Monitoring Cloud Access and Activity
Cloud Access Management analyzes activity occurring on your cloud infrastructure and uses the information gathered to train machine learning (ML) models. These models learn entity behavior based on location, activity type, and activity volume, then apply this knowledge to detect anomalies in behavior.
Location-based anomalies - Cloud Access Management learns the location information for every user session and trains a model to identify anomalous locations that could represent a security risk. When an anomaly is detected, a location alert is created along with usage events to help you quickly diagnose and triage the issue.
Activity-based anomalies - Cloud Access Management learns the activity type and volume for every user and trains a model to identify anomalous activity that could indicate a security risk. When an anomaly like shadow access is detected, an alert is created along with event data to help you quickly diagnose and triage the issue.
Viewing and Triaging Alerts
Cloud Access Management is continuously monitoring your cloud infrastructure, data, and users for high-risk and suspicious behavior. Built-in guardrails and advanced AI models analyze the cloud access graph and identify violations. This gives you better information to triage alerts.
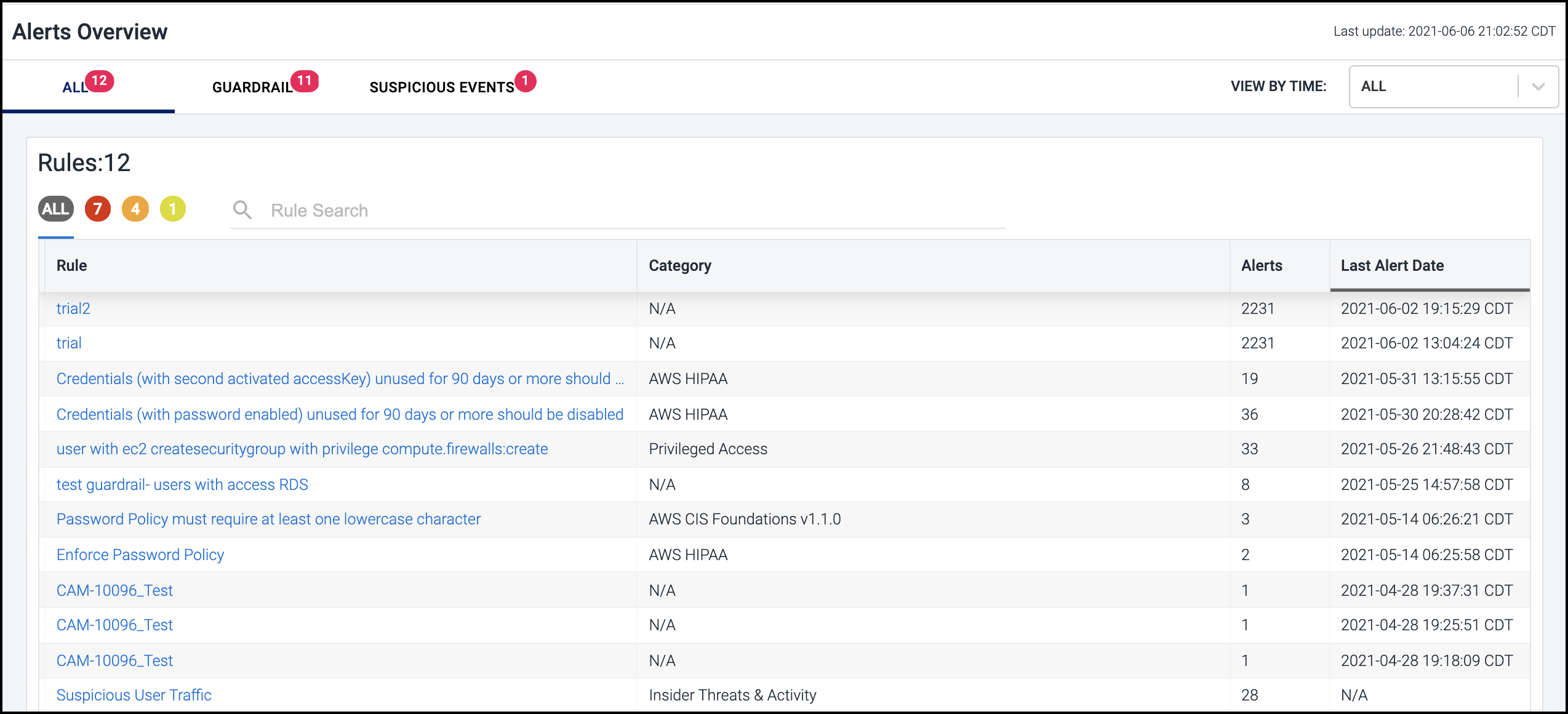
Select Alerts in the left navigation menu to display an aggregated view across the cloud infrastructure. It lists alerts in chronological order, displaying the most recent alert at the top of the list.
