Automating Role Assignment
Users often need to be given access based on attributes like their job title, department, or location. You can configure assignment criteria to automatically grant a role to users who should have it. This also provisions the entitlements in the role’s access profiles to each user’s source accounts.
Additionally, when a user no longer meets the criteria, Identity Security Cloud deprovisions the role and its associated access profiles. This can occur because the assignment criteria or the identity data changed.
Important
Revoking roles and entitlements does not remove source accounts, even if the accounts were created by role provisioning or if all entitlements are removed from the account.
Roles can be automatically assigned to identities that:
- Meet the criteria you configure for role membership.
-
Are added to the role's list of identities.
You can also mark a role as requestable. If a user requests that role and their request is approved, they will gain access to the role and its access profiles.
Configuring Role Assignment
-
Go to Admin > Access Model > Roles.
-
Select the role name in Table view or select the Edit button in Cards view on the role you want to configure.
-
Select Define Assignment.
-
Under Choose Criteria Type, select Standard Criteria or Identity List.
- Use Standard Criteria to configure the logic through data-driven criteria.
- Use Identity List to manually select which identities should have the role.
-
Depending on the criteria type you chose, either use Operator Settings to select the criteria group logic or use the Add Identities dropdown list to add identities.
-
Select Save.
-
In the role header, select Enable Role.
Your new or updated role configurations will be applied to your identities the next time they are analyzed in identity processing. To manually initiate this update for all identities, select Apply Changes at the top of the role list page.
Best Practices
-
For best system performance, when creating or updating multiple roles, wait to select Apply Changes until you have finished the whole set of changes.
-
If an identity has multiple accounts on a source, you can configure access profiles to determine which account receives the entitlements when the role is assigned to the identity.
Standard Criteria
Use the Standard Criteria builder to configure the criteria for selecting the identities that should have this role automatically assigned and provisioned.
-
Select Add Group to begin defining your criteria.
-
In the Type dropdown, select the type of attribute to use in the provisioning criteria.
- Identity Attribute - Use any mapped attribute from an identity profile.
- Account Attribute - Use an attribute from the account schema for the selected source. The description attribute, as well as the attributes marked as the account ID and account name, can't be used for role criteria.
- Entitlement - Use a specific entitlement from the selected source.
-
For account attribute and entitlement types, use the Source dropdown list to select which source the attribute or entitlement should come from.
-
For account and identity attributes, select the name of the attribute in the Attribute field.
Note
Only string and boolean type account and identity attributes are supported.
-
Use the Operation dropdown list to select how to compare the value of the selected attribute with the value you enter. The operations available for selection vary according to the attribute type, but can include the following:
- Equals - The attribute and value must match. Multiple values are compared as OR operations.
- Does Not Equal – The attribute and value cannot match.
- Contains - The specified value must exist somewhere within the attribute’s value.
- Does Not Contain - The specified value cannot exist somewhere within the attribute's value.
- Starts With - The attribute must start with the specified value.
- Ends With - The attribute must end with the specified value.
- Greater Than - The numeric attribute must be greater than the specified value.
- Greater Than or Equals - The numeric attribute must be greater than or equal to the specified value.
- Less Than - The numeric attribute must be less than the specified value.
- Less Than or Equals - The numeric attribute must be less than or equal to the specified value.
-
For identity and account attributes, use the Value field to enter up to 25 text values you'd like to compare to the attribute. Press return after entering each new value. This field is case insensitive.
For entitlements, select up to 25 entitlements of the same entitlement attribute type in the dropdown list. Multiple entitlement attribute types in the same criteria definition are not supported.
Note
To filter on the identity attribute Lifecycle State, you must enter the technical name of the lifecycle state in the Value field.
-
If you need multiple criteria, select Add Criteria to add another row.
Use the Within Groups toggle to specify whether your criteria should be combined with an AND or an OR operator:
- AND means all criteria must be met.
- OR means meeting any of the criteria produces a match.
-
If your requirements are more complex, needing both AND and OR relationships, select Add Group to add another group.
Refer to Standard Role Criteria Examples for more information.
Identity List
When you choose Identity List as the setup type, you choose the identities by name that should receive the role.
-
Search for and select an identity in Add Identities and select the + icon to add it.
-
Repeat to add more identities.
Select the X icon on any row to remove the identity from the role.
