Using Search Queries and Guardrails
Cloud Access Management can continuously run search queries against the cloud access and activity that it's monitoring to detect common security threats such as data exposure, public objects, shadow access, illegitimate network access, and privilege escalation. These search queries are called guardrails.
Cloud Access Management generates a security access graph of all cloud objects and their access relationships and activities. When a guardrail is enabled, it will continuously search this access graph for alerts that meet the criteria of the search query.
To get you started, Cloud Access Management provides a set of pre-built guardrails. When you're more familiar with the monitoring and alerting capabilities of Cloud Access Management, and the specific types of access and activity your organization wants to detect, you can also use the query language to create custom guardrails.
Using Pre-Built Guardrails
Cloud Access Management provides the following pre-built guardrails to detect some of the most common security threats, so you can begin to experience the benefits of this powerful feature right away.
Select a guardrail category to display its associated rules. For more information, refer to Using Guardrails.
Cross Source Access - These guardrails are designed to detect access across sources or subscriptions, which may indicate illegitimate access to cloud resources.
Data Access - These guardrails are designed to detect accidental or malicious exposure of data in workloads running on a cloud platform.
Privileged Access - These guardrails are designed to detect high-risk privileged access that may pose a significant risk to your cloud infrastructure.
Security Best Practices - These guardrails are designed to detect relationships between objects and identities that may represent security risks, such as cloud instances that are exposed to the public, security groups that are accessible from external networks, and Lambda functions with admin access.
Service Access - These guardrails are designed to detect service identities and sources with highly sensitive admin access that may pose a significant risk to your cloud infrastructure.
Shadow Access - These guardrails are designed to detect access from unknown cloud sources or subscriptions that may indicate illegitimate or "shadow" access to cloud resources.
Building Search Queries
Cloud Access Management's flexible query language enables you to build powerful custom queries that search across all of your cloud service providers. Enter your queries in the search bar at the top. As you type, Cloud Access Management will suggest potential additional query components to make it easier.
When building queries, you can search for identities, privileges, and resources.
After you select the type of object you want to search for, you will use a with- clause to look for the relationship between that object and the secondary object you enter. There are three types of with- clauses that you can use:
- "with-access" - access from identity types to resource types
- "with-attribute" - a supported attribute on the specified object type
- "with-privilege" - privileges are permissions at the resource level. Each resource type has its own list of supported privileges that are defined by the cloud vendor platform, such as read, write, list, describe, create, or get.
Use the built-in keywords to tailor your searches, including:
| "user" | “with-access” |
| "role" | “with-attribute” |
| "read" | “with-privilege” |
| "write" |
Important
Names of cloud object instances that overlap with any built-in keywords and operators will cause conflicts, such as naming a role “with-access”.
Review the following examples to learn how to search for different types of users, roles, resources, privileges, time parameters, and machine identities.
Searching on Users
The most common queries show an identity's access on a specific resource. You'll start your query with the identity type and include a with- clause for a resource type. Queries that show relationships from identities to non-resource types, like users who have access to roles and groups, are not currently supported.
You can search on identities like:
- User
- Group
- Role
- Service_account
The following are some examples for how to search on a user:
| Query | Result |
|---|---|
user with-access azure_key_vault |
Show users with access to any Azure key vault resource instances |
user with-attribute group devops |
Show users who are members of the "devops" group |
user with-privilege microsoft.storage write |
Show users who have the write privilege on any Microsoft storage type of resources |
These queries can be further refined by specifying a name for the user or a name of a resource type:
| Query | Result |
|---|---|
user alex.smith with-access azure_key_vault |
Show if user "Alex Smith" has access to any Azure key vault resource instances |
user QA-Test with-attribute group devops |
Show if user "QA-Test" is a member of the "devops" group |
user james with-privilege microsoft.storage write |
Show if user "james" has write privilege on any Microsoft storage type of resources |
You can also specify a name of a resource type for a more granular query:
| Query | Result |
|---|---|
user with-access azure_key_vault keytest |
Show users who have access to the Azure key vault named “keytest” |
For more complex queries, you can combine multiple with- clauses when querying on users, such as “with-attribute” and “with-access”:
| Query | Result |
|---|---|
user with-attribute group guestusers with-access azure_virtual_machine |
Show users who are a member of the group “guestusers” with access to any Azure VM |
You can use "not" for some types of queries. Adding "not" before "group" in the example above shows users who are not part of that group:
| Query | Result |
|---|---|
user with-attribute not group guestusers with-access azure_virtual_machine |
Show users who are not part of the group “guestusers” who have access to any Azure VMs |
Important
User queries are case sensitive when entering the username.
