Working with Discovered Objects
Cloud Access Management automatically detects all resource objects and services across your cloud infrastructure, including the following:
| Instances | Networks |
| Databases | Load balancers |
| Object stores | Encryption keys |
You can view a summary of all discovered cloud objects and the access details for individual objects.
Viewing a Summary of Discovered Cloud Objects
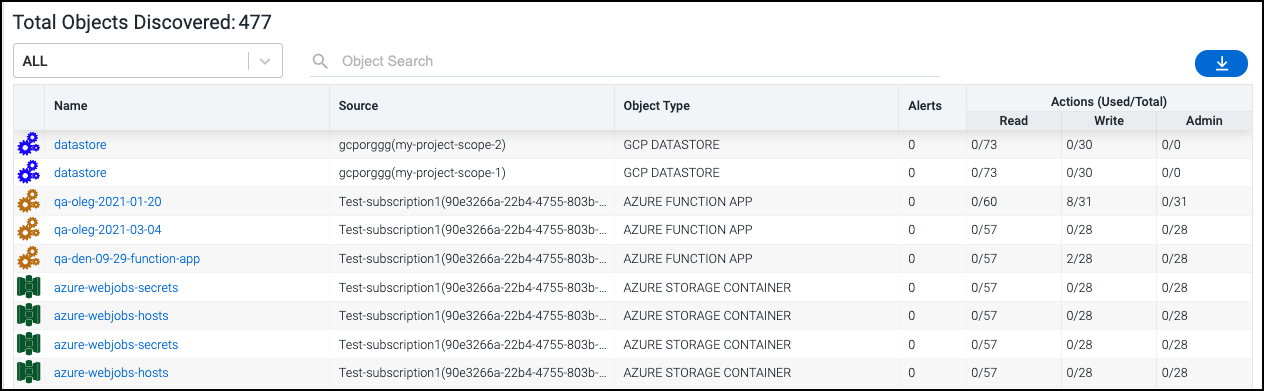
Select Objects in the left navigation menu to view an overview of all objects that Cloud Access Management has discovered across cloud sources, along with the associated security policies and controls, their associated source, and a summary of admin/read/write actions being used (and available) on each object.
Select the download icon
![]() to generate and download a CSV of the discovered objects. You can use the dropdown menu to select an object type and filter the list to display only objects of that specific type.
to generate and download a CSV of the discovered objects. You can use the dropdown menu to select an object type and filter the list to display only objects of that specific type.
Select the ALL option in the dropdown menu to clear the current filter and reset the table to the default view of all discovered objects.
You can also use the Object Search field next to the dropdown menu to search for a specific object by name.
Select the name of an object in the list to view the details page for that object.
Viewing Access Details for an Object
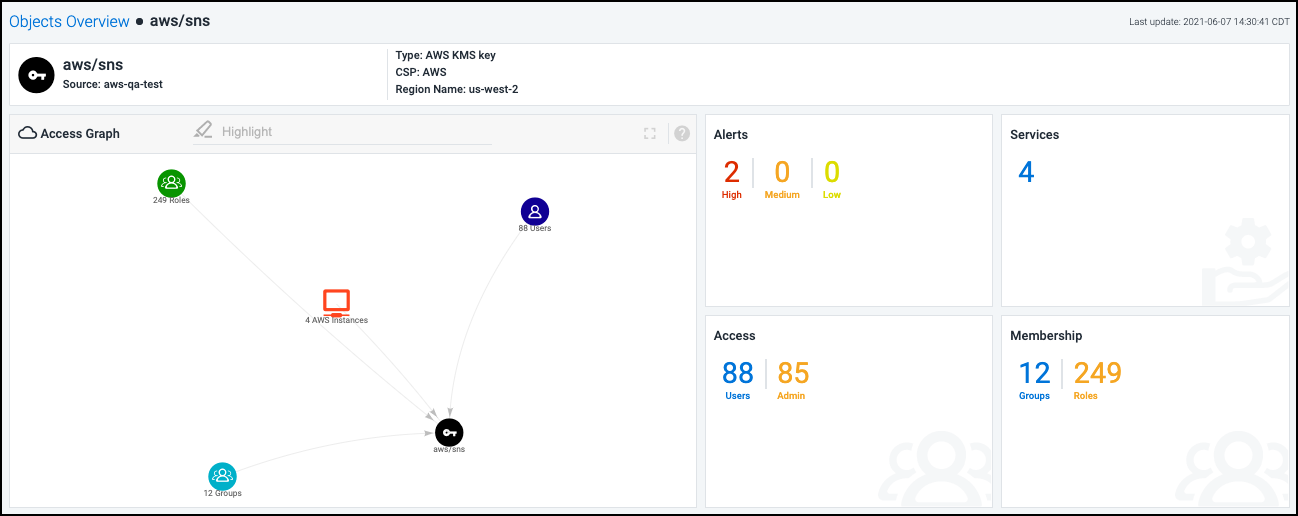
The details page for an object provides a summary of security and access policies affecting that object. Information is organized into tiles based on the data discovered by Cloud Access Management.
