Configuring Trust Policy
Configuring trust policy is a key part of evaluating sessions and identifying potentially malicious activity.
Creating a Trust Policy
To configuring a trust policy to evaluate activity and behavior:
- Select the Menu icon > Trust.
-
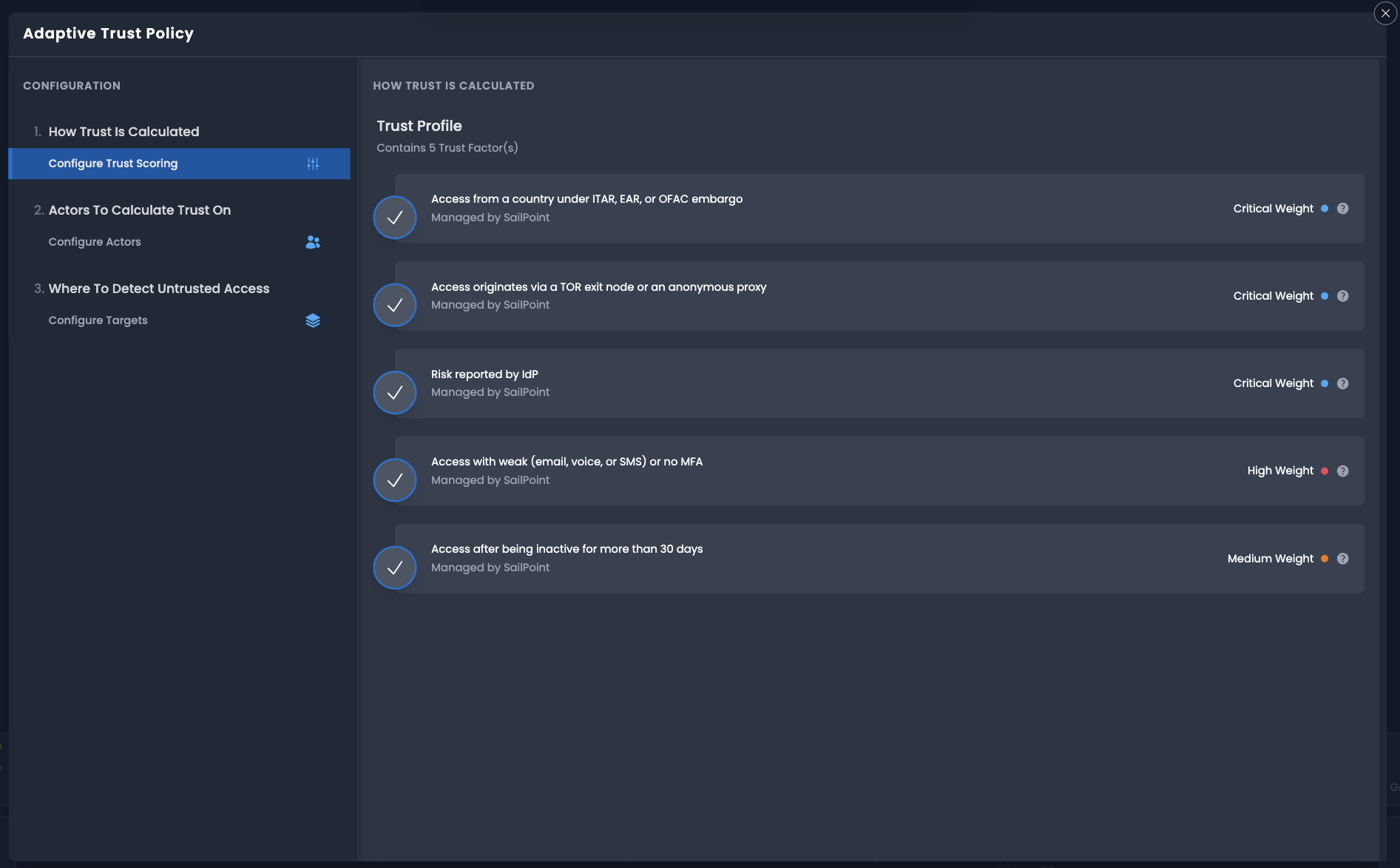
Select Configure Trust Scoring to build your trust profile that includes a set of trust factors and the associated weight for each factor.
