Scheduling a Targeted Certification
Targeted Certifications are the most flexible type of certification. In a Targeted Certification you can certify role, entitlement, and account access for a narrowly defined set of identities. The Targeted Certification gives you a high level of flexibility in choosing which parameters to include in the certification, such as who, what, and when to certify.
Targeted Certification: Who to Certify
To narrow down the identities to certify, choose an option for selecting identities. To certify all identities in your system, do not define any selection criteria.
Filter Identities
Use filters to define the identity list for the certification. You can filter identities by attribute, using operations like Equals, Not Equals, or Starts With. You can choose the values for the filter from a list, or type them in. You can only type in valid values.
You can choose more than one value for any one filter. When you do this, the criteria works as an "or" operation, so the certification will include all identities meeting any of the criteria. For example, filtering on Department Equals and entering two departments will select identities from both those departments.
Add more filters if you want to filter on more than one attribute using an "and" condition. With multiple filters, identities have to meet each of the sets of filter criteria in order to be included. For example, filtering on Department Equals Accounting and Location Equals Berlin will select only identities that are in the Accounting department in Berlin.
Access reviews for Service or RPA / Bot identities are sent to the certifier specified during your configuration process.
Population
Choose from the populations that have been defined in your IdentityIQ system. Populations are saved queries based on searches run from the Identity Search feature of Advanced Analytics. See Advanced Analytics.
Rule
Choose a rule that will select identities. The Targeted Certification does not include a rule editor, so you are limited to choosing existing rules from the list. Only rules with a rule type of CertificationScheduleEntitySelector are included in this list.
Exclude Inactive Identities
Check this to omit identities flagged as Inactive at the time the certification is generated. For recurring certifications, future occurrences will reflect any changes that have happened since the last certification was generated, including identities that have become inactive.
Targeted Certification: What to Certify
This section lets you narrow the focus of the certification by defining which elements of accounts, roles, entitlements, and target permissions to include.
For Roles / Entitlements, you can add more criteria that is specific to entitlements:
-
Check Additional Entitlements to include entitlements that are not contained in a role. If you check this option, you can also add filtering criteria to choose the entitlements to include.
-
Check Include Accounts without Entitlements to include accounts that have no entitlement attributes.
-
Check Target Permissions to include the actions a user can perform on an Unstructured Target such as a file share or folder.
Adding Filters
You can filter the Roles/Entitlements or Accounts to include in the certification, using operations like Equals, Not Equals, or Starts With. You can choose the values for the filter from a list, or type them in. You can only type in valid values.
You can choose more than one value for any one filter. When you do this, the criteria works as an "or" operation, so the certification will include all entities meeting any of the criteria. For example, filtering on Owner Equals and entering two identities will select roles / accounts owned by either of those identities.
Add more filters if you want to filter on more than one attribute using an "and" condition. With multiple filters, entities have to meet each of the sets of filter criteria in order to be included. For example, filtering accounts on Service Account Equals True and Application Equals Active_Directory will select only service accounts on the Active Directory application
Select Attribute
Select a role / entitlement attribute from the dropdown list.
Operator
Select an operator from the dropdown list for this attribute.
Value
Select a value from the dropdown list. The values available are dependent on the attribute and operator selected. You can enter text in the value field for some types of attributes, to help find the value you want; only valid values are supported.
Other Options
Include Policy Violations
Policies are rules that enforce your enterprise's business policies on separation of duty, activity, and risk. Violations of those policies can be included in the access reviews generated by the certification.
Exclude Logical Tier Entitlements
Logical applications are applications formed by the detection of accounts from other applications, called "tier" applications, in existing Identity Cubes. Use this option to exclude entitlements on tier application accounts from the certification. This applies only to logical applications, which are applications formed by the detection of accounts from other applications, called "tier" applications, in existing Identity Cubes.
Filter Logical Application Entitlements
Allow logical entitlements defined on the logical application's managed entitlement list to be included in the certification. Any logical application entitlements are filtered from the tier application entitlements.
Include IdentityIQ Capabilities
Capabilities control access to pages, tabs, and fields within IdentityIQ. Use this option to include IdentityIQ capabilities in the certification.
