Getting Started
To set up Cloud Access Management, you will need to set alerts, determine how users can access your org, and configure and register your cloud service providers (CSPs) and identity service providers (IDPs). Once you complete your configuration, you can view your cloud infrastructure.
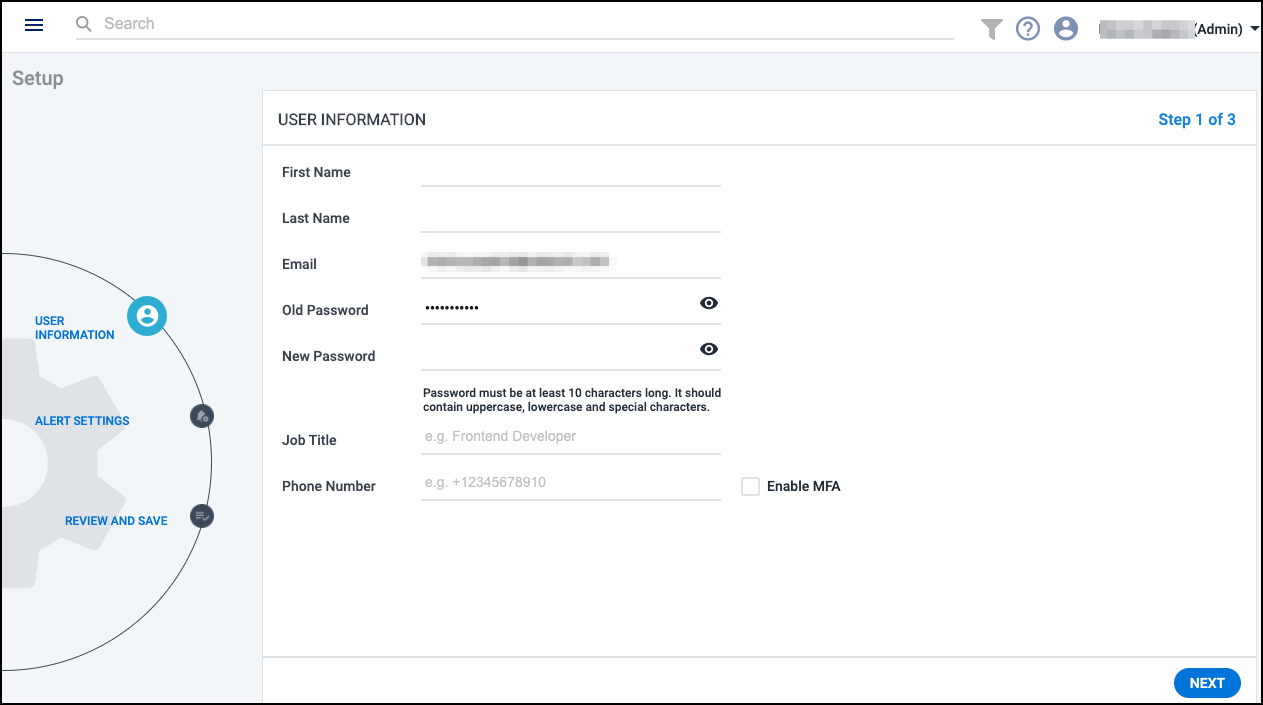
Upon logging in for the first time, enter the username and password that SailPoint sent to your email and configure alert settings.
End your session by selecting the Profile icon
![]() in the top right (or the down arrow to the right of your name) to display the menu. Select Logout.
in the top right (or the down arrow to the right of your name) to display the menu. Select Logout.