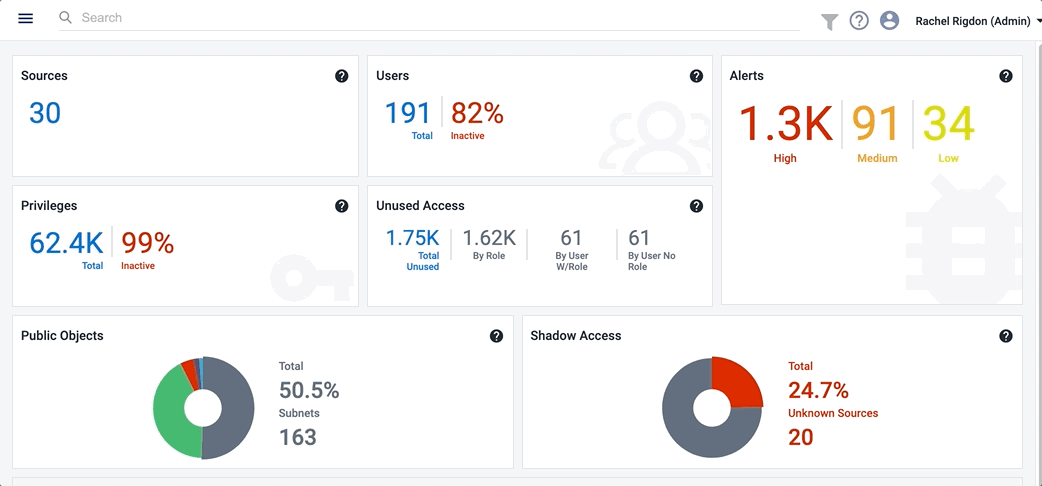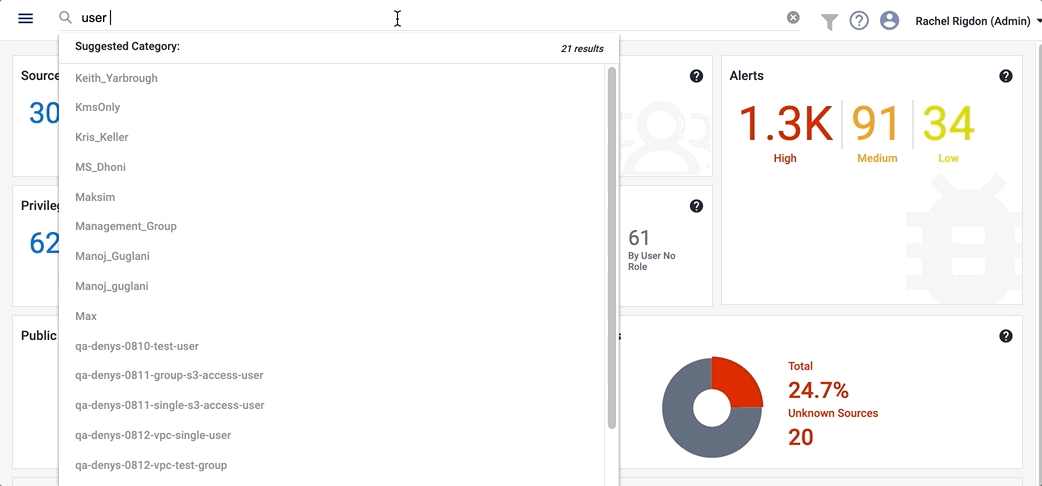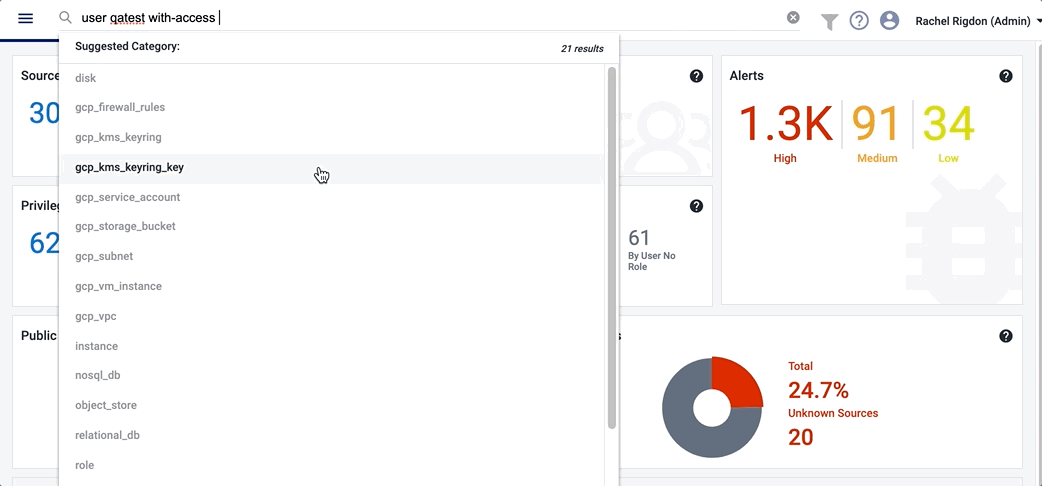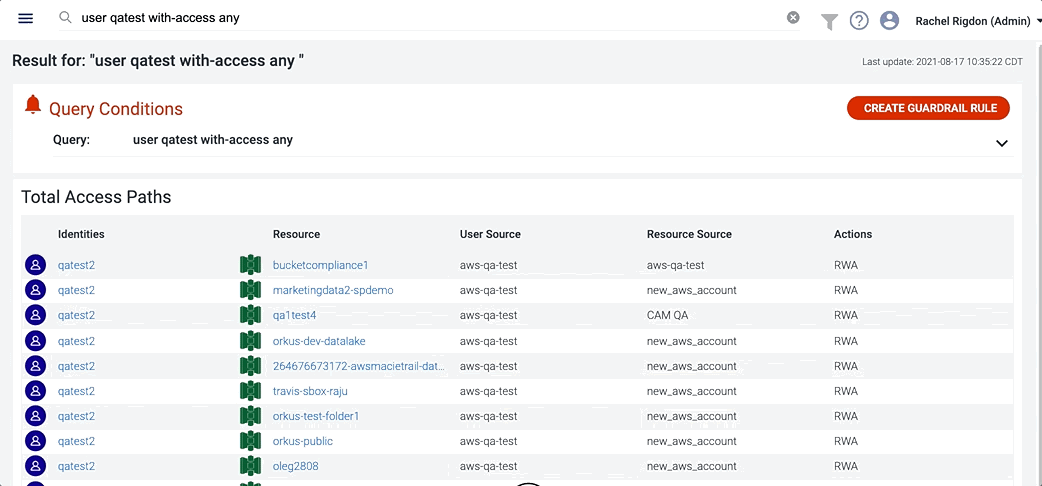
You can combine the “any” keyword with with- clauses, like “with-access any”:
| Query | Result |
|---|---|
User pat.stone with-access any |
Show the cloud access that the user “Pat Stone” has to infrastructure resource objects |
Searching on Roles
Similar to user-based queries, you can build role-based queries like role attribute, role access, or the privileges a role grants.
| Query | Result |
|---|---|
role with-privilege ec2 createsecuritygroup |
Show all roles that have access to the ec2 permission “createsecuritygroup” on any instance |
role projectK with-privilege ec2 createsecuritygroup |
Show if the role “projectK” has access to the ec2 permission “createsecuritygroup” on any instance |
role with-access azure_subnet |
Show roles that have access to any Azure subnets |
role with-access azure_subnet testname/default |
Show roles that have access to the named subnet “testname” |
role with-attribute cloudtype gcp |
Show all GCP roles |
role batchjobs with-access any |
Show the cloud access the role “batchjobs” has |
Note
If you are searching for roles with privilege/permission access, even if a role has access to a particular cloud resource permission, if no objects of that type exist then the query will not return results.
Searching on Resources
The most common use of resource searches is to query on resource attributes. There are fewer query options for resource queries than identity and access types because the with-access clauses do not currently show incoming access to a resource. You can also search on tags, which are attributes on resources.
You can also build searches that show access from a resource to another resource. These types of queries work with hybrid-type services and resources that can act in the cloud as both an identity and a resource, like virtual instances, functions, and other machine identities.
