Working with Discovered Identities
Cloud Access Management detects identities associated with services and users across your cloud infrastructure. You can view a summary of all discovered identities across cloud workloads along with the associated access paths and controls, including:
| Users | Service accounts |
| Groups | Instances |
| Roles | Lambdas |
In addition, Cloud Access Management can detect federated users and groups that have cloud access via a recognized identity provider. For more information, refer to Viewing Access Information from Identity Providers.
Viewing a Summary of Discovered Identities
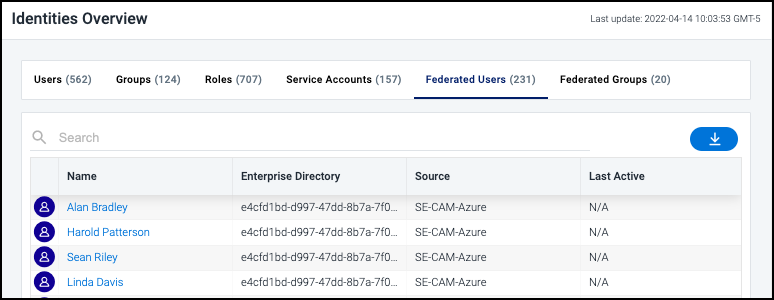
Select Identities in the left navigation menu to display a list of the identities that Cloud Access Management discovered. Select the name of a type of identity listed (users, groups, roles, service accounts, federated users, or federated groups) to filter the list by that type.
Every identity type displays the:
-
name of the user, group, role, service account, federated user, or federated group.
-
source associated with the identity.
-
name of the enterprise directory from which the identity came (federated only).
-
most recent date and time when the user or role accessed the system.
Select the name of an item in the list to view its access details.
Viewing Access Details for an Identity
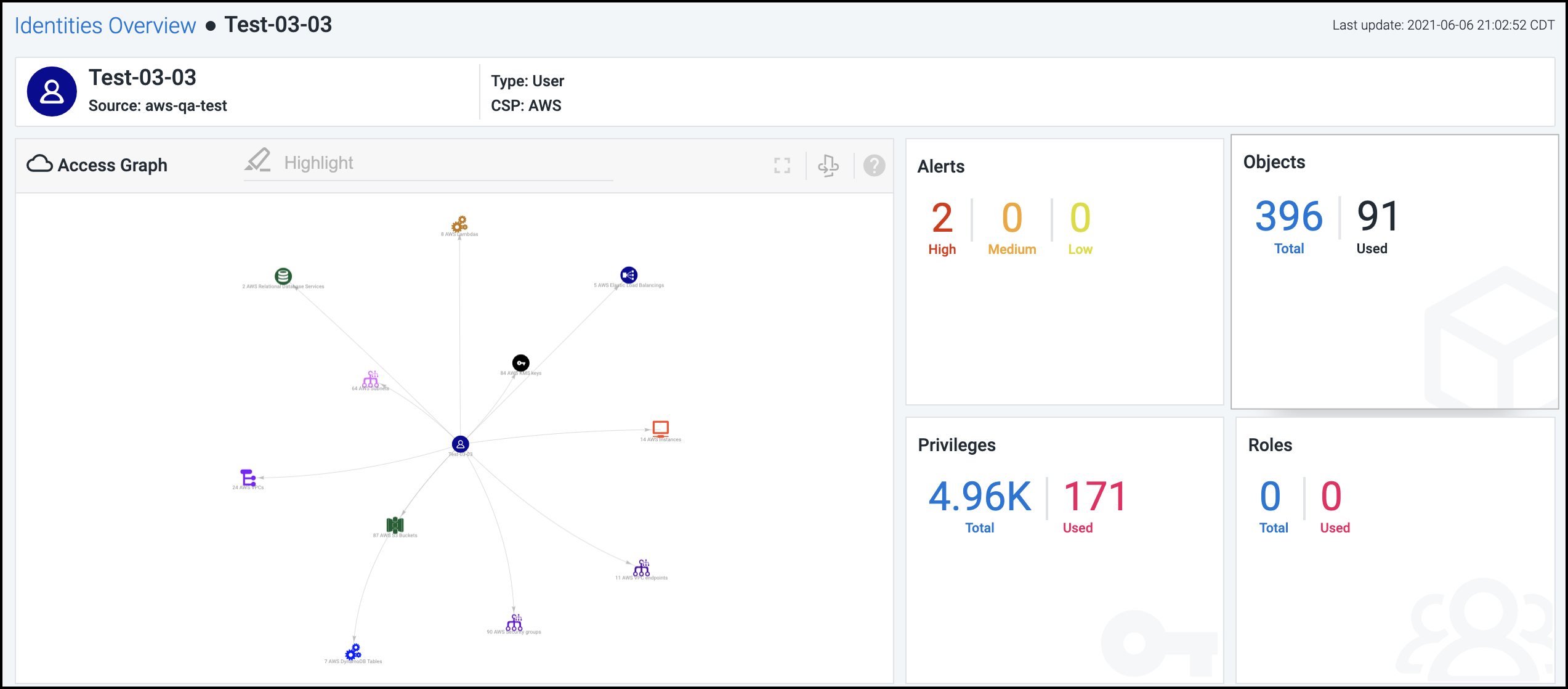
