Troubleshooting
If you encounter any of the following issues or errors, SailPoint recommends that you follow the guidance provided below to resolve the error before contacting SailPoint Support.
Issue: The approval rule configuration does not populate approvals in ServiceNow.
Resolution: Allow the timer to complete. A new 32 minute timer is present between the Check for IdentityNow configuration and Get IdentityNow Pending Approvals workflow of SP_SPNT_SNOW_INT_CreateSailpointAccessRequest. Additionally, the previous 1 minute timer after the approval request has been updated to 32 minutes for the second level approver and onwards.
Resolution: Perform the following steps to remove the dependency.
-
Sign in to ServiceNow using admin credentials.
-
Change the Application Scope to SailPoint IdentityNow for Service Catalog.
-
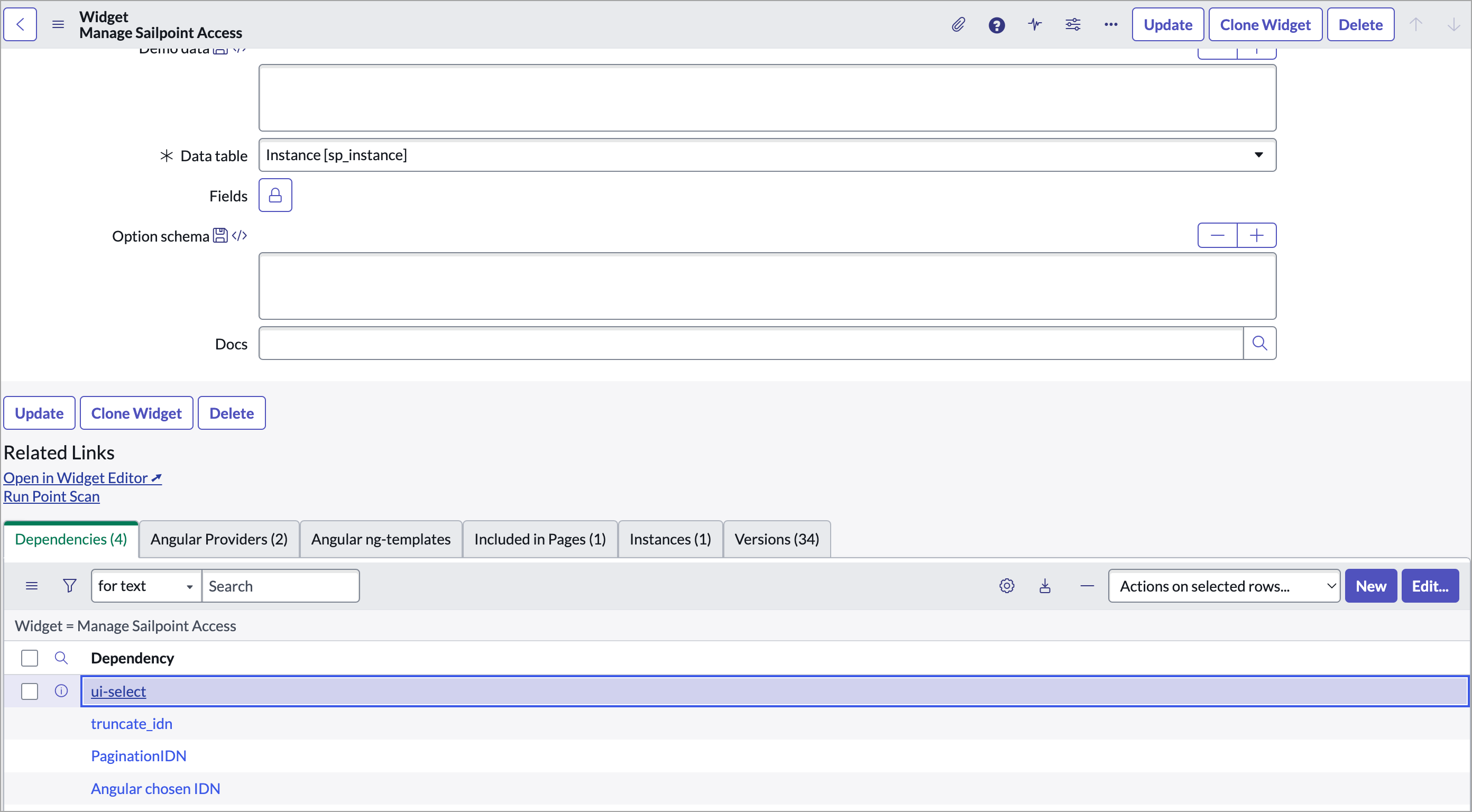
Search widgets in the application navigator, and open the widgets module under Service Portal.
