track. You can also tag items related to PCI or SOX compliance to simplify certification creation and management.
You can tag the following searchable items:
- Access Profiles
- Entitlements
- Identities
- Roles
You can have up to 500 different tags in your site. A tag association is a pairing of 1 tag with 1 object, and you can apply up to 10,000 tag associations. Thus, an object with 500 tags consumes 500 tag associations.
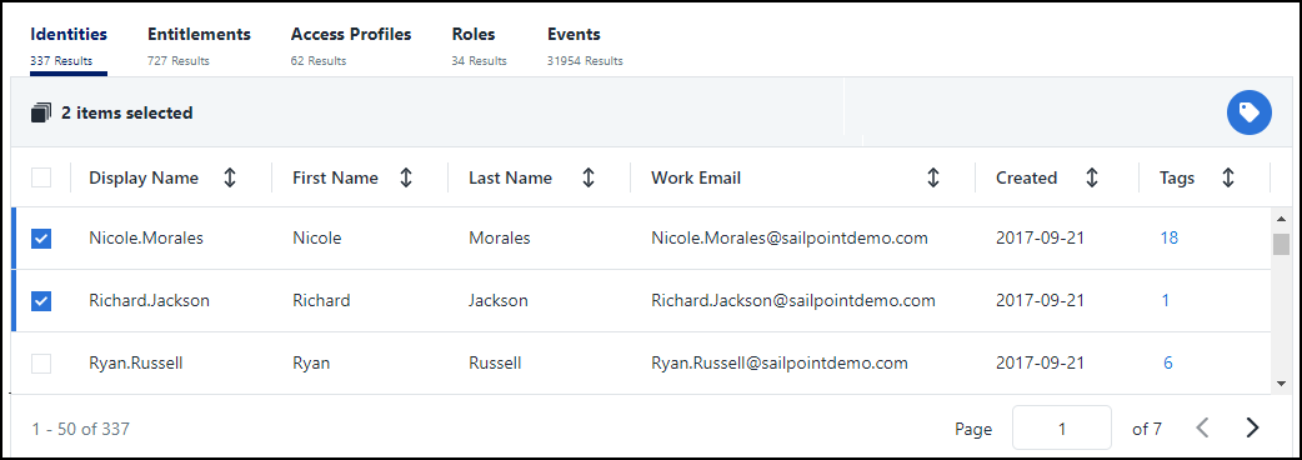
To apply tags to searchable items:
-
Go to Search.
-
Write a search query to return the items you want to tag.
-
Select the checkboxes next to the items you want to tag and select the Tags icon
 .
.You can also open the Tags overlay for a single item by selecting the number of tags in its Tags column.
-
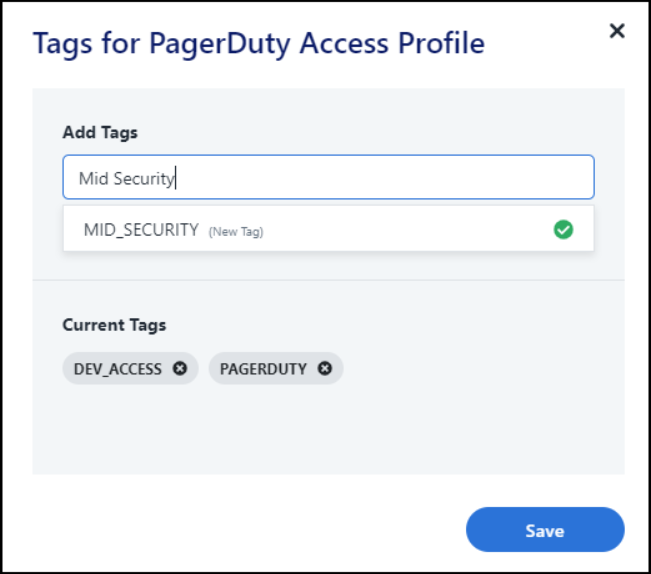
Add your tags one at a time in the Add Tags field, pressing Enter or return between each tag.
