Configuring Access Governance on SSO Providers
SailPoint's governance capabilities can integrate with external SSO providers and access management providers in order to govern these systems. This way, Identity Security Cloud can:
-
Give your employees accounts on your provider based on their role or lifecycle state.
-
Assign applications and entitlements to users in your provider.
-
Allow you to review access to the apps and entitlements your users have.
You can also configure Identity Security Cloud as a service provider in an SSO relationship with your identity provider.
Process Overview:
-
Configure apps in your external SSO provider service that you'd like to govern in Identity Security Cloud.
-
Configure your tenant to manage those applications.
Configuring Apps in Your SSO Identity Provider
To create applications and entitlements in your SSO provider that you'll govern in Identity Security Cloud, you'll assign entitlements to apps and configure them in Identity Security Cloud.
SailPoint can manage the apps on SSO providers with a supported source that uses entitlements and apps. It's been tested as a governance solution with the following providers:
-
Microsoft Entra ID
-
Okta
-
VMWare
Note
You must have an Identity Security Cloud for Okta license to use the Okta integration. Contact your Customer Success Manager for more information.
Complete the following steps:
-
In your SSO provider, create or edit an app.
-
Assign that app to an entitlement or group. If necessary, you can create an entitlement specifically for that app. For more specific instructions, refer to your provider's documentation.
Best Practices
-
Configure the entitlement to be assigned to users manually without a rule or other automatic assignment policy. This way, configurations you make in Identity Security Cloud can control which users are granted the app and your governance policy can be maintained.
-
Prepend the entitlements' names with a unique identifier, such as
SLPT_, to make the entitlement easier to recognize in your tenant's entitlement list.
Configuring Identity Security Cloud to Govern Your Apps
Next, you'll configure your tenant so that the apps from above appear in your Identity Security Cloud interface. This allows you to govern your apps.
Follow the steps below to aggregate entitlements and begin making governance decisions.
Prerequisites:
-
The Provisioning service has been enabled for your org.
-
Entitlements or groups have been created on your SSO provider source.
Complete the following steps:
-
Create a source in Identity Security Cloud for your SSO provider service.
-
Aggregate accounts for that source at least once.
-
Ensure that these accounts correlate to identities by resolving uncorrelated accounts for that source. Accounts that appear in that report are uncorrelated and can't be governed. You can manually correlate those accounts to resolve this.
-
From the configuration page for your source, go to Import Data and select Import Entitlements.
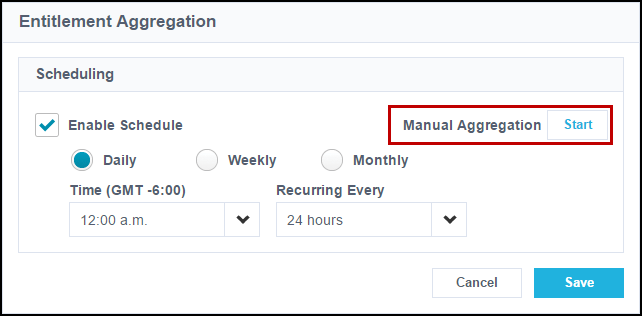
-
Run a full entitlement aggregation by selecting Start next to Manual Aggregation.
Note
If the Import Entitlements page does not display, the source is configured to only recognize entitlements that have been assigned to an aggregated account. Assign entitlements to users in your source before aggregating them.
The entitlements that are loaded in this aggregation are the entitlements that you associated with apps when configuring apps in your SSO provider.
-
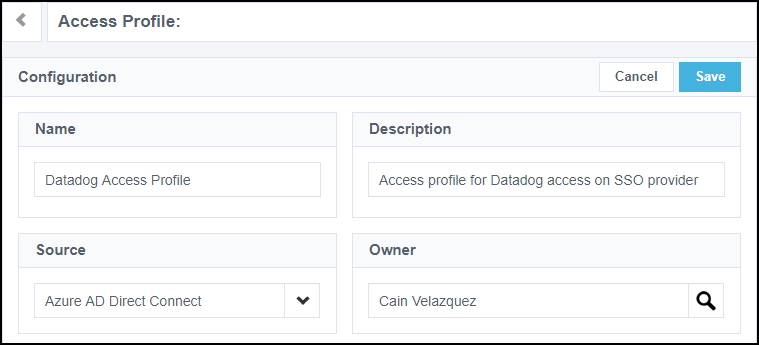
Create access profiles in your org. Make sure each entitlement you associated with an access application on your SSO provider source is assigned to one or more access profiles.
The governance configurations you apply to these access profiles will be applied to the entitlements in them, and by proxy, to the apps on your SSO provider.
