Online User Reports
User-based reports provide summary and detailed views of the risks associated with user privileges and actions.
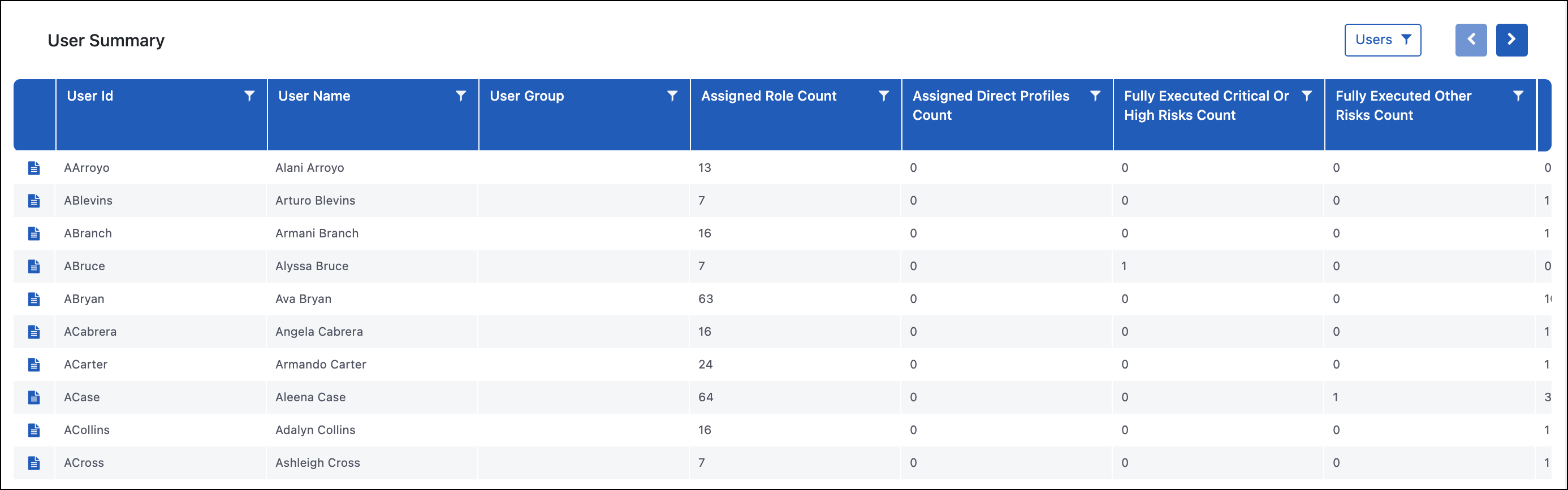
User Summary
Purpose
The User Summary report provides a breakdown of all the active users in the system and key data points for the risks associated with the users. These include the number of roles that are assigned, the number of risks users have access to, and how many of those risks have been executed. Report viewers can also drill down for specific users to review the User Risk Level Details and User TCode Level Risk Details reports and User Remediation.
Use Case
The User Summary report is generally used to identify which users to target during remediation projects. Many organizations prioritize the most impactful changes first, which can include users that have access to high-risk conflicts and/or are executing those risks on both sides so there is a potential of inappropriate activity having occurred.
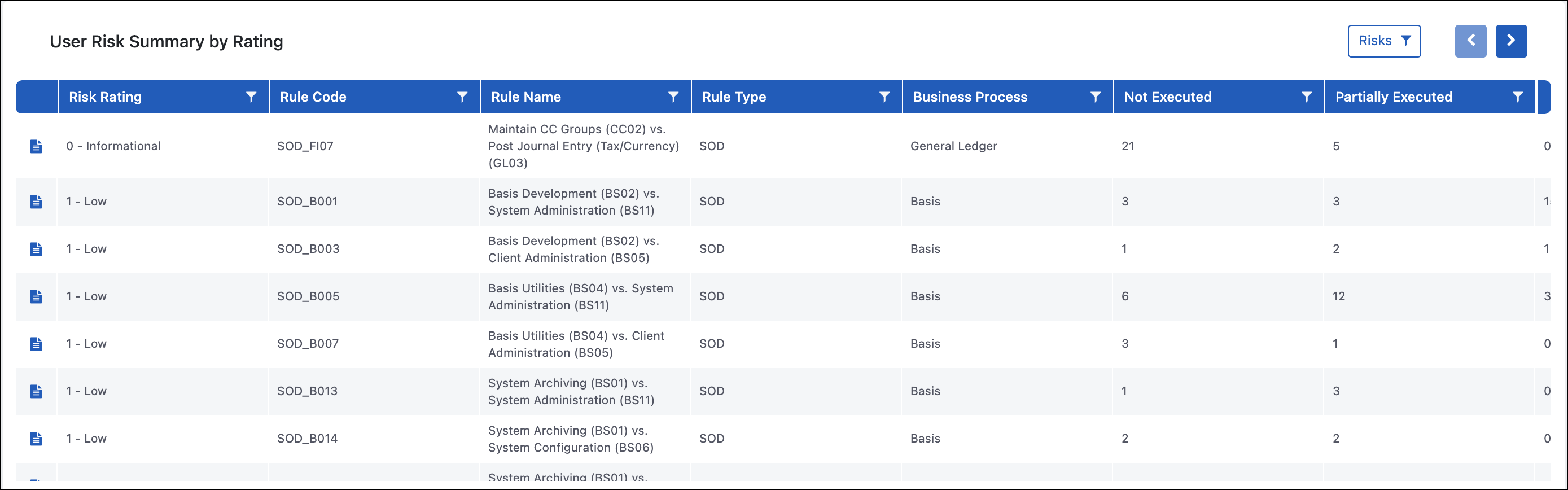
User Risk Summary by Rating
Purpose
The User Risk Summary by Rating report focuses on the risks in the environment. This summary shows all the risks in the system, information on how many users have access to that risk, and whether there have been executed transaction codes associated with the risk. Report viewers can drill down to the User Risk Level Details or User TCode Level Risk Details to see the users who have access to these risks.
Use Case
The User Risk Summary by Rating report is used by organizations to help identify what risks they want to focus on first with remediation efforts. A common approach is to go after high-risk conflicts first, and then within the high risks, they might choose to look at those that are being executed at the highest rate since that will likely be a more complex remediation effort.
User Risk Level Details
Purpose
The User Risk Level Details report shows all of the risks within the system and the users who have access to those risks. Additional information included is related to the risk, such as Risk Name, Risk Rating, and Risk Description, along with utilization information.
