Aggregation and Filter Settings
Aggregation Settings
This section contains the configuration parameters for aggregation and filter settings.
For more information about aggregation, refer to Loading Account Data.
For more information on the key factors to consider when choosing between Full Aggregation and Delta Aggregation, refer to FAQs.
-
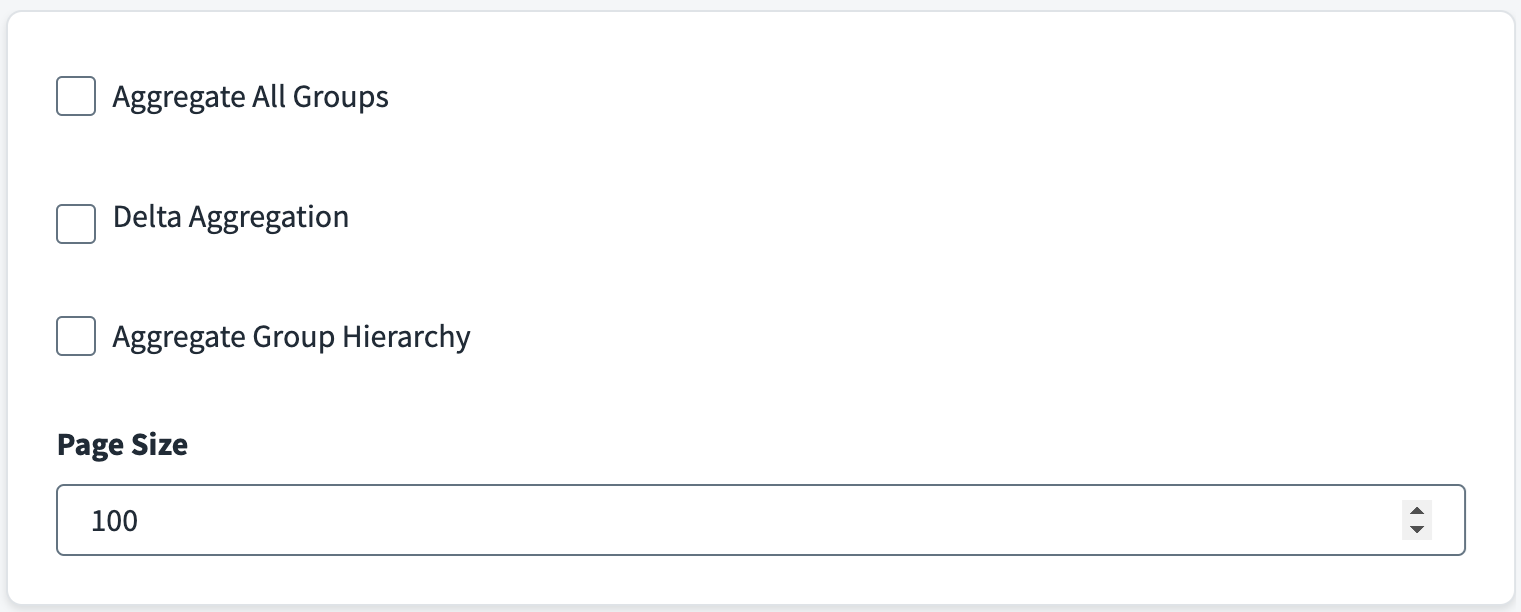
Select the Aggregate All Groups checkbox to aggregate Security, Microsoft 365, Distribution List, and Mail Enabled Security Groups. If this option is not selected, only Security Groups are aggregated.
-
Select the Delta Aggregation checkbox to aggregate delta changes for accounts and groups.
-
Select the Aggregate Group Hierarchy checkbox to read the parent and child group hierarchical information for Microsoft Entra groups.
-
Enter the value of Page Size for the number of objects to be fetched in a single page when iterating over large data sets. The default value is 100.
Note
The connector uses paging and processes the retrieved accounts in parallel, improving account aggregation performance. The default configuration of the connector considers various level of rate limits set by the Microsoft Entra ID managed system. However, you can adjust the connector's aggregation performance by fine tuning the specific data set within your environment using Batch Size Configuration.
