Managing Policies
When using SailPoint's Separation of Duties service, you can implement:
- Separation of Duties policies limit each user's involvement in important processes and protect your organization from individuals gaining excess access.
- General Policies help your organization maintain data integrity.
Note
If you had SoD policies in your org before October 6, 2020, those policies were migrated automatically to General Policies. To use future SoD functionality with these policies, migrate them to access-based policies. Refer to Migrating Policies for more information.
You can have a maximum of 500 total policies, of either type, in your org. In each access-based SoD policy, you can have a maximum of 50 entitlements in each access list. You need at least one entitlement in each access list to prevent errors.
Creating a Separation of Duties Policy
The concept of separation of duties means that people shouldn't have conflicting sets of access - that all their access should be organized in a way that protects your company's assets and data.
For example, people who record monetary transactions shouldn't be able to issue payment for those transactions. Changes to major system configurations should be approved by someone other than the person requesting the change.
Using your internal security rules, you can create Separation of Duties (SoD) policies to enforce and track those rules.
To create an SoD policy, you'll create two lists of access. A violation will be triggered if an identity has access found in both lists.
Prerequisites:
- Know your company's policies and have access to your internal documentation
- Be familiar with Identity Security Cloud's search syntax
To create a separation of duties policy:
-
Go to Search.
-
In the vertical toolbar on the left, select the Policies icon
 .
. -
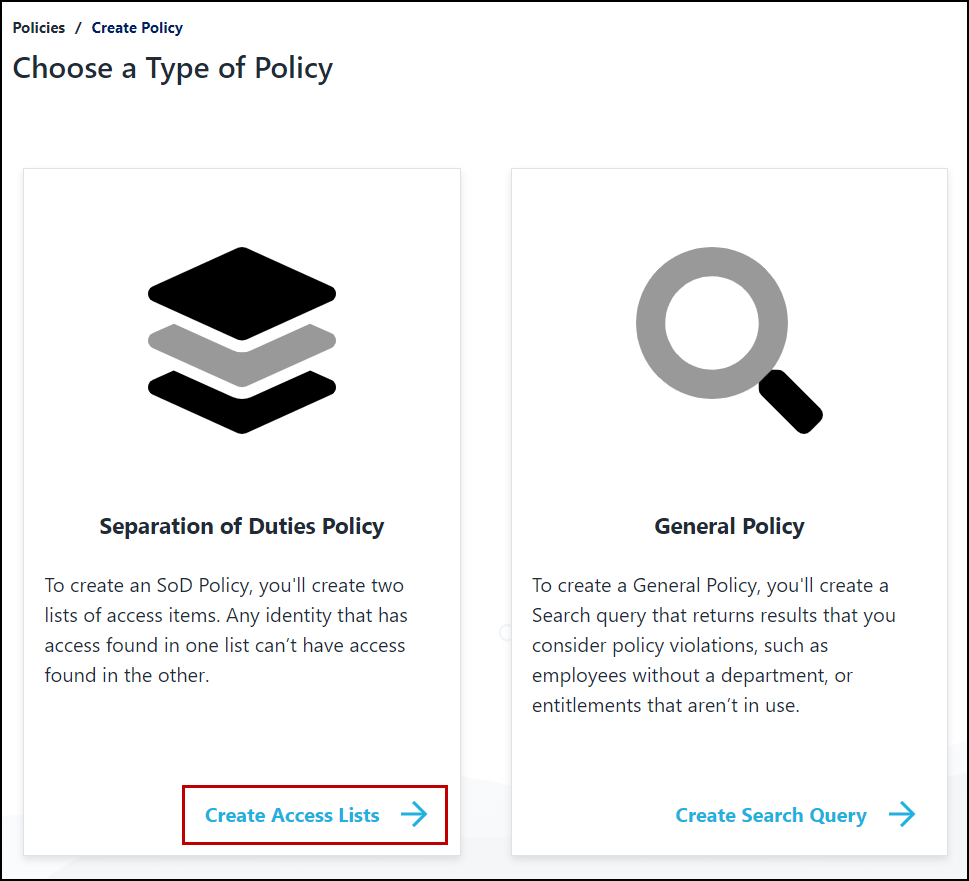
Select Create New Policy.
-
Select Create Access Lists under Separation of Duties Policy.
To create a policy, you'll need to configure two lists of access items. Each access item can only be added to one of the two lists.
Access found in one list conflicts with access found in the other list. An identity in your system will trigger a violation if they have access found in more than one of these lists.
-
Enter a name for each access list. Select Next to see the search page.
