Working with Sources
Once you have configured a CSP or an IDP, you must register them to manage those sources in Cloud Access Management. You can then view the status of your organization's CSP and IDP accounts by selecting the Sources dashboard tile or Sources in the left sidebar.
Registering Cloud Service Provider Sources
After you have configured cloud service providers with your supported cloud sources, you’ll use the information that you saved during that process to access and govern those cloud sources within Cloud Access Management. When registering or editing your source, Cloud Access Management validates the connection using the provided information.
By default, registering a source includes all your available cloud resources, such as Amazon member accounts and Azure subscriptions. If you only want to include a subset of sources, subscriptions, or projects, you can edit the source later. Refer to Setting Source Scope. To register new CSP sources:
- Select Sources in the left sidebar and choose Cloud Sources.
- Select the tab of the CSP source you want to register.
- Select + New to register a new source.
Registering Amazon Web Services
You can register your AWS source member accounts to be governed by Cloud Access Management. You can choose to register your AWS organizations, or you can select individual AWS cloud sources in environments that are not using the AWS Organizations service.
Use the information generated when you configured Amazon Web Services Cloud.
| Field | Description |
|---|---|
| Unique name | Unique user-generated name to identify this cloud instance. |
| Role ARN | The Amazon Resource Name (ARN) for the role generated when creating a new IAM role |
| ExternalID | External ID generated when creating a new IAM role. |
| CloudTrail ARN (optional) | CloudTrail ARN for an organization or individual member account. |
| CloudTrail Bucket Account ID (optional) | Member account ID of the S3 bucket containing CloudTrail data. |
| SNS Topic ARN (optional) | Accessible if your organization has opted to gather trail data from SNS Topic notifications instead of using a CloudTrail ARN. |
Note
If you enter both an SNS Topic and CloudTrail ARN, Cloud Access Management will use the SNS Topic ARN.
If you have integrated Cloud Access Management with Identity Security Cloud, select the Identity Security Cloud source to correlate to.
AWS Organization CloudTrail ARN
You can use the AWS Console or the command line at the root level to get the CloudTrail ARN for an AWS organization.
Using the AWS Console:
- Go to the CloudTrail page.
- Select Trails in the left sidebar and it will show a table with the organization trail.
Using the command line:
- At the root level, run
aws cloudtrail describe-trails - In the output, identify the section that has
"IsOrganizationTrail": true" - In that section,
"TrailARN"will display. That is your CloudTrail ARN for the AWS organization.
AWS Individual CloudTrail ARN
To get the CloudTrail ARN for an individual member account, run: aws cloudtrail describe-trails --trail-name-list TrailName. Replace TrailName with the name of the trail you created when setting up AWS.
Registering Azure Cloud
Use the information generated when you configured Azure Cloud to register Azure Cloud with Cloud Access Management.
| Field | Description |
|---|---|
| Unique Name | Unique user-provided name to identify this cloud instance. |
| Application ID | Application ID generated when registering Cloud Access Management with Azure Cloud. |
| Application Secret | Client secret created during configuration |
| Azure Tenant ID | Tenant ID shown when registering Cloud Access Management with Azure Cloud. |
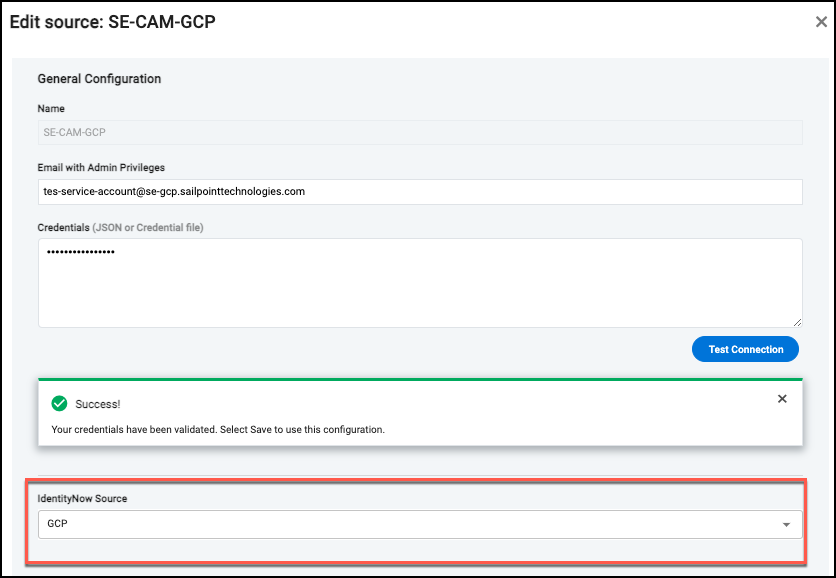
Registering Google Cloud Platform
Use the information generated when you configured Google Cloud Platform to register GCP with Cloud Access Management.