You can filter the list based on the type of event that generated the alert by selecting the GUARDRAIL or SUSPICIOUS EVENTS heading.
You can also filter each list based on severity by selecting the appropriately colored icon above the list: red = High, orange = Medium, and yellow = Low.
Note
If a colored icon isn't shown, it means there are currently no alerts with that severity being generated.
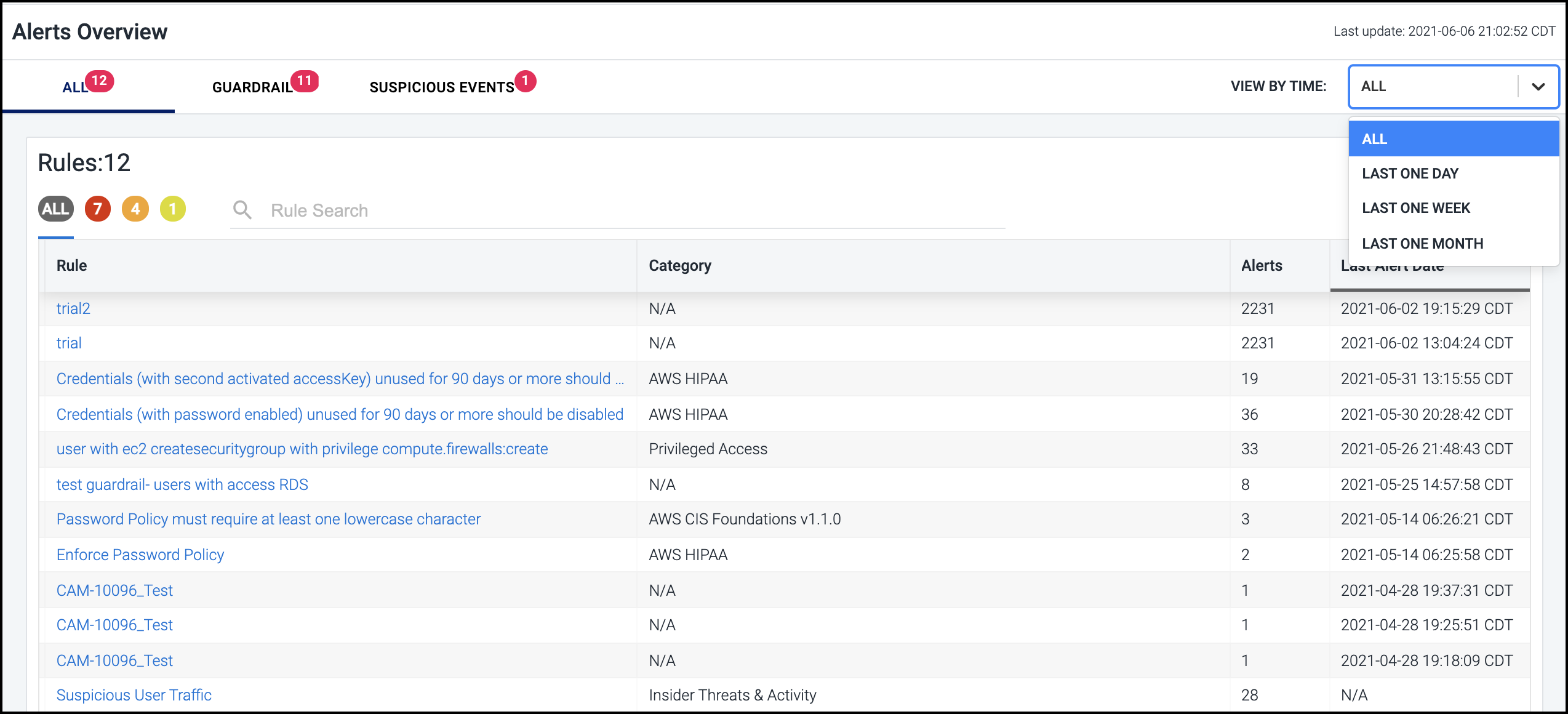
To help you further refine the set of rules displayed, you can filter the list based on whether the associated alert was generated during the last day, week, or month by selecting the corresponding option in the VIEW BY TIME dropdown list.
