Prerequisites for AWS
To use the Data Access Security AWS connector, you must have sufficient permissions in AWS to create a dedicated IAM user.
Creating Dedicated IAM Users
To configure the connector, you will create dedicated IAM users with the policies and roles needed to allow Data Access Security to access your AWS objects.
-
Sign into your organization’s management account.
-
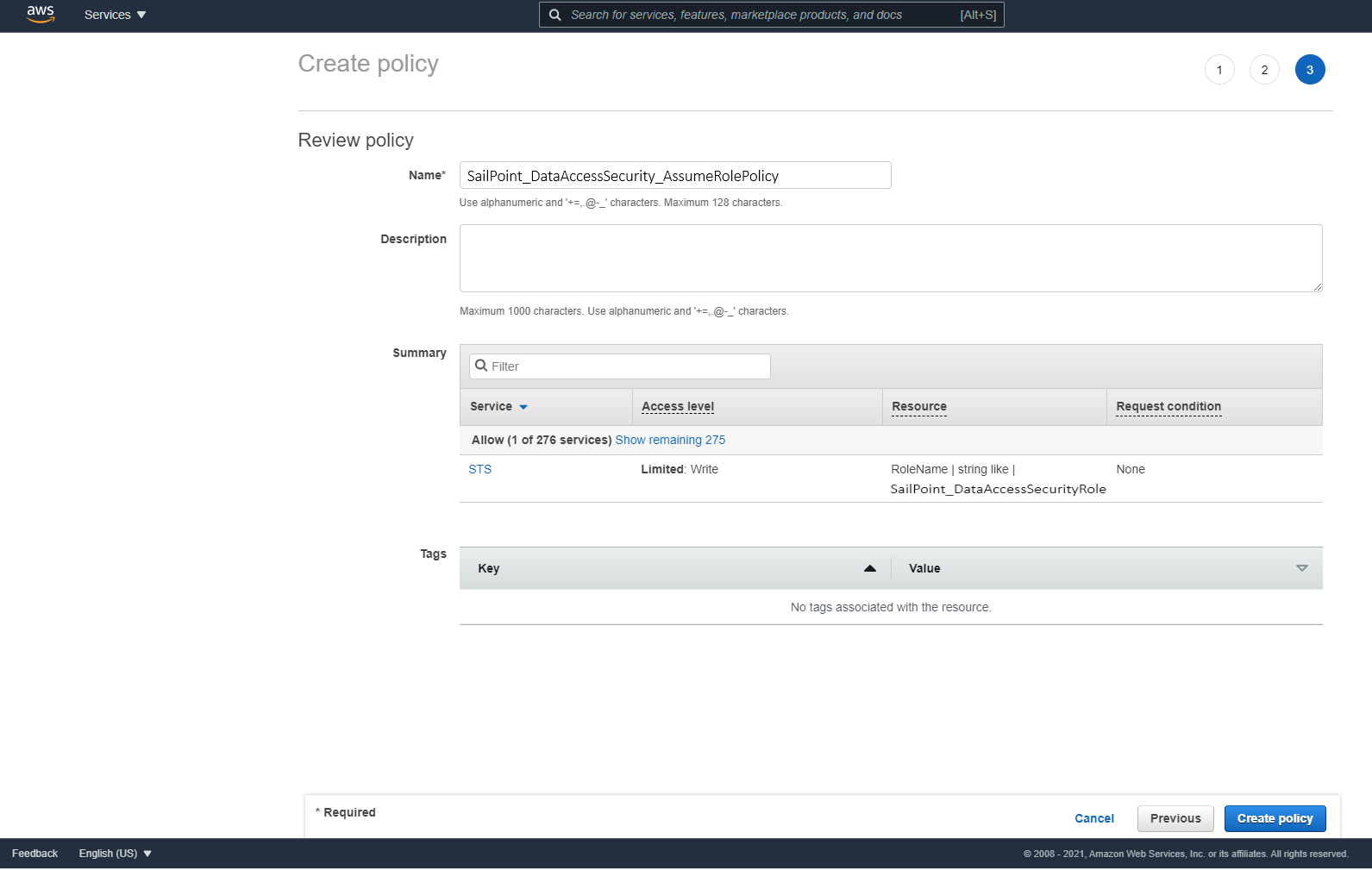
Use the SailPoint_DataAccessSecurity_AssumeRolePolicy.json script to create a policy titled "DataAccessSecurity_AssumeRolePolicy” so the Data Access Security user created in the next step can assume the roles created in each account.
