Setting Utilization Options
To provide context for evaluating sensitive SOD, risks, as well as for reporting on activities related to elevated privileges for emergency access management, you must configure utilization options on the agent for each of the SAP systems governed by Access Risk Management.
It is your BASIS administrator’s responsibility to correctly enable, configure, and monitor the security audit log so the capabilities that rely on SAP security audit logs can operate properly.
Caution
If SAP security audit logging is disabled or runs out of disk space, there is no way for Access Risk Management to recover those logs. This could result in audit control failures, particularly for Emergency Access Management.
To enable Security Audit Logs for EAM Utilization reporting:
-
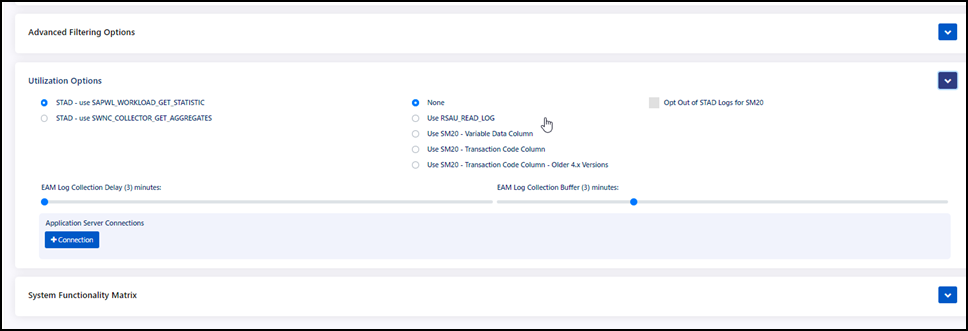
In the Utilization Options section of the SAP system registration page, select the Expand icon
 .
.
-
Select a STAD option.
- If you are running SAP 4.x version, select STAD – use SAPWL_WORKLOAD_GET_STATISTIC
- If you are running SAP ECC version 5.0 or later, select STAD – use SWNC_COLLECTOR_GET_AGGREGATES
-
Follow the logic below to determine which of the following SAP Security Audit Log options to enable as the data source for Emergency Access Management utilization.
- Use RSAU_READ_LOG if function module RSAU_READ_LOG exists in your system.
- Use SM20 - Variable Data Column if RSAU_READ_LOG does not exist when executing function module RSAU_READ_FILE from SE37. When you execute SM20 for Transaction Starts, check whether the transaction code shows up in the Variable Data column.
- Use SM20 - Transaction Code Column if RSAU_READ_LOG does not exist when executing function module RSAU_READ_FILE from SE37. When you execute SM20 for Transaction Starts, check whether the transaction code show up in the Source Transaction column.
- Use SM20 - Transaction Code Column - Older 4.x” if you are on an older 4.x SAP R/3 system.
-
In the Application Server Connections section, select + Connection and enter the Host IP address, Instance Number, and Instance Name of the additional SAP application servers.
Repeat for each application server you have.
Important
You must add every application server connection to ensure that all EAM activity is tracked. Security Audit Log will not work without these connections.
Finding your instance name
You can find the name of your instance by going to TCode ST03N in your Workload Monitor and looking in the ABAP Instance Name column.
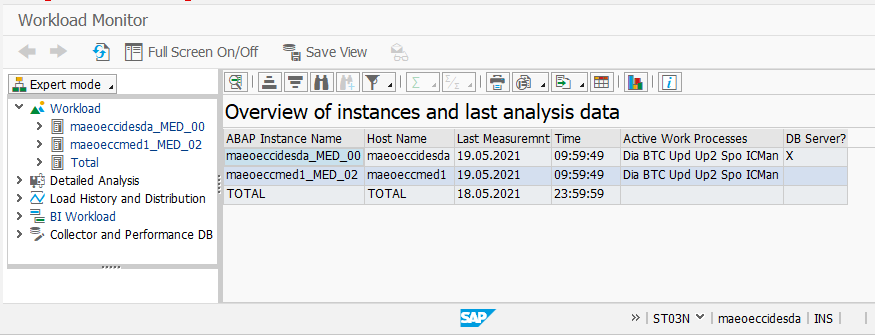
-
Select Save to register your SAP system with these utilization settings.
Enabling Security Audit Logging
The SAP Security Audit Log, or “SM20”, enables SAP administrators to log sensitive system activities for security and auditing purposes, including dialog logons, RFC logons, RFC calls, transaction starts, report starts, user master changes, as well as system and other events. Common concerns about switching to SM20 are that it may result in increased storage costs and burden system administrators managing the log volume.
In all, administrators have the option to log 90 different event types; however, Access Risk Management does not need to log all of these types. The only two that are required are event types AU3 and CUI or Transaction Started / Fiori Application Started. Event types AU3 and CUI will take up less than 1% of the entire log volume, meaning that the total disk space consumed will not impact storage costs or create an undue burden on administrators.
Another common concern is that turning on SM20 may degrade SAP system performance due to generating a lot of log entries, with a high toll on database performance. You should not see a performance impact on your system for two reasons:
- The Security Audit Log has been thoroughly optimized by SAP.
- Both log event retrieval and writing to disk take place in the kernel.
If you are concerned, try it out for a day. Work with your BASIS team to request approval to enable and configure the SAP Security Audit Log with configuration to enable logging for all users, but only event types AU3 and CUI. Collect data for a period of time and verify that there are no adverse performance indications and that the overall disk space requirements are reasonable.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.