Choosing User to Role Review Settings
After you enter the review details for the User to Role type of review, set the time frame for usage data, rulebook(s), the security extract, and what user groups and roles to include or exclude.
Note
This type of review can only be performed by Managers or Role Owners.
-
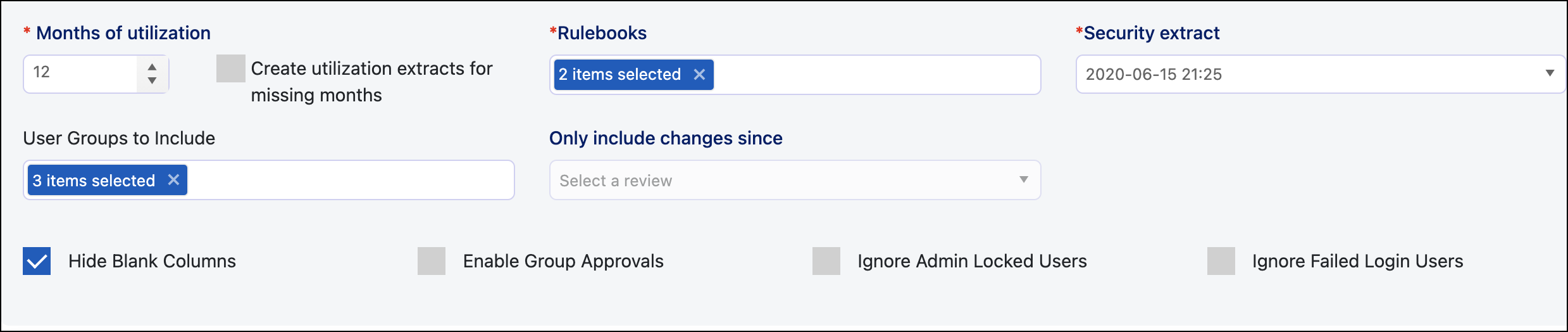
Under Months of utilization, enter or use the arrows to set the time frame the review will use to identify if the transaction codes in those roles are being used, providing insight into whether a role assignment is appropriate for a user based on usage.
Tip
You may want to change the months based on the frequency of reviews. For example, if reviews are done quarterly, you may only need the previous three months of utilization.
-
If you have not run a utilization extract job during the access review time frame, we recommend that you select the Create utilization extracts for missing months checkbox to automatically pull utilization extracts for months missing from the review time frame. Otherwise, they won't be included in the review.
-
Select the rulebook(s) to include in the review. Reviewers can view the rulebook(s) to see the risk associated with the role, helping them decide if that role's access should be retained by the user.
-
Choose a security extract. You can select a previously completed security extract or a live security extract where a new security extract is pulled from SAP to run the analysis for the review.
Note
Previously completed extracts are sometimes used when completing a review for access at a certain point in time, even if that time has passed.
-
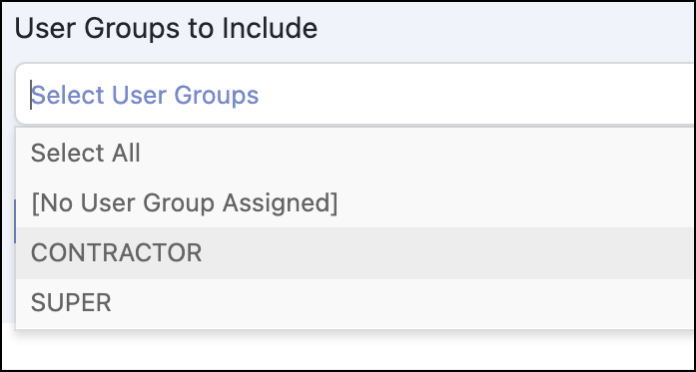
Select the user group(s) to include in the reviews. For example, you may have contractor and super user groups you can select.
-
Use the Only include changes since dropdown menu to create a review that only includes the changes since a previously completed review. Items from previous reviews will appear in the review but will be populated with the response from the last submitted review. This allows reviewers to consider previous decisions when choosing a response.
-
Select the roles to exclude from the review:
- Emergency Access Roles - These roles can be excluded from most access reviews since there is a separate workflow and control process in place for emergency access, and they do not represent a user's typical access. If you want to detect whether a user happens to have elevated access during the review timeline, then don't exclude these roles.
- Standard User Roles - These roles are often excluded because they will be approved every single time since all users must have this role. Excluding them reduces the time it takes to complete the review. It also minimizes the chance of reviewers accidentally rejecting the role assignment and having to add the role back to the user to correct the error.
-
Select the Hide Blank Columns checkbox to exclude any columns that contain no data from the view.

-
Select the Enable Group Approvals checkbox to enable reviewers apply the same decision to all access for an individual user or all the users with a role (instead of being required to review each individual item separately).
-
Select the Ignore Admin Locked Users checkbox to exclude admin-locked users from the access review. You can tell if a user has been admin locked if 32 or 64 appear in the PFLAG field. This is based on the table USR02 in SAP.
-
Select the Ignore Failed Login Users checkbox, to exclude users who are locked due to failed login attempts from the access review. These users are usually included based on the assumption that they will successfully reset their password and have access again soon. The determination is based on the SAP table USR02 for users with the value of 128 in the field PFLAG.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.