-
Make any other necessary configurations to your access profile. This might include:
-
Granting the access profile based on an identity's lifecycle state
-
Granting the access profile based on an identity's role
-
Configuring the access profile for access requests
-
Refer to the Provisioning section for a description of how lifecycle states and roles provision your app to users once you've completed these steps.
Important
Do not enable lifecycle states or roles at this stage.
-
-
Select Applications.
-
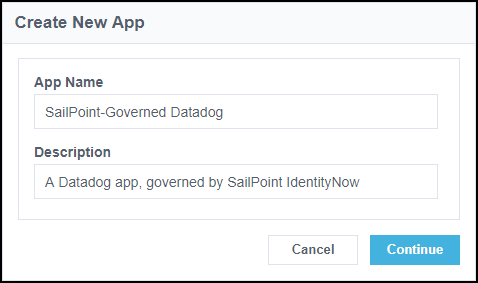
Select or create the access application you'd like to manage that corresponds to the entitlement and app from the user account in the SSO provider.
-
Enter a name and description for your app. SailPoint recommends that you give this app the same name as the app in your SSO provider source.
-
Under App Accounts Created By, select Admin (IT).
- Under Account Source, select Specific Users From Source.
- Beside Select Source, select your SSO provider source.
- Select Save. You'll be prompted to configure access.
- Select the Edit icon
 next to Specific Users From Source to be directed to the Access tab for that access application.
next to Specific Users From Source to be directed to the Access tab for that access application. -
Under Add Existing Access Profiles, select the access profile that is configured for the application's entitlement.
-
Select Save.
-
Make any other necessary configurations to your app. This might include configuring the access application for access requests.
-
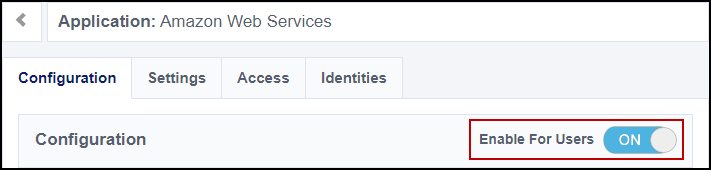
Set Enable For Users to enable the access application for users and select Save.
-
Enable provisioning configurations like lifecycle states or roles.
Governance configurations made within Identity Security Cloud will be enforced on your SSO provider.
Using Identity Security Cloud Services with a Third-Party SSO Identity Vendor
Most of SailPoint's cloud governance services extend governance to your SSO service. These features allow you to use a complete set of identity governance capabilities. Details of how each service works with your provider are listed below.
Access Request
Once you've completed the process of creating apps within your SSO provider and configuring corresponding access applications in Identity Security Cloud, the Access Request service can be configured as usual for your site. Users can authenticate into your tenant and request an access profile(s) to the corresponding access applications in the Request Center. If their request is approved, they're granted the access within the access profile, which adds the access application to their app list within your provider.
In order to use this application, the user must have an account on it. If your SSO provider source is not the source that grants users accounts on this app, you must allow users to request accounts. To do this, create a second access profile and requestable access application that grants accounts on the source of accounts for the app. This way, users can request the access application and the account separately.
Certifications
If your organization uses Certifications, you can create a certification campaign to review users' access to data and access applications. The apps assigned within your SSO service will be represented as access profiles or entitlements in the certification campaign. Revoking access in the certification campaign will remove the app from the SSO provider for that user.
Password Management
You can use Password Management to configure Identity Security Cloud to automatically change passwords within your sources and access applications by creating password sync groups.
Important
When creating password policies using Password Management, make sure that Identity Security Cloud does not require a more complex password than your SSO provider. If this password policy is too complex, when users change their passwords on your SSO provider, the password change will succeed for your SSO provider but fail for Identity Security Cloud and any associated access applications or sources.
Provisioning
You must have Provisioning enabled for Identity Security Cloud to govern your SSO provider's apps.
If a user is provisioned in an access application within Identity Security Cloud, that app will be added to their app list within your SSO provider. The user will also be granted the entitlement that's associated with the app on your provider.
With the Provisioning service, you can use lifecycle states and roles:
-
Lifecycle States:
Using lifecycle states, you can configure policies to determine what access profiles are granted to a user and when, such as automatically granting the access a user needs when they start at your company. When they go on leave or change jobs, you can adjust their access. Access profiles will be granted to and removed from users automatically and the associated access applications will be added to and removed from their app lists on your SSO provider.
-
Roles:
Roles allow you to configure access for users based on their job. You can configure access profiles to grant to users with a particular job title, and if a user's job title changes, you can change the role assigned to them. If a role grants your users an access profile associated with an access application, that app will be added to users' app lists in your provider.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.