Data Access Security Virtual Appliance Cluster Creation
Data Access Security requires the use of virtual appliances to establish connectivity to applications and sources on customer premises within your data centers or your virtual private cloud environment. In addition, it is required to use specialized virtual appliances to perform Data Classification operations for all types of applications.
The following matrix can be used to determine if a virtual appliance is needed and for which component.
| Application Infrastructure | Crawl | Permission Collection | Data Classification | Activity Monitoring |
|---|---|---|---|---|
| Cloud (O365, AWS S3, etc.) | N/A | N/A | Data Access Security - Data Classification Collector | N/A |
| On Premise (Windows Server, Netapp, etc.) | Data Access Security - Resource Collector | Data Access Security - Permission Collector | Data Access Security - Data Classification Collector | Data Access Security – Activity Monitor |
Note
Sources for identity information need to be created in Identity Security Cloud and may or may not require a virtual appliance based on the source. The Data Access Security Identity Collection task relies on these sources to properly associate accounts and entitlements to permissions on the Data Access Security applications.
Important
Based on the type of functionality you plan to incorporate for the connector in Data Access Security (reference table above), select the corresponding virtual appliance cluster component type in Identity Security Cloud.
Crawler Virtual Appliance
In order to take advantage of Data Access Security Resource Discovery within their environments, admins must create a dedicated VA cluster and VAs using the Data Access Security - Resource Collector cluster component.
You can create a dedicated cluster in one of two ways:
- In Identity Security Cloud, follow the steps in Deploying Virtual Appliances and select the Data Access Security - Resource Collector cluster component.
- Use the Data Access Security Application Configuration wizard.
Note
Only on-premise applications require a Resource Collection Virtual Appliance to perform the resource discovery tasks.
-
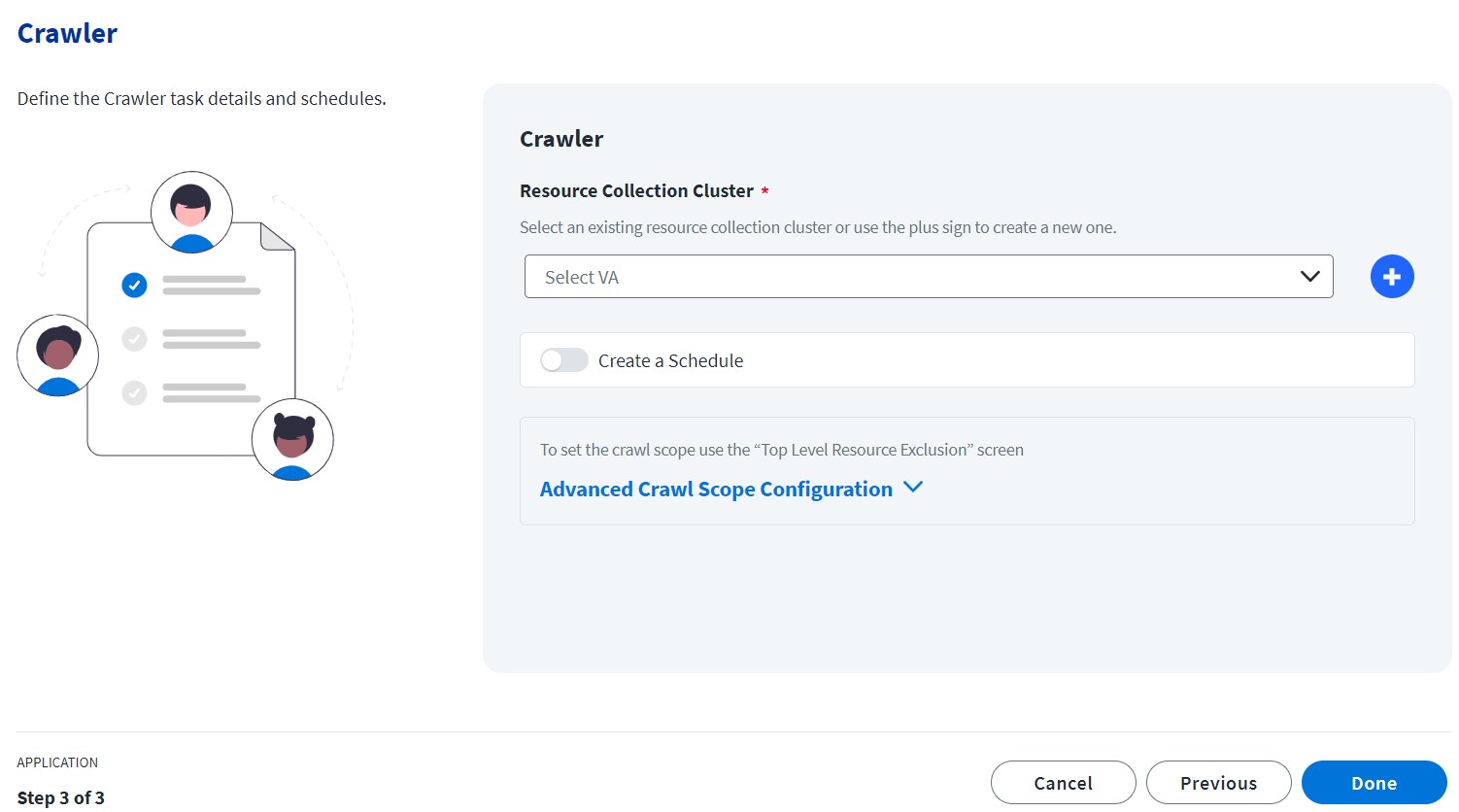
In the Crawler configuration step in the Application Configuration Wizard, use the Resource Collection Cluster dropdown to select an existing one to be used by the applications.