You can see summary-level details on the total transaction codes executed by the user for each of the business functions associated with the risk. Since each business function can contain multiple transaction codes, you will want to access other reports to see the specific transaction codes that are being executed.
The drill-down options from this report are the User TCode Level Risk Details, User Authorization Object Level Hit Details, User Remediations, and Execution Summary for that particular risk and user.
Use Case
This report is often used as a starting point when reviewing the specifics of a risk that a user has access to. The utilization bucket contains key data points used to pick what risk and user to examine.
A common scenario is to review a risk that is being executed on both sides and the summarized utilization. The summary-level utilization data can pinpoint if there are scenarios in which a user is using one function significantly more, so maybe you want them to keep that access but find someone else to take over responsibilities for the other function. In other situations it may be evident that someone is using both functions evenly, in which case you might want to look at applying mitigating controls if there is no way to remediate the risk.
Once you identify the specific user and risk you want to review, you can drill down into the more granular reports to view the transaction codes and authorization objects to which user has access to help make decisions on risk.
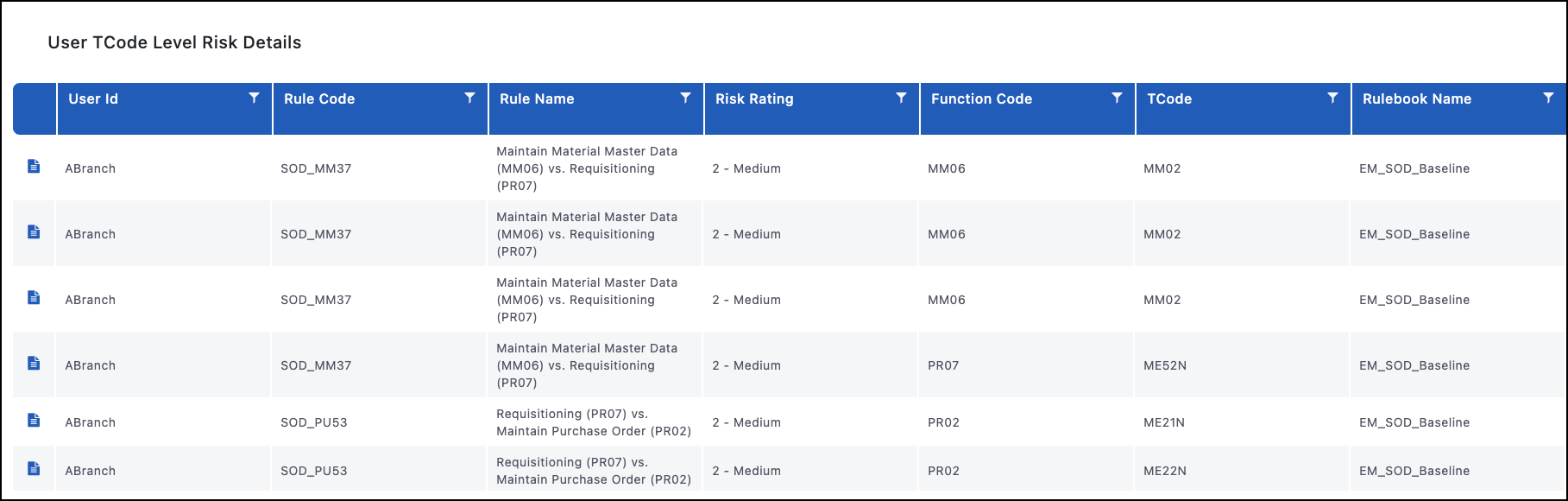
User TCode Level Risk Details
Purpose
The User TCode Level Risk Details report provides a granular view into what is causing a user to have access to a risk. Some things you will be able to identify on this report are the user, what risk they have access to, what transaction codes they have access to from each side of that risk, how many times they have executed each transaction code, and what role(s) gave them access to that transaction code. This report allows you to drill down further to the User Authorization Object Level Hit Details, Role Member TCode Executions, and User Remediations.