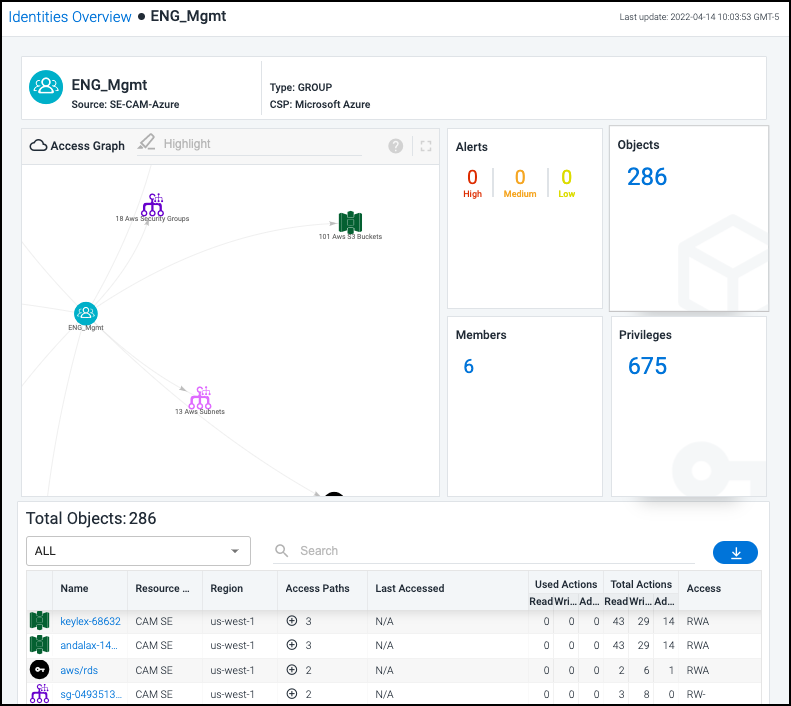
The details page for an identity provides a summary of security and access policies affecting that identity. Information is organized into tiles based on the type of identity and the data discovered by Cloud Access Management. For example, here's what the details page looks like for a user identity:
Alerts - These numbers represent the violations discovered for this identity based on severity. Select this tile for a detailed view into these alerts. For more information, refer to Viewing and Triaging Alerts.
Objects - These numbers represent the number of cloud objects and services that this identity is using and the total number the identity has access to through cloud security policies and controls.
Privileges - This number refers to the total number of privileges associated with this identity. For users, federated users, and service accounts, the number of privileges currently being used (out of the total) is also displayed. Select this tile to view the list of privileges along with the usage information in the table below.
Roles - This tile displays the total number of roles currently assigned to this identity, as well as the number that are currently being used (displayed for users, federated users, and service accounts only).
Members - This number refers to the total number of members in the selected group (displayed for groups and federated groups only).
