Activities
This chapter describes the collecting and monitoring activities (events), as well as the File Access Manager services of the activity collection process.
Note
This section does not discuss how to monitor specific types of applications. The Collector Installation guides provide information on the installation and configuration of specific collectors.
Monitoring Activities
Monitoring activities in involves capturing information about events that users perform on monitored applications.
An activity includes the following elements:
| Element | Description |
|---|---|
| Who | A user performing the action |
| Performed what action? | Read, write, or delete |
| Where? | On what business resource, for example a file, a file folder, a SharePoint site, or an Exchange mailbox |
| When? | Date and time. The timestamp is stored in UTC, and displayed to the user in its current time-zone, based on the computer from which they are connecting |
Event Example
-
User jsmith, performed a write action on the \\file_server\Finance\2015\cashflow.xlsx at 7:35 pm at 16 March 2015.
-
User contextual information for this activity are added from additional data sources, including:
-
Attributes from the user’s Active Directory, such as the user’s display name, groups to which the user belongs, the user’s company, title
-
The department of the user, normally obtained from the Human Resources system
-
Data classification information, for example, when information contains sensitive data about the business resource
-
-
Finally, activity monitoring sends alerts regarding suspicious activities, based upon sets of pre-defined rules.
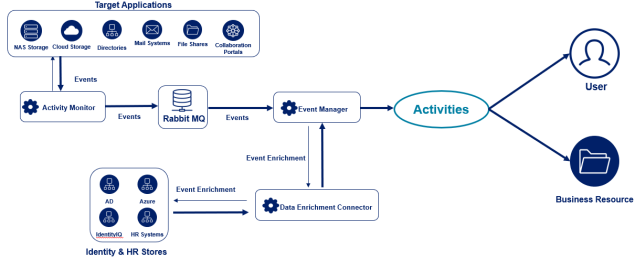
Terminology
| Term | Description |
|---|---|
| Event | An event is anything that occurs in an application. |
| Activity | An activity is a monitored File Access Manager event, such as the execution or modification of a file on a file system, enriched with security attributes (such as details of the executing user from the Active Directory). |
| Alert | The system sends an alert when an activity violates a File Access Manager real-time rule. File Access Manager can issue alerts within the system or send them to other systems, such as SIEM for monitoring. |
| Activity Monitor | Note: Each Collector Installation guide contains specific installation and configuration instructions. The Activity Monitor is a software module that monitors and collects events from an application. Most File Access Manager Activity Monitors work in an agentless architecture, and can monitor and capture events without having to install anything on the application itself. |
| Event Manager | The Event Manager is a service, installed by the File Access Manager Server Installer, which: 1. Pulls events from RabbitMQ. 2. Uses Data Enrichment Connectors (DECs) to enrich events with security attributes. 3. Evaluates discard and alert rules. 4. Saves events to Elasticsearch. |
| Data Enrichment Connector (DEC) | Note: The previous name for a DEC was Whitebox Policy Connector (WPC). The Data Enrichment Connector (DEC) is a software module that facilitates communication between File Access Manager and an organizational/security system. File Access Manager enables the definition of multiple DECs and uses them to enrich monitored activities with information retrieved from various organizational systems. File Access Manager offers DECs for many commonly used systems including Active Directory, SailPoint IdentityIQ, LDAP, and SQL DB. |