Standard Role Criteria Examples
Your role assignment rules may involve multiple criteria. Use these examples as models for how to build your role assignment rules, especially when your assignment criteria are complex and require both AND and OR relationships in their expression.
Operators Within and Between Groups
When you add multiple criteria to a group, they must be connected by an AND operator or an OR operator.
- AND relationships mean all criteria must be met for the identity to qualify for the role
- OR relationships mean matching any of the criteria qualifies the identity for the role
You specify this with the Within Groups operator selection.
When you need to specify more complex requirements, you can add multiple groups so you can use AND relationships within each group and OR between them, or vice versa.
If you choose AND for your Within Groups operator, the operator applied between groups is automatically OR.
If you choose OR for your Within Groups operator, the between groups operator is automatically AND.
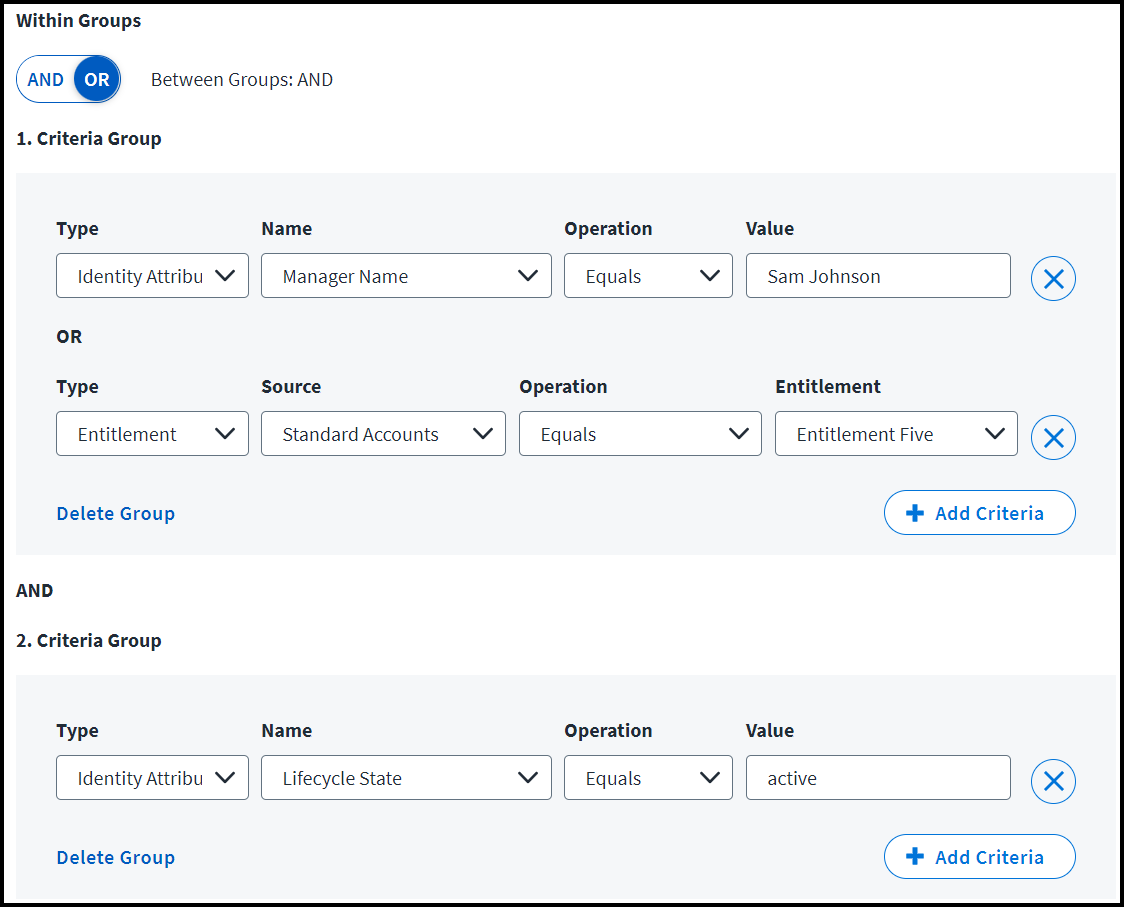
OR Within Groups
This example shows two groups of criteria. They use an OR relationship within each group and an AND relationship between them. This means the role will be granted to users who match at least one criterion from both groups.