Note
Queries that show relationships from identities to non-resource types, like users who have access to roles and groups, are not currently supported.
To search on cloud resource and service objects, begin your query with the CSP resource type. Cloud Access Management prefixes each supported resource type with the CSP or cloud type name:
- aws_*
- azure_*
- gcp_*
Resource object attributes are made up of native and/or computed object attributes.
-
A native resource attribute on a resource can be an account id, subscription id, project name, tag, etc.
-
Computed attributes are calculated and applied in addition to any native object attributes that are attached. For example, a computed attribute can be which cloud type the resource is part of (cloudtype = aws, azure, gcp) or if the resource has public access open to it (publicrisk).
| Query | Result |
|---|---|
azure_sql_db with-attribute subscriptionid 11e3266a-11b4-4711-803b-11111111111 |
Show all Azure SQL databases that are within the subscription id specified in the query |
gcp_big_query_table with-attribute projectname 1234567890_dev-project-Z |
Show all GCP Big Query table resources that are in the project specified in the query |
aws_s3 with-attribute publicrisk true |
Show the AWS S3 buckets that are open to public access |
azure_storage_container with-attribute publicrisk true |
Show the Azure storage containers that are open to public access |
gcp_storage_bucket with-attribute isencrypted false |
Show the GCP storage buckets that are not encrypted |
azure_storage_container with-attribute isencrypted true |
Show the Azure storage containers that are encrypted |
Tags are a type of attribute on resources, which are represented as key:value pairs in CSPs.