-
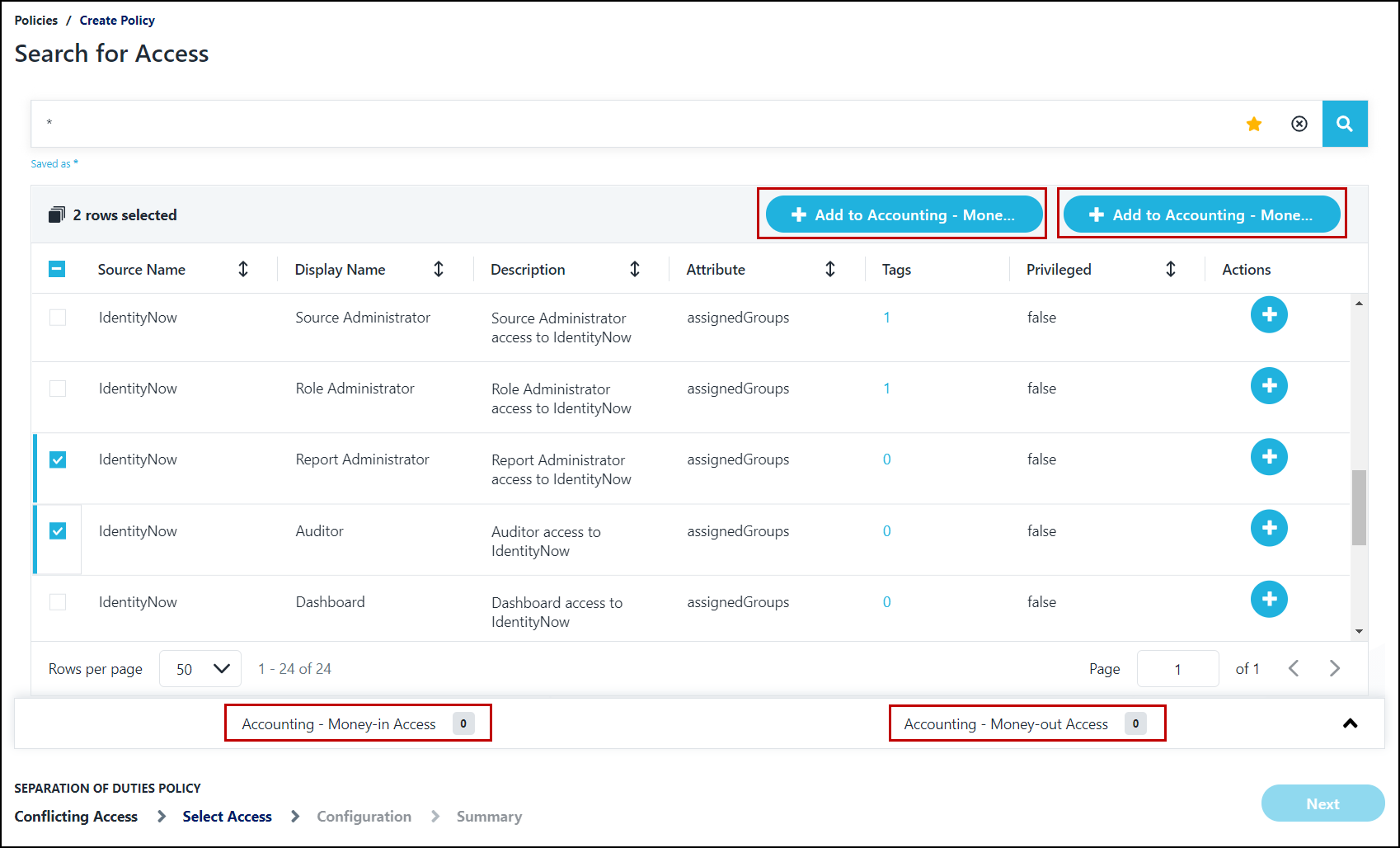
Use Search to find entitlements that you want to add to each list. You can Search for items with a tag using
tags:<term>. -
Select the entitlements that you want to add to one of your lists.
-
Select the + Add button with the name of the appropriate list to add the selected entitlements to that list.
You can also select the + icon beside an individual entitlement and choose which list to add it to.
Notes
- You can revise your search query to find additional entitlements.
- Remove entitlements from each list by expanding the access lists at the bottom of the screen and selecting the X icon beside the entitlement.
When you're finished adding entitlements, select Next to display the Configuration page.
