Configuration in ServiceNow for Client Credentials Grant Type
The SailPoint Identity Governance connector for ServiceNow supports Okta OpenID Connect (OIDC) using the Client Credentials Grant Type.
Perform the following steps to configure the SailPoint Identity Governance connector for the ServiceNow application for Okta OIDC using the Client Credential Grant Type:
-
Go to System OAuth > Application Registry > Okta OIDC Configuration.
-
Enter the Client ID and Client Secret of the application registered in the Okta OAuth OIDC server.
-
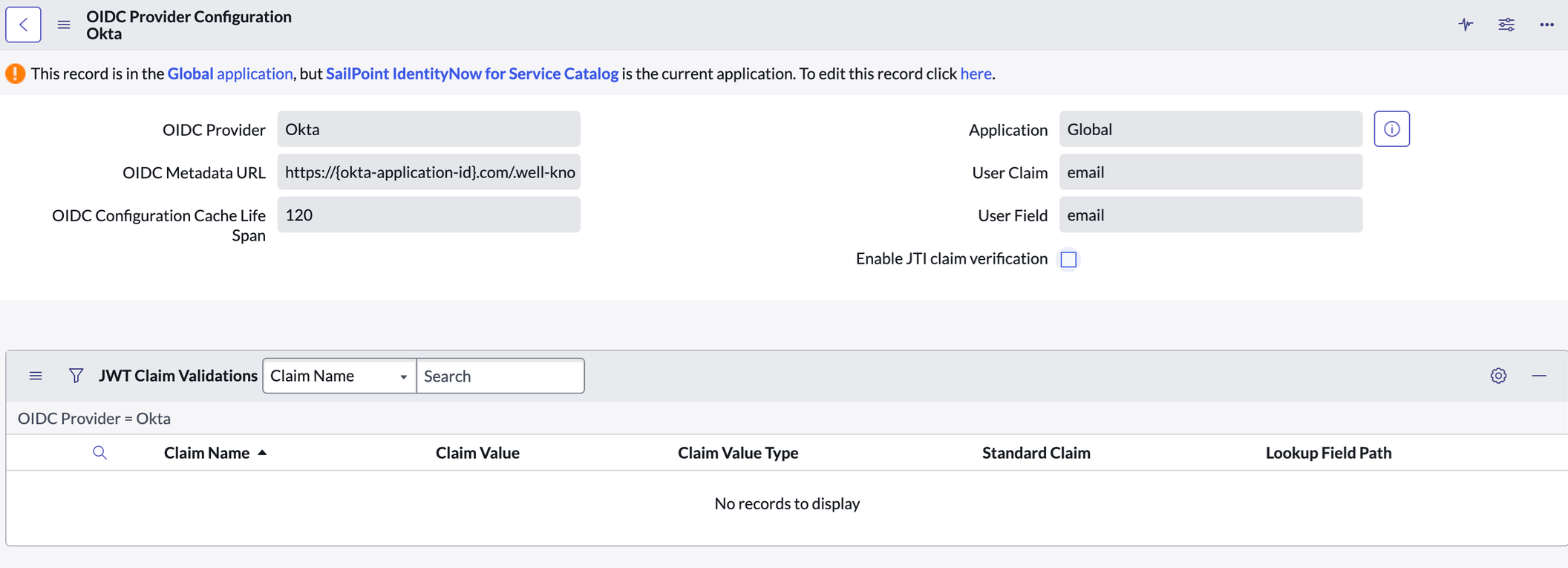
Go to the OAuth OIDC Provider Configuration preview.
Note
The connector validates the received access token in ServiceNow with the help of OIDC Provider configuration.Provide the following details in the OAuth OIDC Provider Configuration for access token validation:
-
Enter the OIDC Metadata URL, where it returns the OpenID Connect metadata about your authorization server. This information is used to configure connector interaction with Okta. For example,
https://{yourOktaDomain.com}/oauth2/{authorizationServerId}/.well-known/openid-configuration
-
Update the User Claim and User Field correlation to validate the resource endpoint permission.
Note
The matched user should have thex_sapo_iiq_connect.adminrole to execute governance application APIs. -
Deselect the Enable JTI claim verification checkbox.
-
Update claims in JWT Claims Validations to validate the received access token.
-
You can use the Audience value of the Okta Authorization Server for the Client ID in the Okta application server.