Factor weights determine the factors impact on a sessions trust score. Factor weights may be set to critical, high, medium, or low. A critical factor weight will be weighed most heavily during session scoring. Factors with a low weight will be weighed least heavily during session scoring.
Note
Factors and their weights are not currently configurable.
-
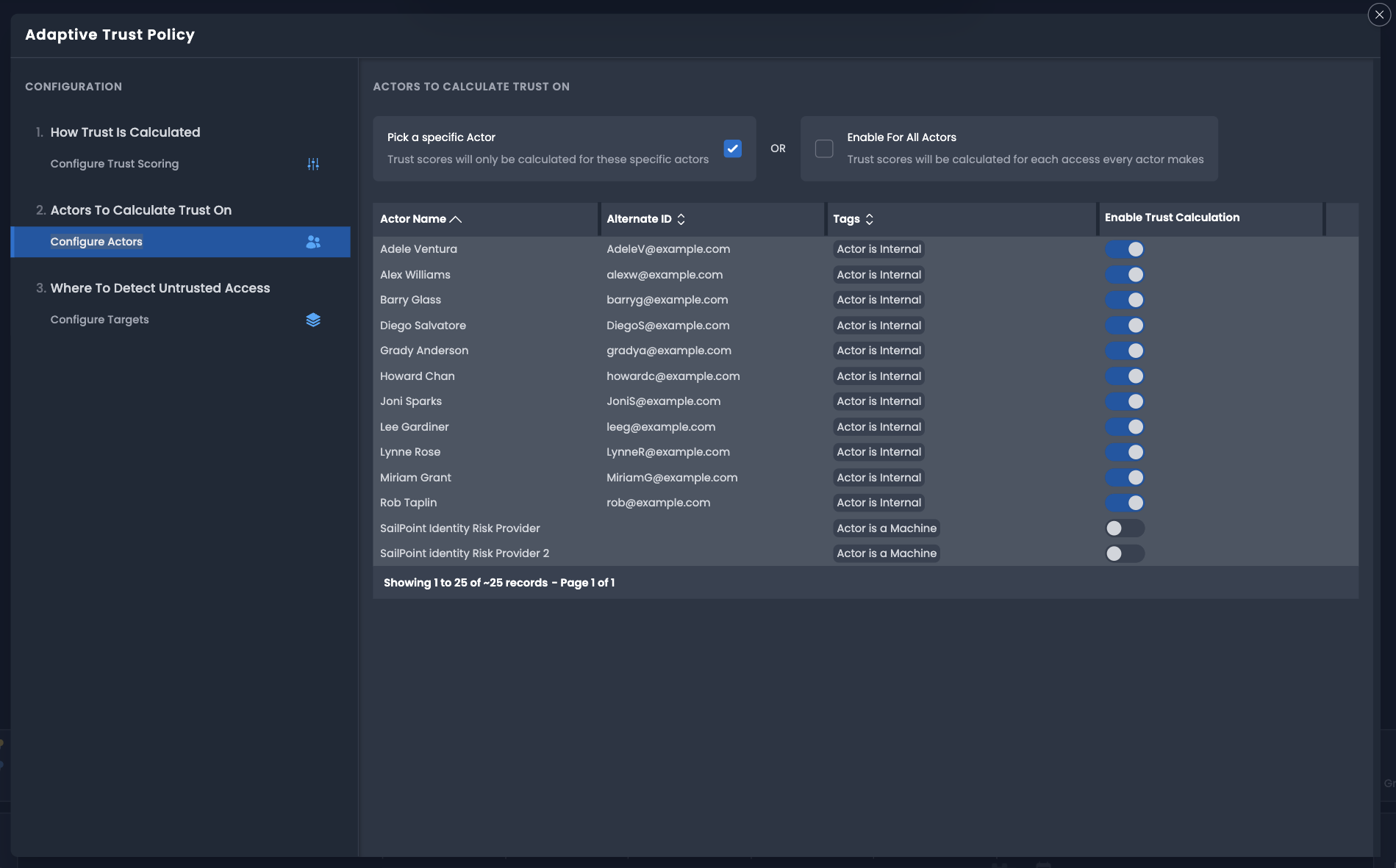
Select Configure Actors to determine which actors in your environment should be evaluated. The policy can be applied to individual actors regardless of whether they are a actor, human or machine.
