Verification Algorithms screen
Description
The Verification Algorithms table shows the custom verification algorithms uploaded by the users, or as part of a policy upload from another File Access Manager system.
This table does not contain the standard out of the box verification algorithms.
Access
File Access Manager website:
Compliance > Data Classification > Verification Algorithms
Permission
By default, this page is accessible only to Administrators.
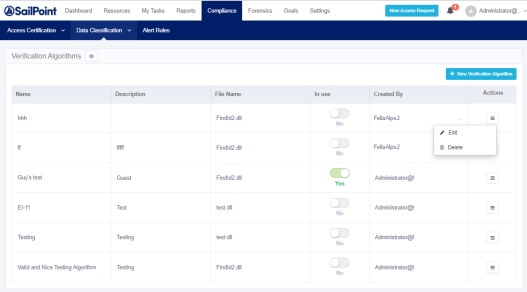
Table fields
Name
Verification algorithm name. This name will also appear in the dropdown list of verifications, along with the existing, out of the box verification algorithms.
Description
Added when the verification algorithm is uploaded.
File name
The verification algorithm dll file created by the user and uploaded to File Access Manager.
In use
This flag indicates whether this algorithm is part of a policy object, that is used in an active policy.
Created by
The user uploading the algorithm. Verification algorithms that are uploaded to the system using the policy upload tool, will be listed in the verification algorithms list as Created By “Conversion.”
See Transferring Data Classification Policies Between Systems for further details on imported policies.
This screen can be used to:
-
View custom built verification algorithms.
-
See whether an algorithm is in use
-
Edit an algorithm details: Update the name, upload a new file or update the description.
-
Upload new verification algorithms (See below how to create an algorithm dll),
-
Delete verification algorithms.
Uploading a New Verification Algorithm
A new verification algorithm must follow the guidelines below:
-
Extension: .dll
-
File size: Up to 5 MB
-
The verifier name must be unique in the list of verification algorithms.
-
Open the Verification Algorithms panel.
-
Click + New Verification Algorithm.
-
Select File.
-
Select a .dll file from your computer.
-
Enter the name and description of the verification algorithm (see description above).
Name
Verification algorithm name. This name will appear in the dropdown list of verifications, along with the existing, out of the box verification algorithms
Description
Free text description of the verification algorithm.
-
Click Save or Cancel to continue.
Deleting a Custom Verification Algorithm
-
Open the Verification Algorithms panel.
-
Click the menu icon on the row of the verification algorithm you want to delete, to open the action menu.
-
Click Delete.
Note: If the algorithm is currently part of a policy object that is used in an active policy, a popup message will warn the user before deleting.