For example, the list below is filtered to display only those alerts generated by guardrail rule violations that have occurred in that last week that are considered low severity.
To search the rules list, simply type a search string in the field above the list. Rules that contain a match are displayed as you type.
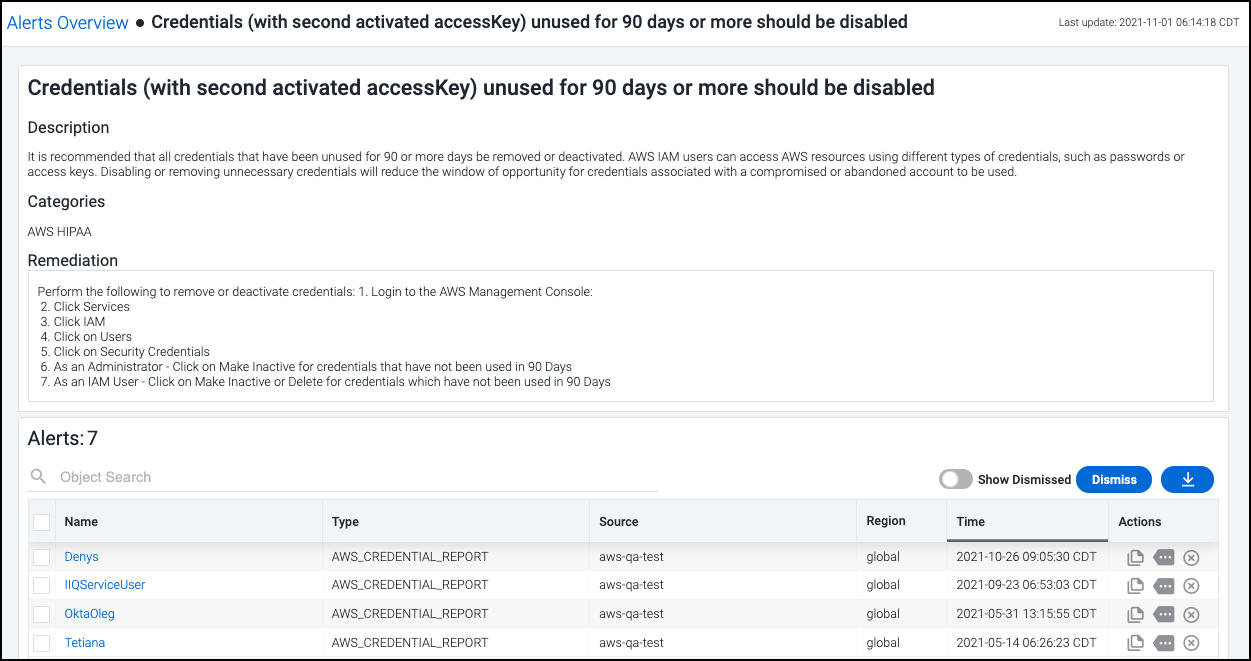
Select a rule to view the information about the specific violations
that triggered the alert, as well as suggested steps to remediate the
issue. Select the download icon
![]() to generate and download a CSV of the discovered violations.
to generate and download a CSV of the discovered violations.