Include IdentityIQ Scopes
Scopes are used to restrict access to objects in IdentityIQ. If scoping is enabled in your implementation, use this option to include scopes in the certification.
Targeted Certification: Choose Certifier
Use the Choose Certifier section to configure who will perform the certification by reviewing and deciding on access.
Targeted certifications are designed to enable you to get very specific on the certification scheduling page to select exactly who should be the certifier for the certification. Tools are provide that eliminate the need to reassign certifications. This design provides the flexibility of rules from the user interface so that you can schedule certifications without having to write rules.
If required, reassignment can be performed by specifying a Certifier type rule in the Primary Certifier field. For example, if the certifier should be a manager except if the target identity is a manager themself or has no manager, a Certifier type rule can contain the following:
import sailpoint.object.Identity;
Identity target = entity.getIdentity(context);
if (target.getManagerStatus() || (target.getManager() == null)) {
return "spadmin";
}
return target.getManager().getName();
Pre-delegation rules can still be used to support the Delegation and Forwarding of access reviews, but any reassignment components are ignored. Pre-delegation rules are set in the Targeted Certification: Additional Settings section.
Primary Certifier
Choose the Primary Certifier for the access reviews.
Manager
The manager of each identity will act as the primary certifier for that identity. A backup certifier is also required.
Owner
For Roles, the role owner always acts as the primary certifier. For Additional Entitlements, you can choose from the Application Owner or the Entitlement Owner as the primary certifier. A backup certifier is also required. Pre-delegation rules do not support reassignments in the Targeted Certification. Use the Primary Certification field in a Certifier type rule for reassignment
Rule
Choose the certifier using a rule. The Targeted Certification does not include a rule editor, so you are limited to choosing existing rules from the list. Only rules with a rule type of "Certifier" are included in this list. A backup certifier is also required. If you want to use a rule to manage reassignments, use a Certifier Rule here to control reassignments rather than a pre-delegation rule; pre-delegation rules do not support reassignments in the Targeted Certification.
Single Certifier
Choose an identity or workgroup who will be responsible for the access review. You have the option to add a backup certifier, but a backup certifier is not required.
Backup Certifier
A Backup Certifier is required for all types of Primary Certifier except single certifier. The Backup Certifier is the user or workgroup that will be assigned the review if the Primary Certifier can not be identified (for example, in a manager certification when an identity does not have a manager assigned).
Advanced Options
Reassignments
With reassignment, you can pass individual line items or an entire identity to another user to review. The person the items are reassigned to assumes complete responsibility for all decisions on those items, and must sign off on those decisions themselves.
Enable Bulk Reassignment
Allow reviewers to reassign multiple items simultaneously within an access review.
Limit Reassignments / Reassignment Limit
Limit the number of times reviewers can reassign an item in the access review. If you opt to limit reassignments, include the number of reassignments allowed.
Require Reassignment Completion
Require the completion of all reassigned reviews before the parent review can be completed.
Return Reassignments to Original Access Review
When a reassigned review is signed off, return the reassigned review to the original access review owner. When items are returned, the original owner can modify the decisions the reassigned reviewer has made.
Automatically Sign Off When All Items Are Reassigned
Allow the access review to be automatically signed off when all items in the access review are reassigned. This option can only be enabled if the Require Reassignment Completion and Return Reassignments to Original Access Review options are not enabled.
Self Certification
Allow self certification for
Choose which users may self-certify – that is, be the certifier for their own access, either by forwarding or reassigning an access review: All certifiers, Certification and System Administrators, or System Administrators only
Self Certification Violation Owner
For users that are not allowed to self-certify, this is the identity or workgroup that will receive any items that would require a self-certification - that is, when the reviewer and the user whose access is under review are the same person. If a Self Certification Violation Owner is not specified, any items that require self-certification will be read-only to the reviewer.
Other
Prompt for Sign Off
Display an overlay prompting reviewers to sign off, when the access review is complete.
Require Electronic Signature
Require an electronic signature as part of the sign-off process. Reviewers use their IdentityIQ login as authorization for the electronic signature.
Electronic Signature Meaning
If you choose to require electronic signature, choose the meaning (the text that goes with the electronic signature) from the list. Electronic signature meanings are defined in Global Settings > Electronic Signatures.