| Field | Description |
|---|---|
| Name Source | Unique user-provided name to identify this cloud instance. |
| Email with Admin Privileges | Email of the administrator for this source, created when you registered your GCP organization with SailPoint. |
| Credentials provided by uploading a file or pasting a JSON | Key generated when creating a service account. |
Correlating Identity Security Cloud Identities
You can connect Identity Security Cloud sources to your cloud service providers in Cloud Access Management. This allows you to correlate your cloud users with corporate identities in Identity Security Cloud.
You will first need to create or edit a source in Identity Security Cloud to use Amazon Web Services, Azure, or Google Cloud Platform. Aggregated accounts and entitlements on that source can be correlated to identities in Cloud Access Management.
To correlate a Cloud Access Management source with an Identity Security Cloud source:
- In Identity Security Cloud, configure and aggregate your source in Identity Security Cloud.
-
Sign in to Cloud Access Management. If you are already signed in to Cloud Access Management, sign out and sign back in to display the source.
-
In Cloud Access Management, select Sources > Cloud Sources.
-
Register a new source, or select Edit on an existing source.
-
Use the dropdown list at the bottom to select the Identity Security Cloud source. Sources are filtered based on CSP. For example, GCP sources in Cloud Access Management will only show GCP Identity Security Cloud sources in the list.
Note
The Identity Security Cloud Source dropdown list only displays if a source can be correlated to that CSP.
Viewing Identity Attributes
To view an identity's Identity Security Cloud attributes in Cloud Access Management, select Identities in the left sidebar to view the list of cloud users.
On the Users tab, select a correlated identity from the Identity column. Only correlated identities are selectable. When you select an identity, its Identity Security Cloud attributes, such as the Identity Profile, Permissions, and Account ID, are displayed.
Updating Correlated Identities
Cloud Access Management tracks and updates identity details whenever an identity is created, deleted, or attributes are changed. Changes to uncorrelated identities are not tracked.
When any of the following attributes are changed in Identity Security Cloud, Cloud Access Management applies that change to the accounts on the correlated source during the next correlation process.
-
Name (username or ID)
-
displayName
-
first name
-
last name
-
lifecycle status
Important
Processed correlations are displayed with the next scheduled or manually triggered inventory refresh.
If a source is deleted or uncorrelated, all entries for that source are removed from Cloud Access Management within 24 hours of deletion/decorrelation.
Managing Cloud Service Provider Sources
After your CSP sources have been registered, you can view and refresh your included sources and set scopes to generate the organization hierarchy.
Expand Sources in the left sidebar and choose Cloud Sources. Select the tab for the CSP you want to view to display its registered source accounts.
Note
If you register a source containing unknown accounts, it will be displayed as an Unknown Source with shadow access. You can view source and networks with shadow access by selecting the Shadow Access tile on the Dashboard.
Refreshing Source Inventory
Your source inventory is the total accounts, subscriptions, and projects registered with Cloud Access Management. It refreshes nightly to keep it up to date with the data in your CSPs.
You can also trigger a manual refresh to update your Cloud Access Management data before the nightly refresh. You may want to do this if you added a source or changed an account's scope. To manually refresh your CSP source accounts, select Refresh inventory in the upper right. This updates all accounts on all CSPs.