The time stamp indicates when the violation was detected - and the alert was generated - with the most recent occurrence listed first.
Just like the Compliance dashboard, you can choose how you want to handle each violation:
-
To ignore a specific violation and no longer display it, select the Dismiss icon
 in the Actions column. You can also use the Dismiss button to dismiss a set of selected violations or all violations at once.
in the Actions column. You can also use the Dismiss button to dismiss a set of selected violations or all violations at once. -
Select the Copy cloud resource name icon
 in the Actions column to copy the
ID of the cloud source associated with that violation to the
clipboard. You can then paste this identifier into the cloud
platform's UI to search for the specific instance and perform any
necessary diagnostics or troubleshooting.
in the Actions column to copy the
ID of the cloud source associated with that violation to the
clipboard. You can then paste this identifier into the cloud
platform's UI to search for the specific instance and perform any
necessary diagnostics or troubleshooting. -
If there is additional context available, you can select the View Context icon
 to view more details about the violation.
to view more details about the violation.
To take a closer look at the identity, object, or network involved in a violation, select the name to open it in the corresponding dashboard.
Detecting Unused Access
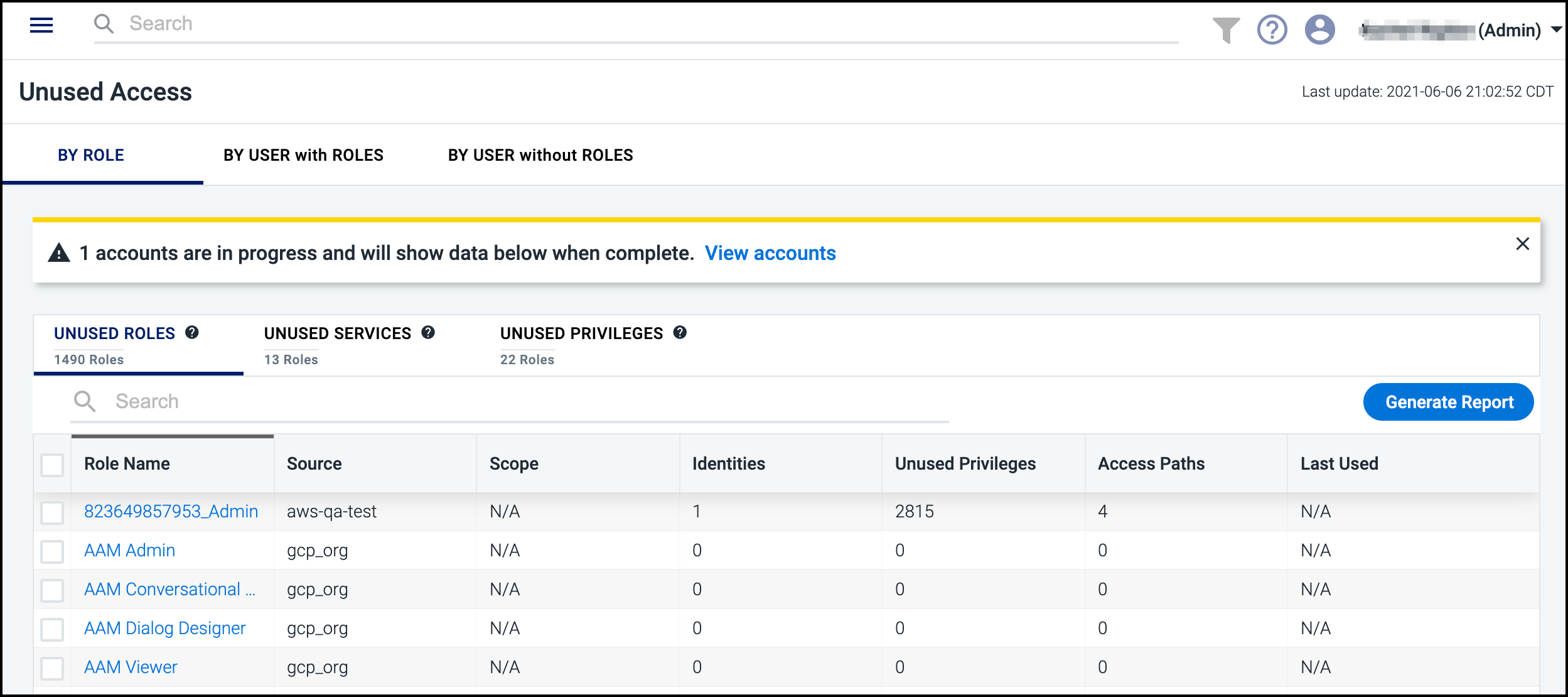
Cloud Access Management surfaces the unused access of roles, services, and privileges to help you identify and enforce the minimum amount of permissions needed to perform tasks.
To help you enforce and maintain least privilege access, Cloud Access Management detects:
-
Unused roles assigned to identities on a cloud platform
-
Unused services on a cloud platform (for example, storage, database, EC2 instances, virtual machines)
-
Unused privileges (limited to admin and write)
Note
Only administrative and write activities are tracked - read access is not.
Viewing Unused Access
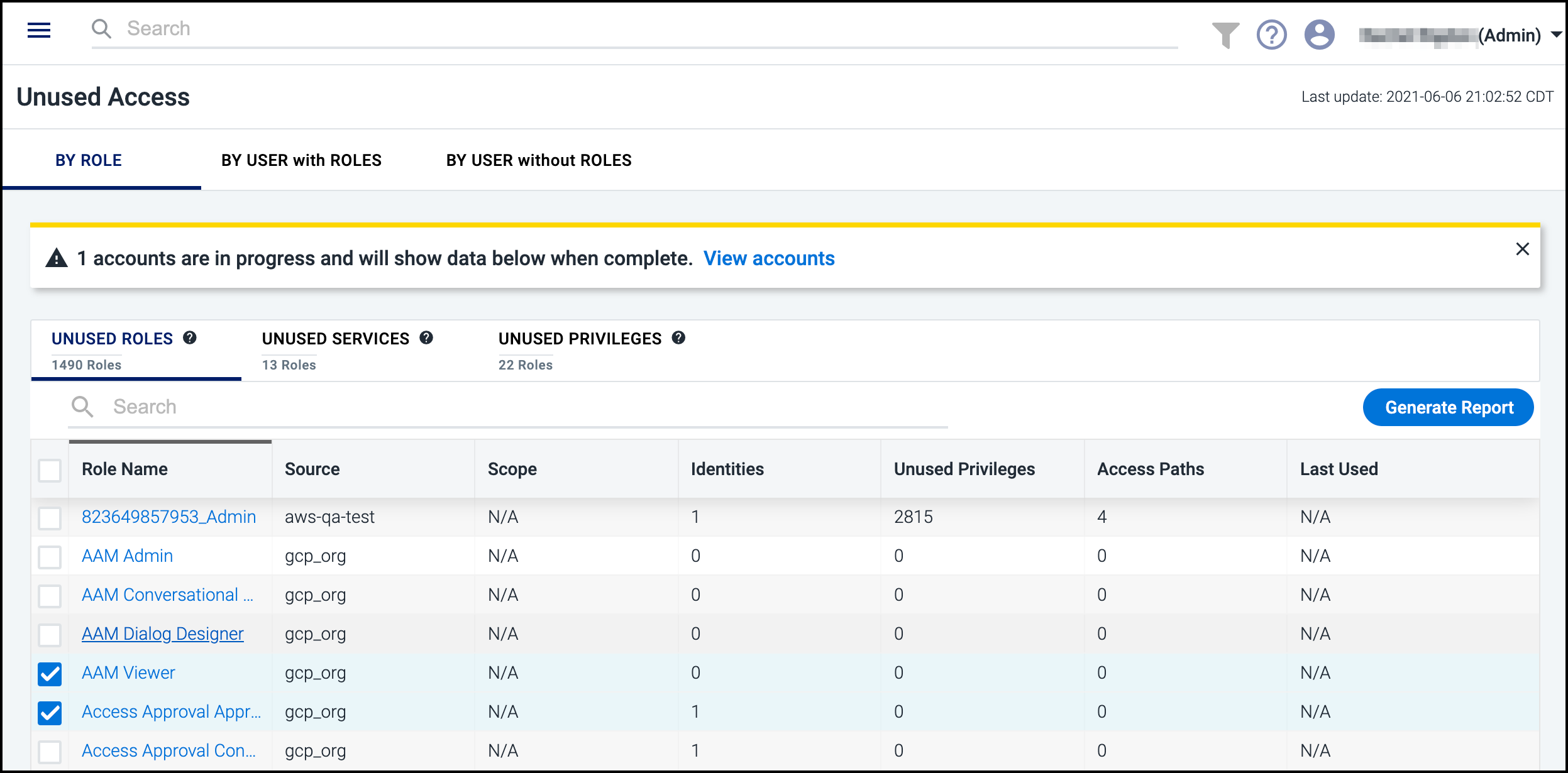
To view unused roles, services, and privileges, select Unused Access from the left menu.
Select the BY ROLE, BY IDENTITY with ROLES, or BY IDENTITY without ROLES tabs to filter the unused access information. Use the search field to quickly find usage information about specific roles, services, or privileges. The BY IDENTITY without ROLES tab shows unused access that is granted directly to a cloud user, as opposed to being granted by a role.
Examples
Viewing Unused Roles and Services
Cloud Access Management determines what services are unused by looking within the context of the user access to the source. For example, if a role is given access to S3 and EC2, but EC2 has not been accessed in 90 days, then the EC2 service connected to that role would be marked as unused. A service is only listed as unused within a role if all instances of that service have not been accessed. For example, if a role references more than one storage service instance, and at least one instance of that service has been accessed recently via the role, then the service is considered in use for that role.
To find unused roles providing access to service accounts, select the BY IDENTITY with ROLES tab and then filter by UNUSED SERVICES. If, for example, you have two roles providing access to the same service, but only one role is used, that identity's unused role and service will be shown.