Automatically Sign Off When Nothing to Certify
If the access review contains no items, allow the review to be signed off automatically with the assigned reviewer's credentials. This sign-off occurs even if there are subordinate access reviews.
Suppress Notification When Nothing to Certify
Do not send a notification email when the assignee has nothing to certify.
Sign Off Approval Rule
A rule can determine if any additional review is needed on the Sign-Off decision. If you enable this option, you also choose the rule to run after initial sign-off by the reviewer, and a Sign Off Approval Notice Email Template. The rule determines if the decisions need to be reviewed by another approver. If so, the user is notified via email using the email template, and the certification request is sent to that user's inbox. This process is repeated until no more reviewers are discovered by the rule. The Targeted Certification does not include a rule editor, so you are limited to choosing existing rules from the list. Only rules with a rule type of CertificationSignOffApprover are included in this list.
Bulk Reassignment Modification Notices
Choose the email template to use to send bulk reassignment notices.
Targeted Certification: Schedule
Use the Schedule section to configure when and how frequently this certification should run.
Start
Execution Frequency
If you want the certification to run on a recurring basis, choose the frequency.
Start Date
The date the certification will be launched.
Start Time
The time the certification will be launched. Certification start times must be at least one minute later than the current time. For example, if it is currently 11:41, the certification start time must be 11:42 or later. Certifications that run across time zones run at the time scheduled, relative to the time zone in which they are scheduled. For example, a certification scheduled to run at 1:00 PDT will run at 4:00 EDT.
Run Now
Start the certification immediately after Schedule Certification is clicked. If this is a recurring certification, the subsequent certifications are scheduled accordingly.
Enable Staging Period
A staging period is when the access reviews have been created but are not yet visible to certifiers, allowing the owner to review the certification before making it active. You can view what the certification definition produces before the certification is activated. If the generated certification does not match your needs, you can cancel the certification and redefine it as needed. If the certification is accurate, activate the schedule.
Initial Notification Email Template
The default email template to use for sending initial certification notices to certifiers.
Suppress Initial Notification
Check this option if you do not want send initial notification emails to certifiers.
Note
Automatic approvals are not dismissed in the access reviews if you turn off the automatic approval feature and then activate a staged certification. To remove automatic approvals access reviews generated by a staged certification, you must delete and redefine the certification.
Active
Active Period Duration
The review period when all decisions required within this certification must be made. During this phase changes can be made to decisions as often as needed. You can sign off a certification in the active period only if no roles or entitlements were revoked, or if a challenge period is not active. When you sign off a certification, the certification enters the end phase or the revocation phase. To enter the revocation phase, the revocation period must be active and a revocation decision must exist.
Active Period Enter Rule
A rule to run when the certification enters its active period. Rules of type CertificationPhaseChange are included in the list.
Notifications and Reminders
Reminders can be sent to the certifiers during the Active period if they have not yet completed and signed off on their access reviews. Escalations can be used to transfer responsibility to someone else (such as the certifier's manager or the certification owner) when a certifier has not completed the access review and the end of the Active phase is near.
Click Add to create a reminder or escalation.
Create a Reminder
Send First Reminder Notification
When to send the first reminder email. After Start means days after the certification's scheduled start date. Before Expiration means days before the Active or Challenge (if enabled) period ends.
Reminder Frequency
How frequently email reminders are sent, until the request is completed or expires.
Reminder Email Template
The email template to use for reminder notifications.
Additional Email Recipients
Activate this option to add more email recipients. Then choose how the additional recipients are defined:
-
Recipient Rule: To use a rule to add more email recipients, choose from the list. Rules of type EmailRecipient are included in this list.
-
Select Additional Recipients: Add identities or workgroups who should receive email notifications for reminders. You can choose multiple recipients.
Create Another
Check this box then click Add to create additional reminders.
Create an Escalation
Escalate
When to trigger an escalation. You can only choose After Sending Reminders if at least one reminder has been created. Day(s) After Start means days after the certification's scheduled start date. Day(s) Before Expiration means days before the Active or Challenge (if enabled) period ends.
