Configuring Google Cloud Platform
To configure Google Cloud Platform to work with Cloud Access Management, you'll need to set up the project, accounts, APIs, and roles with the minimum set of permissions required to display your organization hierarchy.
Use an administrator role in the Google Cloud Platform Console and follow the directions on this page to configure and register your GCP account with Cloud Access Management.
Creating Project and Service Accounts
You will need a project and attached service accounts to connect to your organization. Ensure that you have selected the organization as the scope.
Follow the Google Cloud documentation to:
-
Compute Engine Cloud Bigtable Admin Cloud Functions Cloud SQL Admin Cloud Logging Identity and Access Management (IAM) Cloud Resource Manager Admin SDK Cloud Key Management Service (KMS) BigQuery Additional APIs may be needed to process new types of resources.
-
Caution
The service account key allows the code to provide credentials to the API and will generate a JSON file. Any application can access the organization through this JSON file, so save it in a secure place.
You must now create a custom role to grant the service account access to an organization.
Granting Service Account Access to an Organization
Once you have created service accounts for the project, you must grant those accounts a set of read-only access to your Google Cloud Platform organization.
Follow the Google Cloud documentation to:
-
Create a custom role in your organization with the required permissions.
Required Permissions
Permission Description bigquery.datasets.get Get the specified dataset resource by ID bigquery.datasets.getIamPolicy Get the access control policy for a BigQuery Dataset bigquery.tables.get Get the specified table resource by ID bigquery.tables.getIamPolicy Get the access control policy for a BigQuery Table bigquery.tables.list List tables and relevant metadata bigtable.instances.getIamPolicy Get the access control policy for a BigTable Instance bigtable.instances.list List instances and relevant metadata bigtable.tables.getIamPolicy Get the access control policy for a BigQuery Table bigtable.tables.list List tables and relevant metadata cloudfunctions.functions.getIamPolicy Get the access control policy for a Cloud Function cloudfunctions.functions.list List functions and relevant metadata cloudfunctions.locations.list List locations and relevant metadata cloudkms.cryptoKeyVersions.list List crypto key versions and relevant metadata cloudkms.cryptoKeys.getIamPolicy Get the access control policy for a Cloud KMS crypto key cloudkms.cryptoKeys.list List crypto keys and relevant metadata cloudkms.keyRings.getIamPolicy Get the access control policy for a Cloud KMS key ring cloudkms.keyRings.list List key rings and relevant metadata cloudsql.databases.list List databases and relevant metadata cloudsql.instances.list List instances and relevant metadata compute.disks.getIamPolicy Get the access control policy for a compute disk compute.disks.list List disks and relevant metadata compute.firewalls.get Get the specified firewall resource by ID compute.firewalls.list List firewalls and relevant metadata compute.instances.getIamPolicy Get the access control policy for a compute instance compute.instances.list List instances and relevant metadata compute.networks.list List networks and relevant metadata compute.regions.list List regions and relevant metadata compute.routes.list List routes and relevant metadata compute.subnetworks.getIamPolicy Get the access control policy for a compute subnetwork compute.subnetworks.list List subnetworks and relevant metadata compute.zones.list List zones and relevant metadata iam.roles.list List roles and relevant metadata iam.serviceAccounts.getIamPolicy Get the access control policy for a service account iam.serviceAccounts.list List service accounts and relevant metadata logging.logEntries.list List logging entries resourcemanager.folders.getIamPolicy Get the access control policy for a folder resourcemanager.folders.list List folders and relevant metadata resourcemanager.organizations.get Get the specified organization resource by ID resourcemanager.organizations.getIamPolicy Get the access control policy for an organization resourcemanager.projects.get Get the specified project resource by ID resourcemanager.projects.getIamPolicy Get the access control policy for a project resourcemanager.projects.list List projects and relevant metadata storage.buckets.getIamPolicy Get the access control policy for a storage bucket storage.buckets.list List storage buckets and relevant metadata storage.objects.getIamPolicy Get the access control policy for a storage object storage.objects.list List storage objects and relevant metadata
Granting Service Account Access to the Domain
You must grant the service account access to your Google admin domain and determine the access and privileges assigned to your service account.
Follow the Google Identity documentation to delegate domain-wide authority to the service account.
- In the Client ID field, enter the client ID that was generated when you created the service account. This can be found in the Service Accounts details page.
- In the OAuth scopes (comma-delimited) field, add:
https://www.googleapis.com/auth/admin.directory.user.readonlyhttps://www.googleapis.com/auth/admin.directory.group.readonly
Configuring a Restricted Admin Role
Cloud Access Management must assume a Google Cloud Provider admin role to build the organization hierarchy and read identities (users, roles, groups). You can use the default admin role or configure a custom admin role with more restricted permissions.
To create an admin role with the minimum required permissions to be used by Cloud Access Management:
Follow the Google Workspace documentation to:
-
Create a custom role with the following privileges.
-
Organizational Units - Read
-
Users - Read
-
Groups - Select the checkbox.
-
Directory Sync - Manage Directory Sync Settings (which will automatically select Read Directory Sync Settings)
-
Corresponding Admin API privileges will be automatically selected.
-
-
Assign the role to an email that will be used to connect GCP with Cloud Access Management.
Note
You can also create a new user and assign the role to them.
Cloud Access Management will be able to assume the role with the set permissions when you register your GCP organization.
Using the Command-Line Interface
You can optionally set up your GCP configuration using the command-line interface. Follow the Google Cloud documentation to install and initialize the gCloud CLI.
Registering Your Google Cloud Platform Organization
Once you have the necessary roles and permissions in your organization, you must register it with Cloud Access Management.