-
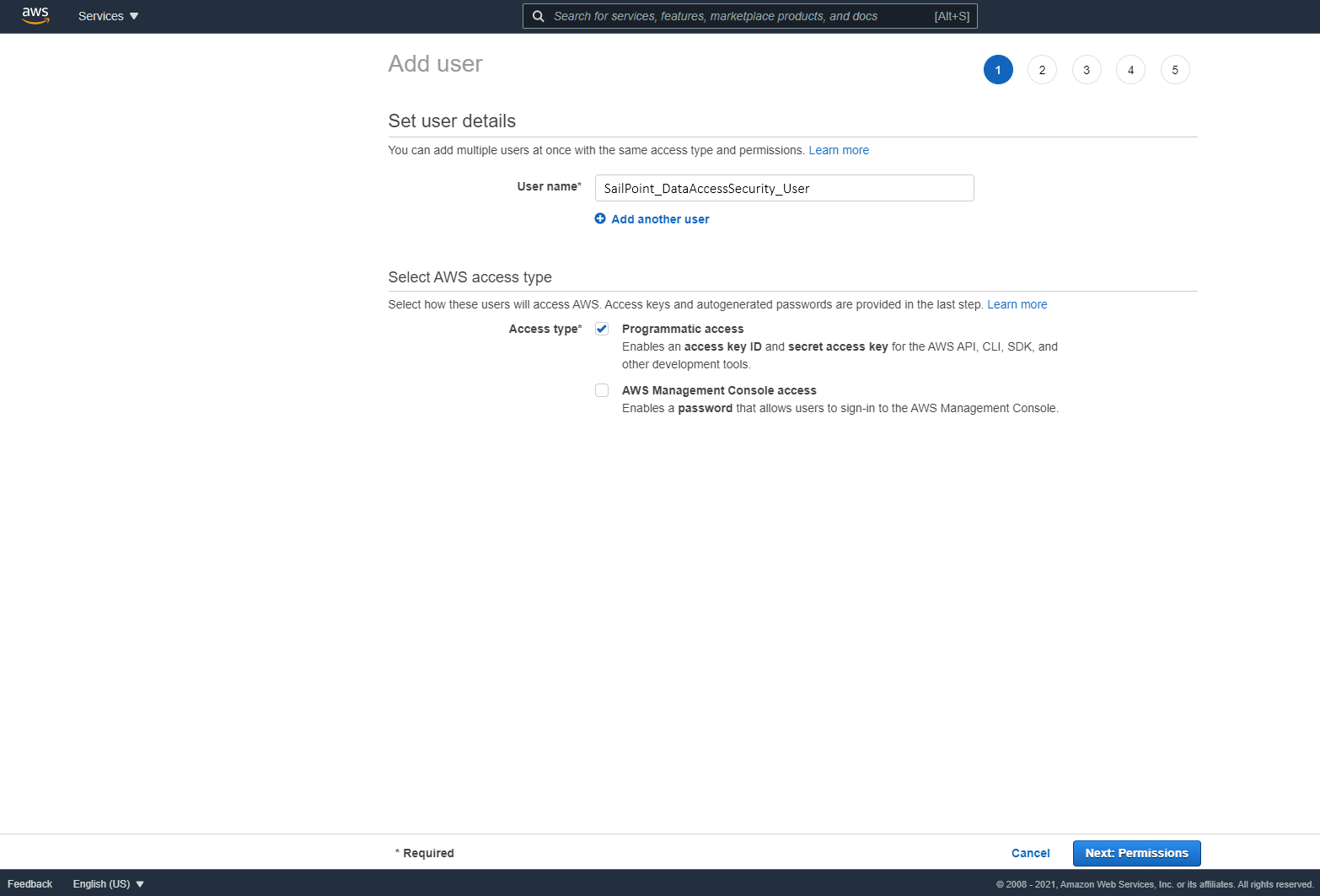
Create an IAM User for Data Access Security and select Programmatic access. This access requires an access key and secret key.
-
Attach the "SailPoint_DataAccessSecurity_AssumeRolePolicy" policy created above to the new user.
Important
Save the generated Access Key and Secret Key in a secure place.
