Connector Architecture
In Identity Security Cloud, a source is a configured instance which communicates with an associated connector to read or write user account or entitlement objects. Connectors are technical component interfaces which communicate with target systems via native APIs to read or write user account or entitlement objects. Essentially, sources communicate with connectors.
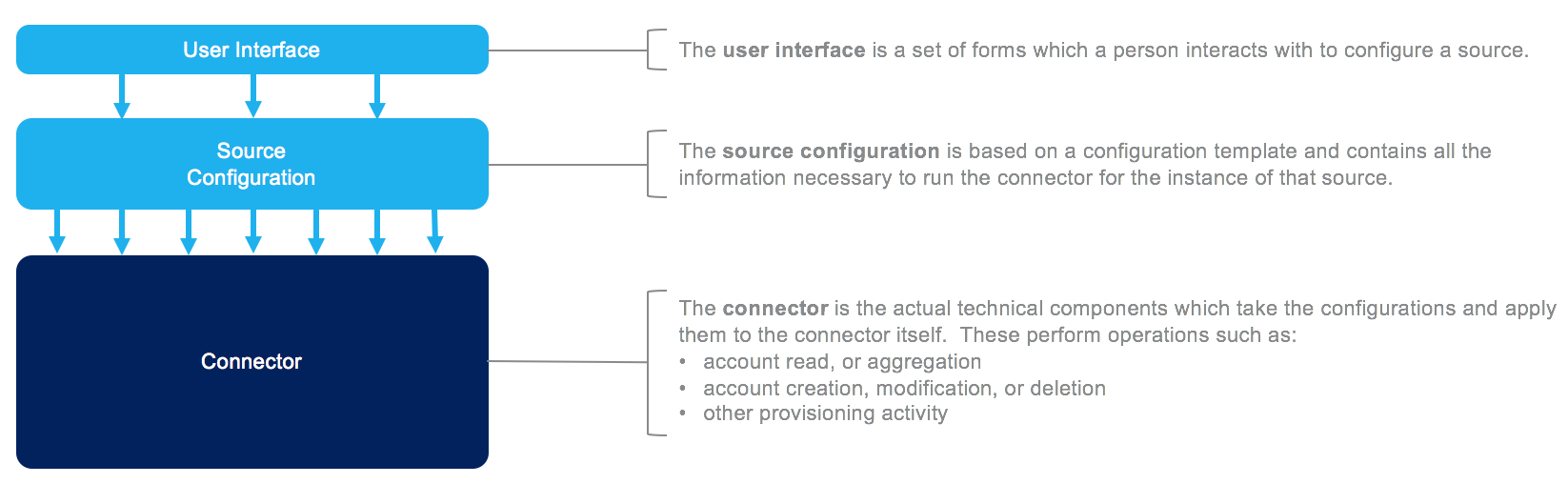
From a connector anatomical perspective, connectors are made up of three components:
-
The user interfacedisplays a set of forms which an administrator completes to configure a source.
-
The source configuration is based on a configuration template. It contains all the information necessary to run the connector for the instance of that source.
-
The connector is the technical component(s) which take the configurations and apply them to the connector itself. The connector performs operations such as:
-
Account read or aggregation
-
Account creation, modification, or deletion
-
Provisioning activities
-
So in Identity Security Cloud's environment, where can you find these artifacts? It is important to understand the architecture of how the various components interact with one another.
In Identity Security Cloud, there are components which are stored in the cloud itself. However there is an on-premise cloud connector gateway which is deployed as part of the SailPoint-managed Virtual Appliance, or VA. The connectors run from the VA and communicate with the target system(s) which can be on your internal network, or in the cloud.