To query on tagged resources, Cloud Access Management prefixes a string “tag-“ to the name of the tag. If, for example, you name a tag in your CSP “department”, it is applied to various cloud resources and will be displayed in the query language as “tag-department”. You can query both for the presence of a tag and on the value of a tag. Here are some sample queries on tags:
| Query | Result |
|---|---|
aws_s3 with-attribute tag-department |
Show AWS S3 buckets that have the tag “department” |
aws_s3 with-attribute tag-department finance |
Show AWS S3 buckets that have the tag “department” and a tag value of “finance” |
gcp_storage_bucket with-attribute tag-qa |
Show GCP storage buckets that have the tag “qa” applied (Google Cloud Platform label) |
Searching on Privileges
Cloud Access Management maps synthetic, or computed, privileges from your CSP platforms to three general categories: “read”, “write”, “admin”. Searching on these categories simplifies finding the summary access a user has without having to analyze a large list of individual permissions across several cloud resources.
Notes
- The “admin” keyword does not refer to an administrative group or role; it refers to cloud permissions with administrative permissions like being able to create and delete.
- The “read” keyword can also represent vendor-specific permissions like “list” and “describe”, as well as “read”, which is a common native permission available on cloud resource types within Azure.
Searching on Time Parameters
You can query cloud access based on time with the “used-in” operator using numbers that represent days. The syntax of using “used-in” is as follows:
{query statement} used-in ( < or > ) [1-90]
The less-than operator shows access within the last number of specified days. The greater-than operator shows that it has not been accessed in more than the number of days specified.
| Query | Result |
|---|---|
{query statement} used-in < 5 |
Show query parameters that have been accessed within the last 5 days |
{query statement} used-in > 20 |
Show query parameters that have not been accessed in more than 20 days |
For example:
| Query | Results |
|---|---|
user with-access aws_s3 used-in < 5 |
Show users who have accessed any AWS S3 bucket within the last 5 days |
user sam with-access aws_s3 used-in < 5 |
Show if user "sam" accessed any AWS S3 bucket within the last 5 days |
aws_s3 used-in < 5 |
Show AWS S3 buckets accessed within the last 5 days |
role with-access any used-in < 5 |
Show any role accessed within the last 5 days |
Note
If your time-based query times out or returns an error, try again using a narrower time frame.
Searching on Machine Identities
Some cloud object types are dual in nature and can act as both a resource type that performs some defined function or service, and as an identity type that can access other cloud resources. These are referred to as machine identities, which include object types like instances, virtual machines, compute engines, and functions. Normally you cannot query on a resource for access to another resource, but these machine identity types are an exception.
These special type of cloud object types can be specified on either the left or right side of a query for reporting on access.
| Query | Result |
|---|---|
azure_virtual_machine with-privilege microsoft.keyvault vaults/delete |
Show any virtual machine instances in Azure that have the admin right to delete key vaults |
aws_lambda functionName with-access aws_s3 |
Show if a specific AWS Lambda function has access to any S3 buckets |
Creating Custom Guardrails from Search
Once you have built your query, you can save those searches to create custom cloud access policies, or guardrails, for your org to monitor. Guardrails continuously search for alerts that meet the criteria of the search query.
Use the following information to create powerful searches and guardrails.
Entering Your Query
-
Select the Search field at the top of the page. If you know your query, enter it here. If you want help building your query, select the Search field and choose a category from the suggested list that appears when you type.
Tip
To display more category suggestions, select the Search field and press Space on your keyboard. This displays the next set of suggestions that are relevant to your previous selection. You can continue to press Space to display more suggestions.
-
Enter or select your query categories until you are satisfied with the results and then press Enter (or Return for MacOS) on your keyboard to run the search query. Results that match the search criteria will be displayed in the table below.
-
If you want to further refine your search, select the down arrow in Query Conditions. Select ADD and REMOVE to change the IF conditions of the query. Select EXECUTE to display the new results.

Note
All autocomplete queries that include the pattern
used-in <1-90>will return a maximum of 1,000 records. Create a more specific query to avoid returning an incomplete data set.
At any time, you can filter your searches by cloud source. Select the Filter icon ![]() to the right of the Search field and choose the cloud source within which you want to search. Select APPLY NOW. To search across all of your cloud sources, select the Filter icon
to the right of the Search field and choose the cloud source within which you want to search. Select APPLY NOW. To search across all of your cloud sources, select the Filter icon ![]() again and select RESET ALL.
again and select RESET ALL.