-
Open the widget for Manage SailPoint Access, and scroll to the dependencies. Select the ui-select dependency, then select the Edit button.
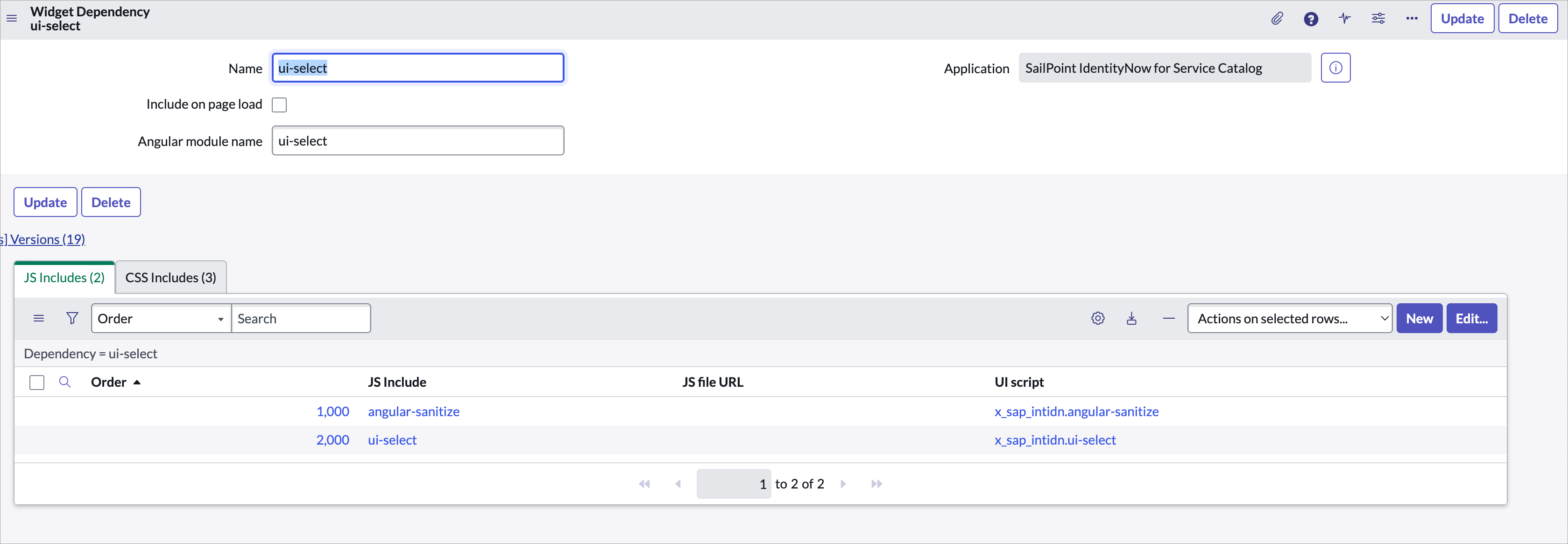
-
On the JS Includes tab, select the Edit button.
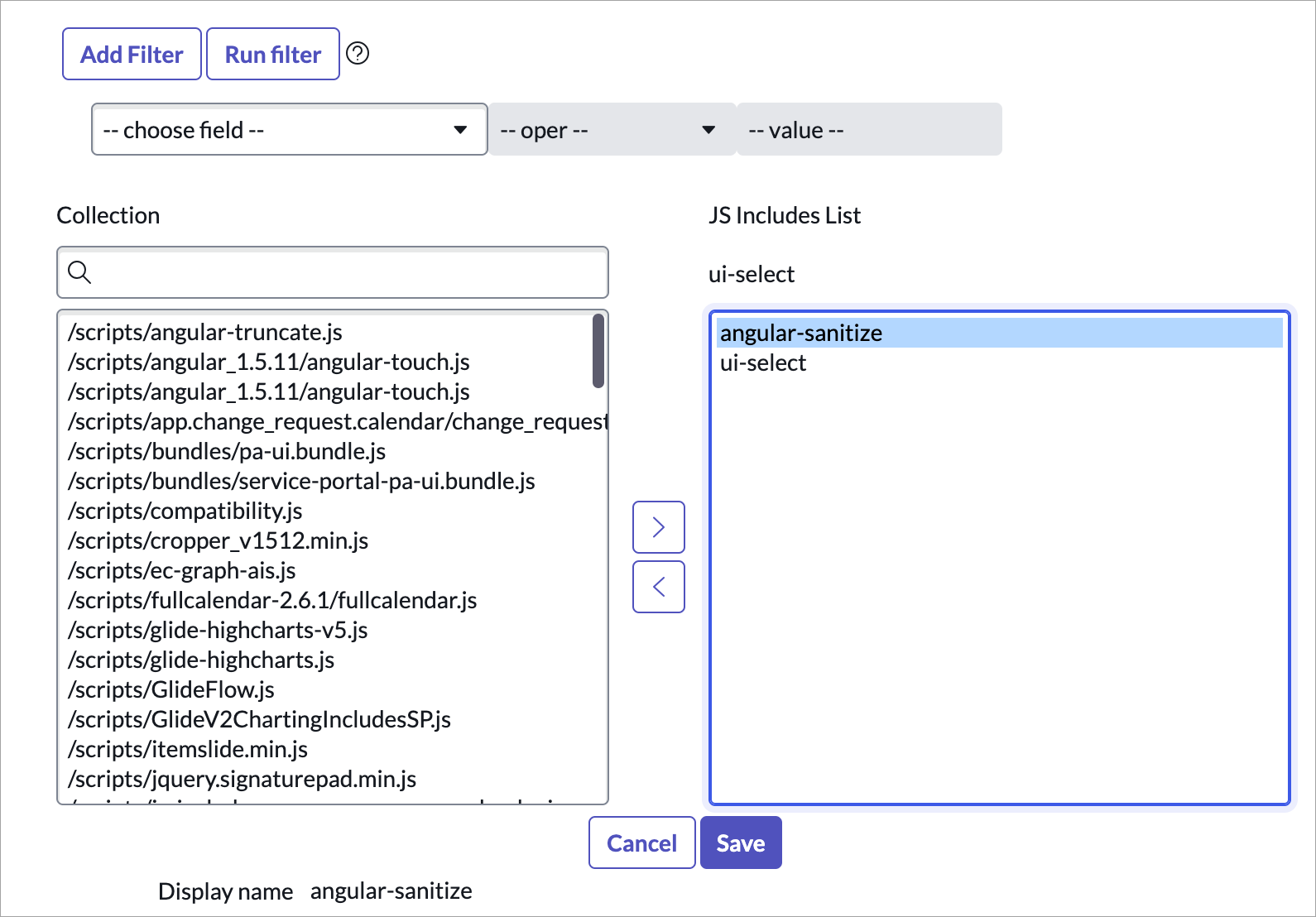
-
From the JS Includes List, highlight
angular-sanitizeand press the < button to move it back to the Collection. Select Save. -
On the widget page for Manage SailPoint Access, select the Update button.
Issue: The approval request fails with the following error: Failed creating access request. IDN user session is expired.
Resolution: Provide the x_sap_intidn.user role to the approvers.
Issue: The recommendations tab is visible although you did not opt for an IAI license.
Resolution: Perform the following steps to update the script and insert a new API link.
Update the Script:
-
Open ServiceNow as Admin and enter
Script Includesinto the search field. -
Select Script Included under System Definition.
-
Open the
SP_SPNT_SNOW_INT_GetOrgInfoscript include. -
Copy and paste the following code into the script section, and then select Update.
var SP_SPNT_SNOW_INT_GetOrgInfo = Class.create();
SP_SPNT_SNOW_INT_GetOrgInfo.prototype = Object.extendsObject(
SP_SPNT_SNOW_INT_Common, {
/*_________________________________________________________________
* Description: A method that is calls the API and check if access request recommendation is enabled in IDN
* Parameters: void
* Returns: boolean
________________________________________________________________*/
isRecommendationEnabled: function() {
if (!this.getRecommendationsProductFlag()) {
return false;
}
if (!this.getRecommendationsFeatureFlag()) {
return false;
}
return true;
},
/*_________________________________________________________________
* Description: A method that calls the API associated with link 'getTenantInfo' and returns the response for further processing
* Parameters: void
* Returns: boolean
________________________________________________________________*/
getRecommendationsProductFlag: function() {
try {