Configuring Alert Settings
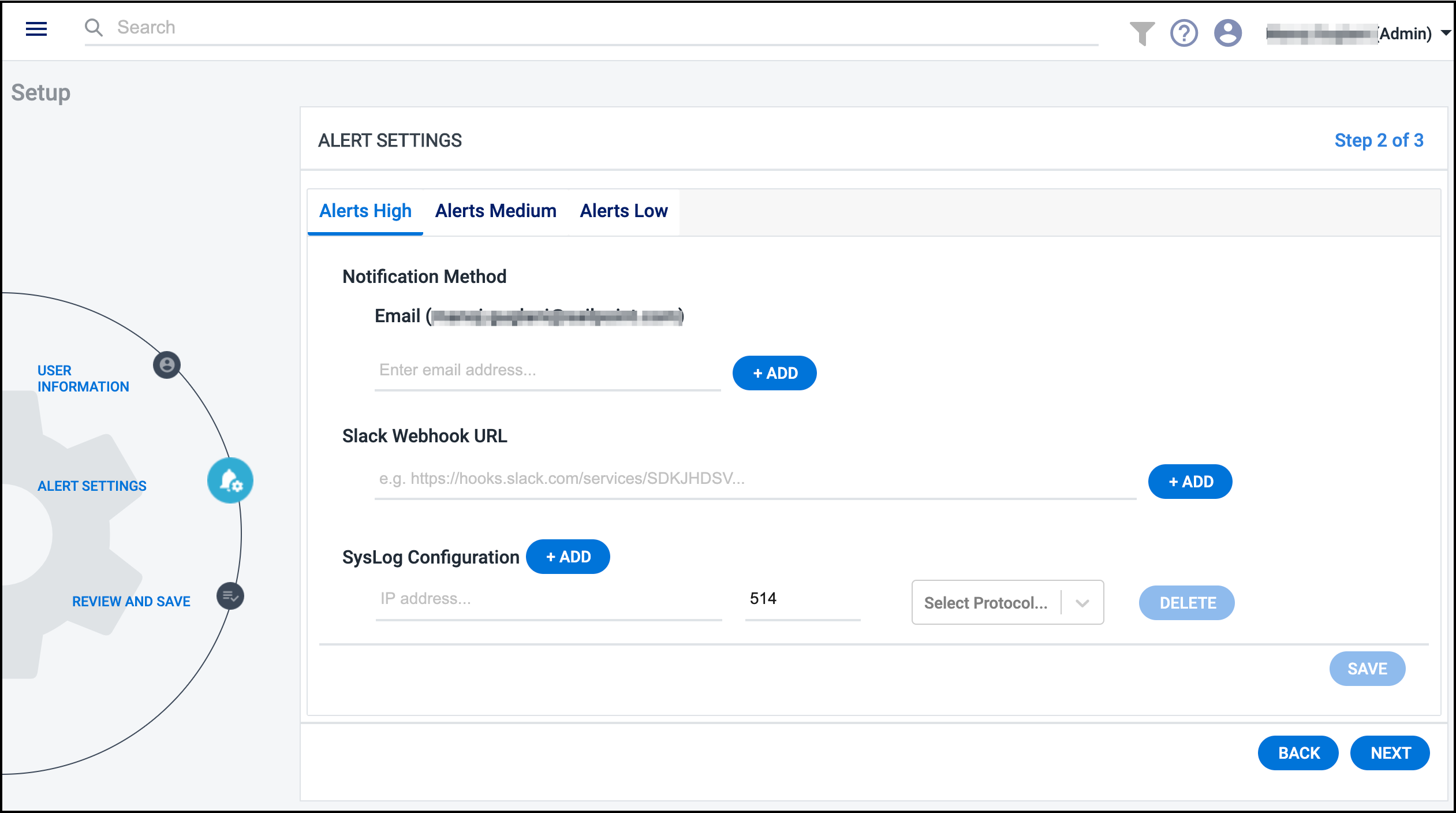
Cloud Access Management offers numerous ways to create, view, and triage alerts raised from suspicious events and risky activity in your cloud landscape. You can configure how you want to be notified of these alerts based on their severity.
Select the Alerts High, Alerts Medium, and/or Alerts Low tabs to configure the notification methods for each alert level.
You can choose your preferred method (or combination of methods) to receive alert notifications.
-
Email - Specify the email address(es) you want to receive alert notifications.
-
Slack - If you've enabled incoming webhooks in your Slack settings, provide the incoming webhook URL so Cloud Access Management can post alert notifications to the Slack channel you've configured to receive messages.
-
Syslog - Specify the IP address, port number, and protocol (
udportcp) of the syslog server you want to collect Cloud Access Management alert notifications.
Note
The alert settings you specify will apply to all registered
cloud sources. They can be changed any time by selecting the Settings icon ![]() and selecting Alert Settings.
and selecting Alert Settings.
Logging in with Your Identity Security Cloud Credentials
Your Cloud Access Management user account information is automatically generated from your Identity Security Cloud user account. Users must exist in Identity Security Cloud and be granted the appropriate access level to work in Cloud Access Management.
Users can log into Cloud Access Management with their Identity Security Cloud credentials using SailPoint's Shared Authentication Service, or you can configure authentication through SAML Single Sign On.
You can work with your CSM and SailPoint Services to identify the best method for your organization. If you are already using Identity Security Cloud, contact your identity team administrator for assistance.
Setting Access Levels
To determine what users can do in Cloud Access Management, you can give limited or administrative access to users by granting user level permissions in Identity Security Cloud.
Only users with the Cloud Gov Admin user level can manage the sources page and add, edit, or delete cloud sources. Additionally, only administrators can perform manual inventory refreshes.
Grant all other users the Cloud Gov User user level.
Caution
The Org Admin user level also grants access to Cloud Access Management but includes full admin privileges in Identity Security Cloud, and should only be applied when that level of access is appropriate.
