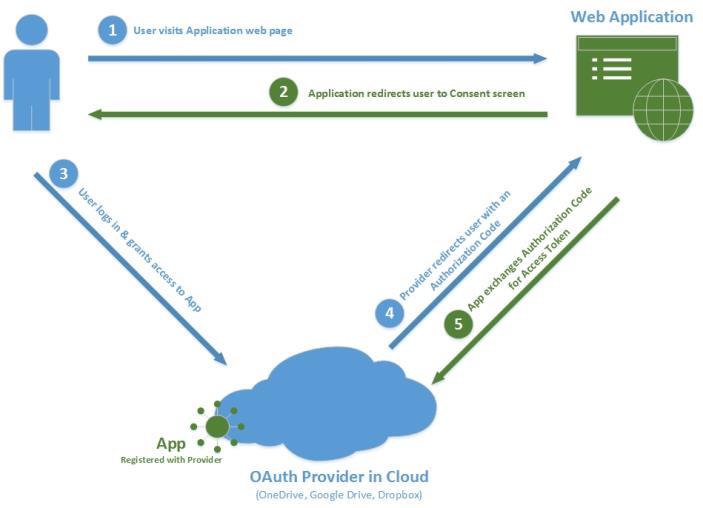
The OAuth2 Authentication Flow
Preliminary Setup
-
An app is registered in the provider's app management console. See description per application in the relevant connector installation guide.
-
App registration generates a set of identifiers: ClientId and ClientSecret. These identify the app uniquely and are used for issuing token requests.
App registration includes definition of a redirect URI that is used for user redirection upon completion of the authentication process.
-
Upon successful authentication and consent, the provider will redirect the user; the redirection URI will be appended with a user authorization code in the URL query string.
Authentication Flow
-
An end user browses to a special App Authorization URL – this is typically a credentials' input form at the provider's website
-
The end user logs in to the provider with one of the following outcomes:
-
Login Failure – The end user is redirected to the app's redirect URI with an error message in the query string.
-
Login Success – The end user is presented with a consent form that lists the permissions that the app is requesting. There are two possible outcomes:
-
Consent Declined – The end user is redirected to the app's redirect URI with an error message in the query string.
-
Consent Given – The end user is redirected to the app's redirect URI with a user authorization code in the query string.
-
-
-
A web page, or some other code, issues a token request using the user authorization code. This code is active for roughly 30 seconds.
-
The provider responds with a token set.
-
The access token can be used to issue requests to OAuth2-enabled services exposed by the provider.