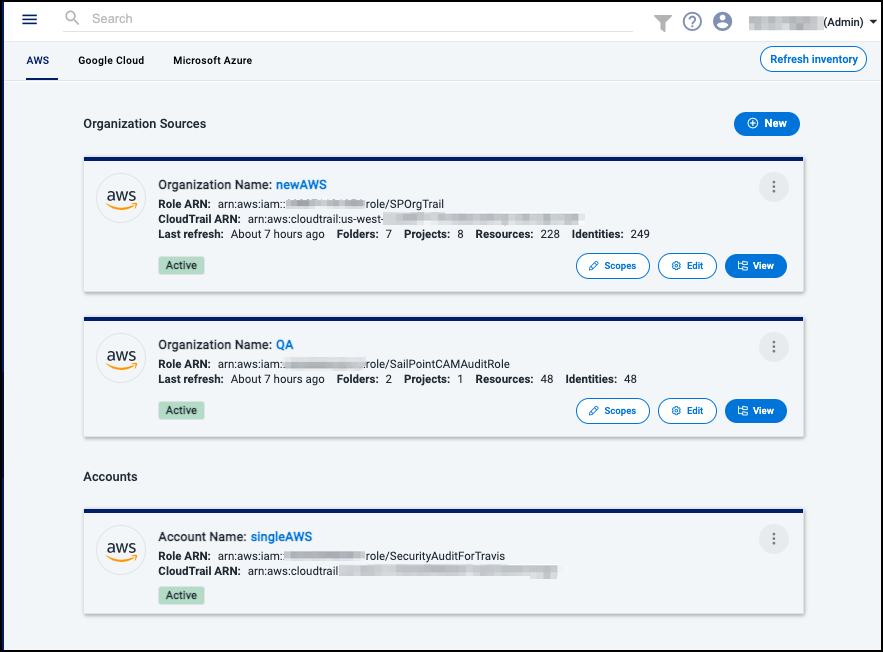
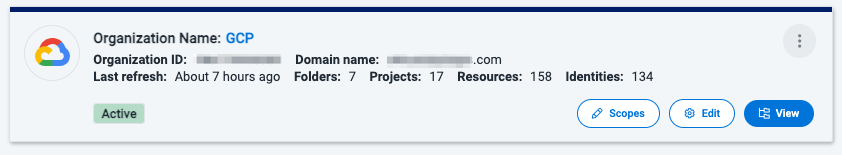
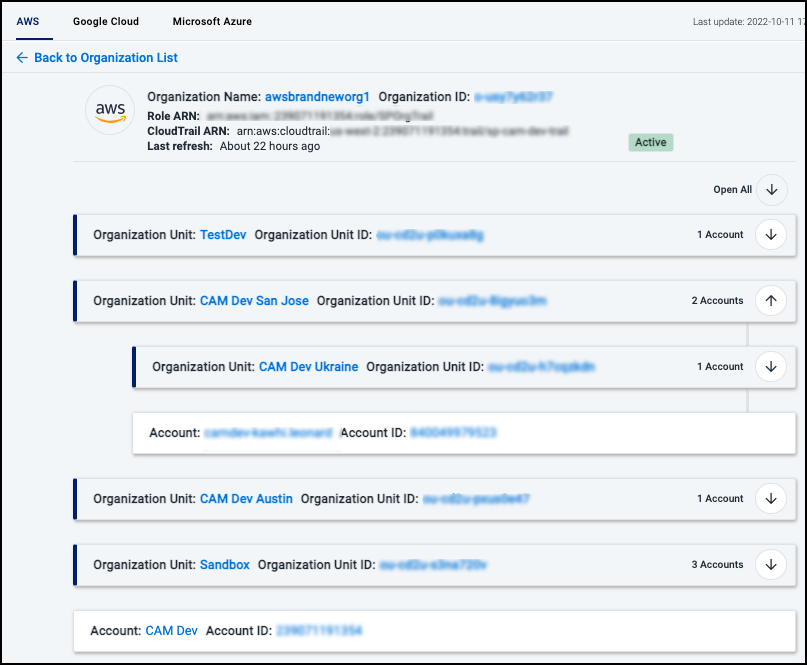
Viewing Source Status
You can view your sources and their names, included objects, and data state.
Each source displays:
-
Identifying information such as the Role ARN or organization ID
-
Time the data was last refreshed
-
Number of folders, projects, resources, and identities in its hierarchy
-
Status of the source refresh
Each of your sources will be in one of these states:
-
Active - The source data are actively being used in Cloud Access Management
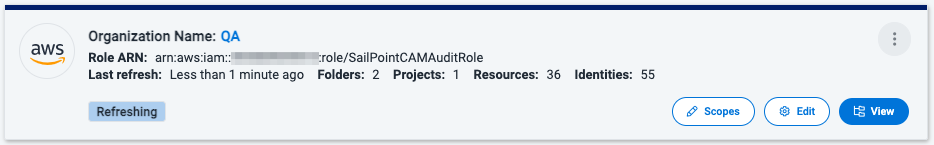
-
Refreshing - The source data are being updated from the CSP
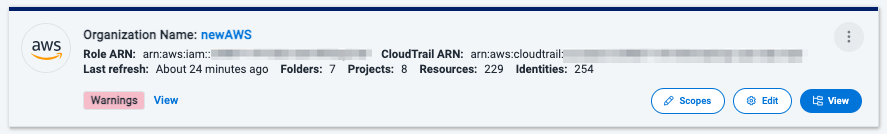
-
Warnings - Errors were found during the refresh, and the source data was not updated. Select View next to Warnings for more information.
When your cloud inventory has successfully refreshed, your sources will display the Active badge.