-
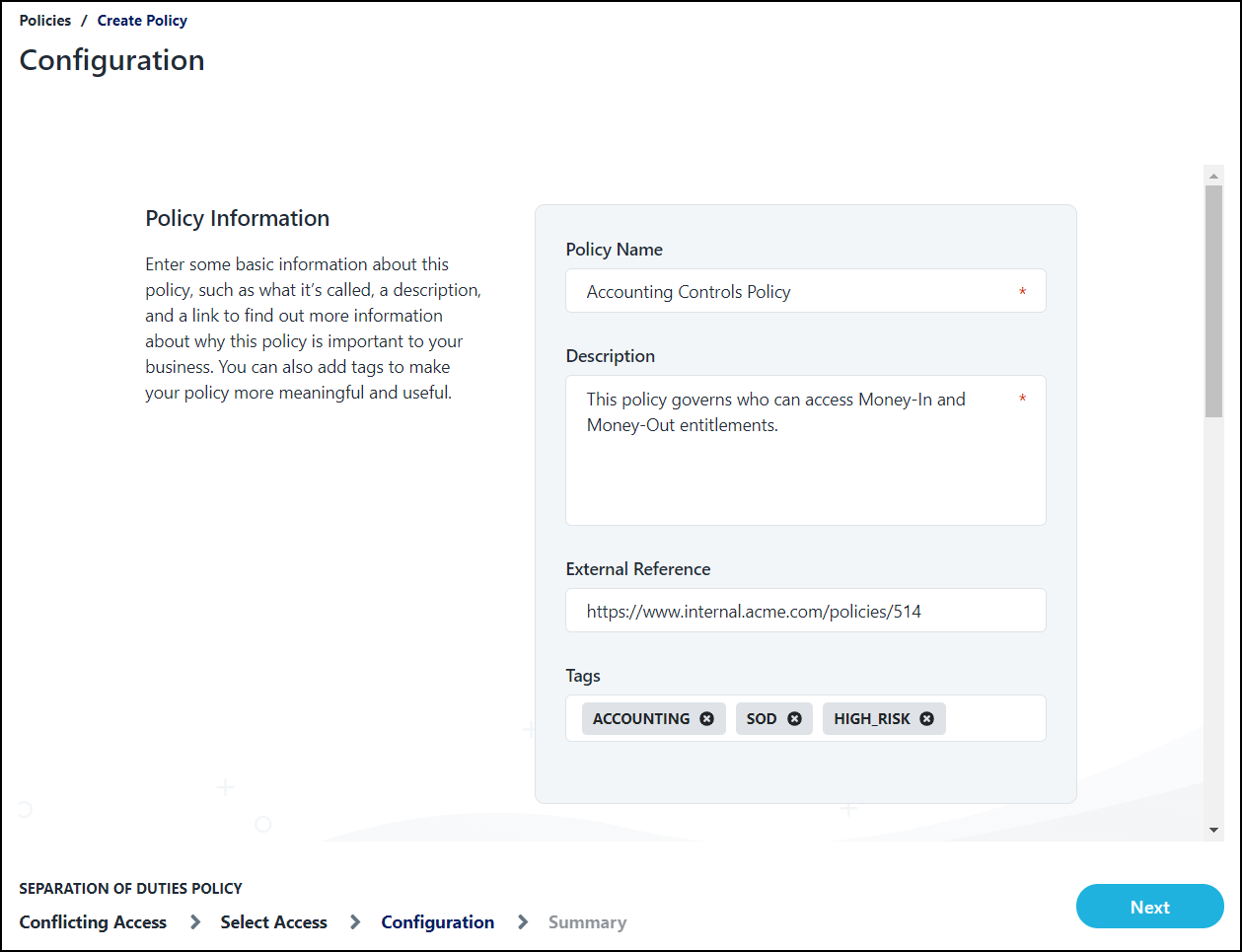
In the Policy Information section, enter the following:
Policy Name - The name of your SoD policy as you call it in your organization. This field is required.
Description - A description of the policy and why it's important. This field is required.
External Reference - A link to a reference site, such as an internal policy or a standards body, that describes this policy and its connections to stakeholders.
Tags - Assign labels to your policy to make it easier to categorize and review later. For example, you can assign risk or priority, define the regulation or certification it's supporting, or record the policy stakeholders involved.
-
In the Separation of Duties Policy Owners section, enter the following:
-
Policy Owner - This user or governance group is the subject matter expert and point of contact for the policy. This field is required.
