Configuring Microsoft Entra ID as an SSO Identity Provider
You can configure Identity Risk as an enterprise application with Microsoft Entra ID to enable SSO. This configuration supports Service Provider Initiated (SP-initiated) SSO and Just-In-Time (JIT) provisioning.
Prerequisites
To get started, you'll need the following:
Microsoft Entra:
- The
Tenant IDfor your organization. - A user with the appropriate administrator privilege to configure a new enterprise application for Identity Risk.
Identity Risk:
- Your organization's Identity Risk tenant.
- A user with the appropriate administrator privilege to assign roles to new users.
Configuring SSO Integration
You must initiate SSO integration with Entra ID in Identity Risk. This provides the necessary configuration required to register Identity Risk with Microsoft Entra ID.
- Select
 in the upper-right corner of Identity Risk.
in the upper-right corner of Identity Risk. - Select SSO.
- On the SSO Integration page, select Entra ID as the SSO provider.
-
Copy the Microsoft Entra ID
Reply URLandIdentifier (Entity ID)and save it somewhere accessible. You'll need this information to register Identity Risk in Microsoft Entra ID.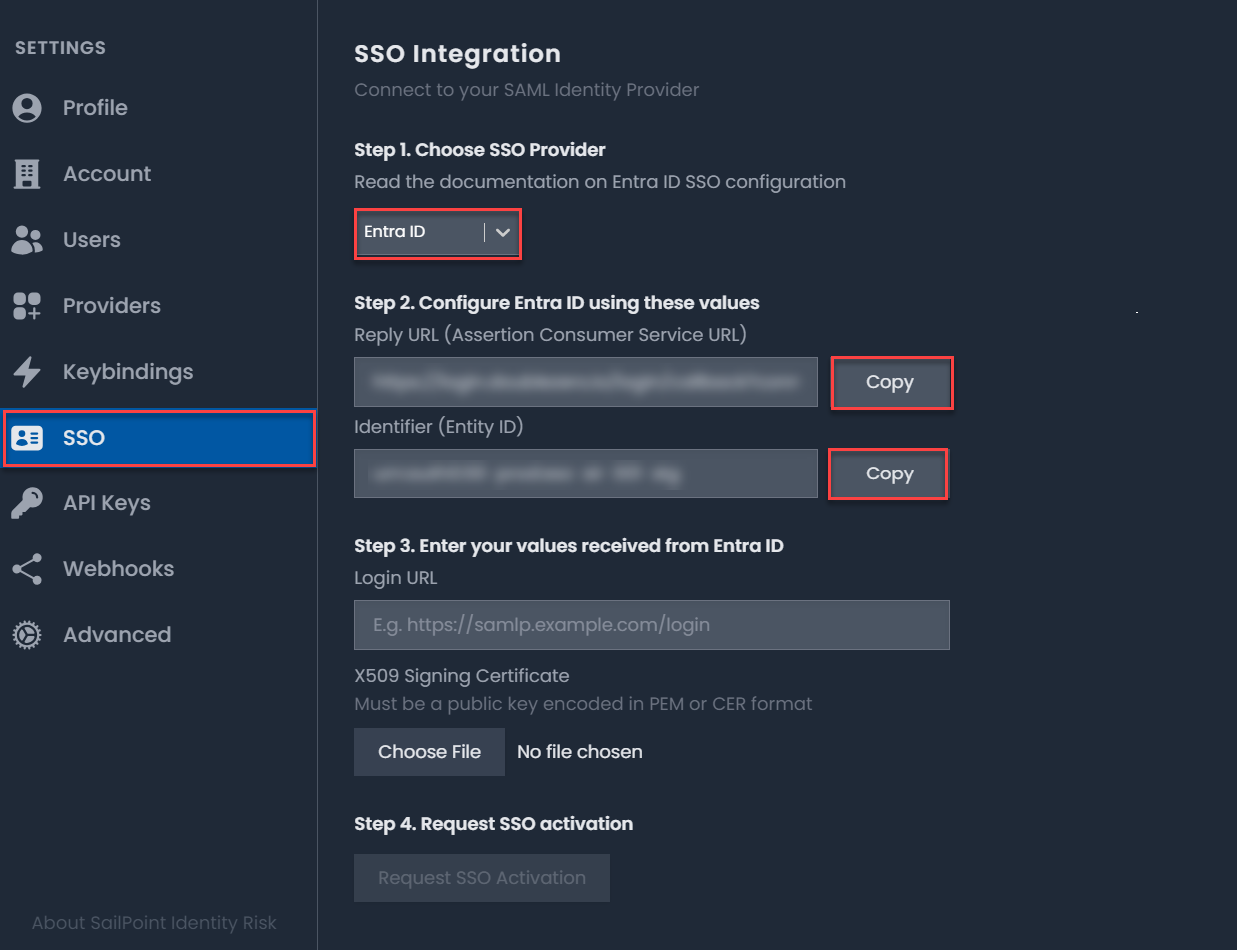
Note
Do not close the SSO Integration page. You'll return here to complete the configuration.