var recProductFlagEnabled = false;
var action = 'getTenantInfo';
var accessTokenServiceAccount = this.authScript.getServiceAccountAccessToken();
var request = this.createHttpRequest('GET', action, {
headers: {
Authorization: 'Bearer ' + accessTokenServiceAccount
}
});
request.setEndpoint(this.getEndpointUrl(action));
var response = request.execute();
var statusCode = response.getStatusCode();
if (statusCode === 200) {
var responseBody = response.getBody();
var res = JSON.parse(responseBody);
res.products.forEach(function(product) {
if (product.productName == 'iai') {
recProductFlagEnabled = product.licenses.some(function(feature) {
return feature.licenseId == 'iai:recommendations';
});
}
});
return recProductFlagEnabled;
}
return false;
} catch (ex) {
gs.error('Error when trying to get product flag info: ' + ex.message);
return '';
}
},
/*_________________________________________________________________
* Description: A method that calls the API associated with link 'getOrgInfo' and returns the response for further processing
* Parameters: void
* Returns: Object
________________________________________________________________*/
getRecommendationsFeatureFlag: function() {
try {
var action = 'getOrgInfo';
var accessTokenServiceAccount = this.authScript.getServiceAccountAccessToken();
var request = this.createHttpRequest('GET', action, {
headers: {
Authorization: 'Bearer ' + accessTokenServiceAccount
}
});
request.setEndpoint(this.getEndpointUrl(action));
var response = request.execute();
var statusCode = response.getStatusCode();
if (statusCode === 200) {
var responseBody = response.getBody();
var orgInfo = JSON.parse(responseBody);
return orgInfo.iaiEnableAccessRequestRecommendations ? true : false;
}
return false;
} catch (ex) {
gs.error('Error when trying to get org info: ' + ex.message);
return '';
}
},
type: 'SP_SPNT_SNOW_INT_GetOrgInfo'
}
);
Insert a new Identity Security Cloud API link:
-
Open ServiceNow as Admin and enter
IdentityNow Linksinto the search field. -
Select IdentityNow Links under SailPoint IdentityNow for Service Catalog.