Escalation Rule
This rule transfers ownership of the access review to a different identity. Choose a rule from the list; rules of type WorkItemEscalationRule are included in this list. The rule is run if the access review has not yet been finished and signed off by the certifier at the time specified in the Escalate section above.
Escalation Email Template
The email template to use for escalation notifications.
Additional Email Recipients
Activate this option to add more email recipients. Then choose how the additional recipients are defined:
-
Recipient Rule: To use a rule to add more email recipients, choose from the list. Rules of type EmailRecipient are included in this list.
-
Select Additional Recipients: Add identities or workgroups who should receive email notifications for escalations. You can choose multiple recipients.
Create Another
Check this box then click Add to create more escalations.
End
Enable Revocation Period
Enabling a revocation period makes IdentityIQ periodically scan identities to determine whether the requested remediations have been carried out. Remediation occurs whether or not a Revocation period is enabled, but when the Revocation period is enabled, IdentityIQ monitors the status of remediation requests; when it is not enabled, remediation requests are processed but are not tracked.
When the revocation phase is entered, revocation is done automatically if your provisioning provider is configured for automatic revocation, or manually using a work request assigned to an IdentityIQ user with the proper authority on the specified application. The revocation phase is entered when a certification is signed off, or when any Active and Challenge phases have ended.
Revocation completion status is updated at an interval specified during the deployment of IdentityIQ. By default this is performed daily. Revocation requests that are not acted upon during the revocation phase can be escalated as required.
If the revocation period is disabled, the certification is not scanned for completed revocations and revocation status might not be accurately reflected throughout the product.
Revocation Period Duration
The length of the revocation period.
Revocation Period Enter Rule
A rule to run when the certification enters the revocation period. Rules of type CertificationPhaseChange are included in this list.
Process Revokes Immediately
Select this option to indicate that revocations should happen immediately when a decision is made. Otherwise, revocations are not launched until the certification is signed off.
Revocation Notifications
Use this option to send email reminders or escalations before the revocation period expires. Reminders send emails as the end of the revocation period approaches. Escalations use rules to determine how the work item for the revocation is escalated (for example, by transferring responsibility to the certifier's manager). You can only add revocation notifications if Enable Revocation Period is selected. Click Add to create a reminder or escalation.
Create Revocation Reminder
Days Before Expiration to Send First Reminder Notification
When to send the first reminder email.
Reminder Frequency
How frequently email reminders are sent, until the request is completed or expires.
Reminder Email Template
The email template to use for reminder notifications.
Additional Email Recipients
Activate this option to add more email recipients. Then choose how the additional recipients are defined:
-
Recipient Rule: To use a rule to add more email recipients, choose from the list. Rules of type EmailRecipient are included in this list.
-
Select Additional Recipients: Add identities or workgroups who should receive email notifications for revocations. You can choose multiple recipients.
Create Another
Check this box then click Add to create additional reminders.
Create Revocation Escalation
Escalate
When to trigger an escalation. You can only choose After Sending Reminders if at least one reminder has been created. Day(s) Before Expiration means days before the Active or Challenge (if enabled) period ends.
Escalation Rule
This rule transfers ownership of the access review to a different identity. Choose a rule from the list; rules of type WorkItemEscalationRule are included in this list. The rule is run if the access review has not yet been finished and signed off by the certifier at the time specified in the Escalate section above.
Escalation Email Template
The email template to use for escalation notifications.
Additional Email Recipients
Activate this option to add more email recipients. Then choose how the additional recipients are defined:
-
Recipient Rule: To use a rule to add more email recipients, choose from the list. Rules of type EmailRecipient are included in this list.
-
Select Additional Recipients: Add identities or workgroups who should receive email notifications for revocation escalations. You can choose multiple recipients.
Create Another
Check this box then click Add to create additional notifications.
Notify Users of Revocation
Send an email notification to identities whose access was revoked.
End Period Enter Rule
A rule to run when the certification begins its end period. Rules of type CertificationPhaseChange are included in this list.
Enable Challenge Period
A challenge period allows users to be notified of revocation decisions affecting their access. The affected user has the duration of the challenge period to accept the loss of access, or to challenge the decision with a justification for continued access. The Challenge period begins when the Active Period ends. The certifier can consider a challenger's justification and can change decisions based on the challenge.