Note
Tags must be between 3 and 128 characters. Valid characters include A-Z, 0-9, and underscores
_. Tags are automatically converted to uppercase, and spaces are converted to underscores.Each item can have up to 30 tags. To remove a tag from an item, select the X icon next to the tag.
-
When you're finished, select Save.
You can now search for items with that tag using tags:<term>.
Choosing Tag Terms
Work with your governance experts and security teams to establish a list of tags that are most expressive of governance objects and access managed by Identity Security Cloud, such as:
- Risk levels
- Remediation urgency levels
- Affected departments
- Compliance and regulatory categories
Search Categories
Each search category represents a type of data you can search for. You can view results by category using the tabs at the top of the table.
- Identities - Search the correlated identities you have in Identity Security Cloud.
- Roles - Search roles.
- Access Profiles - Search access profiles.
- Entitlements - Search the entitlements you've loaded into Identity Security Cloud.
- Events - Search for certain audit events in your system. These audit events use a normalized name and include additional information about each event.
- Attribute sync events are treated as Events in Search because of their lower impact and higher frequency.
- Account Activity - Account activity covers most activity that Identity Security Cloud completes on source accounts. You'll see the following types of actions when you search for account activity:
- Access Request - Search on access requests.
- Account Attribute Update - Search for events that involved updating a single attribute on an account.
- Account State Update - Search for events that involved locking or unlocking an account on a source.
- Certification - Search for events involving removing an entitlement from a user as a result of the entitlement being revoked during a certification.
- Cloud Automated
<Lifecyclestate>- Search automated lifecycle state changes that resulted in an identity being assigned to a different lifecycle state. The<Lifecyclestate>variable will be replaced with the name of the lifecycle state that the identity moved to. - Identity Attribute Update - Search on the times when an identity's attribute was updated within Identity Security Cloud as the result of a provisioning action. When updating an identity attribute also updates an identity's lifecycle state, you'll also see the event Cloud Automated
<Lifecyclestate>. Updates to identity attributes that occur as a result of an aggregation are not included in Account Activity. - Identity Refresh - Search identity refreshes that happen whenever a user gets a new role, an identity profile is updated, or an app is assigned to users based on that app being assigned to All Users From Source or Specific Users From Source.
- Lifecycle State Refresh - Search the actions that took place when a lifecycle state was changed. This event only occurs after Cloud Automated
<Lifecyclestate>or Lifecycle State Change. - Lifecycle State Change - Search account activity that resulted in an identity being manually assigned to a null lifecycle state.
- Password Change - Search password changes on sources.
Search Glossary
Our documentation uses specific terminology to refer to different parts of a search query. This terminology is defined below.
Query
Everything you enter into the search bar is your query. By adjusting your query, you narrow down your results.
| Query Examples |
|---|
attributes.location:austin |
@access(displayName:administrator AND source.name:Oracle |
Term
The words you use in a query to specify the results you want. The results that are returned contain your terms.
| Description | Example |
|---|---|
| "Active directory" is the search term. | "active directory" |
| "Austin" is the term. The rest of the query consists of fields. | attributes.location:austin |
Field
Specifying a field in your search query is similar to telling Search which folder you'd like to look in. It's a way of telling Search where it should look for the term. All searchable items have fields.
| Description | Example |
|---|---|
| "Name" is the field on the right, specifying that this query only searches in the name field for the term "donald.hernandez". | name:donald.hernandez |
| This query specifies to search in the attributes field for a second field called location. | attributes.location:austin |
| This query searches within the attributes field for the location field, and the manager field for the the name field. | attributes.location:austin AND NOT manager.name:"Amanda Ross" |
First-Level Field
The deepest category you can search in is the first-level field. This is always the field physically closest to your terms in a search query. In our JSON data models, the first-level field is the key in a key/value pair. In other words, first-level fields contain actual data, as opposed to more fields.
| Description | Example |
|---|---|
| Name is the first-level field on the right. In queries with only a single field, that's always a first-level field. | name:donald.hernandez |
| Location is the first-level field because it's the field describing the actual data. | attributes.location:austin |
| The query on the right contains the first level fields name, privileged, and entitlementCount. | @access(source.name:"Directory" AND privileged:true) AND entitlementCount:>15 |
Operator
To combine different terms and attributes of a search category in your query, you can use operators. Operators determine how to run your query and how the results are calculated.