-
Select the New button, and add the following:
Action:
getTenantInfoLink:
/beta/tenant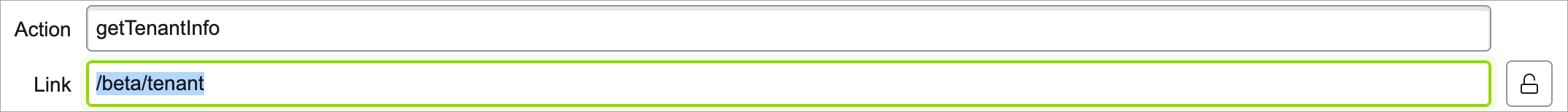
-
Select Save.
Issue: Inactive members in the Identity Security Cloud governance group cause ServiceNow approvals to be skipped and requested items to be canceled.
Resolution: When the Approval Flow is set to Configurable approval and the applicable approval definition for an item is set to be Identity Security Cloud Workflow, ServiceNow skips the approvals and cancels the requested item. This happens if any of the approvers in the Identity Security Cloud governance groups are missing or inactive in ServiceNow. This is the expected behavior as integration expects all of the approvers to be valid in ServiceNow. Perform the following to customize this behavior to allow the approvals to be requested even if only one member of the governance group is present and valid in ServiceNow:
-
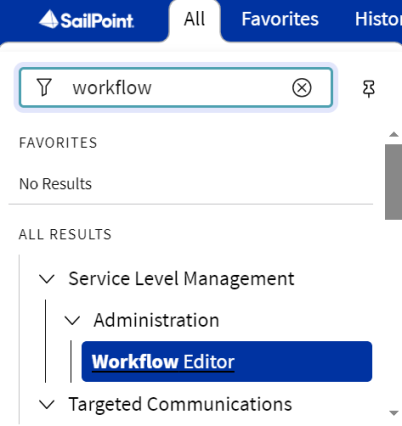
Sign in as admin in your ServiceNow instance, and go to Workflow Editor.
-
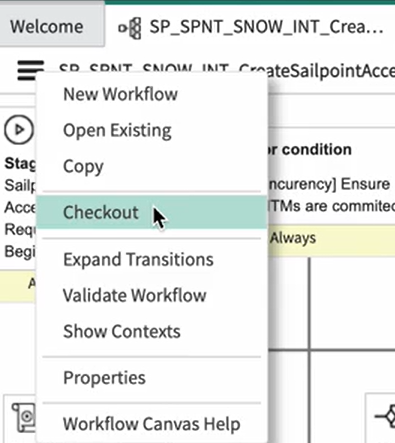
Open the
SP_SPNT_SNOW_INT_CreateSailpointAccessRequestworkflow, and checkout the workflow using the Checkout option. -
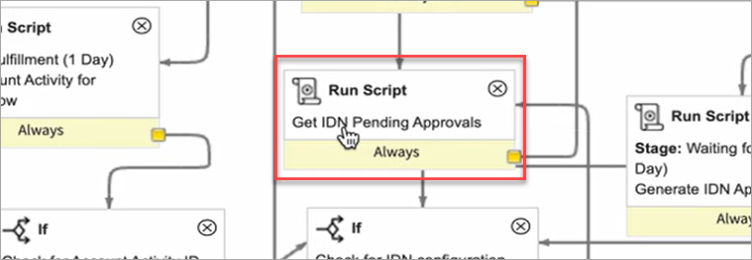
Double-click Get IDN Pending Approvals and run the script activity to edit it.
-
Replace the code in the script tag with the following code.
