User Reports
User reports show greater detail of risks in the system, users with access to them, and the actions they are taking within risks. You can also refer to the Dormant Users report to view users who have not logged in to SAP within the number of days you select.
User Conflicts Matrix Report
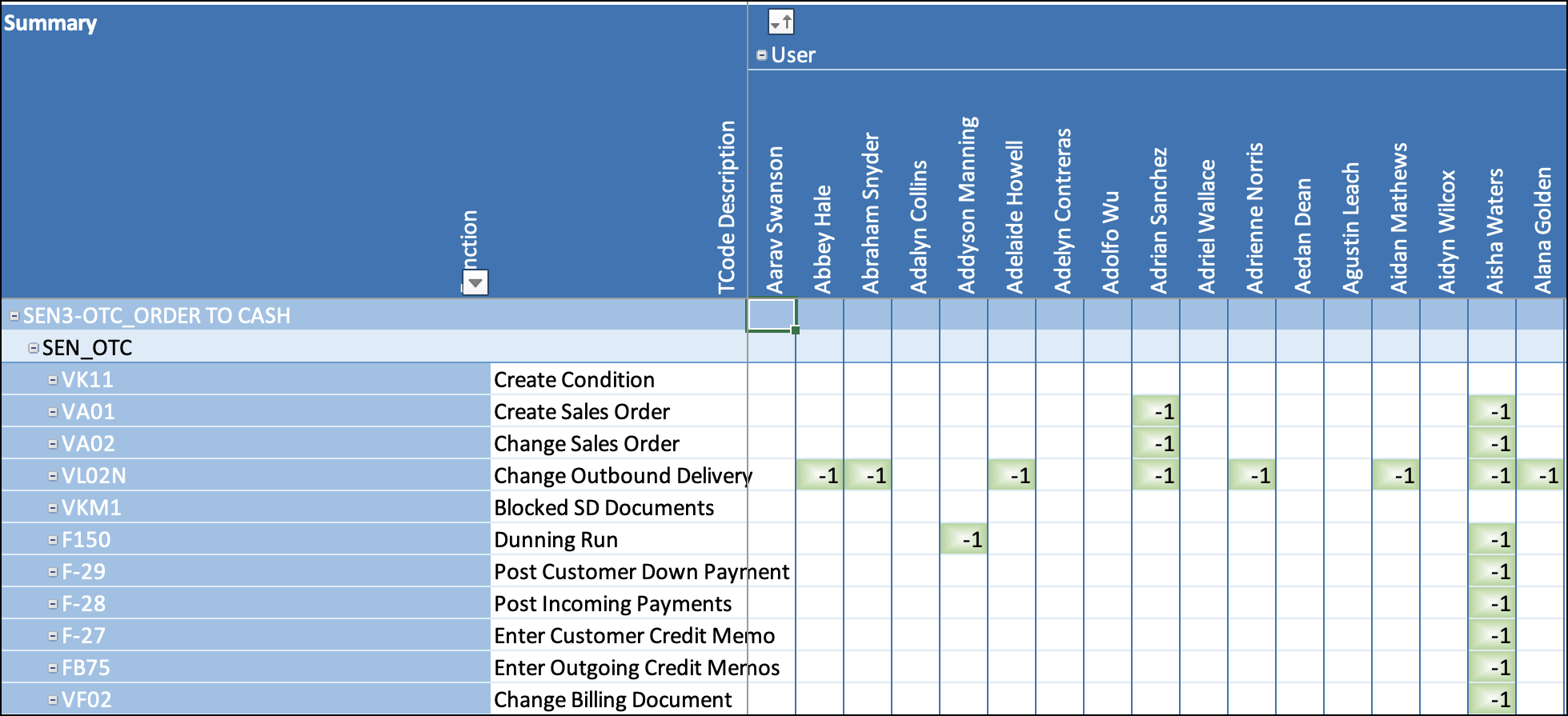
The User Conflicts Matrix report takes the information from the BP Conflicts Summary report and then goes to the next level of detail. Through this report, you can see all the risks in the system, the users who have access, and if they are executing the transaction codes within the risk. This graphical view can help to determine where to focus your time regarding risks and users.