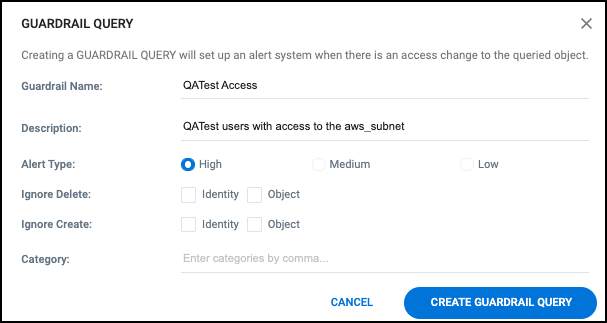
Creating Guardrails
-
After running the search query, select the large red CREATE GUARDRAIL RULE button to the right of the query.
-
Enter a unique name and description for the guardrail query.
-
Specify the type of alert you want the guardrail to generate if the query conditions are met.
Note
The level of severity you choose will impact how guardrail violations are displayed on the Compliance dashboard, as well as whether or not alerts are sent.
-
To help reduce potential "noise" generated by a guardrail, you can optionally configure it to ignore, delete, or create actions on identities and/or objects that would otherwise be detected by the query.
-
To associate the query with a search category, enter one or more labels in the Category field (separating multiple entries with commas). A folder icon is created for each category you enter, and the current guardrail is associated with each category.
-
Select CREATE GUARDRAIL QUERY to save the guardrail.
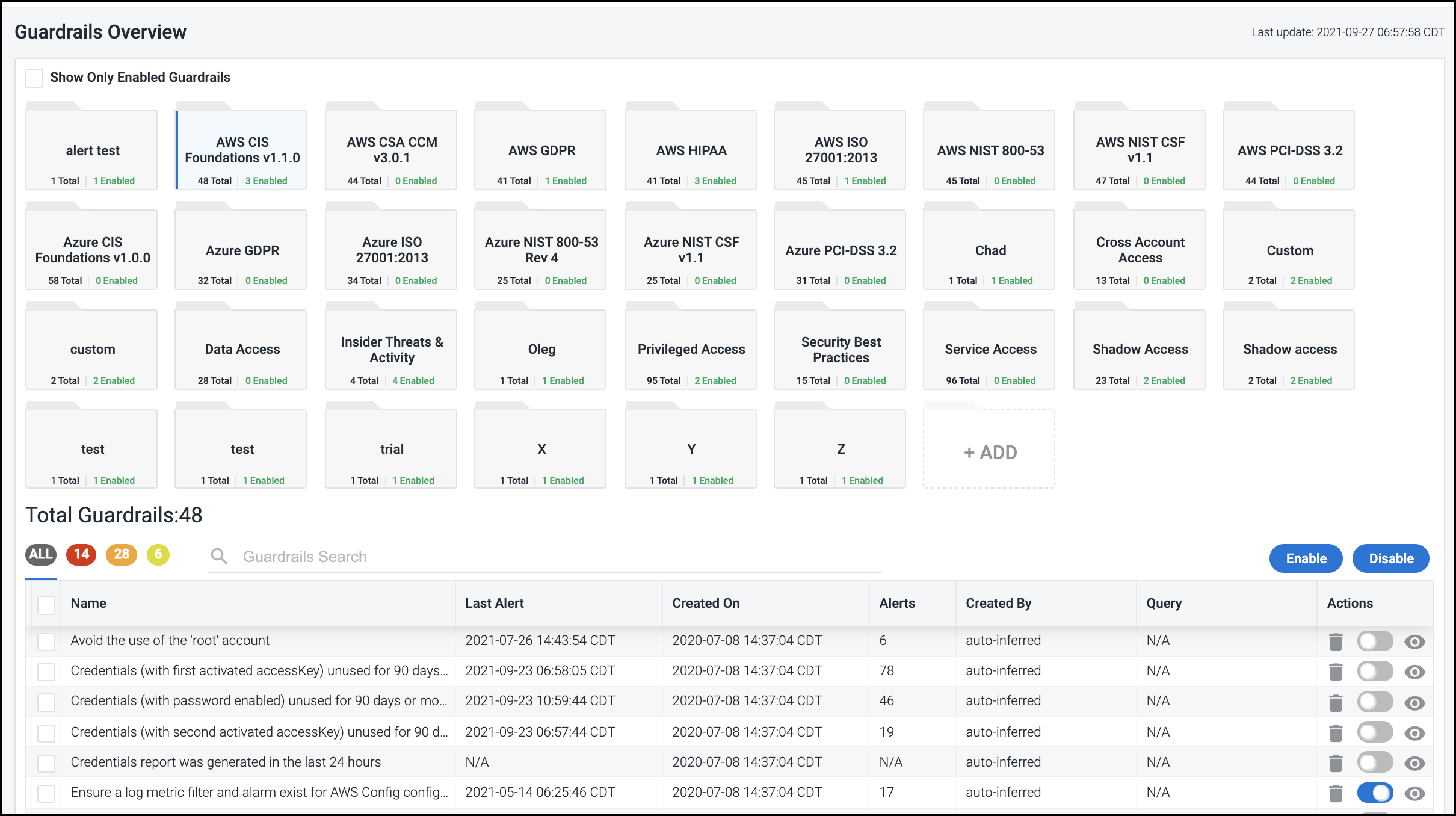
Using Guardrails
Select Guardrails in the left menu to view the guardrails that are currently available to use.