Authenticating Users with SAML
Identity Security Cloud and Cloud Access Management can use SAML-based identity providers, such as Okta, Microsoft ADFS, or Ping Identity to support federated users.
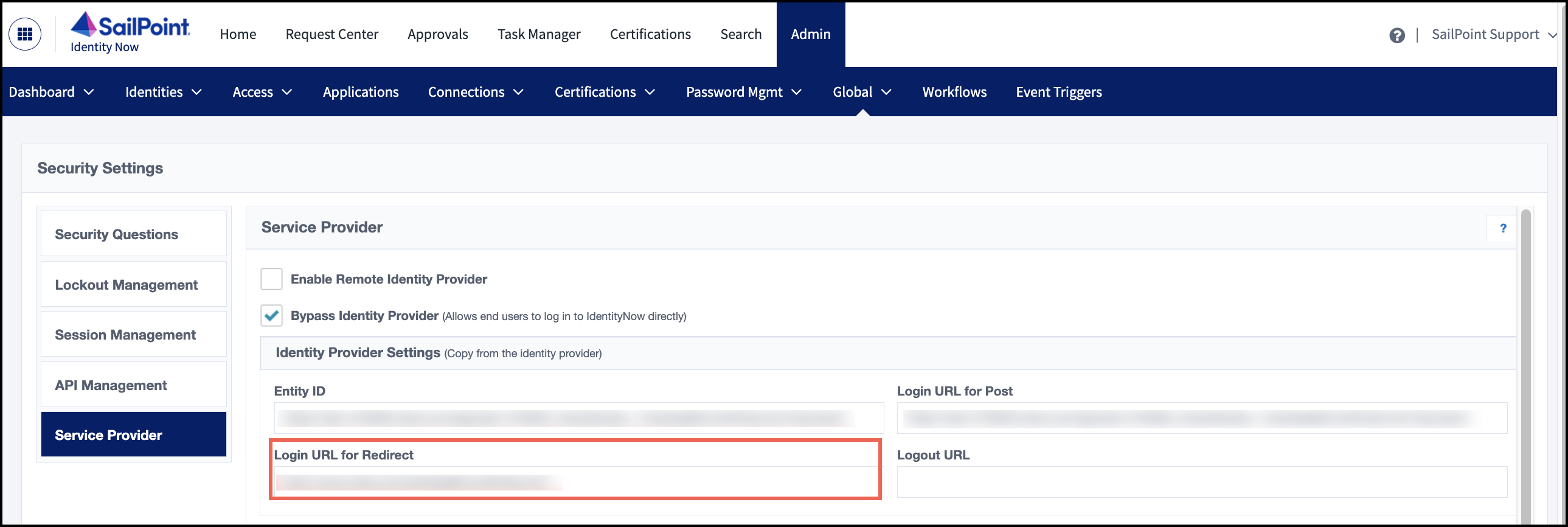
Because Cloud Access Management uses Identity Security Cloud for its authorization, you must configure Identity Security Cloud to accept the authorization URL from Cloud Access Management to know where to forward user information and redirect the user.
- Configure Identity Security Cloud as your service provider using your selected identity provider's settings.
- Gather the redirect URL specified by your SAML provider. It must follow this pattern, according to your org name:
https://org.cam.sailpoint.com/authorize/idn. - Configure your SAML provider to specify that URL as the default relay state.
- In Identity Security Cloud, go to Admin > Global > Security Settings > Service Provider.
-
In the Identity Provider Settings section, enter the login URL for redirect.
Configuring and Registering Providers
You must configure and register your cloud and identity provider sources to enable Cloud Access Management to provide governance data.
-
Configure your cloud service providers. When you're done configuring, register your CSP source(s).
-
Configure your identity providers. When you're done configuring, register your IDP source(s).
Viewing Your Cloud Infrastructure
The Dashboard shows data from the most recently refreshed source inventory of your configured and registered CSPs and IDPs.
| Object | Definition |
|---|---|
| Sources | View the status of your configured Amazon Web Services accounts, Google Cloud sources, and Azure subscriptions. |
| Users | Discover user identities, including inactive ones, across cloud sources, including service accounts, security principals, groups, and privileged users. |
| Privileges | Monitor and analyze the privileges in your cloud platforms to identify inactive, unused, and excess access. |
| Unused Access | View sensitive access across cloud sources that has not been used for the past 90 days. This includes access provided by roles, users, services, and direct IAM user access without roles. |
| Alerts | View the number, type, and severity of alerts raised by anomalous behavior associated with your CSPs. |
| Public Objects | Track the instances, object stores, relational databases, security groups, and subnets that make up your publicly accessible objects in the cloud infrastructure. |
| Shadow Access | Use saved search queries, or guardrails, to track the access your external sources and networks have to identify analogous and unauthorized access to your data. |
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.