Reviewing and Approving Access
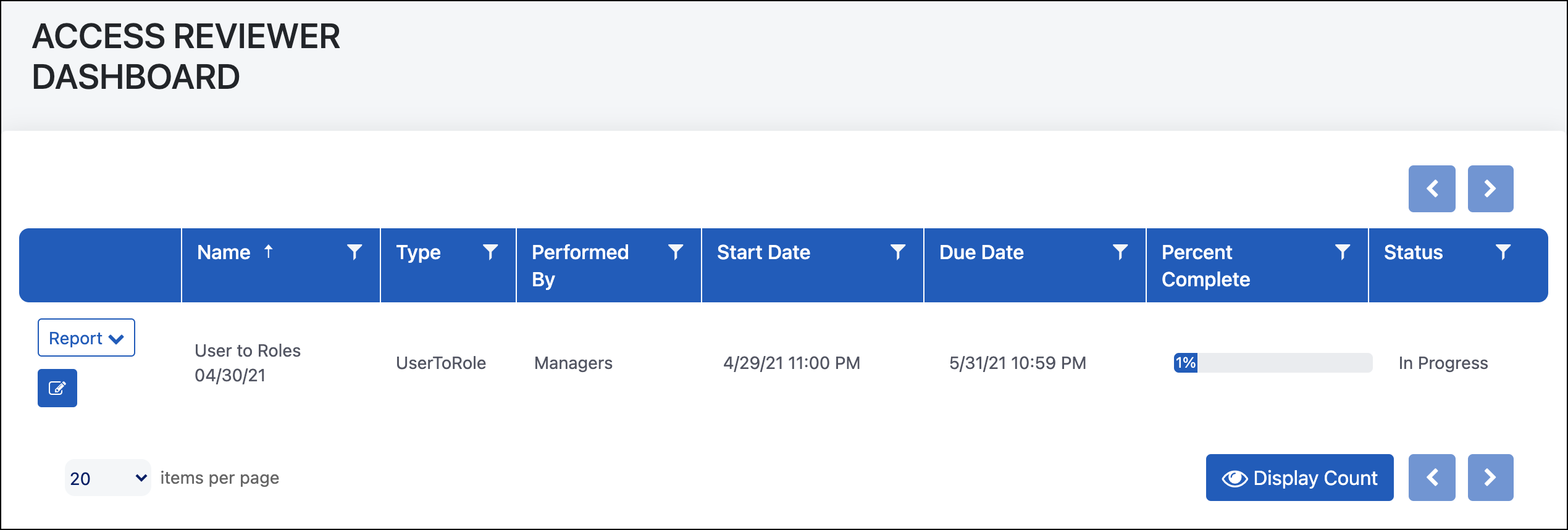
Reviewers can access the review by selecting the link in their email or
by selecting ACCESS REVIEWER > REVIEWER DASHBOARD and
selecting the Review icon ![]() .
.
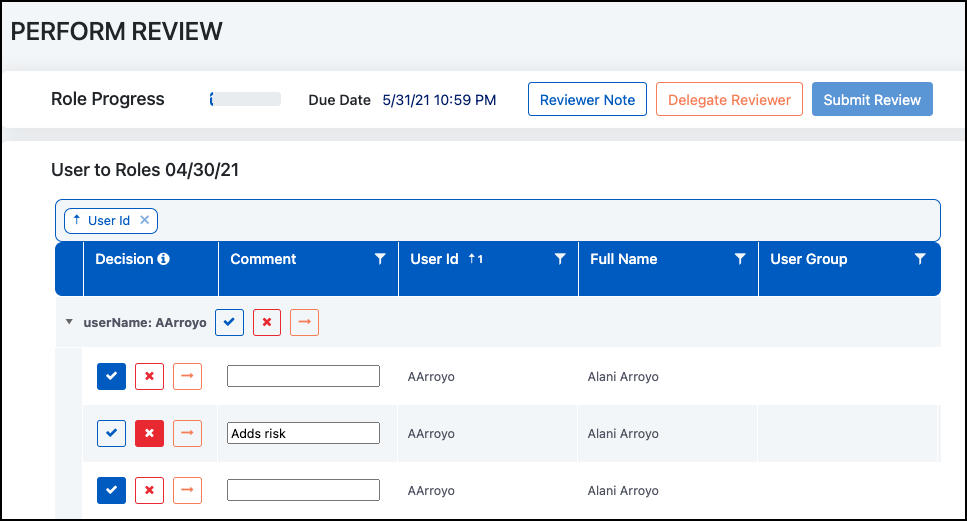
When reviewing access, reviewers can choose from the following options:
-
 Approve the access
Approve the access -
 Reject the access. When
rejecting an item, the reviewer will be required to fill in the
comment field with a reason.
Reject the access. When
rejecting an item, the reviewer will be required to fill in the
comment field with a reason. -
 Delegate the review of a specific
access item. When delegating, the reviewer will be required to
select who to delegate the item to and provide a reason for
delegating it.
Delegate the review of a specific
access item. When delegating, the reviewer will be required to
select who to delegate the item to and provide a reason for
delegating it.
Reviewers can also leave a note about the review or delegate the entire review to someone else.
When a delegated review includes access items that are assigned to the user who has been newly delegated to complete that review, those items will be automatically reassigned directly to an administrator. This prevents users from approving their own access. The admin can choose to review the items themself or redelegate to a different user.
Reviewers will use the information provided to make decisions on access. For example, in the User to Role review, the reviewers may look at the TCodes, TCode usage, and risks associated with each user to decide if their assigned roles are appropriate.
Important
Associated risk is identified by determining if any of the transaction codes in the role are associated with access in a risk. This does not mean there is an inherent risk in the role.
If a role has risk associated with it but no utilization, a reviewer might decide to reject that role since there is risk, and it is not being used. Likewise, if a role has neither risk nor utilization, reviewers might still reject it to follow best practices around least privileged access.
Reviewers will select Submit Review to complete their review. When all reviews are completed, you can generate audit reports or kick off a job to remove all rejected roles.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.