Guardrails are stored as categories, so you can group them based on cloud platform, access type, alert type, or another category that's meaningful to your organization. Select a category folder icon to view the set of guardrails with that category in the list below.
To create a new category for related guardrails, select the empty placeholder folder labeled + ADD and enter a unique name for the new category.
Important
Category folders are deleted once their last guardrail is removed. To retain your category, keep at least one guardrail in it.
To filter the list to show only enabled guardrails, select the Show Only Enabled Guardrails checkbox at the top of the screen.
Note
An N/A in the Last Alert column means that the guardrail
hasn't generated an alert, an N/A in the Alerts column means
that the guardrail rule hasn't been violated, and an N/A in the Query column means that the guardrail is not query based.
If a guardrail name is blue, select it to view the associated query and the type of alert that a guardrail violation will generate.
Note
The alert type or severity impacts how guardrail violations are displayed on the Compliance dashboard, and well as whether alerts are sent.
To help reduce potential "noise" generated by a guardrail, you can configure Cloud Access Management to ignore delete or create actions on identities and/or objects that would otherwise be detected by the query. Cloud Access Management will still detect those actions, they just won't trigger a guardrail violation and resulting alert.
To associate the query with a particular category of guardrails, use the Category field to select from a list of generated categories. The guardrail query will be added to the folder with the corresponding label.
If you edit a guardrail in any of the ways mentioned above, be sure to select UPDATE GUARDRAIL QUERY to save your changes.
Tip
You can also use an existing guardrail as the basis for a new guardrail by giving it a new unique name.
Enabling Alerts
To enable a guardrail to generate alerts - via email, Slack, or SysLog - set the toggle to blue in the Actions column for the specific guardrail. Cloud Access Management will use the information you provided when you configured alert settings to direct the alert appropriately.
After you enable alerting for a guardrail, an alert will be sent whenever a new violation is detected.
In addition to issuing alerts, Cloud Access Management also provides a separate Compliance dashboard that summarizes all guardrail activity. Refer to Viewing a Summary of All Compliance Alerts for more information.
Advanced Guardrails for Compliance Governance
To support your governance and compliance efforts, you can create more advanced guardrails to address compliance-specific use cases such as the following:
Workload Governance - Isolate access to a specific workload due to PCI or dev/prod isolation
Data Governance - Secure access to sensitive data due to GDPR, CCPA, or other regulations
Privilege Governance - Control access to sensitive privileges from high-risk user groups
Workload Governance
This type of guardrail can be used to restrict access to sensitive production or compliance (PCI) workloads from instances, Lambda functions, or users. A workload can refer to thousands of objects and hundreds of security policies and controls which are continuously changing. Cloud Access Management dynamically controls access to your sensitive workloads by continuously monitoring the security access graph for guardrail violations.
Examples:
-
instance with-attribute not accountid with-access any withattribute accountid
-
user with-attribute not accountid with-access any withattribute accountid
-
aws_lambda with-attribute not accountid with-access any with-attribute accountid
Data Governance
This type of guardrail can be used to restrict access to sensitive data based on attributes such as location or tags. For example, to enforce GDPR you can restrict access to GDPR data from Lambda functions or instances not in the European Union.
Examples:
-
aws_lambda with-access aws_s3 with-attribute regionname eu-west-3
-
instance with-attribute publicrisk true with-access aws_s3 with-attribute isencrypted true
-
role with-access aws_dynamo_db_table with-attribute tag-compliance gdpr
-
user with-attribute not group dbadmin with-privilege admin with-access aws_rds
Privilege Governance
This type of guardrail can be used to prevent unauthorized users from gaining access to sensitive privileges tied to your cloud infrastructure. For example, you can restrict access to administrator-type privileges from users who are not in an Admin group.