Search supports the operators AND, OR, and NOT.
| Description | Example |
|---|---|
| This query uses the operator OR to return all identities that are in either Austin or Houston. | attributes.location:austin OR attributes.location:houston |
| This query uses AND to return identities with access in a source containing the word "Directory" in its name, that has any privileged access, as well as having 15 or more total entitlements. | @access(source.name:"Directory" AND privileged:true) AND entitlementCount:>15 |
Object
In JSON, an object is any field that, instead of containing data, contains more fields. This means that second-level fields, third-level fields, and nested-level fields are all objects.
| Description | Example |
|---|---|
| Attributes is an object because it contains the first-level field "firstName." | attributes.firstName:kari |
| Both access and source are objects. "Source" is an object that contains the field "name." "Access" is an object that contains all the fields enclosed in parentheses after it. This means that "access" is an object that contains the object "source" and the fields "name" and "privileged." | @access(source.name:"Directory" AND privileged:true) AND entitlementCount:>15 |
Second-Level Field
Second-level fields are a type of object. Each second-level field contains a specific set of first-level fields. They're always followed by a period, a first-level field, and the search term.
| Description | Example |
|---|---|
| Attributes is the second-level field in this query because it contains the first-level field "location." | attributes.location:london |
| Source is the second-level field on the right. It contains the first-level field "name." It's contained within the nested object "accounts." | @accounts(source.name:AD) |
Third-level fields are similar, referring to objects that contain both second- and first-level fields. At this time, these are only found in the account activity data model.
Nested Object
Nested objects can contain any number of fields in them. They represent an object contained within the data about another object, such as an account object in the identity object.
Queries for nested objects are always preceded by an @ symbol and followed by a set of parentheses containing any additional fields and the search terms.
Nested objects are treated differently than regular fields because any item in a searchable category could potentially have more than one of anything in a nested object. For example, an identity only has one displayName, so that's treated as a first-level field. However, an identity could have any number of accounts, so accounts is a nested object.
| Description | Example |
|---|---|
| In this query, accounts is the nested-level field. It contains the second-level field "source," which contains the first-level field "name." | @accounts(source.name:AD) |
| AccountRequests is the nested-level field. It contains the first-level field "op," which is short for operation. | @accountRequests(op:enable) |
| Access is the nested-level field. It contains the second-level field "source" and the first-level field "name," as well as the first-level field "privileged." Everything within the parentheses is within the nested field. | @access(source.name:"Directory" AND privileged:true) AND entitlementCount:>15 |
Viewing Events
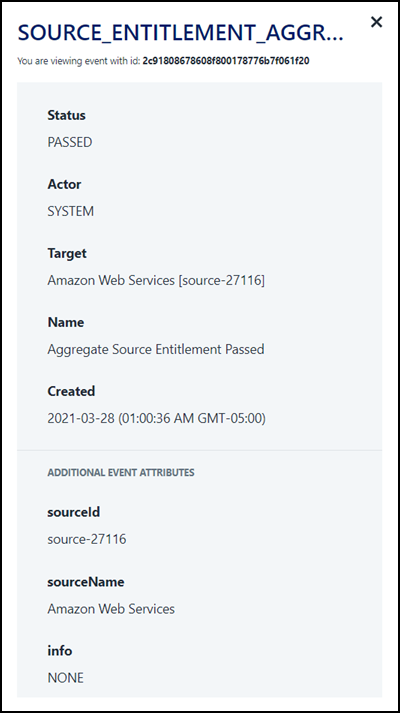
You can view your site's audit events in Search. Select an event to view more details about it.