Copy(function(current) {
workflow.scratchpad.pendingApprovals = [];
var approvalsService, action, accessToken, pendingApprovals, grUser, authScript, result, allApproversMissing;
approvalsService = new x_sap_intidn.SP_SPNT_SNOW_INT_ApprovalsREST();
authScript = new x_sap_intidn.SP_SPNT_SNOW_INT_Auth();
accessToken = authScript.getServiceAccountAccessToken();
action = current.variables.u_access_action.toString() == 'Add' ? 'GRANT_ACCESS' : 'REVOKE_ACCESS';
pendingApprovals = approvalsService.getPendingApprovalsForRequestedObject(accessToken, current.variables.u_identity_external_id.toString(), current.variables.u_access_id.toString(), action);
allApproversMissing = pendingApprovals.length > 0 ? true : false;
workflow.scratchpad.autorRejectIdnId = '';
grUser = new GlideRecord('sys_user');
//Validate each individual pending approver record
for (var i = 0; i < pendingApprovals.length; i++) {
result = approvalsService.getOwnerIdentity(pendingApprovals[i].owner.id.toString());
grUser.initialize();
grUser.addQuery(gs.getProperty('x_sap_intidn.x_sp_spnt_snow_int.servicenow_account_attribute'), approvalsService._lookupV2object(result, gs.getProperty('x_sap_intidn.x_sp_spnt_snow_int.spnt_identity_attribute')));
grUser.addActiveQuery();
grUser.query();
if (grUser.hasNext()) {
allApproversMissing = false;
workflow.scratchpad.autorRejectIdnId = '';
workflow.scratchpad.pendingApprovals.push(pendingApprovals[i]);
} else {
workflow.scratchpad.autorRejectIdnId = pendingApprovals[i].id.toString();
}
}
if (allApproversMissing) {
workflow.scratchpad.autoRejectIdn = 'true';
workflow.scratchpad.pendingApprovals = pendingApprovals;
current.comments = "Approver is skipped from the approval execution plan. Possible reason: Inactive Users";
}
})(current); -
Select Update.
-
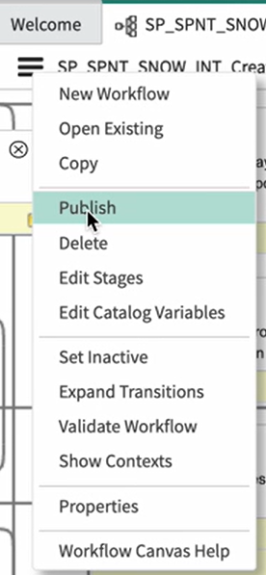
Select Publish from the menu options.
Points to remember
-
This fix will apply to all the cases where the Identity Security Cloud set up has a group.
-
This is a quick fix specific to your instance, therefore you must reapply the fix during upgrades.
Version 3.2.0 and later
-
Sign in as admin on your ServiceNow instance, go to Application Navigator and
type sys_extension_instance.LIST, then press Enter. -
In the newly open tab search for Point is
x_sap_intidn.IDNWorkFlowGroupBehaviour. Two results will be available. -
Make the row with class name ProceedForAll as
active false. -
Make the row with class name ProceedForAnyone as
active true. -
To go backto the original behavior, revert the changes.
-
Resolution:
-
Open ServiceNow as Admin and enter Widgets into the search field.
-
Select Widgets under Service Portal.
-
Open the Manage Sailpoint Access widget.
-
Change the Application scope to SailPoint IdentityNow for Service Catalog.
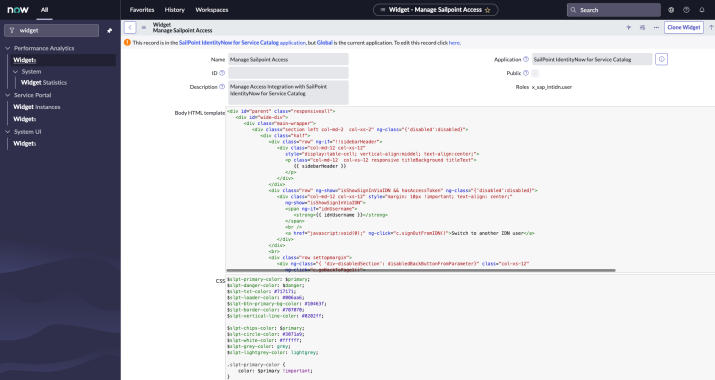
-
Add the following lines to the end of the CSS:
.ui-select-focusser.ui-select-offscreen{
display: none;
}
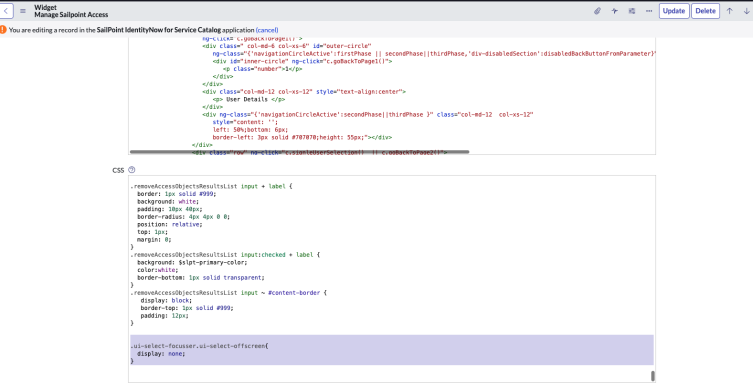
Resolution:
-
Open ServiceNow as Admin and enter Widgets into the search field.