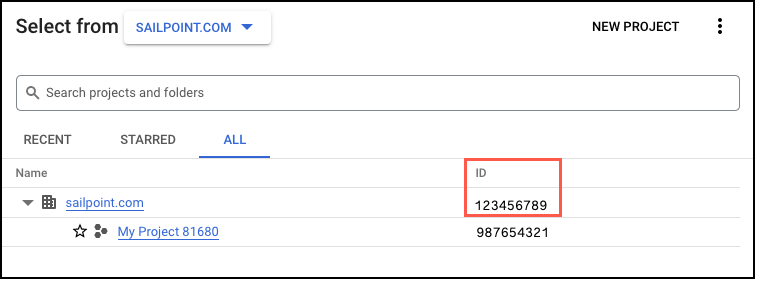
- In the Google Cloud Platform console, select the dropdown menu with your project or organization name.
-
Select the All tab and copy the organization ID.
-
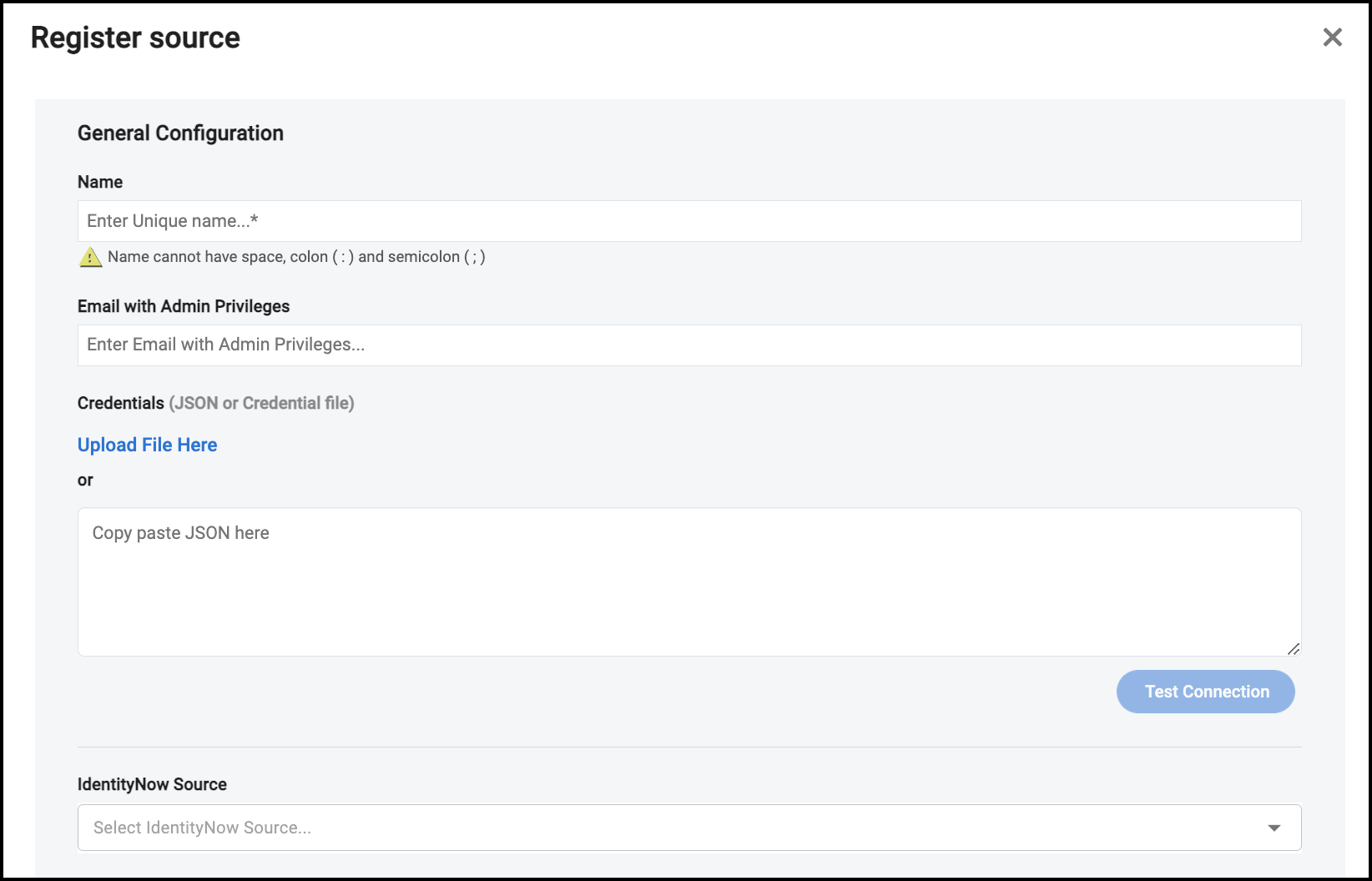
In Cloud Access Management, name the source or paste the organization ID.
-
Enter your administrator email. This email must have admin access to Google Admin. The domain must be the same as the organization name. For example, if the organization name is "testorg.com", then the admin email will need to be formatted like "smith@testorg.com".
-
Upload or paste the JSON file you received when creating the key for the service account.
-
If you have a correlated source in Identity Security Cloud, the Identity Security Cloud source dropdown menu will display. Refer to Correlating Identity Security Cloud Identities for more information.
Documentation Feedback
Feedback is provided as an informational resource only and does not form part of SailPoint’s official product documentation. SailPoint does not warrant or make any guarantees about the feedback (including without limitation as to its accuracy, relevance, or reliability). All feedback is subject to the terms set forth at https://developer.sailpoint.com/discuss/tos.