Aggregation Settings
This section contains the configuration parameters for aggregation and filter settings.
For more information about Aggregation, refer to Loading Account Data.
-
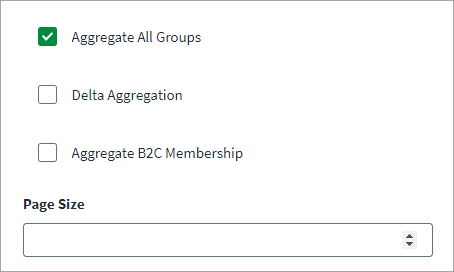
Select the Aggregate All Groups checkbox to aggregate Security, Microsoft 365, Distribution List, and Mail Enabled Security Groups. If this option is cleared, only Security Groups are aggregated.
-
Select the Delta Aggregation checkbox to aggregate delta changes for accounts and groups.
-
(Applicable for B2C tenant only) Select the Aggregate B2C Membership checkbox to fetch B2C user memberships for all users.
-
Enter the value of Page Size for the number of objects to be fetched in a single page when iterating over large data sets.
When configuring the filters, consider that the connector prioritizes account filters over group filters during aggregation. For example, the connector aggregates groups, which fall outside of the group filter, if the group is associated with an account included within the account filter.
Note
-
If the filter (either Group Filter or User Filter) uses any advanced query filter (per the Microsoft documentation), then Advanced User Filter and Advanced Group Filter should also be selected.
-
The connector supports advanced query filters like
endsWith,NOT, andNEduring aggregation. The Azure API does not support the advanced query filters while also using an expanded attribute such asmanagerin the URL. When using the advanced filters, ensure that you remove themanagerattribute from the account schema and remove theownersattribute from the group schema. -
If you're using the advanced filters you must add the
supportsAdvancedAccountFilterattribute to the source XML using the IdentityNow REST API. The connector will then automatically add the required header (ConsistencyLevel:eventual) in the header and add&$count=trueFor example:
POST https://{orgName}.api.identitynow.com/cc/api/source/update/{source ID}
In the body of the POST, use the form-data as follows:
-
Key:
supportsAdvancedAccountFilter -
Value:
true
-
-
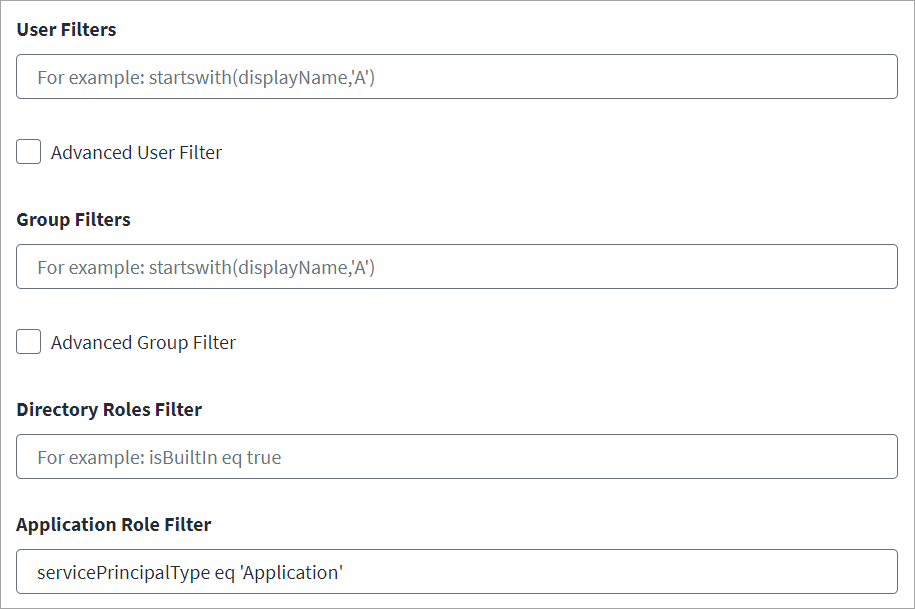
Set the User Filters to define the scope of Accounts applied during account aggregation. For example, to aggregate those Azure AD users who are active, use
accountEnabled eq true. For more information on filters, refer to the Microsoft documentation. -
Select Advanced User Filter to include advanced filter queries such as endsWith, NOT, and NE during aggregation processes.
-
Set the Group Filters to define the scope of Groups applied during group aggregation. Group filters apply during entitlement aggregation. For example, to only aggregate Azure AD groups whose display name is starting with letter A, use
startswith(displayName,'A'). For more information on filters, refer to the Microsoft documentation. -
Select Advanced Group Filter to include advanced filter queries such as endsWith, NOT, and NE during group aggregation processes.
-
In the Directory Roles Filter field, when the entitlement schema "roles" is present in the source, enter filter statements to ensure that only the specified roles are aggregated during entitlement aggregation. For example,
isBuiltIn eq true. For more information on filtering conditions and values, refer to the Microsoft documentation. -
In the Application Role Filter field, enter any filter statements to apply during entitlement aggregation. An application role is an entitlement object that captures the details related to the AppRoles defined within the scope of enterprise applications. For example:
-
For a filter to match the Enterprise Application default view on the Azure portal use the following:
tags/Any(x: x eq 'WindowsAzureActiveDirectoryIntegratedApp')
-
For a filter to exclude Microsoft's built-in service principals use the following:
appOwnerOrganizationId ne f8cdef31-a31e-4b4a-93e4-5f571e91255a&$top=100
-
-
Select Save.