Scheduling the User Conflicts Matrix Report
 When scheduling the User Conflicts Matrix report, the fields that need
to be populated are:
When scheduling the User Conflicts Matrix report, the fields that need
to be populated are:
-
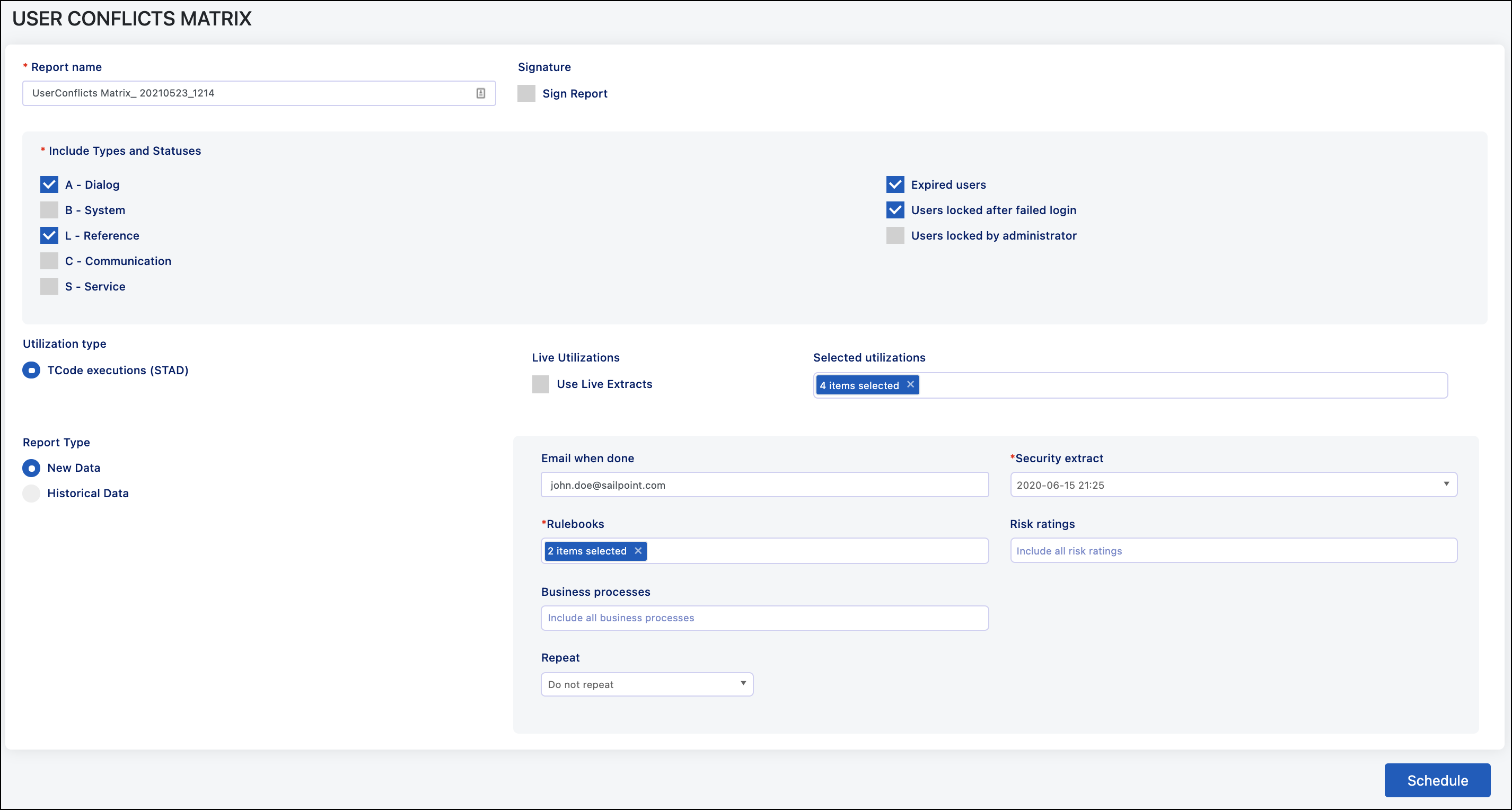
Report Name - Defaults to the report type and date/time but can be customized.