Viewing Unused Roles and Privileges
To dislpay the unused privileges for the
Viewer role, you can select BY ROLE then UNUSED PRIVILEGES to view whether that privilege and role is listed. Select
the role name to access the report showing which specific privileges
associated with the role aren't being used.
Viewing by Identity with or Without Roles
Use the BY IDENTITY with ROLES or BY IDENTITY without ROLES tabs to display the total privileges available to each identity and how many of those are unused. Like looking for unused access by role, you can select the tabs to view the unused roles, services, and privileges for each identity.
You can also display the relevant policies and export reports for unused access. For example, to view all of the unused privileges for a particular role based on identity:
-
Select BY IDENTITY with ROLES then UNUSED PRIVILEGES to display the source, total/unused privileges, and roles for each identity.
-
Select an identity name to display the number of unused roles and unused privileges that exist for that identity.
-
Select the role name to display a table of all unused privileges for the selected role and the associated policies granting that access.
-
Select the download icon
 from the Actions column to export a report of that specific privilege.
from the Actions column to export a report of that specific privilege.
Generating Unused Access Reports
Capture unused access data with the reports function. On the Unused Access page, select the tabs for the type of unused access you want, such as By User without Roles and Unused Users. Next to each entry is a checkbox that you can select to specify what should be included in your report.