|
Selecting an audit event in Search displays the name and technical ID of the event. The technical ID is unique to that event instance, and can be used to find it again. The event's status is displayed, so you can see its progress. You can also view the user or system that initiated the event, as well as the target system the action is being performed on. If the event contains special attributes, you can view those at the bottom of the panel. |
|
Event Types
Each event is categorized into a type, so that you can search on related information easily. See below for the type as it appears on the event, its description, and a search query to return results of that type.
| Type | Description | Search Query |
|---|---|---|
| AUTH | Events related to any kind of authentication. | type:auth |
| SSO | Any events involving signing into an app using SSO. | type:sso |
| PROVISIONING | Audit events related to provisioning. | type:provisioning |
| PASSWORD_ACTIVITY | Events related to password changes within Identity Security Cloud. | type:password_activity |
| SOURCE_MANAGEMENT | Events related to managing a source. | type:source_management |
| ACCESS_REQUEST | Audit events related to access request activity. | type:access_request |
| USER_MANAGEMENT | Events generated by a user or admin performing actions that impact a user's Identity Security Cloud experience. | type:user_management |
| CERTIFICATION | Audit events related to certifications. | type:certification |
| ACCESS_ITEM | Any events related to changes made to entitlements, access profiles, or roles. | type:access_item |
| SYSTEM_CONFIG | Changes made at the org-level, such as adding new strong-authentication questions or branding. | type:system_config |
| IDENTITY_MANAGEMENT | Events generated by an admin performing management on an identity in the system. | type:identity_management |
| NON_EMPLOYEE | All events related to the management of non-employees, as configured in non-employee sources. | type:non_employee |
| APPROVAL_REQUEST | All events related to approval requests. | type:approval_request |
Event Statuses
You can search on an event's status to see whether it represents a completed action or failure.
| Status | Description | Search Query |
|---|---|---|
| approved | An access request was approved. | status:approved |
| detected | A system involved captured this event when a state changed. | status:detected |
| escalated | An access request was escalated by the system to a new reviewer. | status:escalated |
| failed | The event was captured when an action failed. | status:failed |
| forwarded | An access request was manually forwarded to another user. | status:forwarded |
| ignored | A request sent from the Password Interceptor was ignored. | status:ignored |
| passed | The event was completed successfully. | status:passed |
| processed | A request sent from the Password Interceptor was processed. | status:processed |
| rejected | An access request was rejected. | status:rejected |
| started | A job was started and hasn't been completed yet. | status:started |
| terminated | A system involved cancelled the request. | status:terminated |
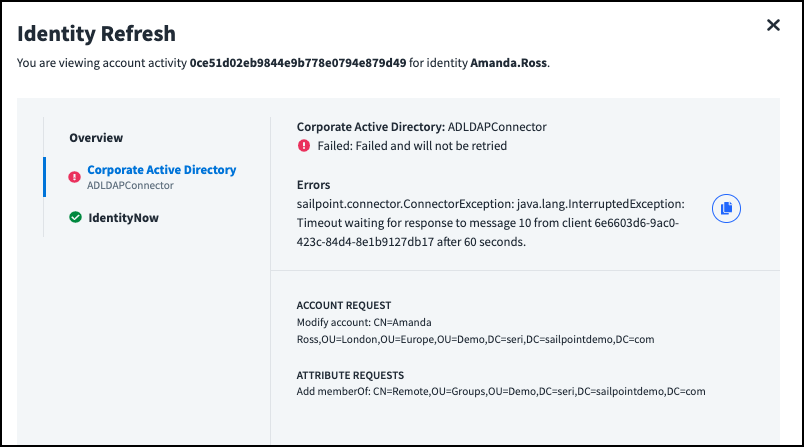
Viewing Account Activity
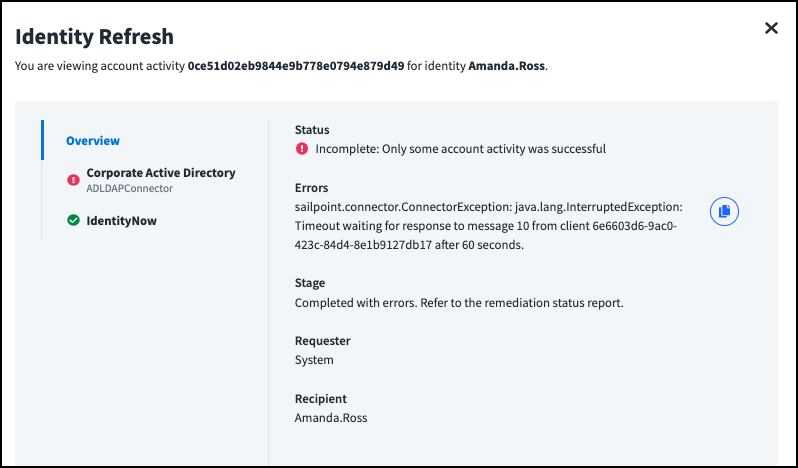
Searching on account activity can give you insight into the actions Identity Security Cloud performs on third-party systems. Select an account activity search result to view details about the action, such as the sources involved, errors or warnings, and the requestor and recipient of the action.
