Getting Started
Welcome to SailPoint Identity Risk.
Identity Risk expands and strengthens your organization's identity security by enabling you to detect, analyze, and respond to active and latent threats.
This guide will help you access your Identity Risk tenant, connect your organization's SSO, and configure providers.
Accessing Identity Risk
When your Identity Risk tenant is created, SailPoint will send you a welcome email that includes a link to reset the password for your Identity Risk account. If you're the initial user, you will be assigned the Owner role, which grants you administrative permission to add other user accounts, integrate SSO providers, and configure providers.
Adding Additional Users
If you are the initial user or a user with the Owner role, you can add additional users and assign them roles, depending on the access they require. Users can also be added through your organization's SSO if you integrate it with Identity Risk.
Configuring Your SSO
Identity Risk integrates with external SSO providers to provide a streamlined user experience for authentication to multiple applications.
You can integrate Identity Risk with the following SSO identity providers:
Configuring Providers
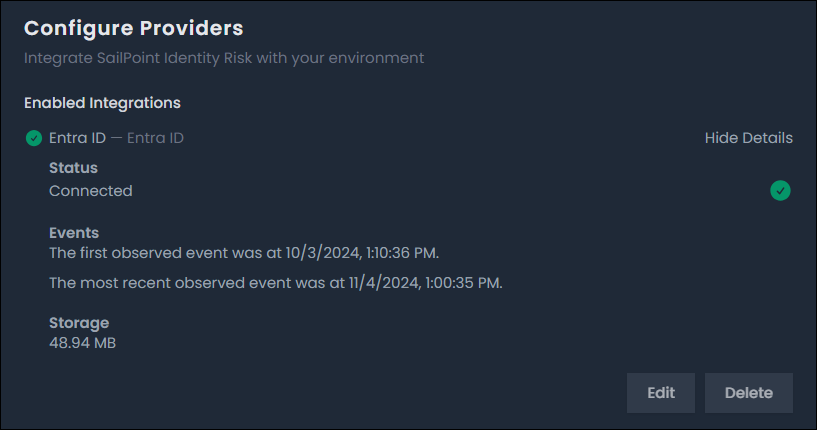
To ingest your data in to Identity Risk, you'll configure a provider in the Settings panel. SailPoint recommends configuring an identity provider such as Entra ID or Okta as your first data source. You can then supplement this data by adding additional providers.
Identity Risk integrates with the following providers:
Once a provider is successfully connected and active, its status will change to "Connected". The provider's first and most recent observed events will also populate and update as reported.
After a few minutes, your organization's data will populate in the following pages:
- Insights - Review five information panels to understand the trends, behaviors, and potential risks that affect your organization's identity security.
- Identity Map - Visualize and explore identities and their behaviors across devices, applications, and resources.
- Permissions Navigator - Explore the authentication and access policies configured in your identity platforms.
- Trust - Evaluate sessions to discover and remediate malicious activity in your organization.