Select a tile to display more detailed information about that tile in the list below. The access graph is also updated based on your selection. For information on using the access graph, refer to Using the Access Graph to Understand Relationships.
Alerts - These numbers represent the violations discovered for this object based on severity. Select this tile for a detailed view into these alerts. For more information, refer to Viewing and Triaging Alerts.
Services - This number refers to the total number of cloud instances and services that have access to this object through cloud security policies and controls. Select this tile to display information about each of these services in the list below.
Access - These numbers represent the users and admins that have access to this object through various cloud security policies and controls. Select this tile to display information about each of the users that have access to the object in the list below. Select a number in the tile to display information about that subset of users only.
Membership - These numbers represent the total number of groups and roles that have access to this object. Select this tile to display information about each group and role that has access in the list below. Select a number in the tile to display information about that selection only.
Using the Access Graph to Understand Relationships
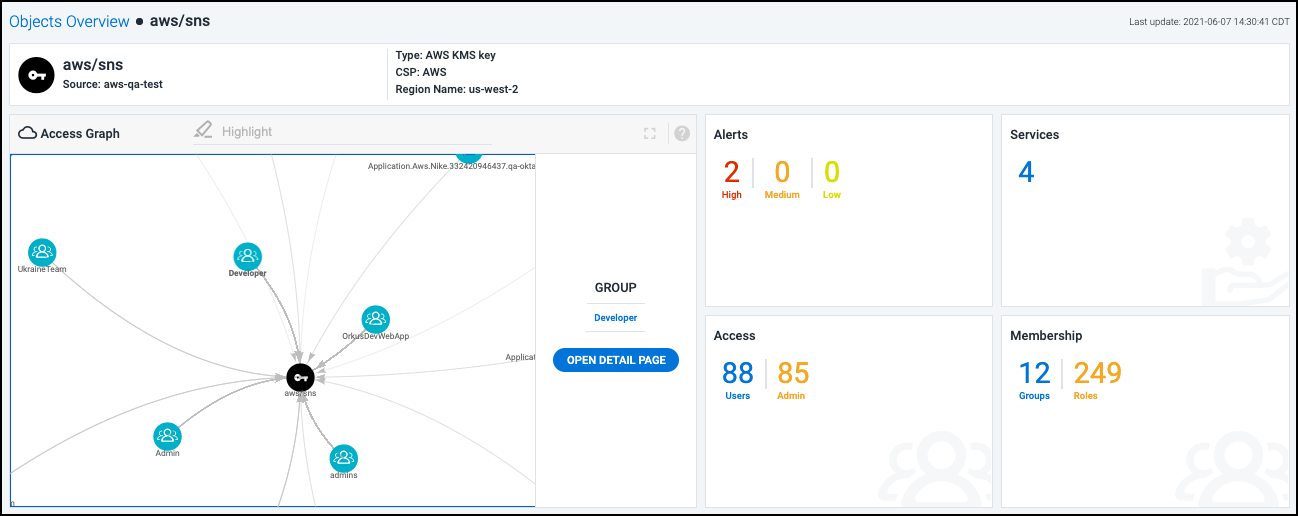
Cloud Access Management captures all access defined in cloud security policies and generates an access graph to represent that information visually. Objects and users are represented as nodes in the graph, and their relationships are represented by the lines that connect them.
To enlarge the access graph, select the Show Fullscreen icon in the top right corner of the graph. Select it again to return to the standard view (where the tiles on the right are also visible).