Select Generate Report and choose to either generate a report for all the roles, services, or privileges you’re looking at or to generate a report on the selected items only.
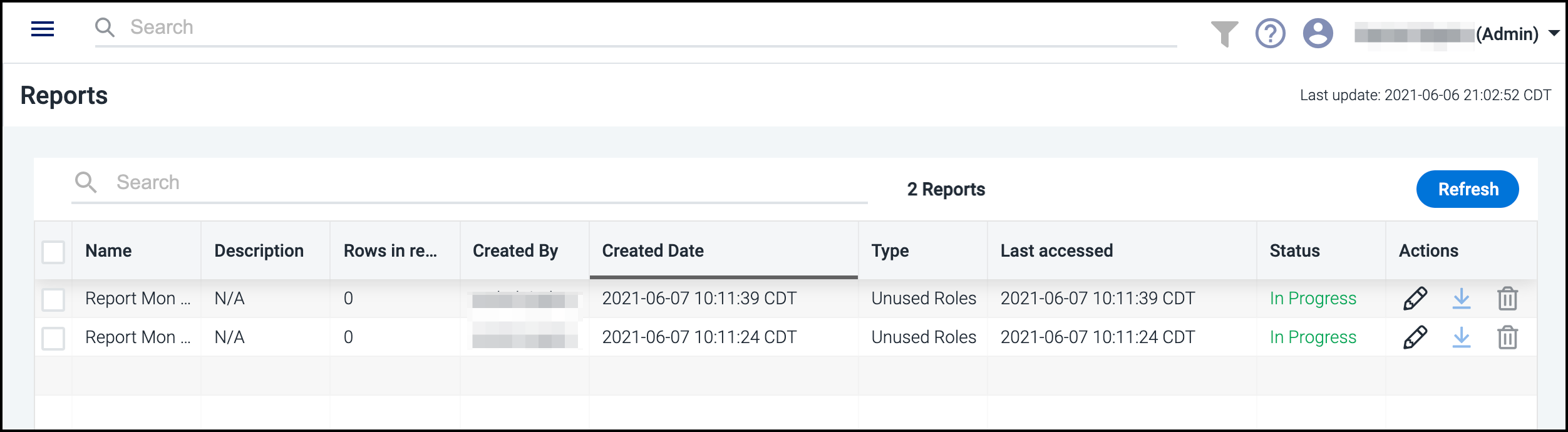
Generated reports are accessible by selecting Reports from the left navigation menu. There you can view all of the reports with descriptions, creator, type, and more.
Important
Reports are automatically deleted 30 days after they were last accessed. Five days before a report is removed, it will show an Expiring status to notify you of this action.
You can download or delete multiple reports at once. Select the checkboxes next to each report and choose the download ![]() or delete icon
or delete icon ![]() that appears above the Actions column. Multiple reports are downloaded as
that appears above the Actions column. Multiple reports are downloaded as .xlsx files in a .zip container.
To edit, download, or delete an individual report, select the edit ![]() , download
, download ![]() , or delete
, or delete ![]() icon in the Actions column. Editing allows you to change the name and description of the file.
icon in the Actions column. Editing allows you to change the name and description of the file.
Viewing High-Risk Privileges
Cloud Access Management detects all privileges associated with your cloud infrastructure and uses the information gathered to determine who has access to each privilege and how they are being used in your cloud environment. This is an essential first step to eliminating the security risks associated with excess privileges, including insider threats and breaches due to compromised credentials.