-
Select Widgets under Service Portal.
-
Open the Manage Sailpoint Access widget.
-
Change the Application scope to SailPoint IdentityNow for Service Catalog.
-
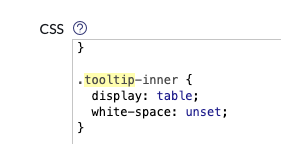
In CSS, search for .tooltip-inner and add the following line to the CSS class:
white-space: unset;
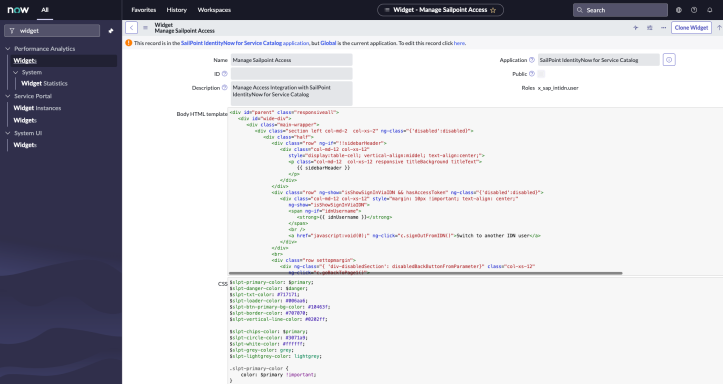
Resolution:
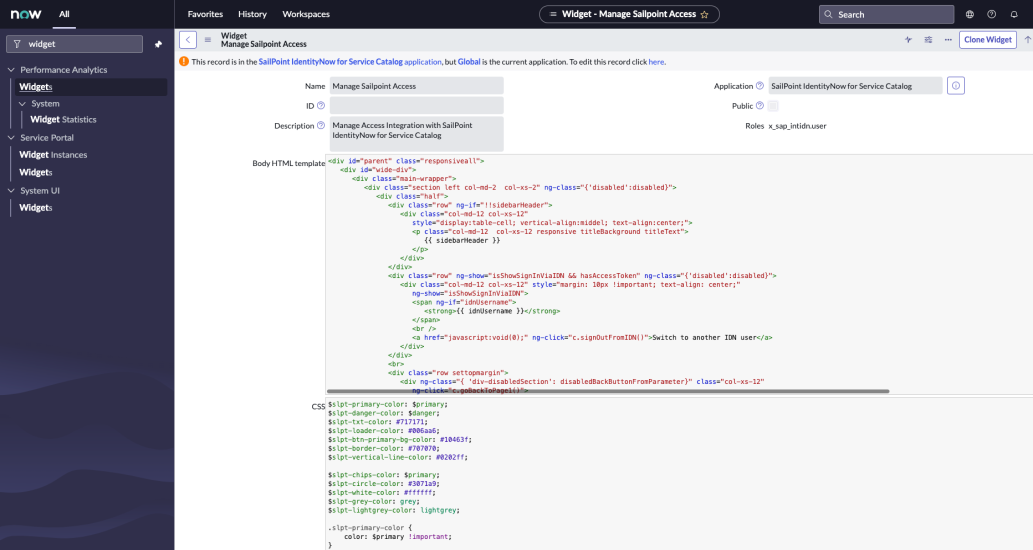
-
Open ServiceNow as Admin and enter Widgets into the search field.
-
Select Widgets under Service Portal.
-
Open the Manage Sailpoint Access widget.
-
Change the Application scope to SailPoint IdentityNow for Service Catalog.