Select an item in the graph to view identifying details in a side panel. If there are additional details available for the item, you can select OPEN DETAIL PAGE to view them.
Select a line that's connecting items in the graph to display the relationship details in a side panel.
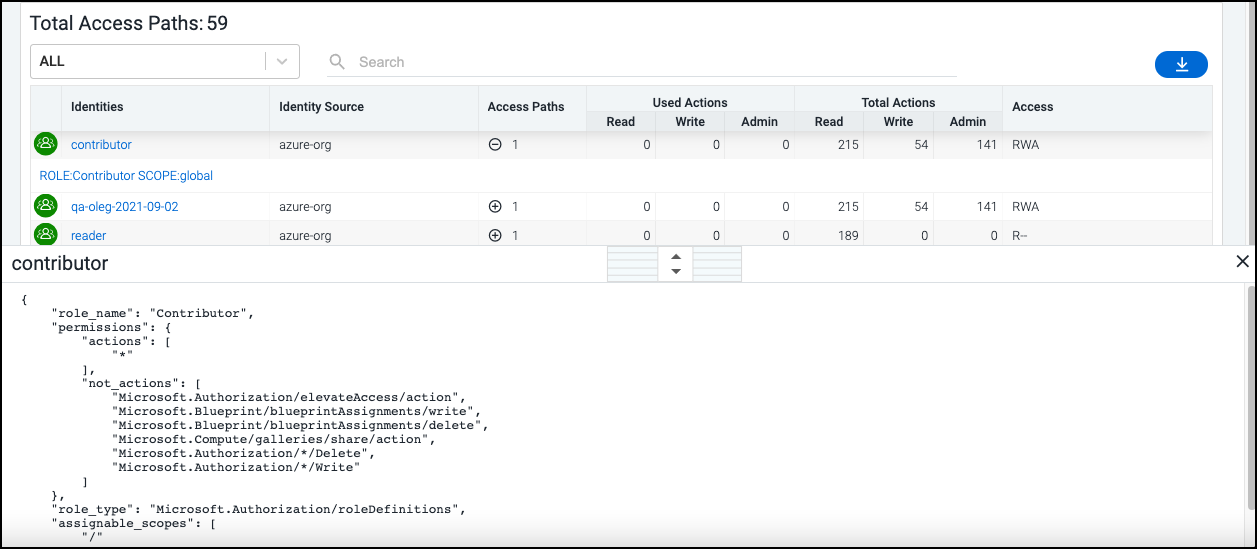
Viewing an Object's Total Access
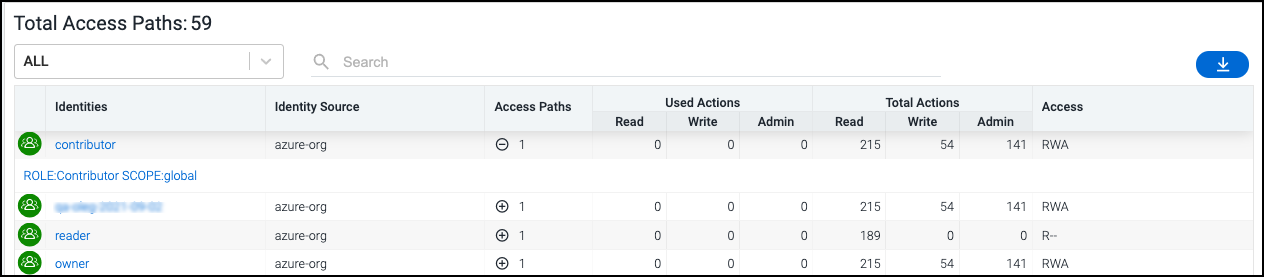
By default, the bottom section of the overview page for an object displays a list of all identities and roles that have access to the specific object, as well as the following information:
-
the name of the cloud source associated with the object
-
the number of access paths being used to control that access
-
a summary of admin/read/write access being used (and available)
Note
When you select a tile, the information displayed in the list changes to match the context of your selection.
Select the plus + sign in the Access Paths column for an entry in the list to view the name of the specific policy that is granting the access to the identity or role.
Select an access path name to open the path details in a JSON viewer below.
To close the JSON viewer, select the X icon in the top right of the window.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.