Creating a Chat Application Proxy for IdentityIQ in Azure
The Chat Proxy application acts as an Azure Entra Application Proxy, securing the Azure bot message endpoint (/api/messages) to facilitate communication between Microsoft Teams and IdentityIQ application running in your enterprise. By establishing an Entra proxy URL for the Microsoft Teams bot server endpoint, it ensures that messages sent from Microsoft Teams to the bot are securely routed. This setup leverages Azure Entra's capabilities to provide authenticated access, apply conditional access policies, and terminate traffic in the cloud, thereby enhancing security and compliance.
Note: It is essential to follow the specified sequence of steps as mentioned in the document when creating the necessary applications for integrating IdentityIQ with Microsoft Teams. For a visual guide to the recommended setup order, refer to Best Practices for Configuring IdentityIQ Microsoft Teams.
Important: This guide ONLY provides instructions for configuring specific Azure component configurations required to support IdentityIQ’s Notifications and Access Request Approval work item features in Microsoft Teams. It is intended as an aid to implementers but should be used in conjunction with Microsoft’s official documentation to ensure access to the most accurate and up-to-date information. For broader information on Azure or general setup tasks related to Microsoft Teams and SSO, please refer to Microsoft's official documentation.
Perform the following steps to create a Chat Application Proxy in Azure:
-
Sign into Azure portal and navigate to your Microsoft Entra ID.
-
Under Manage > Enterprise applications, select + New application.
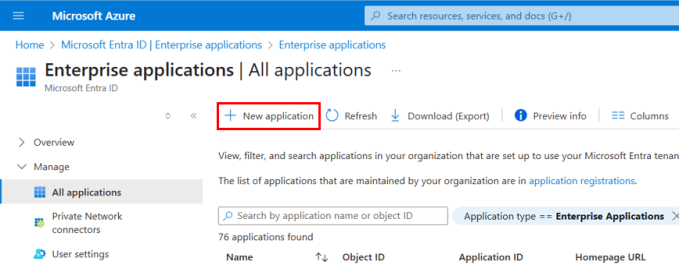
-
On the Microsoft Entra Gallery page, select Add on-premises application.
-
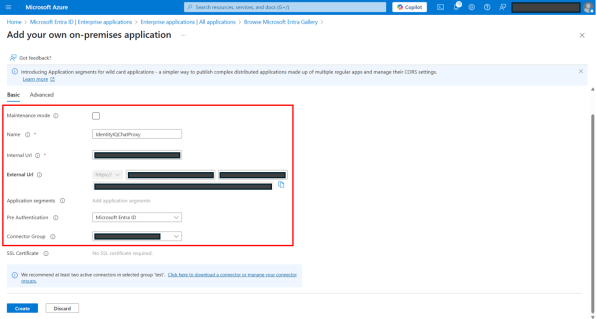
On the Add application page, provide the following details:
-
Under the Basic tab:
-
Maintenance mode – Keep it unselected. This is the maintenance page that users see during maintenance and downtime events.
-
Name – Name of your Chat Application Proxy in Azure. See Best Practices for Configuring IdentityIQ Microsoft Teams to define an appropriate application name.
-
Internal Url – Add the Internal Url in the format; https://<VM Name Bot Server URL>:<PORT>/<IdentityIQ Teams APP ID without Dashes>/api/.
Note: This URL is the bot server private bot endpoint within your enterprise that the public proxy will direct messages to.
-
External Url – An auto-generated external URL with application name options as input. The URL can be customized.
Note: This is your bot server public endpoint which Microsoft Teams will communicate with for IdentityIQ chat. The bot messaging endpoint is securely exposed externally to Microsoft Teams via an Entra Id proxy. Only secured messages from Microsoft Teams can be successfully processed by the messaging endpoint.
-
Pre Authentication – Attribute for pre authentication. By default, Microsoft Entra ID is selected. Select Passthrough from dropdown.
-
Connector Group – Select the appropriate connector group from the dropdown.
-
-
Under the Advance tab, select Validate Backend SSL certificate checkbox.
Note: If your virtual machine (VM) does not have a valid certificate, unselect the Validate Backend SSL certificate checkbox.
-
Select Create.
-
You now have successfully created a Chat Application Proxy in Azure. For next step, refer Creating an Azure Bot for IdentityIQ's Microsoft Teams .