Use Case
Once you identify a specific risk to review for a user, this report shows details around that risk to assist decisions. Understanding what transaction codes a user has actually executed and where that access is coming from provides insight into how to deal with the risk either through remediation or mitigating controls assignment(s).
Another possible use case is for organizations to review their Display Only roles. If a transaction code appears in a role marked as display-only, additional investigation is recommended. In this scenario, you will use the User Authorization Object Level Hit Details report to identify if the role is giving additional authorizations or if that user is getting them from other roles or transaction codes. Since SAP has more transaction codes than authorization objects, this cross-pollination of authorizations is not uncommon.
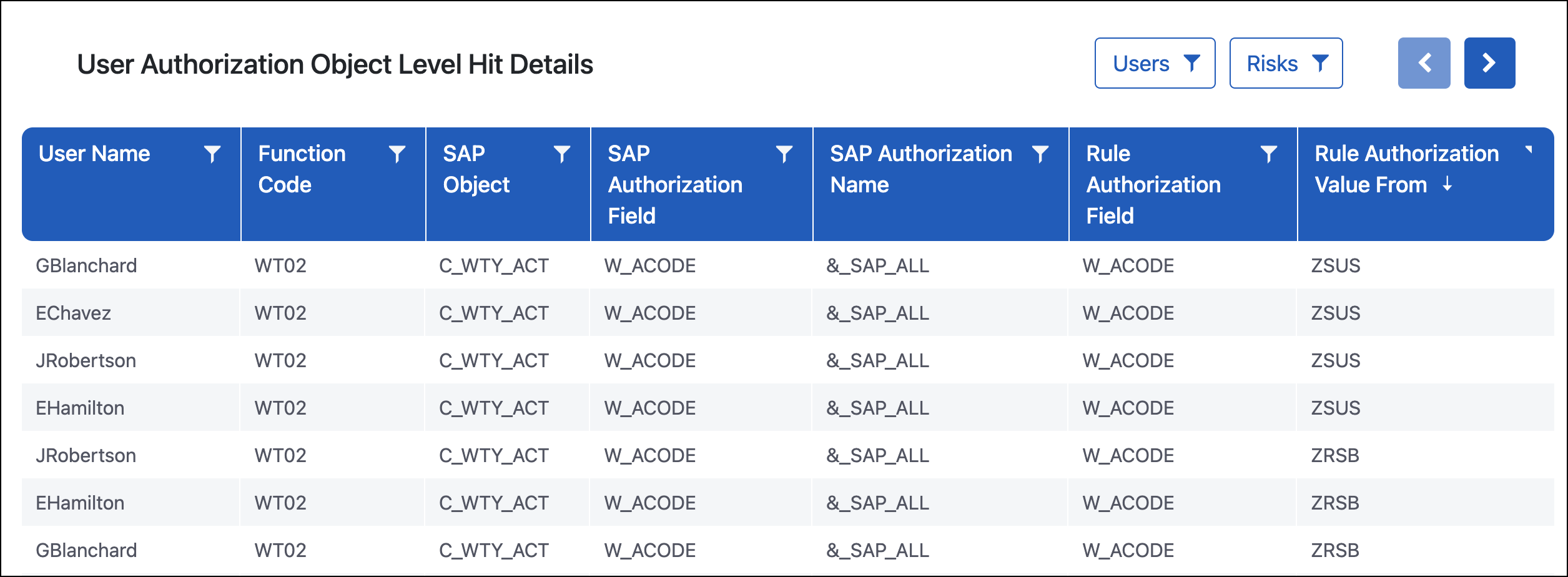
User Authorization Object Level Hit Details
Purpose
The User Authorization Object Level Hit Details report drills down to the most granular layer of security role data. This report shows every authorization object to which the user has been assigned (shown in the columns starting with SAP) compared to the access searched for in the rulebook (shown in the columns starting with Rule).