You can configure Batch Size Configuration in your existing sources by adding the userAggregationBatchSize attribute to your source XML using the following REST API:
POST https://{orgName}.api.identitynow.com/v3/sources/{source ID}
In the body of the POST, use the form-data as shown below:
[
{
"op": "add",
"path": "/connectorAttributes/userAggregationBatchSize",
"value": "45"
}
]
For more information on SailPoint's REST APIs, refer to Best Practices: REST API Authentication and REST API - Update Source (Partial) in the SailPoint Developer Community.
Filter Settings
When configuring the filters, consider that the connector prioritizes account filters over group filters during aggregation. For example, the connector aggregates groups, which fall outside of the group filter, if the group is associated with an account included within the account filter.
-
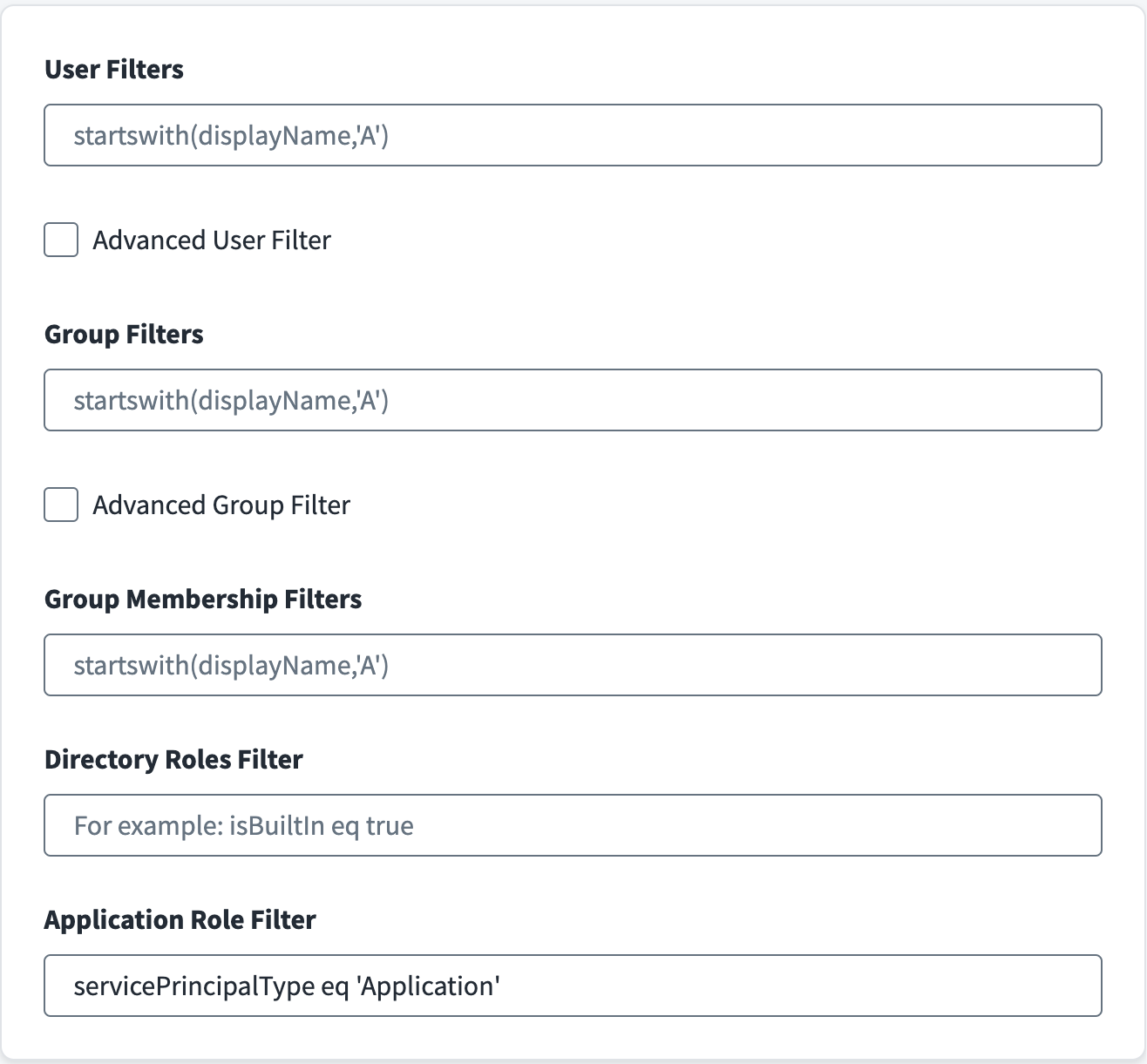
Set the User Filters to define the scope of Accounts applied during account aggregation. For example, to aggregate those Microsoft Entra ID users who are active, use
accountEnabled eq true. For more information on filters, refer to the Microsoft documentation. -
Select Advanced User Filter to include advanced filter queries such as
endsWith,NOT, andNEduring aggregation processes.To use the extension attributes from
onPremisesExtensionAttributese.g.extensionAttribute1,extensionAttribute4etc. as user filter, please use the below syntax:onPremisesExtensionAttributes/extensionAttribute1 eq '21' Screenshot
Screenshot

Note Select the “Advanced User Filter” checkbox as it is advanced query filter.
-
Set the Group Filters to define the scope of Groups applied during group aggregation. Group filters apply during entitlement aggregation. For example, to only aggregate Microsoft Entra ID groups whose display name is starting with letter A, use
startswith(displayName,'A'). For more information on filters, refer to the Microsoft documentation. -
Select Advanced Group Filter to include advanced filter queries such as endsWith, NOT, and NE during group aggregation processes.
-
Select the Group Membership Filters to define the scope of the group memberships included in account aggregation. These filters apply during the account aggregation and are only applicable to memberships belonging to
objectType = group. These are only applicable to the Security, Office 365, Mail Enabled Security, and Distributed type of group memberships. For more information on filters, refer to the Microsoft documentation.Note