-
If there are no available clusters in the dropdown or if the clusters are being used to capacity and you would like to associate the configured applications to a new cluster, select the plus (+) icon next to the cluster dropdown to add another cluster.
Note
This creates an empty virtual appliance cluster. Make sure to go back to Identity Security Cloud to properly configure the virtual appliance to the cluster. See Virtual Appliance Important Details for more information.
-
A confirmation message is displayed asking you to confirm the operation. Upon approval, a new cluster is created with a default name of “DAS crawler collector cluster.” Subsequent clusters will have a number added to their name to differentiate the ones previously created.
Permission Collector Virtual Appliance
In order to take advantage of Data Access Security Permission analysis within your environment, admins must create a dedicated virtual appliance cluster and virtual appliances using the Data Access Security - Permission Collector cluster component.
You can create a dedicated cluster in one of two ways:
- In Identity Security Cloud, follow the steps in Deploying Virtual Appliances and select the Data Access Security - Permission Collector cluster component.
- Use the Data Access Security Application Configuration wizard.
To get started:
-
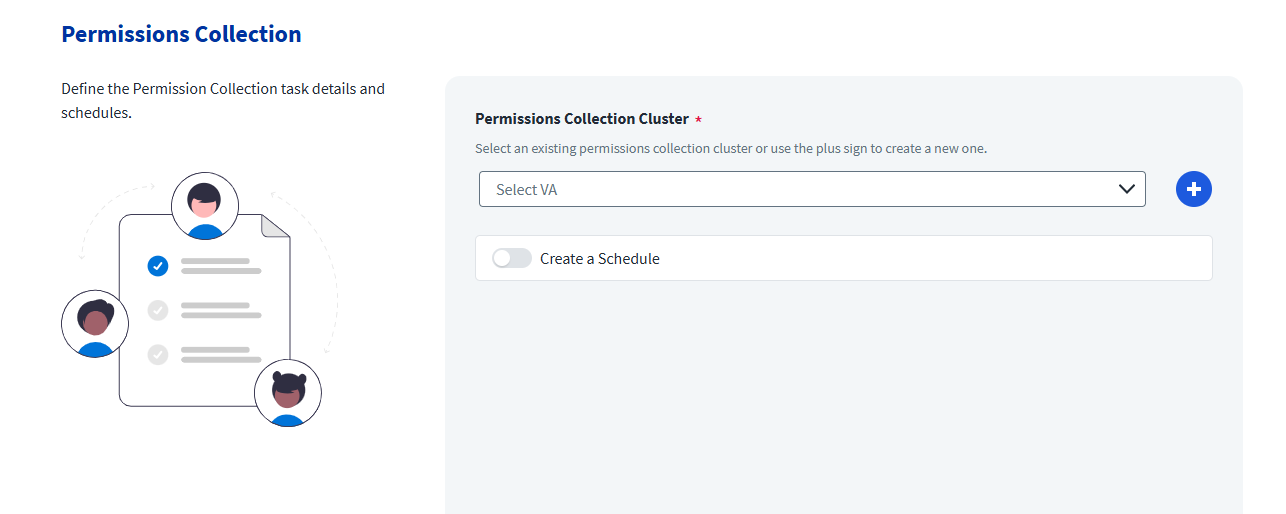
In the crawler configuration step in the Application Configuration Wizard, use the Permission Collection Cluster dropdown to select an existing one to be used by the applications.
-
If there are no available clusters in the dropdown or if the clusters are being used to capacity and you would like to associate the configured applications to a new cluster, select the plus (+) icon next to the cluster dropdown to add another cluster.
Note
This creates an empty virtual appliance cluster. Make sure to go back to Identity Security Cloud to properly configure the virtual appliance to the cluster. See Virtual Appliance Important Details for more information.