Use Case
This report is heavily used to understand why a user has access to a risk. A common findings is that a transaction code associated with a risk is coming from a Display Only role on the User TCode Level Risk Details report. This may look like a false positive, however, there are two possible explanations that this report can help identify:
-
The Display Only role is giving more than display access. This will be clearly indicated when you go to this report since the same role will appear throughout the Role Name column.
-
The transaction code is coming from the display role and the create or change authorizations are coming from a different role the user has assigned. Since there are more transaction codes in SAP than there are authorization objects, this cross-pollination or sharing of authorizations is common. This is identified because you will see the different roles giving access in the Role Name column.
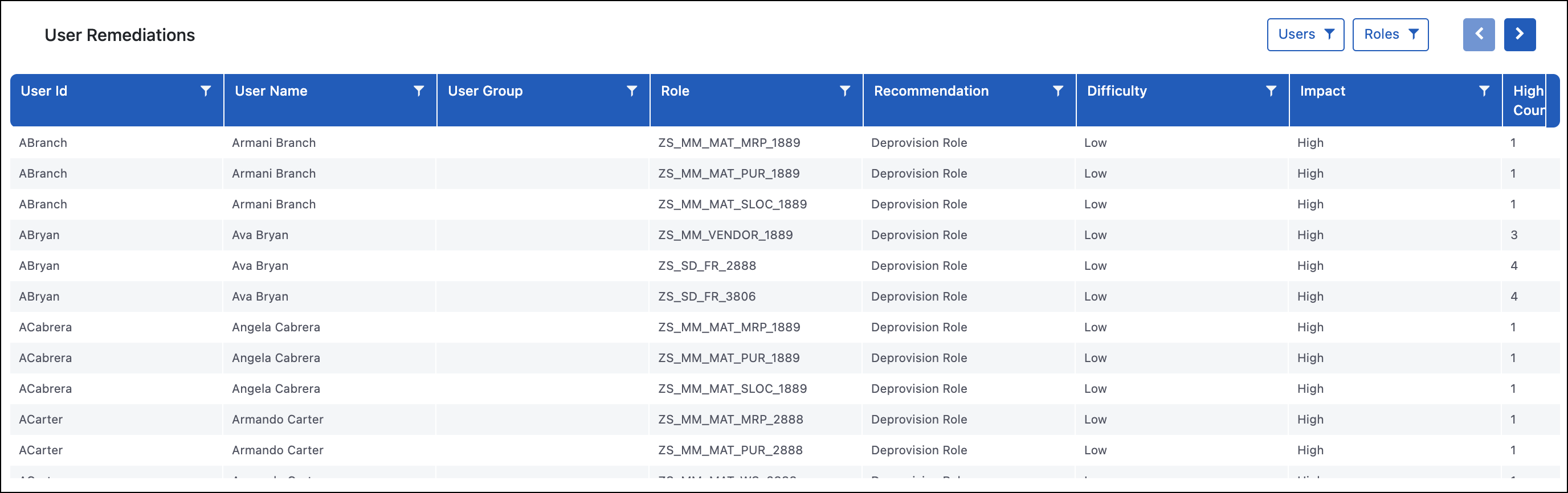
User Remediations
Purpose
The User Remediations report is used to reduce risk in the system by identifying what roles users have assigned but are not utilizing. The report indicates if any of the transaction codes associated with the access has been executed. This report also identifies how many risks are associated with that role and how many of those risks fall into the High or Critical risk rating.
Important
If a risk is on this report, it simply means that a transaction code in the role is associated with a business function. It does not mean that there is an inherent risk in that role, so this report is a good first step to removing unnecessary access in the system that has the potential for that risk.
Use Case
Organizations use this report when doing an initial cleanup or periodic review to ensure users do not have unnecessary roles that they are not using. Since only the utilization stored in SAP is initially imported to Access Risk Management, which is generally three months, organizations should allow some additional months to collect utilization data and then remove the roles that are not being used. If the end goal is reaching a state of least privilege, this is a common first step to reducing the unneeded access in SAP.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.