Role Criteria: Grant this role to users who meet both of these requirements:
- Users who have either the manager Sam Johnson or the entitlement on the Standard Accounts called "Entitlement Five"
- Users in an active lifecycle state
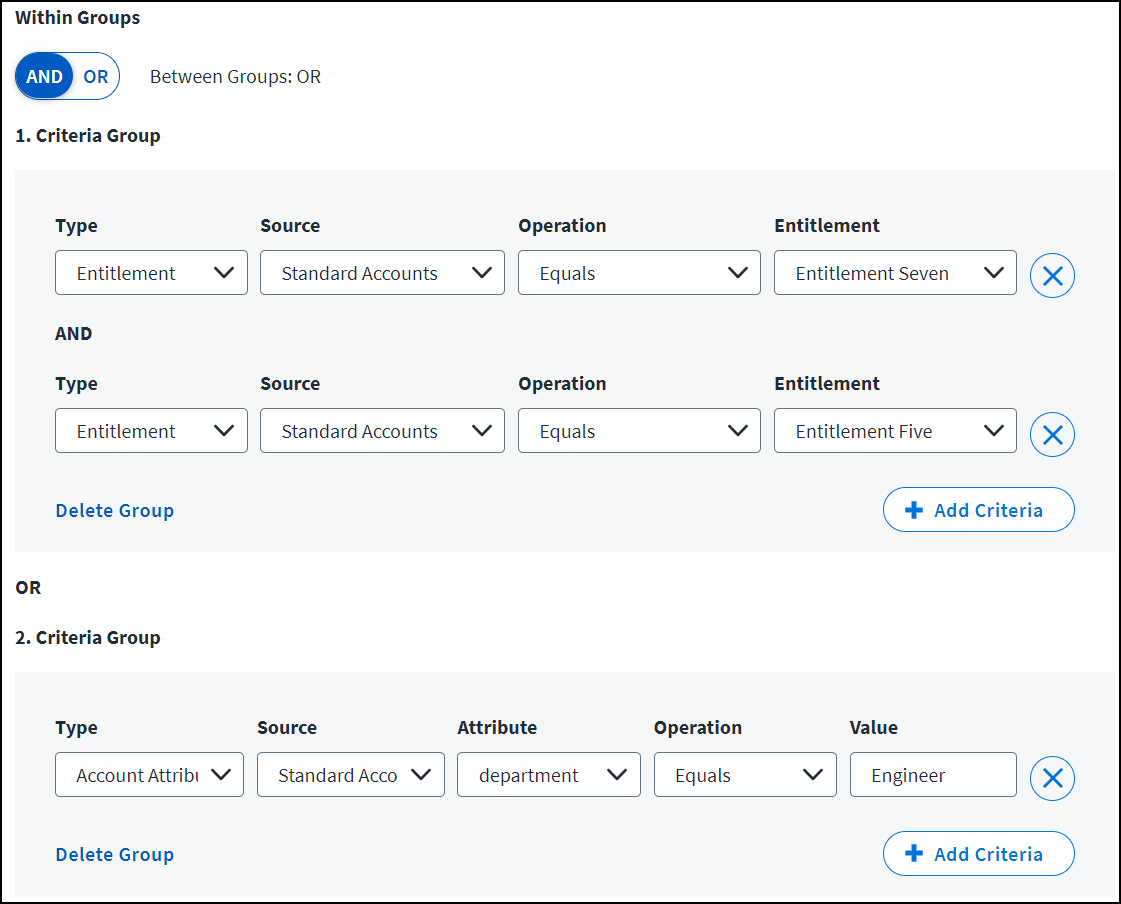
AND Within Groups
This example shows two groups of criteria with an AND relationship within each group and an OR relationship between groups. This means the role will be granted to users who match all criteria within either group.
Role criteria: Grant this role to identities that meet either of these requirements:
- Identities that have both the Entitlement Seven and Entitlement Five entitlements from the Standard Accounts source.
- Identities with the Engineer value in the department attribute on the Standard Accounts source.
In this example, users with only one of the specified entitlements won't receive the role unless they are also in the Engineer department on the Standard Accounts source.
Role Provisioning Retries
Automated role provisioning requests which fail with a retryable error are automatically retried once per hour, up to 3 times.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.