-
A confirmation message is displayed asking you to confirm the operation. Upon approval, a new cluster is created with a default name of “DAS crawler collector cluster.” Subsequent clusters will have a number added to their name to differentiate the ones previously created.
Data Classification Virtual Appliances
Data Access Security's Data Classification engine identifies and categorizes data based on data sensitivity, its impacts, and the importance of the data to the business. Data Classification enables organizations to identify business-critical information and “crown jewels”, such as intellectual property, as well as sensitive and regulated data, that need to be tightly governed to comply with regulations.
In order to take advantage of Data Classification within their environments, Admins must create and deploy a dedicated VA cluster and VAs using the Data Access Security - Data Classification Collector cluster component.
You can create a dedicated cluster in one of two ways:
- In Identity Security Cloud, follow the steps in Deploying Virtual Appliances and select the Data Access Security - Data Classification Collector cluster component.
- Use the Data Access Security Application Configuration wizard.
To get started:
-
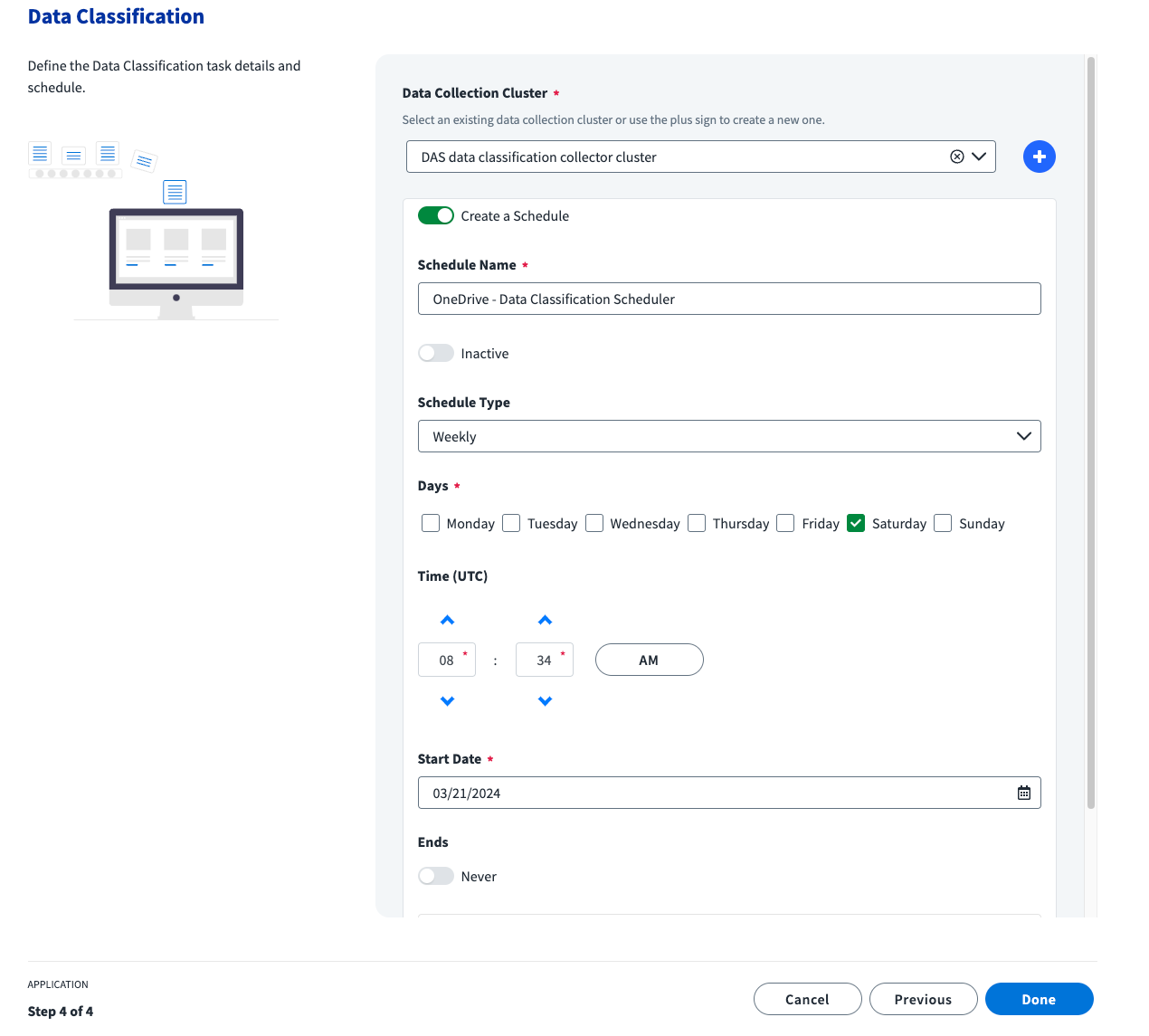
In the Data Classification configuration step in the Application Configuration Wizard, use the Data Collection Cluster dropdown to select an existing one to be used by the applications.