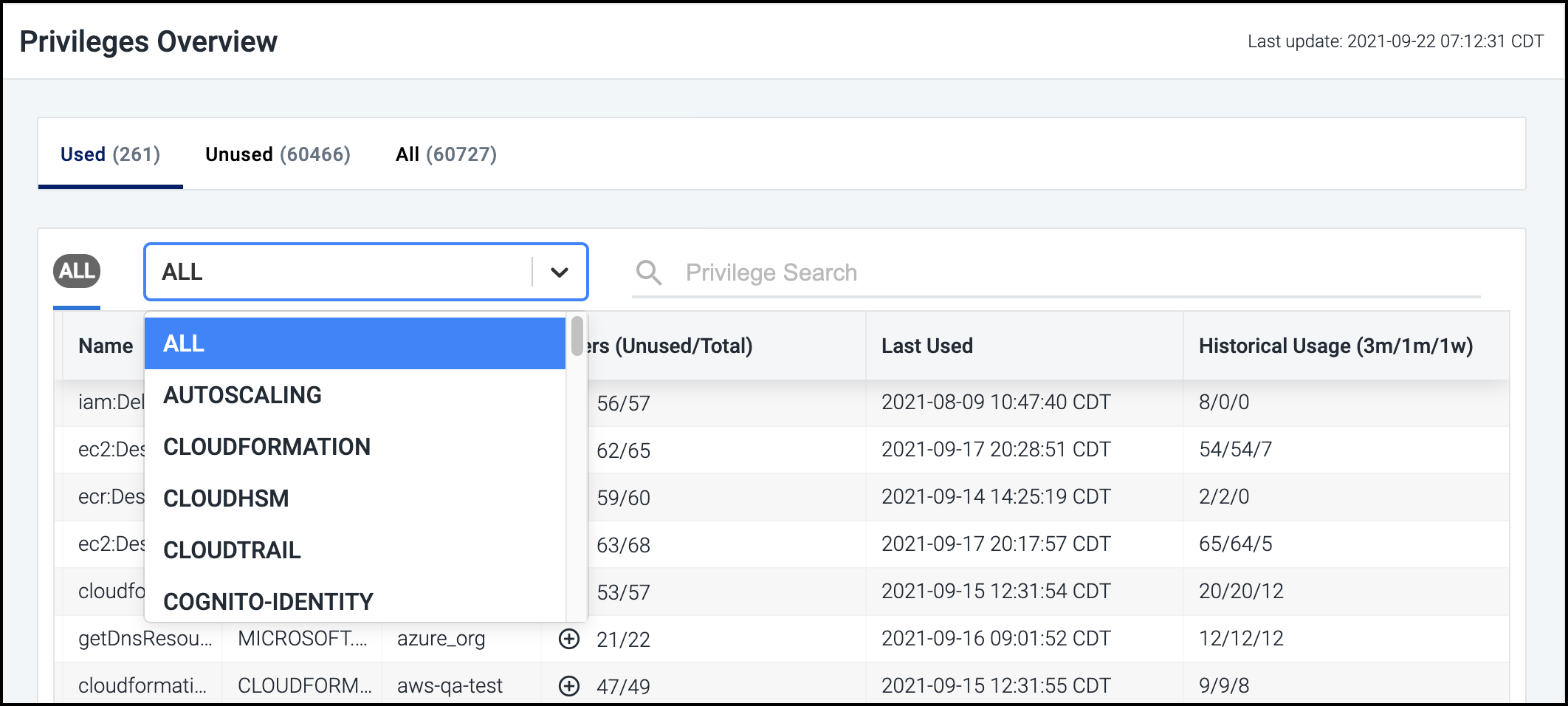
Select Privileges from the left navigation menu to display a list of the privileges that Cloud Access Management discovered, along with the following information for each:
-
the type of service each relates to
-
the associated cloud source
-
the total number of users with that privilege and how many aren't using it
-
the date and time that the privilege was last used (if applicable)
-
a summary of usage since you registered the source with Cloud Access Management
Tip
To display the names of the users with a specific privilege, select the expand icon ![]() in the Users column for the item.
in the Users column for the item.
You can filter the list by selecting the Used, Unused, or All headings, as well as by selecting a category from the dropdown list.
You can also use the search field above the list to search for all privileges related to specific objects or identities by name.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.