-
User Types and Statuses - Allows you to select what users will be included on the reports. The default settings are to include dialog users and locked users due to failed logins (too many incorrect password attempts). You can also choose to include any other combination of user types and lock statuses.
-
Live Utilizations - If selected, the system will run a new utilization extract for any months missing within the period selected to include. Note that SAP stores this data for three months by default, so you will most likely get blank extracts for months beyond those three.
-
Selected Utilizations - Includes all available extracts from the last 12 months; however, you can include more or less depending on what is available in the system.
-
Report Type - Allows you to select if you want to use a previously completed analysis file, the raw data file that compares user access to the rulebook or run a new one. The options are:
-
Historical Data - You will be provided a list of previously completed analysis files to choose from.
-
New Data - You will run the analysis as part of the reporting job. The additional fields in here are:
-
Email When Done - Email will be sent to this user once the job completes. This will default to the person who is running the job.
-
Security Extract - Select whether to use a new security extract or run the analysis from an existing extract.
-
Rulebooks - Select what rulebook(s) to include in the analysis.
-
Risk Ratings - Select what risks to include in the analysis based on the risk rating.
-
Business Processes - Select what risks to include in the analysis based on the business process.
-
Repeat - You can set up this report to run as a one-time report or recurring monthly basis.
-
-
Viewing the User Conflict Matrix
The Conflict Matrix tab shows the risk at the user level in a pivot table that can be used to identify where the risks are and where you might want to focus your remediation efforts. You can see the business functions that make up the risk, the users who have the access, and if they have executed the transaction codes.
The different colored squares are:
-
Green (-1) - The user has access to this transaction code, and all required authorizations for the rule, but has not executed the transaction code.
-
Red (1) - The user has access to this transaction code, and all required authorizations for the rule, and has executed the transaction code.
-
White/Blank - The user either does not have access to the transaction code or has access to the transaction code but not the required authorization objects.
Double-clicking a square in the table will redirect you to the Data tab with filters applied for the user and transaction code that you chose.
Use Case
This report is used for general reporting purposes and to help identify areas to focus your remediation efforts. Since you do not take transaction codes away from users directly, this is another tool to help focus on specific users, risks, or roles for remediation. With this information, the organization may want to see what roles are giving access and determine if the transaction code can be removed from any of those roles.
Data Tab
The Data tab contains all the information that was used to generate the pivot table from the Conflict Matrix tab. This includes users, risks, transaction codes, the role that gave the transaction code, and utilization data. This can be used to filter through the different risks and see which users have that access and what transaction codes they are using.
Reference Tabs
The additional tabs on the report are for reference purposes. These include:
-
Properties - Shows the information that was used to create the report. This includes the account information, user who scheduled the snapshot, the rulebook used, along with the dates and times of the security and utilization extracts.
-
Risk Descriptions - Shows the risks, risk rating, and description that are defined in the rulebook.
-
Mitigating Controls - Shows the different mitigating controls in the system along with the objective and description defined for those mitigating controls. This is used as reference when you want to know more information about the mitigating control in place for a risk/user since most reports just show the mitigating control code.
Dormant Users Report
The Dormant Users Report shows users who have not logged in to SAP within the number of days you select.
Scheduling a Dormant Users Report
Since the Dormant Users Report does not include an analysis portion or utilization data there are fewer fields needed:
-
Report Name - Defaults to the report type and date/time and can be customized.
-
Security Extract - Select the time you want to use for the test. For this report, you cannot use live data.
-
Days Until Dormant - Define how many days a user has to have not logged into SAP for them to be considered dormant.
Viewing the Dormant Users Report
The Dormant Users report has two tabs:
Users Tab
This shows the usernames and the date they last logged on.
Properties Tab
This shows the information that was used to create the report. This includes the account information, user who scheduled the report, and the date and time of the security extract.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.