Registering Identity Risk with Microsoft Entra ID
You can now register Identity Risk as an Enterprise Application with Microsoft Entra ID.
- Select Microsoft Entra ID in your Microsoft Azure portal.
- On the left, select Enterprise applications and select New Application.
- Under Browse Microsoft Entra Gallery, select Create your own application.
- Enter a name for your Identity Risk application.
- Select the option Integrate any other application you don't find in the gallery (Non-gallery).
- Select Create to add the application.
- In [Your Application] | Overview, go to Set up single sign on and select Get started to configure the SSO method.
- In Single sign-on, select SAML as the method.
- In Set up Single Sign-On with SAML go to Basic SAML Configuration and select Edit.
- In Basic SAML Configuration, select Add Identifier and copy the
Identifier (Entity ID)value from Identity Risk > Settings > SSO and paste it into the Identifier (Entity ID) field. -
Go to Add reply URL, copy the
Reply URLvalue from Identity Risk > Settings > SSO and paste it into the Reply URL (Assertion Consumer Service URL) field.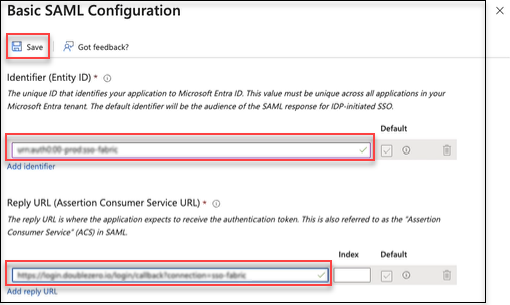
-
Select Save.
- In SAML-based Sign-on, go to Attributes and Claims and select Edit.
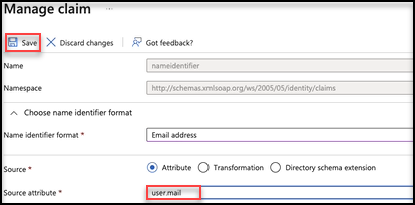
- Go to Attributes & Claims > Claim name and select Unique User Identifier (Name ID).
- Go to > Manage claim and select Source attribute. Select
user.mailfrom the dropdown list. -
Select Save.
-
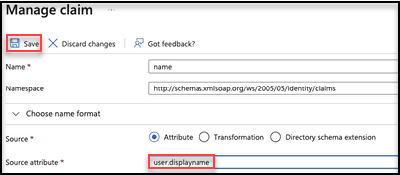
Go to Attributes & Claims > Additional claims and select Claim name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name.
- Go to Manage claim and select Source attribute. Select user.displayname from the dropdown list.
-
Select Save.
-
Close Attributes & Claims.
- Go to SAML Certificates and select Download for Certificate (Base64) to download the X.509 Certificate.
- Go to Set up and copy the Login URL.
Completing Microsoft Entra ID SSO Integration
- On the SSO Integration page of Identity Risk, paste the Login URL copied from the Microsoft Azure Portal > Set up into the Login URL field.
- In X509 Signing Certificate, select Choose file.
- Upload the X.509 Signing Certificate downloaded from the Microsoft Azure Portal > SAML Signing Certificates.
- Select Request SSO activation.
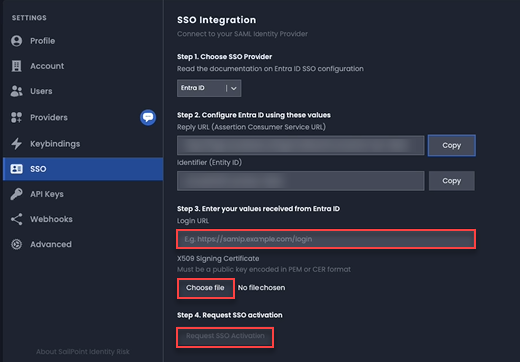
A support ticket will be submitted to Identity Risk. Once provisioning is successfully completed, you will receive a notification to confirm SSO is available for your tenant.
Onboarding a Microsoft Entra ID SSO User
Once your SSO Integration with Microsoft Entra ID is enabled, test the SSO connection for an initial user. This process can be followed to enable new users assigned access through Microsoft Entra ID can access Identity Risk.
Each new user will be Just-In-Time provisioned in Identity Risk on their first login through the SSO. However, an Identity Risk administrator must assign the user a role before they can complete their login.
- In the Microsoft Azure portal, assign users and group to enable access to the Identity Risk application.
-
The user navigates to Identity Risk portal Login page and selects the Continue with Microsoft SSO login option.