-
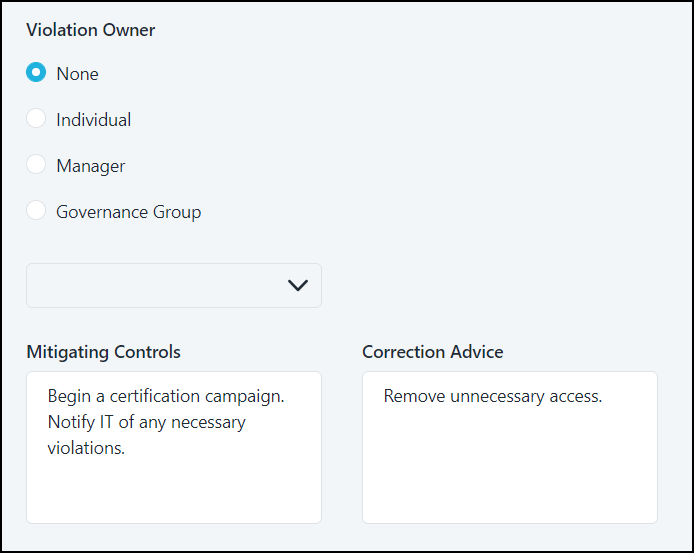
Violation Owner - This user or governance group will be automatically included in policy subscriptions to be notified of policy violations.
If you don't want a violation owner for your policy, you can select None.
If you choose to use a governance group or individual as an owner for this policy, enter the name of that entity in the field. When you select this field, the first six items of your selected type are displayed. To retrieve more, begin typing.
-
-
In the Addressing Violations section, enter the following:
- Mitigating Controls - Instructions on what to do if a violation is unavoidable.
- Correction Advice - How to correct violations.
-
Select Next and review your policy.
-
Select Save Policy.
A success message is displayed.
After you've created a policy, you can edit the policy or take action by downloading reports, enabling the policy, or disabling it.
Creating a General Policy
General policies are intended to keep your identity data organized.
For example, you can create a policy to verify that all employees in your org have a department code to ensure your corporate policies are implemented. Alternatively, you can identify employees who don't have managers to prevent problems with certifications.
To create a general policy, you'll start with a search query to find all identities that meet criteria that violate your organization's internal policies.
Prerequisites:
- Know your company's policies and have access to your internal documentation
- Be familiar with Identity Security Cloud's search syntax
To create a general policy
-
Go to Search.
Note
You can also get to this page by selecting the Policies icon
 in the vertical toolbar, selecting Create New Policy, and choosing Create Search Query under General Policy.
in the vertical toolbar, selecting Create New Policy, and choosing Create Search Query under General Policy. -
Enter a search query. This query should return identities with data is in violation with your internal policies.
For example, you could search for identities in an error status, or who don't have a manager or a department code.
-
Select General Policy.
-
Select Next.
-
Enter the following information on the Configuration page:
Violation Owner - You can choose an individual, manager, or governance group as the violation owner. This user or governance group:
- Will be notified when there are violations to this policy and will be automatically included in any subscriptions to this policy.
- Will be assigned to all remediations and violations when this feature becomes available.
If you don't want a violation owner for your policy, you can select None.
Mitigating Controls - Instructions on what to do if a violation is unavoidable.
Correction Advice - How to correct violations.
Select Next.
-
Enter the following information on the Information page:
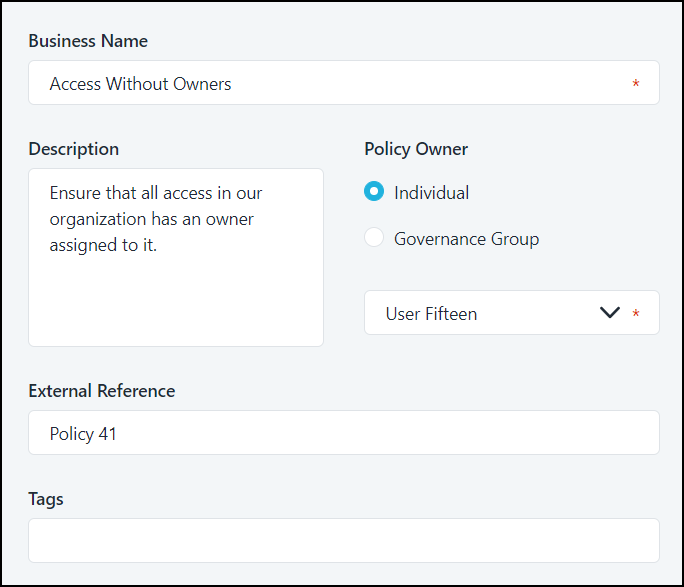
- Business Name - The name of your SoD policy as you call it in your organization. This field is required.