Challenge Period Duration
The length of the challenge period.
Challenge Period Enter Rule
A rule to run when the certification enters the challenge period. Rules of type CertificationPhaseChange are included in this list.
Email Notifications
-
Challenge Period Start Notices to Certifiers: Email template for notifying certifiers when the challenge period will start.
-
Challenge Period End Notices To Certifiers: Email template for notifying certifiers when the challenge period will end.
-
Challenged Decision Notices To Certifiers: Email template for notifying certifiers when a decision has been challenged.
-
Challenge Decision Expiration Notices To Challengers And Certifiers: Email template for sending challenge decision expiration notices to challengers and certifiers.
-
Challenge Creation Notices To Challengers: Email template for notifying challengers that a challenge has been created.
-
Challenge Expiration Notices To Challengers: Email template for sending challenge expiration notices to challengers.
-
Challenge Accepted Notices To Challengers: Email template for notifying challengers that a challenge has been accepted and agreed to by the certifier.
-
Challenge Rejected Notices To Challengers: Email template for notifying challengers that their challenge has been rejected by the certifier.
Enable Automatic Closing
Automatic closing enables IdentityIQ to automatically complete and sign off access reviews that are unsigned by the access review’s expiration date. Automatic closing occurs after all the other phases that have been enabled for the certification are complete.
Closing Rule
A rule to run at the beginning of the automatic closing process. Rules of type CertificationAutomaticClosing are included in the list.
Action Taken On Undecided Items
The action IdentityIQ will take on any undecided items when automatically closing the access review.
Automatic Closing Signer
An identity or workgroup to add as the signer of the access review when it is automatically closed.
Time After Certification Expiration
The amount of time following this certification's expiration date that IdentityIQ should wait before attempting to automatically close it.
Comments
Include any comments to add to undecided items when automatically closing this access review.
Targeted Certification: Additional Settings
Use the Additional Settings section to configure general information and reviewer options for the certification.
Certification Name
A name to identify the certification to certification owners. You can use free text as well as parameterized dates such as creation day, quarter, or year.
Certification Owner
The identity or workgroup responsible for the certification.
Advanced Options
Enable Bulk Clear Decisions
Allow certifiers to cancel multiple decisions simultaneously in the access review.
Update Entitlement Assignments
Enable this to cause decisions made on entitlement values in the access review to apply to the entitlement assignment model. When this is enabled, approvals create assignments, and revocations remove assignments.
Enable Partitioning
Partitioning aids the performance of certification scheduling, by subdividing activity across multiple threads, to increase processing throughput and speed. If you enable partitioning, you also set the Number of Partitions. If you do not enter a number, IdentityIQ will calculate an optimal number.
Show Access Recommendations
Enable access recommendations from AI-Driven Identity Security to appear in access reviews. This option is visible only if you have implemented SailPoint AI-Driven Identity Security.
Automatically Approve Recommended Items
Automatically mark access review items that are recommended for approval as Approved, and move them from the Open to the Review tab of the access review. This option is visible only if you have implemented SailPoint AI-Driven Identity Security.
Show Classifications
Show classification information in the access reviews. When enabled, classifications provide additional information about roles, managed attributes and policy violations.
Show Elevated Access
When enabled, this will show roles or entitlements that have elevated access.
Delegation Options
Require Delegation Review
Enable this option to require the original access review owner to review all delegated access reviews.
Line Item Delegation
Enable this option to allow certifiers to delegate individual items from an access review.
Identity Delegation
Enable this option to allow certifiers to delegate entire identities in an access review.
Disable Delegation Forwarding
Select to disallow the forwarding of a work item that was delegated by a different user.
Pre-Delegation Rule
Select a pre-delegation rule from the dropdown list. Pre-delegation rules do not support reassignments in the Targeted Certification. Use the Primary Certification field in a Certifier type rule for reassignment.
Email Owner on Pre-Delegation Completion
Send a email to the owner of the original certification upon completion of the certification by the delegates.
Approve Options
Require Comments For Approval
Enable this option to require the certifier to include comments when an access review item is approved.
Enable Bulk Approval
Enable this option to allow users to bulk approve access review items.
Revoke Options
Enable Bulk Revocation
Enable this option to allow users to bulk revoke access review items.