-
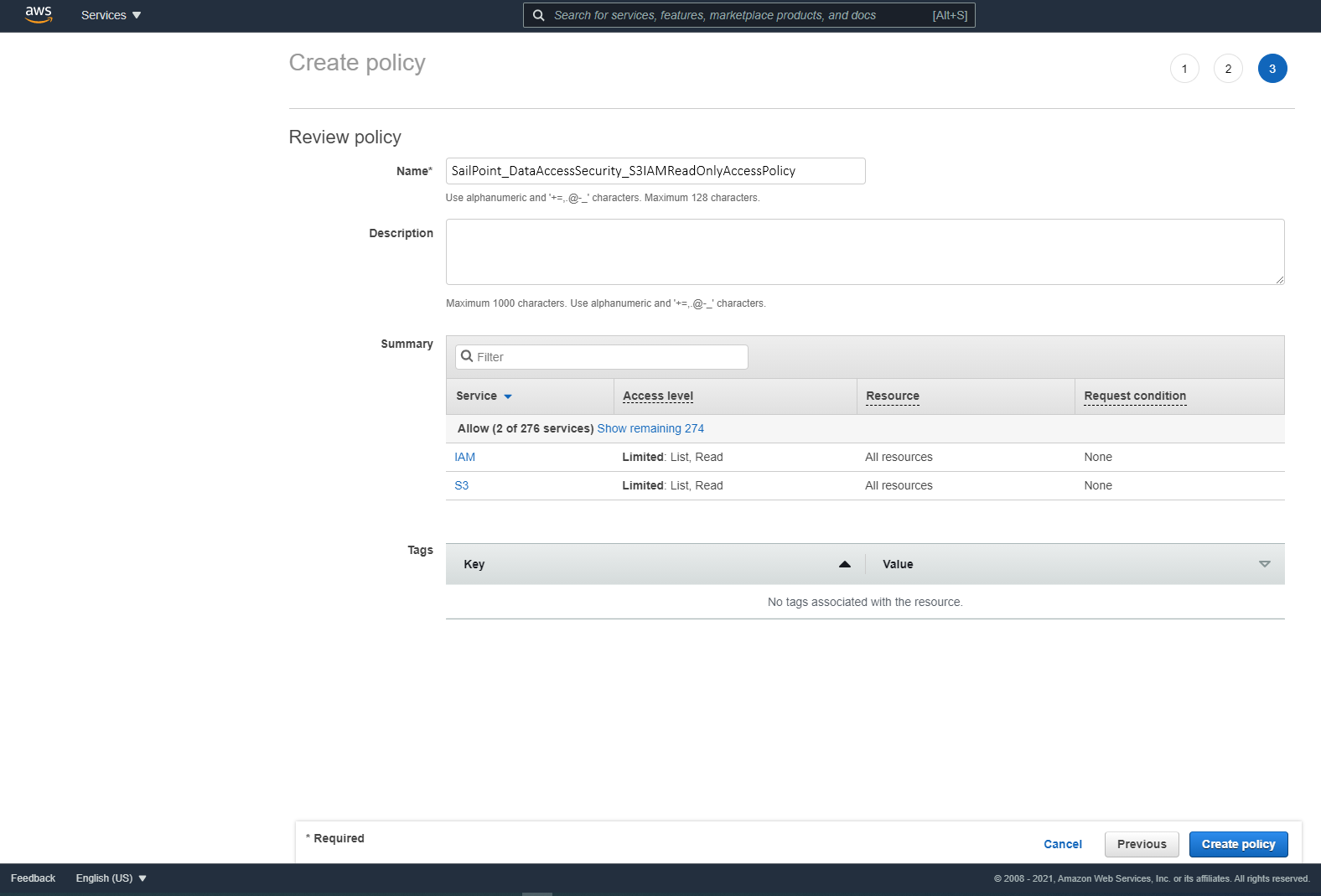
On each organization account the connector should analyze, including the management account, use the SailPoint_DataAccessSecurity_S3IAMReadOnlyAccessPolicy.json script to create a policy titled “SailPoint_DataAccessSecurity_S3IAMReadOnlyAccessPolicy” with the required permissions for the connector.
-
Create a new role titled “SailPoint_DataAccessSecurityRole”, which the Data Access Security user will assume on each organization account the connector should analyze. Select Another AWS Account to enter the user account ID.
-
Attach the "SailPoint_DataAccessSecurity_S3IAMReadOnlyAccessPolicy" policy you created above.
-
Enter the role name SailPoint_DataAccessSecurityRole.
Important
This name cannot be changed.
-
Edit the trust relationship of the new role.
-
Edit the JSON file.
Use the DataAccessSecurity.json (Dedicated User) script and replace
rootin the Principal section withuser/{DAS IAM User username}whereDAS IAM User usernameis the user created above.
Appendix: AWS JSON Scripts
You can copy or download the following scripts to create the roles and policies required to connect AWS and Data Access Security.
Important
Do not change the file names.
Assume Role Policy
Download or copy the SailPoint_DataAccessSecurity_AssumeRolePolicy.json to create a policy defining the roles the IAM user can assume in each account.
S3 IAM Read-Only Access Policy
Download or copy the SailPoint_DataAccessSecurity_S3IAMReadOnlyAccessPolicy.json to create a policy with read-only access to your S3 objects.
Dedicated IAM User-Creation Policy
Download or copy the DataAccessSecurity.json (Dedicated User) script to set the dedicated IAM user who can use the roles and policies you've configured.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.