- To select a subset of actors, select Pick a specific Actor. To view more actors in this list, page through the results by selecting the arrows at the bottom of the panel. Alternatively, select Enable For All Actors to apply to all actors.
-
Select the Enable Trust Calculation toggle to add an actor.
-
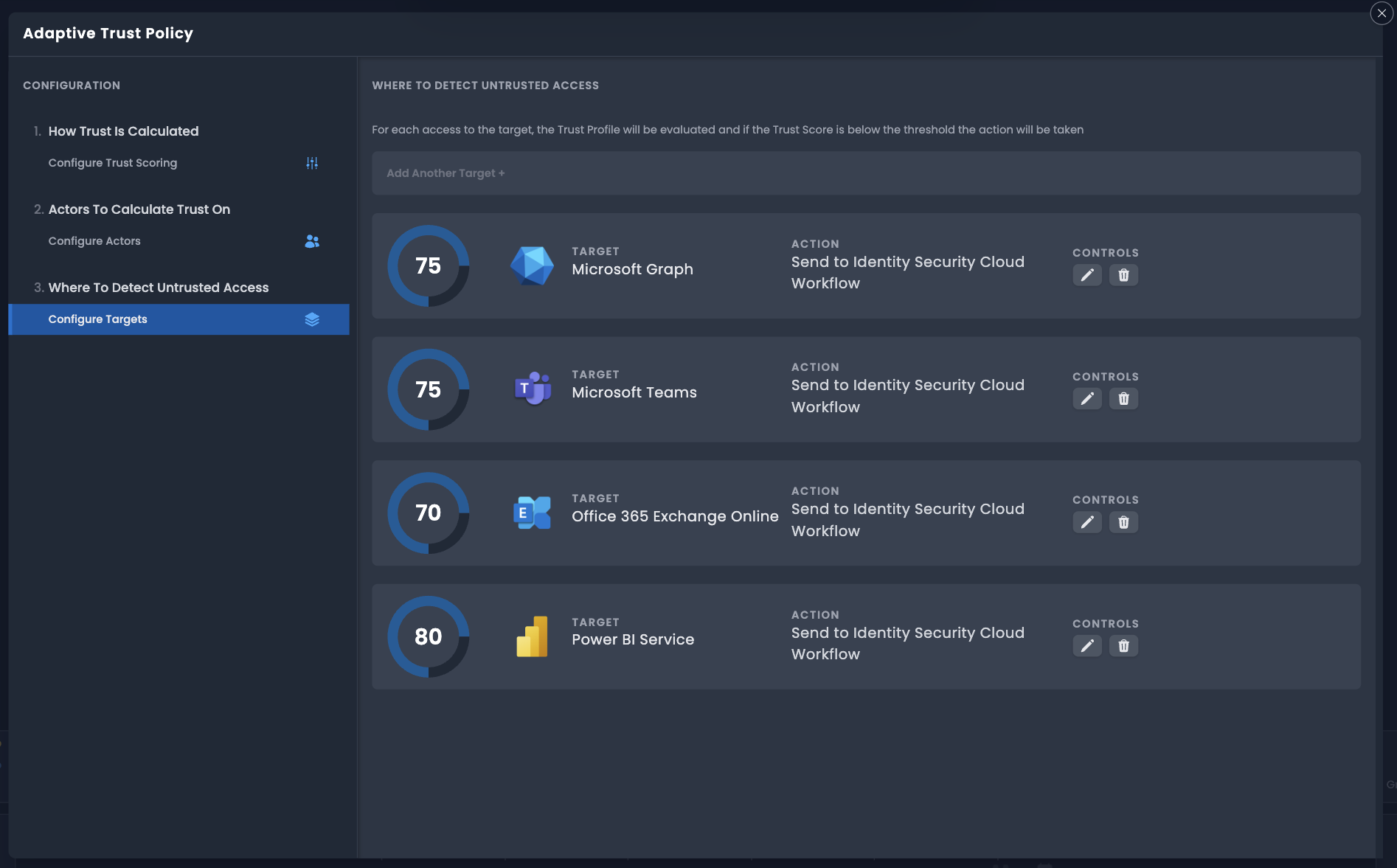
Select Configure Targets. The final step is to map a trust profile to a set of target applications.
- In WHERE TO DETECT UNTRUSTED ACCESS, select Add Another Target +.