Examples:
-
user with-attribute not group admins with-privilege admin
-
aws_lambda with-privilege admin with-access any with-attribute tag-env prod
-
role with-privilege ec2 deletevpc
-
instance with-attribute publicrisk true with-privilege kms decrypt with-access aws_s3 withattribute regionname eu-west-3
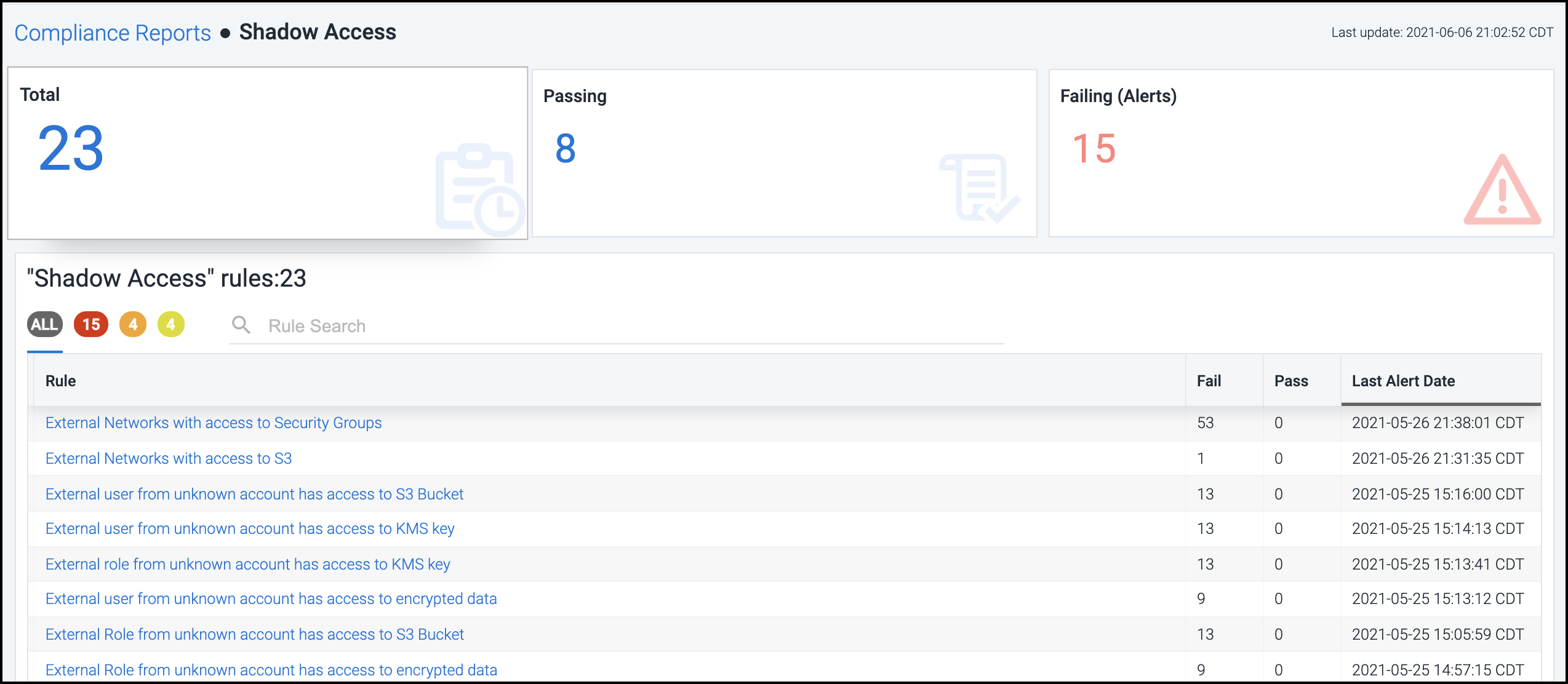
Viewing a Summary of All Compliance Alerts
Select Compliance in the left menu to view the results being generated based on all guardrails that are currently enabled across the entire cloud environment.
The tiles at the top of the Compliance Reports page represent the following information:
Total Tests - the total number of guardrail checks that Cloud Access Management is currently running
Passing Tests - the number of guardrail checks that are currently passing successfully
Failing Tests - the number of guardrail checks that are currently failing, resulting in alerts
Select a tile to view additional details about the subset of guardrail queries responsible for generating those test results in the list below.
You can view the total number of checks being run for each guardrail, as well as the number that are currently failing and passing.
Note
The guardrail list is sorted by the most recent status change, with the guardrail category that triggered the most recent failure listed first.
To download a report for offline use, simply select the Download icon ![]() in the Report column for a specific guardrail. An
in the Report column for a specific guardrail. An .xlsx file is generated and named using the current day, date, and time (based on your time zone).
If, after taking a closer look, you find information that warrants alert notifications, you can configure Cloud Access Management to send them for the associated guardrail(s). For more information, refer to Enabling Alerts.
Select a guardrail name to take a closer look at the set of guardrail rules that comprise that category. Each guardrail rule represents a specific check that Cloud Access Management performs against your cloud infrastructure.
Note
The Rule list is sorted by the most recent status change with the rule that triggered the most recent failure listed first.
To filter the list by severity of the alert, select the appropriately colored icon above the list, where red = High, orange = Medium, and yellow = Low.
You can change the severity of alerts triggered by a specific guardrail rule by editing the guardrail. For more information, refer to Using Guardrails.