You can provide filters as mentioned in the examples above, and the connector ensures the formation of an appropriate advanced filter query. This field supports advanced filter queries such asendsWith,NOT, andNE.For example,
-
To aggregate only group memberships with group display name starting with 'A', use
startswith(displayName,'A'). -
To aggregate only group memberships with groups not belonging to on-premises AD (or to only include cloud group memberships), use
onPremisesSyncEnabled ne true. -
To exclude dynamic group memberships during account aggregation , use
NOT groupTypes/any(c:c eq 'DynamicMembership')
Important
SailPoint recommends excluding membership information is not a best practice from a governance and security standpoint. You should have full visibility into users and devices, including their groups, assigned permissions, and how these configurations impact access to resources. The group membership filter should be used carefully and only when necessary, ensuring that access is managed and only the right individuals have access to sensitive information or resources. -
-
In the Directory Roles Filter field, when the entitlement schema "roles" is present in the source, enter filter statements to ensure that only the specified roles are aggregated during entitlement aggregation. For example,
isBuiltIn eq true. For more information on filtering conditions and values, refer to the Microsoft documentation. -
Select Save.
Note
-
If the filter (either Group Filter or User Filter) uses any advanced query filter (per the Microsoft documentation), then Advanced User Filter and Advanced Group Filter should also be selected.
-
The connector supports advanced query filters like
endsWith,NOT, andNEduring aggregation. The Azure API does not support the advanced query filters while also using an expanded attribute such asmanagerin the URL. When using the advanced filters, ensure that you remove themanagerattribute from the account schema and remove theownersattribute from the group schema. -
If you're using the advanced filters you must add the
supportsAdvancedAccountFilterattribute to the source XML using the Identity Security Cloud REST API. The connector will then automatically add the required header (ConsistencyLevel:eventual) in the header and add&$count=trueFor example:
POST https://{orgName}.api.identitynow.com/cc/api/source/update/{source ID}
In the body of the POST, use the form-data as follows:
-
Key:
supportsAdvancedAccountFilter -
Value:
true
-