- Select Choose Target and select a target from the dropdown.
-
Select Threshold and enter a trust threshold for the application. The threshold is the minimum trust score required to access this application without triggering a response action.
For example
Setting a threshold of 75 will require a score equal to or greater than 75 to access the application. A score lower than 75 will automatically trigger a response action. It is recommended that critical applications have a higher threshold.
-
Select Action and select an action from the dropdown. Available response actions are:
- Disable - Action is not executed.
- Send to Identity Security Cloud Workflow - Invokes a SaaS Workflow triggered by the Identity Risk Detected trigger.
-
Select Add Policy to save the configuration.
-
Repeat the process for other target applications.
Once configured you'll see trust scoring data begin populating in Insights and associated actor and target profiles. While trust scoring is valuable information for determining anomalous or potentially malicious activity, leveraging Workflows will provide an automated response to activity which does not meet the defined trust policy.
Using Workflows
Leveraging Workflows allows you to configure an automated response to activity that does not meet the defined trust thresholds for the application.
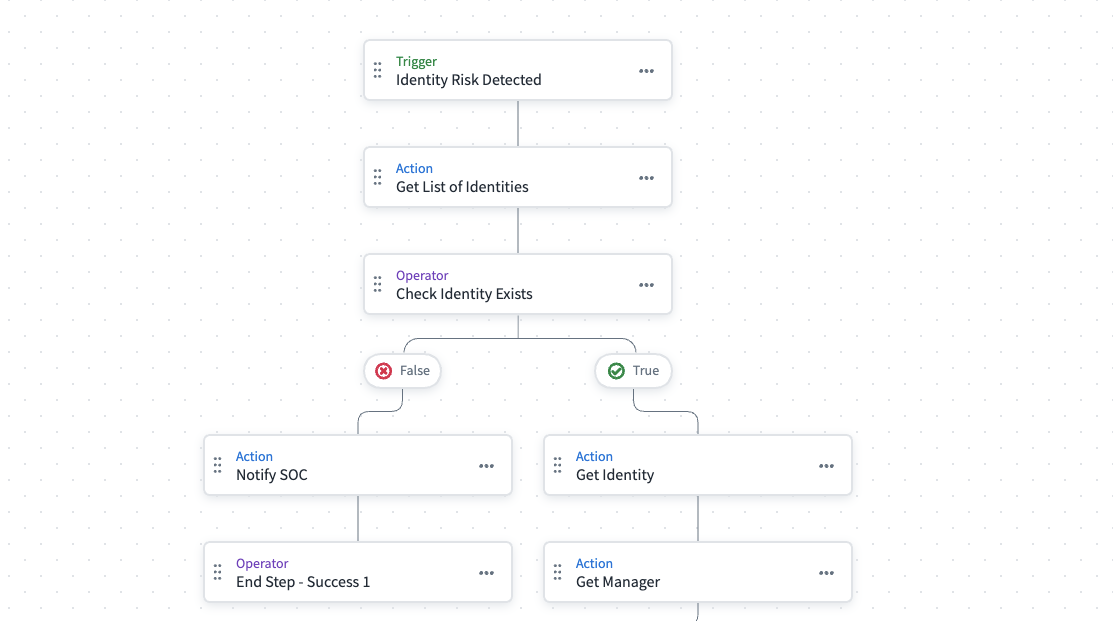
To build an automated workflow in SailPoint's cloud services, you can use the visual builder or you can configure a workflow using JSON. To begin building a workflow, go to Admin > Workflows. Use the Identity Risk Detected trigger to run when a session activity matching the policy is evaluated and results in a trust score below the defined threshold.
For more information about workflows, refer to Identity Security Cloud Workflows.
Workflow Example
Note
Trust scores are calculated on a session-by-session basis, to reduce the risk of overwhelming recipients with notifications, we strongly recommend that thorough testing occurs prior to enabling a workflow.
Viewing Trust Scores
Trust scores can be viewed on the dashboard, as follows:
-
Insights - Trust and Access pages. Provides high level metrics and statistics on the state of trust across your environment. Identify low-trust sessions and view aggregated trust scores.
-
Identity Map - Actor Profile and Target Profile. Actor Profile trust scores can be viewed for that actor over the specified time range. Target Profile trust scores can be viewed for that target over the specified time range.