Enable Account Revocation
Enable this option to allow users to bulk revoke all entitlements for a specific account.
Enable Bulk Account Revocation
Enable this option to allow users to revoke all entitlements for a specific account in bulk.
Require Comments for Revocation
Require the certifier to include comments when a certification item is revoked.
Allow Options
Enable Allow Exceptions (applies only to non-policy violation items)
Enables certifiers to allow exceptions on access review items such as roles or entitlements, that are not policy violations. Allowing an exception means the user should not have access indefinitely, but can retain access for a specified period of time.
Deprovision Items When Exception Expires (applies only to non-policy violation items)
Enables automatic deprovisioning of access when the allowed exception period has expired. This setting applies only to items such as roles or entitlements, that are not policy violations. This option is available only when the Enable Allow Exceptions option is also enabled.
Enable Bulk Allow Exceptions
Enable this option to allow users to allow exceptions in bulk.
Enable Allow Exception Popup
Enable this option to allow certifiers to view the Allow Exception popup and manually set expiration dates and allow comments. This applies to both violation and non-violation items.
Require Comments When Allowing Exceptions
Enable this option to require the certifier to include comments when an exception is allowed.
Default Duration for Exceptions
Set a default time period for which exceptions are allowed during the access review.
Access Review Properties
Custom Name
The name of the access review(s). If you do not enter a name here, IdentityIQ will use a default name that includes the type of the certification and the date it was generated. You can use free text as well as parameterized dates such as creation day, quarter, or year.
Custom Short Name
A shorter name for the access review(s). You can use free text as well as parameterized dates such as creation day, quarter, or year.
Tags
Labels that are used to classify certifications for searching and reporting.
Targeted Certifications Cloud Filtering
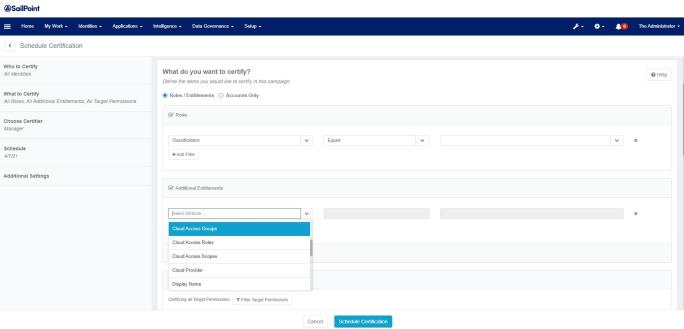
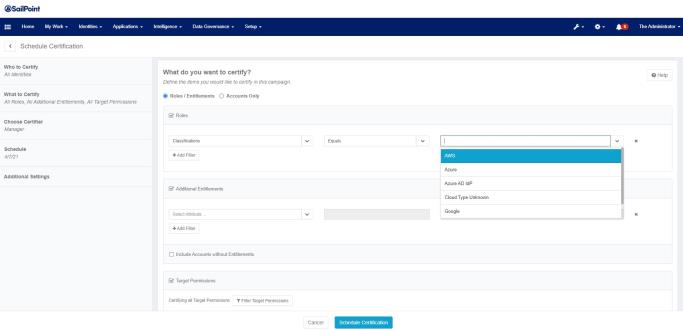
When integrated with IdentityIQ, Cloud Access Management allows the user to define a Targeted Certification to specify cloud specific selection criteria for Roles and Additional Entitlements.
The selection criteria for Targeted Certifications is used to decide which entitlements and / or roles will be included as certifiables when the certification is generated.
Note
New search criteria have been added for Additional Entitlements. All new search criteria will appear as a pull-down option. They will only appear if Cloud Access Management is enabled.
-
Cloud Access Scopes – matches ManagedAttributes which have any of the given scopes indirectly from their Cloud Access Manager groups or roles.
-
Cloud Access Roles – matches ManagedAttributes which map to any of the given roles directly or indirectly from their Cloud Access Manager groups.
-
Cloud Access Groups – matches ManagedAttributes which map to any of the given groups.
-
Cloud Provider – matches ManagedAttributes which have a Cloud Access Manager group or (indirectly) a Cloud Access Manager role with any of the given clouds set directly.