You can search on errors and warnings using fields in the @accountRequests object. Select a source to view details about the provisioning actions performed on it and their status, warnings or errors, and the account and attribute requests.
Account Activity Statuses
There are several types of statuses available in account activity. Each is searchable using a different query and refers to a different part of the action being performed.
Status
The status of an account action is its overall status. For example, if the status of an account attribute update action is complete, all modifications to the account have been finished, and all of the applicable account attributes were updated. Status can also be found in the list of account activity search results, using the column header Status.
| Status | Description | Search Query |
|---|---|---|
| Complete | Approved actions have completed. If an access request was rejected, the Completed badge will still display even though no account actions took place. |
status:complete |
| Failure | All actions related to this account activity failed. | status:failure |
| Incomplete | Some of the actions requested were completed successfully, but some failed. | status:incomplete |
| Pending | The account activity hasn't been attempted yet, but it's scheduled to be attempted. | status:pending |
Stage
The stage of an account action is its progress. This reflects whether Identity Security Cloud still has actions ongoing related to the account activity or whether it's finished. Stage can also be found in the list of account activity search results, using the column header Stage.
| Stage | Description | Search Query |
|---|---|---|
| Completed | The action was confirmed on the source. | stage:completed |
| Executing | The action is in progress. | stage:executing |
| Terminated | The action was cancelled and won't be retried. | stage:terminated |
Account Request Status
The account request status is the status of each individual part of the larger action that was triggered in Identity Security Cloud. For example, if you're looking at an account attribute update, Identity Security Cloud might have attempted to update 4 different accounts related to a single user. Each source account being edited might have a different account request status. This data can be found by selecting an account action and navigating to one of the sources being updated.
| Account Request Status | Description | Search Query |
|---|---|---|
| Pending | The actions on the account are in progress. | @accountRequests(result.status:pending) |
| Committed | The requests have been sent to the connectors. | @accountRequests(result.status:committed) |
| Finished | The results have been confirmed on the source, whether they were successful or failed. | @accountRequests(result.status:finished) |
| Unverifiable | The request was sent to the source, but the source's account schema doesn't have the attribute being provisioned. | @accountRequests(result.status:unverifiable) |
| Failed | The action failed and won't be retried. | @accountRequests(result.status:failed) |
| Retry | The action failed, but Identity Security Cloud is going to try again. | @accountRequests(result.status:retry) |
| Manual Task Created | The action was requested on a source that isn't a direct connect source. We've created a manual task for the source owner. | @accountRequests(result.status:"Manual Task Created") |
| IdentityNow Task | The action was performed on Identity Security Cloud successfully. | @accountRequests(result.status:"IdentityNow Task") |
Take a look at our additional Search documentation to learn more about what you can search on and how to build a query.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.