-
In Body HTML template, search for modalTemplateAccessProfileDetailsPage2.html
-
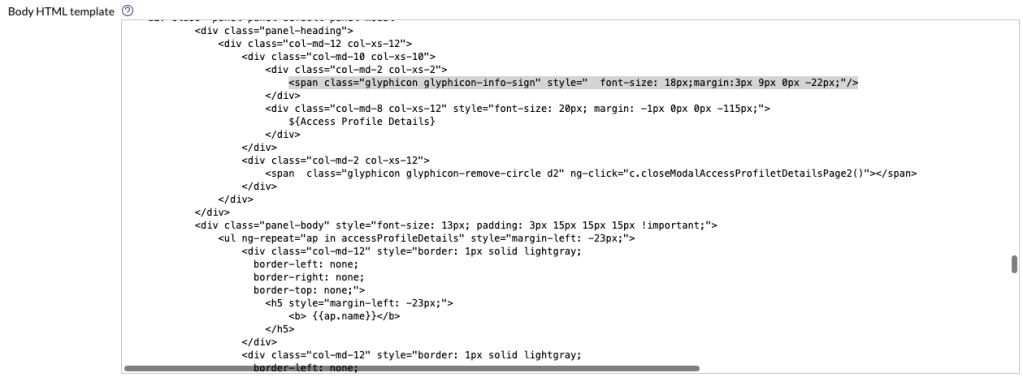
Change the <i> tag to a span tag in the following two places:
-
<i class="glyphicon glyphicon-info-sign" style=" font-size: 18px;margin:3px 9px 0px -22px;"/>
<span class="glyphicon glyphicon-info-sign" style=" font-size: 18px;margin:3px 9px 0px -22px;"/>
-
<i class="glyphicon glyphicon-remove-circle d2" ng-click="c.closeModalAccessProfiletDetailsPage2()"></span>
<span class="glyphicon glyphicon-remove-circle d2" ng-click="c.closeModalAccessProfiletDetailsPage2()"></span>
When trying to select a user in ServiceNow Catalog, the following error is displayed: Selected user doesn't exist in IdentityNow system
Resolution: Ensure that all of the links are available in the app, and that none of them are missing. Refer to Identity Security Cloud Links to ensure all links are present and correct for your installed application version.
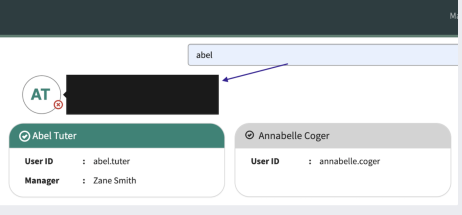
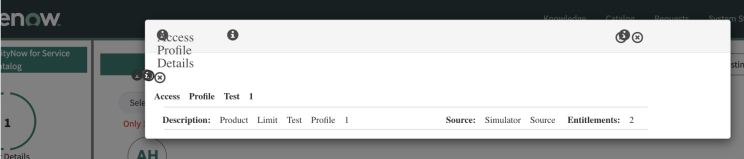
Issue: The tooltip shown while hovering over the selected user has the manager header spanning across two lines. This occurs due to the different CSS applied by ServiceNow in the Service Portal and Employee Service Center.
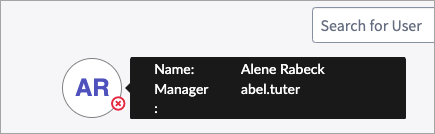
Resolution: Use the following steps to update the CSS in the widget.
-
Sign in as admin to the ServiceNow instance, and go Widgets under the Service Portal application.
-
Search for the Widget named
Manage SailPoint Accessand open the record.
-
In the CSS section of the widget, search for
.item-added-tooltip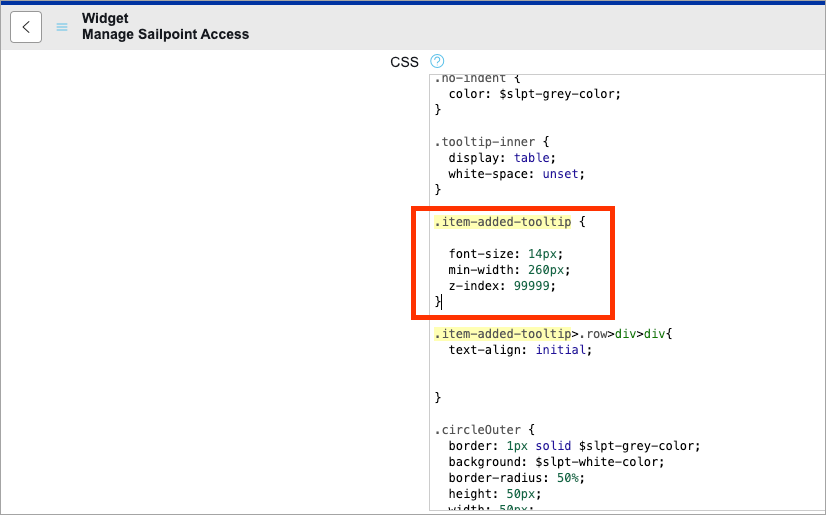
-
Replace the block of 5 lines with the following:
Copy.item-added-tooltip {
font-size: 14px;
min-width: 275px;
z-index: 99999;
} -
Select Update.