Users - This tile displays the total number of users currently assigned this role, as well as how many users are currently using the access privileges granted by the role (displayed for roles only).
Instances - This tile displays the total number of instances accessible to identities with this role, as well as how many instances are currently being accessed by identities with the role (displayed for roles only).
Select a tile to display more detailed information related to that tile in the list below. The access graph is also updated based on your selection. For information about the access graph, refer to Using the Access Graph to Understand Relationships.
Notes
- GCP grants the Billing Account Creator and Project Creator roles to all users in the primary domain by default, so Cloud Access Management will list those roles for those users unless you have removed those roles from the organization resource.
- Cloud Access Management does not track deny assignments created with Azure RBAC.
Viewing an Identity's Total Access
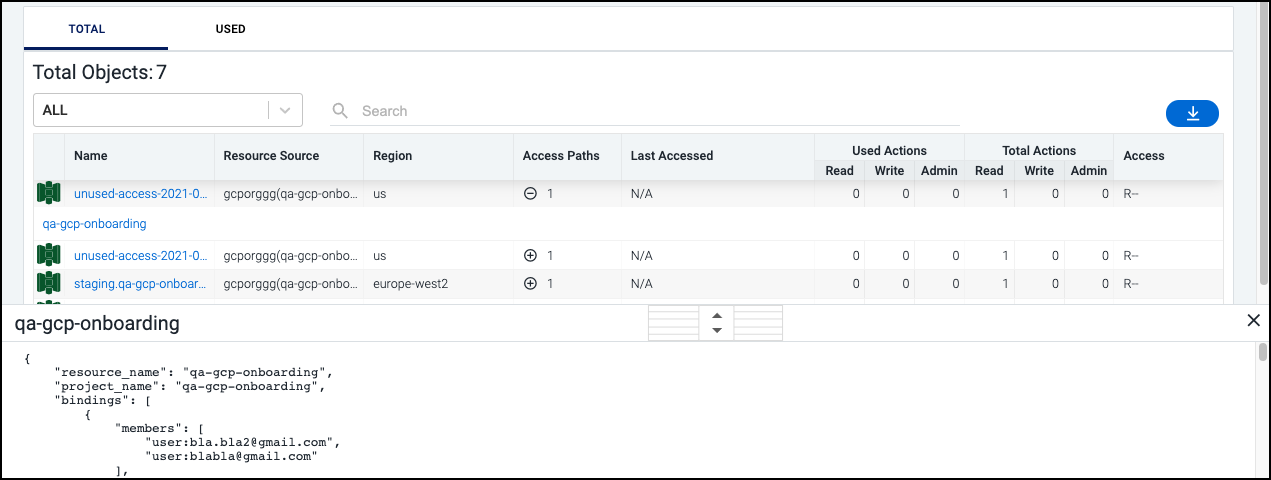
By default, the bottom section of the details page for an identity displays a list of all objects the identity can access, as well as the following information:
-
the number of access paths being used to control that access
-
the name of the cloud source associated with the object
-
the region where the associated cloud instance is located
-
a summary of admin/read/write access being used (and available)
Note
When you select a tile, the information displayed in the Objects Accessed list changes to match the context of your selection.
You can view the total number of objects or select the USED tab to display only used objects. Select the expand icon
![]() in the Access Paths column to view the policies. Select the policy name to display its JSON.
in the Access Paths column to view the policies. Select the policy name to display its JSON.
Viewing Access Information from Identity Providers
Once you have configured and registered your identity provider, Cloud Access Management will display the federated access. Federated access includes any users and groups detected from an enterprise directory that have access to cloud roles configured via a registered identity provider.
Select Identities in the left navigation menu and select the tab above the table to display that type of identity:
- Users
- Groups
- Roles
- Service Accounts
- Federated Users
- Federated Groups
For example, selecting Federated Users will display all users who are authenticated into Cloud Access Management via an identity provider such as Azure AD. With some CSPs, federated users will not have native IAM users or credentials, as they assume temporary cloud role access during their session.
Select an entry to display its access graph and accessed objects.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.