-
If there are no available clusters in the dropdown or if the clusters are being used to capacity and you would like to associate the configured applications to a new cluster, select the plus (+) icon next to the cluster dropdown to add another cluster.
- A confirmation message is displayed asking you to confirm the operation. Upon approval, a new cluster is created with a default name of “DAS data classification collector cluster”. Subsequent clusters will have a number added to their name to differentiate the ones previously created.
Activity Monitoring Virtual Appliance
In order to take advantage of Data Access Security event collection within your environment, Admins must create a dedicated virtual appliance cluster and virtual appliances using the Data Access Security - Activity Monitoring cluster component.
You can create a dedicated cluster in one of two ways:
- In Identity Security Cloud, follow the steps in Deploying Virtual Appliances and select the Data Access Security - Resource Collector cluster component.
- Use the Data Access Security Application Configuration wizard.
Note
Only on-premise applications require Activity Monitoring Virtual Appliance to perform the resource discovery tasks.
-
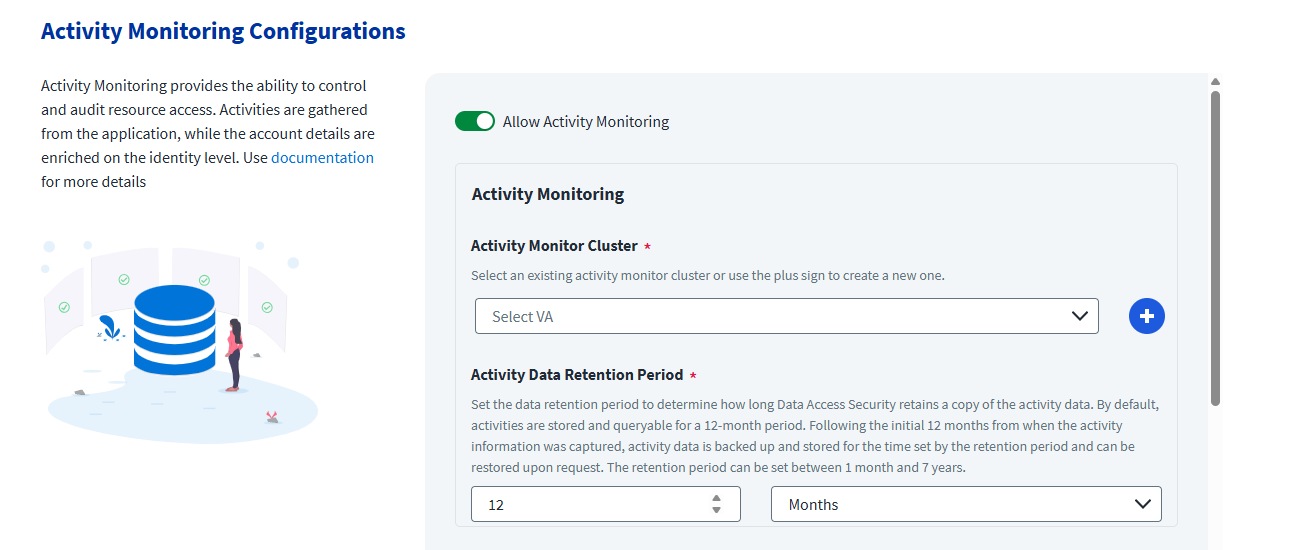
In the Crawler configuration step in the Application Configuration Wizard, use the Activity Monitoring Cluster dropdown to select an existing one to be used by the applications.
-
If there are no available clusters in the dropdown or if the clusters are being used to capacity and you would like to associate the configured applications to a new cluster, select the plus (+) icon next to the cluster dropdown to add another cluster.
Note
This creates an empty virtual appliance cluster. Make sure to go back to Identity Security Cloud to properly configure the virtual appliance to the cluster. See Virtual Appliance Important Details for more information.
-
A confirmation message is displayed asking you to confirm the operation. Upon approval, a new cluster is created with a default name of “DAS crawler collector cluster.” Subsequent clusters will have a number added to their name to differentiate the ones previously created.
Note
Some activity monitoring connectors require the virtual appliance to accept incoming network traffic. See the relevant connector documentation for details.
Virtual Appliance Important Details
Note
Create new VAs to associate them with the Data Access Security VA clusters. Do not associate existing Identity Security Cloud VAs with Data Access Security clusters. VAs cannot migrate across cluster components.
A VA Cluster can contain one or more VAs. We recommend adding multiple VAs to support redundancy and high-availability, as well as scale per performance.
A VA Cluster can service multiple applications and can be associated with one or more applications. There is no need to create a separate cluster for each application, as there is no coupling between applications and clusters.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.