- Description - A description of the policy and why it's important. This field is required.
- Policy Owner - This user or governance group is the subject matter expert and point of contact for the policy. This field is required.
- External Reference - A link to a reference site, such as an internal policy or a standards body, that describes this policy and its connections to stakeholders. If you'd like to be able to select the link to navigate to the site, be sure the link works when you enter it.
- Tags - Assign labels to your policy to make it easier to categorize and review later. For example, you can assign risk or priority, define the regulation or certification it's supporting, or record the policy stakeholders involved. You can Search for items with a tag using
tags:<term>.
Select Next.
-
Review your policy and select Create.
After you've created a policy, you can edit the policy, or take action by downloading reports, enabling the policy, or disabling it.
Editing Policies
Basic information about all policies can be edited. You can also edit the access lists in access-based SoD policies.
Prerequisite: One or more SoD or general policies has been created in your organization.
To edit a policy:
-
Go to Search.
-
Select the Policies icon
 in the vertical toolbar.
in the vertical toolbar. -
Select the policy you want to edit.
-
Select the Options menu and select Edit.
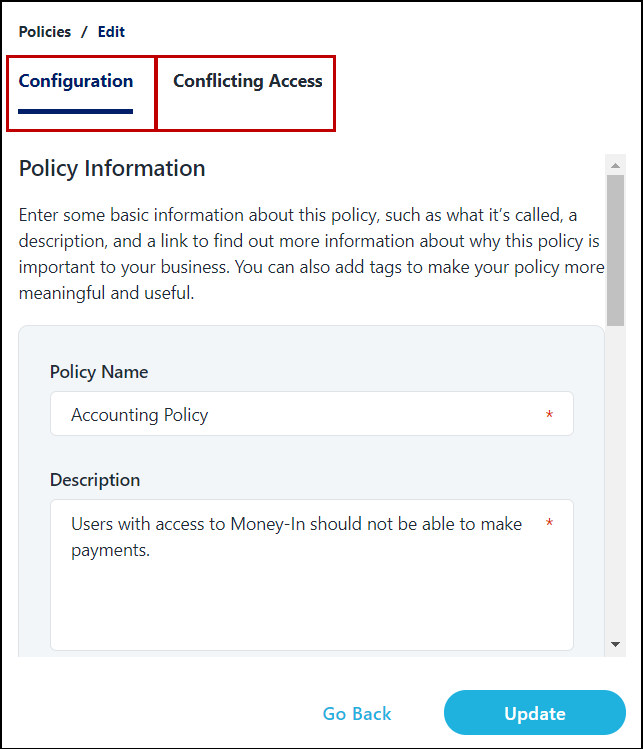
-
Make changes to the data about your policy on the Configuration tab. If you need to make changes to an SoD policy's access lists, select the Conflicting Access tab.
The policy name and description are shown with more options.
Taking Action on Policies
You can take action on your existing policies from the Policies list.
-
Go to Search.
-
Select the Policies icon
 in the vertical toolbar.
in the vertical toolbar. -
Select the policy you want to edit.
You can take the following actions:
- To enable or disable the policy, select the corresponding option in the menu. Violations of disabled policies don't appear in the results of bulk violation reports.
- To delete the policy, select Delete. Deleted policies can't be recovered.
Policy and Violation Limits
You can have a maximum of 500 total policies, of either type, in your org. In each access-based SoD policy, you can have a maximum of 50 entitlements in each access list.
Reports on policy violations are limited to a specific number of violations. Excessive policy violations could be indicative of a larger data problem or a sign that your policy is incorrectly constructed. Consider correcting those issues before downloading reports of your policy violations.
Your site has the following limitations on violations:
- A report of the violations for a single policy won't show more than 2,000 violations and a message will be displayed in the report.
- A report of the violations for all enabled policies won't show more than 10,000 violations, and a message will be displayed in the report. Each multi-policy report will display up to 2,000 violations for a single policy before displaying violations for the next policy in the list.
- Your site can't have more than 50,000 violations across all enabled and disabled policies. If you generate a report that exceeds this limit, you will be warned that you cannot generate additional violation reports until there are fewer violations in your site.
Migrating Policies
If you had separation of duties policies before Oct. 6, 2020, these policies were automatically migrated to general policies when access-based SoD policies were introduced.
This is because those legacy policies and general policies are constructed the same way with search queries.
To use future functionality related to SoD, such as preventative SoD, you’ll need to migrate these policies to access-based SoD policies.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.