Error: Access profile user requested has already been in an access with state as NOT_ALL_ITEMS_PROVISIONED.Account Activity Id:xxx
Resolution: Incorporate the following changes:
-
On the ServiceNow tenant, go to System Definition > Scripts Include > SP_SPNT_SNOW_INT_AccessValidationREST script.
-
Take a back up of the script.
-
On line number 79 locate one if loop as below -
if (
accessRequestStatus[l].state != "REQUEST_COMPLETED" &&
accessRequestStatus[l].state != "REJECTED" &&
accessRequestStatus[l].state != "CANCELLED" &&
accessRequestStatus[l].state != "TERMINATED" &&
accessRequestStatus[l].state != "ERROR" )
-
Add two more conditions here for NOT_ALL_ITEMS_PROVISIONED and PROVISIONING_FAILED state as shown below:
if (
accessRequestStatus[l].state != "REQUEST_COMPLETED" &&
accessRequestStatus[l].state != "REJECTED" &&
accessRequestStatus[l].state != "CANCELLED" &&
accessRequestStatus[l].state != "TERMINATED" &&
accessRequestStatus[l].state != "ERROR" &&
accessRequestStatus[l].state != "NOT_ALL_ITEMS_PROVISIONED") &&
accessRequestStatus[l].state != "PROVISIONING_FAILED")
Note
Be aware that modifying the script will require manual updates for this change after each upgrade.
-
Change the ServiceNow scope to SailPoint IdentityNow for Service Catalog.
-
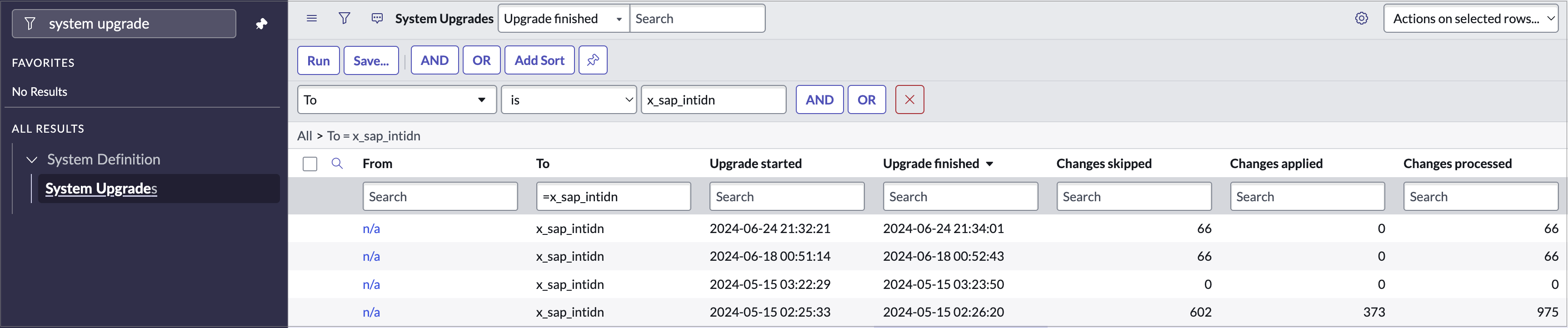
Go to System Diagnostics > Upgrades History and apply the filter with
to_version=x_sap_intidn -
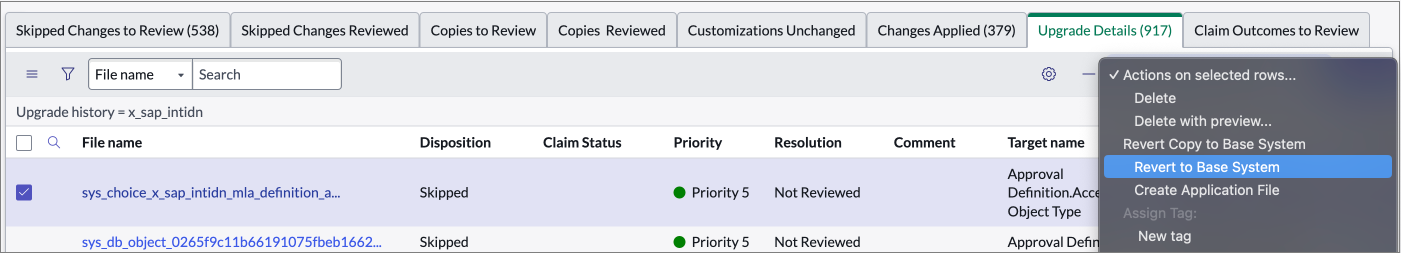
Open the skipped records to review them. Select single or multiple records and then Revert to Base System to restore them to their original, out-of-the-box (OOB) state.
Additional FAQs and Troubleshooting