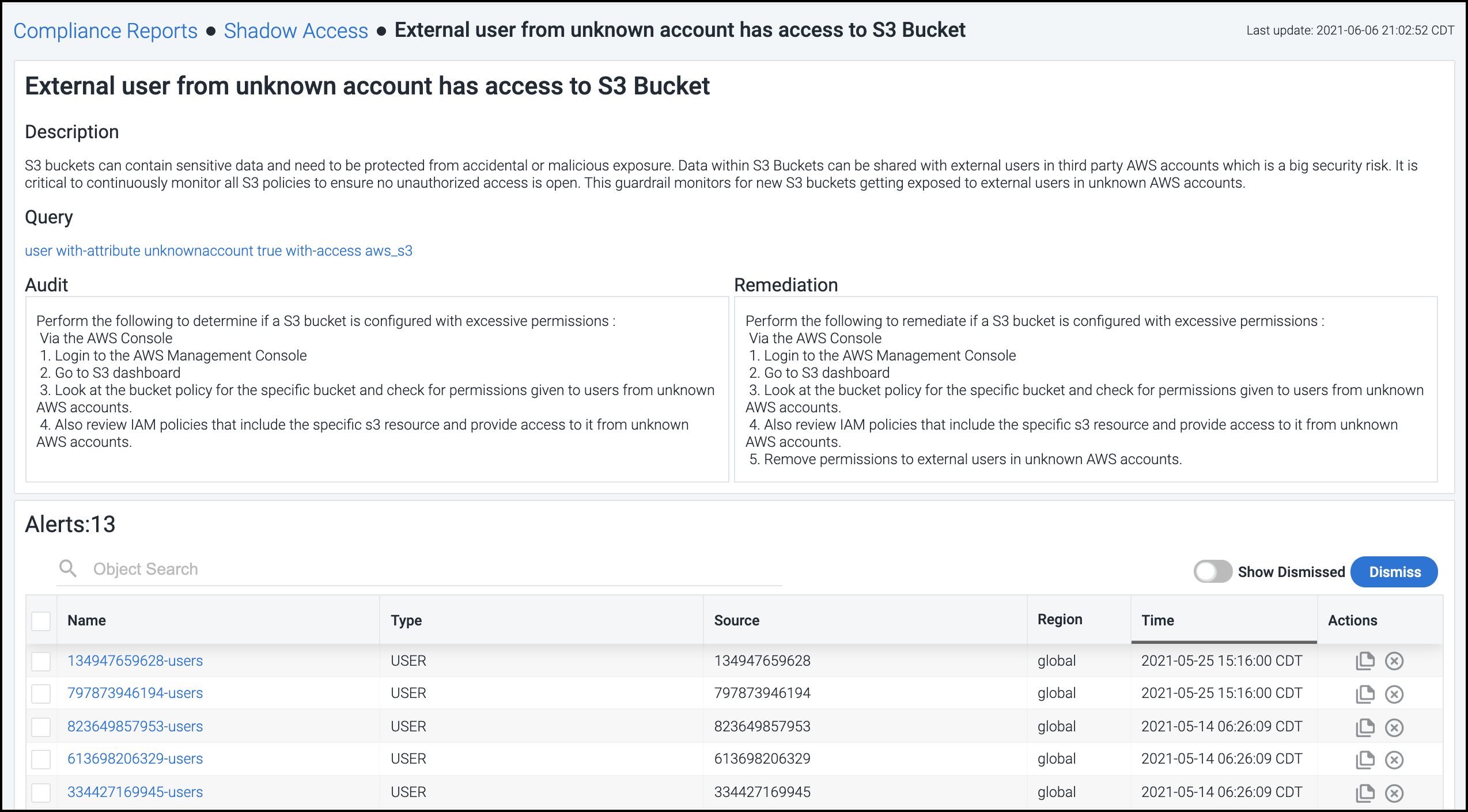
Select a guardrail rule in the list to view details about the specific alerts on that rule as well as suggested steps to remediate the issue.
From this view you can choose how you want to handle each alert:
-
To ignore a specific alert and no longer display it, select the Dismiss icon
 in the Actions column. Select the Dismiss button to dismiss a set of selected alerts or all alerts.
in the Actions column. Select the Dismiss button to dismiss a set of selected alerts or all alerts. -
Select the Copy Cloud Resource Name icon
 in the Actions column to copy the ID of the cloud source associated with that alert to the clipboard. You can then paste this identifier into the cloud platform's UI to search for the specific instance and perform necessary diagnostics or troubleshooting.
in the Actions column to copy the ID of the cloud source associated with that alert to the clipboard. You can then paste this identifier into the cloud platform's UI to search for the specific instance and perform necessary diagnostics or troubleshooting.
To take a closer look at the identity, object, or network involved in an alert, select the name to open it in the corresponding dashboard.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.