Viewing Permissions
The Permission tab provides four different views on a resource:
- Simple - High level view. Shows who has direct access to what. You can filter the results by the permissions type (menu on the left panel).
- Tree - Gives the view from a resource perspective on the entire resource. Each user within the resource will have a three line menu displayed next to their name.
-
Overexposed - Accessible by everyone or a larger part of the organization. The definition for overexposed can be configured through the Overexposed Resources section within the General tab under Settings. There are three different scope or view types:
- Unique Permissions or Critical Data
- Unique Permission only
- Critical Data only
-
Excess — View users who overlap and have redundant access paths granting similar or excessive permissions to the same resource.
Overexposed View
This screen allows the user to view overexposed resources which are resources that have numerous members.
You can view the following information on this screen:
- The resource path of the selected resource
- The group responsible for the overexposure
- The type of overexposed access
- The data classification categories within the resource
All connected applications display within the left-hand window under the All Application tab. If there are a lot of applications, there are multiple ways to find the desired one.
If you know the application name or application path, use the search bar to locate it.
Use the filter icon in the search bar to select the Search contains resource name option. This option allows the user to fine-tune the search if they know a specific name or phrase in the name of the application.
Under the My Resources tab, a user can see all of the resources they own.
Note
Administrators can view both the All Application and My Resources tabs. Data owners can only view the My Resources tab.
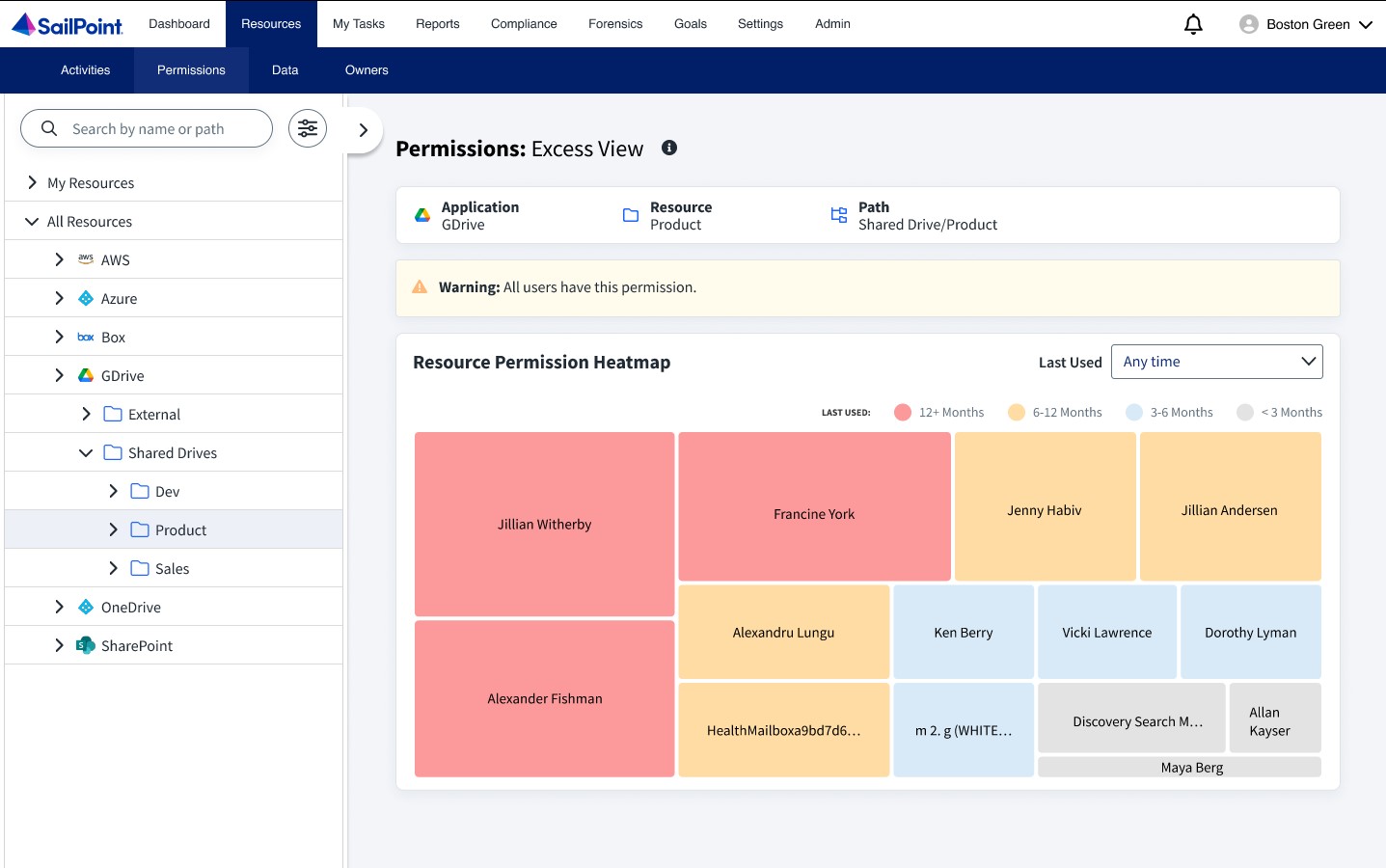
Excess View
This screen provides information on users who have excessive permissions within the organization, such as stale or redundant permissions. The heatmap visually displays these excess access paths for the selected resource.
The size of each block represents the amount of redundant access paths that have been granted or the amount of excessive permissions that the resource has. The heatmap blocks have distinct colors according to the time period they have been unused by the user. The color legend which depicts the level of staleness is at the top of the heatmap.
Additionally, the Excess View screen allows data to be filtered based on permission staleness.
Selecting a block provides the user with a snapsnot of information regarding that resource including user information, the permission count, and the types of permissions granted. For more information on that selected resource, select View Access Paths.
After selecting View Access Paths, you can select between two tabs on the View Details window.
- Permission List – provides the same type of info that was presented when the resource block was selected from the heatmap.
- Access Paths – provides a tree view of the user with all of the access they have. Each colored branch depicts the timeframe that resource was last used.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.