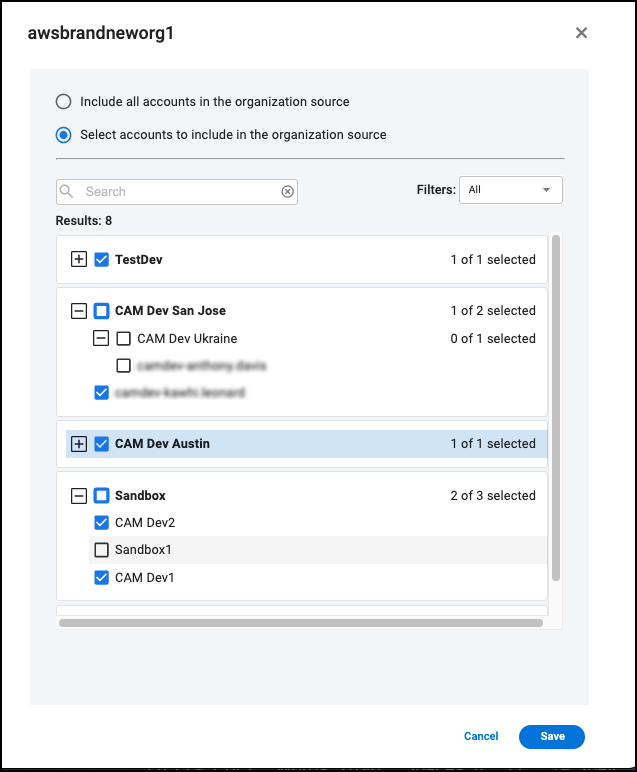
Setting Source Scope
By default, all configured cloud sources are registered with Cloud Access Management. You can edit the source scope to specify a subset of your cloud source hierarchy to include.
To define what is included from that source in Cloud Access Management:
-
Select Scopes on the source.
-
Select the radio button next to Edit accounts.
-
Filter, search, and deselect accounts to exclude from the organization source. You cannot deselect the AWS management account.
-
Select Save to submit your hierarchy changes.
-
Select View in the source to display your updated source hierarchy.
Editing and Deleting Sources
To change your source configuration:
-
Select Edit on the source.
-
Make your changes and select Test Connection to confirm you can connect to your CSP using the provided configuration.
-
Select Save.
To delete a source, select the menu icon
![]() on the right and select
Delete.
on the right and select
Delete.
Caution
When you delete a source, its usage data is removed. If you re-register a source, usage tracking will not include prior data and will begin at the date of re-registration.
Registering Identity Provider Sources
After you've configured identity providers with your supported identity provider sources, you'll use the information that you saved during that process to access and govern those sources.
When registering new IDP sources, Cloud Access Management validates that a connection can be established with the provided configuration information.
To register new IDP sources:
- Expand Sources in the left sidebar and select IDP Sources.
- Select the tab of the IDP source you want to register.
- Select the blue button + Register to register a new source.
Registering Azure Active Directory
Once Azure Cloud is configured, you can register it as an identity provider in Cloud Access Management.
On the IDP Sources page, select Azure Active Directory at the top to register your source using the following fields:
| Field | Description |
|---|---|
| Active Directory Name | Unique user-provided name to identity this IDP instance |
| Directory ID | TenantID in Azure Cloud |
| Application ID | Application ID of the Cloud Access Management application |
| Application Secret | Secret associated with Cloud Access Management. You can find this in the Azure Portal by selecting the SailPoint application in App registration and viewing Certificates & secrets. |
| SAAS Application Cloud Type | Select Amazon Web Services from the dropdown list. |
| SAAS Application ID | Application ID of the AWS application registered with Azure. |
Registering Okta
Once Okta is configured, you can register it as an identity provider in Cloud Access Management.
On the IDP Sources page, select the icon for Okta to register your IDP source using the following fields:
| Field | Description |
|---|---|
| Source Name | Unique user-provided name to identify this IDP instance |
| Organization URL | URL where your organization's Okta is hosted |
| Application Token | API token generated by following these directions |
| Application ID | Okta Application ID found by following these directions |
| SAAS Application Type | Select Amazon Web Services from the dropdown list. |
Managing Identity Provider Sources
After your IDP sources have been registered, you can view and make edits to them on the sources page. Expand Sources in the left sidebar and select IDP Sources, then choose the tab of the IDP you want to view or edit. This will show you all of the sources you have registered with Cloud Access Management.
The source status is shown on the left, alerting you to any state changes. Select the menu icon
![]() on the right to edit or delete the source.
on the right to edit or delete the source.
Caution
If you delete a source, Cloud Access Management cannot connect to it and will cease all governance activities immediately. You must re-register the source to resume governing its resources and activity.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.