Note
The user should be provided with the Identity Risk application URL or told to access the application through the Microsoft Azure portal > My Applications page.
-
The user's first login and successful authentication through Entra ID SSO triggers:
- The automatic creation of the user's account in Identity Risk.
-
A welcome email sent to the user. This email notifies the user that although they have successfully authenticated in to Identity Risk, they have not been assigned a role. The user must contact an administrator to assign roles before continuing.
Note
An Identity Risk administrator is not automatically notified, so the user is required to contact an administrator.
-
Identity Risk administrator assigns a role to the new user via the Identity Risk > Settings > Users > Users and Roles page.
Note
Users automatically created from an SSO Integration will have a tick in the SSO column.
-
The user selects the Try Again button to successfully complete their login.
Onboarding a Microsoft Entra ID SSO User through Entitlements
An entitlement can be created and delegated to a user by an administrator or requested by a user in the Request Center.
To allow users to request an entitlement:
- Assign a group to the Entra ID enterprise application created when Configuring SSO Integration in Identity Risk.
- Configure Identity Risk as a source in Identity Security Cloud.
- Identity Risk Entra ID SSO entitlement granted by an Identity Security Cloud administrator or requested from the request centre by a user.
Troubleshooting
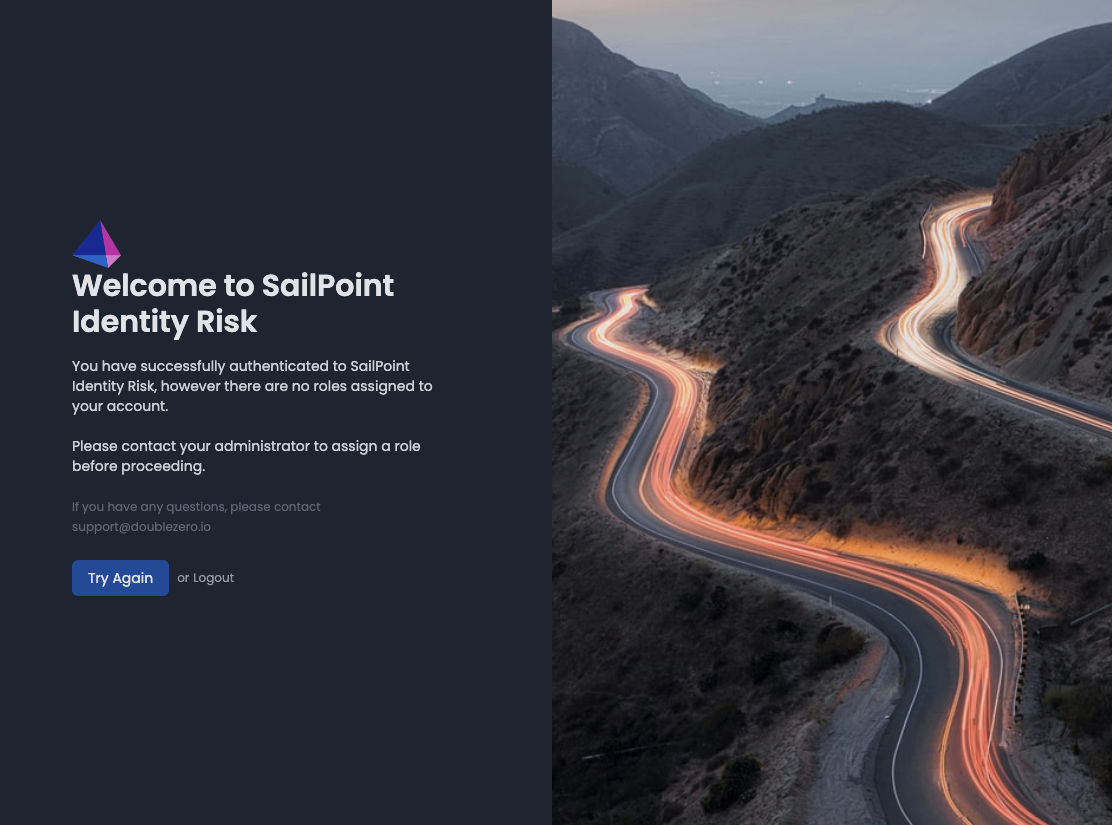
If a user receives the following message when they log in, their Identity Risk account was not configured correctly.
Welcome to Identity Risk
You have successfully authenticated to Identity Risk; however, there are no roles assigned to your account.
Please contact your Identity Risk administrator to assign a role before proceeding.
The Identity Risk administrator needs to assign an appropriate role to the newly created user via the Settings > Users > Users and Roles page before the user can successfully log in.
Notes
Local account access may be disabled for preexisting users once testing is complete and the necessary role assignments are in place.