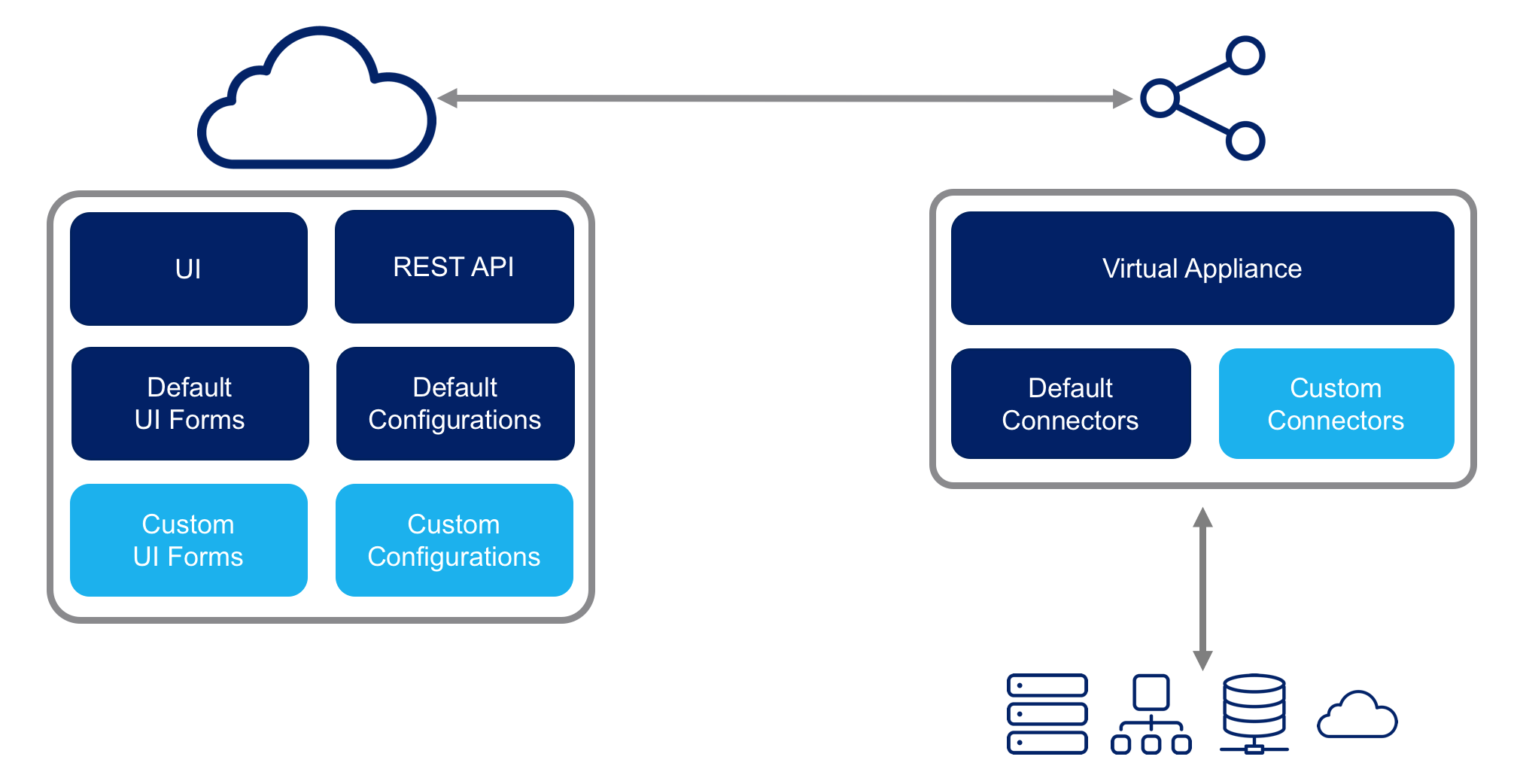
Based on the diagram, you can determine which components are deployed where, and how they should be configured.
User Interface Forms
-
XML configuration
-
Deployed in the cloud
Source Configuration Template
-
XML configuration
-
Deployed in the cloud
Custom Connector
-
Compiled Java JAR package
-
Deployed in the Identity Security Cloud Virtual Appliance
These will be used as a basis for the components which will be built in this guide.