OAuth 2.0
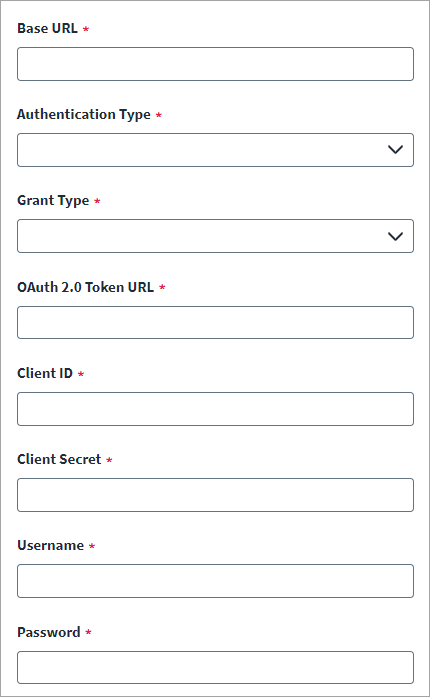
OAuth 2.0 authentication uses an access token for connection. An access token is generated based on the selected grant type, which then allows the generated token to be used.
-
From the Grant Type dropdown, select one of the following:
Password
-
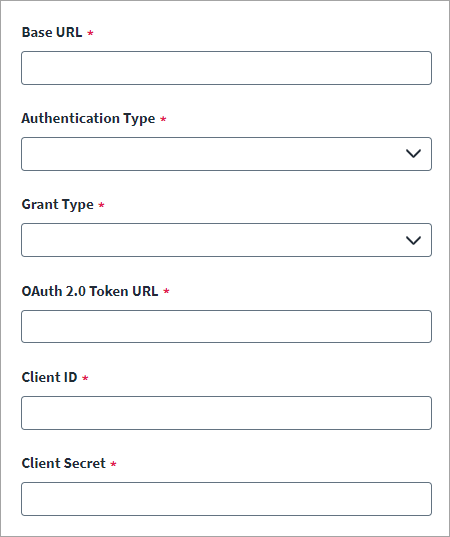
In the OAuth 2.0 Token URL field, enter the OAuth 2.0 Token URL for generating the access token.
-
Enter the Client ID and accompanying Client Secret created in the SCIM 2.0 source.
-
Enter the Username and Password the connector needs to authenticate with the SCIM 2.0 source.
-
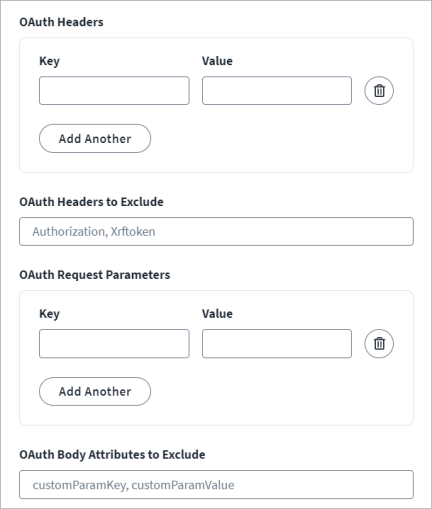
For OAuth Headers add the Key and Value pairs to set up the custom headers for the access token. The SCIM 2.0 SaaS source adheres to the generalized specifications of the OAuth 2.0 grant types. For some managed target systems, however, custom headers may be required to be part of the access token generation request. You can add the custom headers as an attribute. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Headers to Exclude. By default, an Authorization BASIC header with Base64-encoded client ID and client secret are a part of the access token generation request. Some managed target systems do not support this header. If there is no Authorization BASIC header required for such managed target systems, it can be excluded from the request.
-
Set the custom OAuth Request Parameters for the access token. For some managed target systems, custom request parameters may be required to be part of the access token generation request. You can add the custom request parameter as an attribute. For example, some managed target systems require explicit scope attributes in request parameters. In that case, add the scope as the key and value in OAuth Request Parameters. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Body Attributes to Exclude. To remove any of the standard request parameters that are not supported by managed systems access token generation requests, you must configure the request parameters to exclude them from the access token request.
-
Select Save.
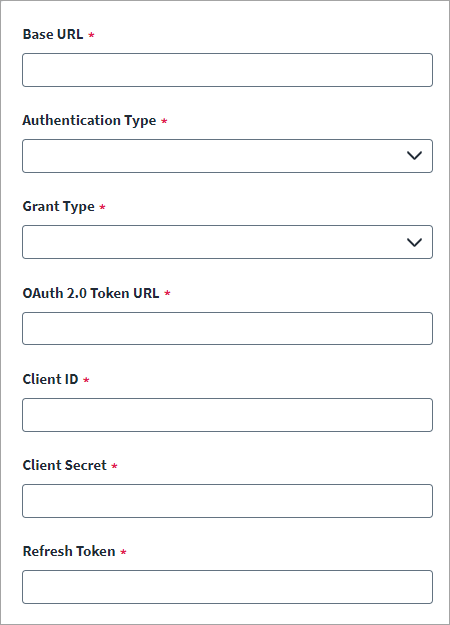
Refresh Token
-
Enter the OAuth 2.0 Token URL for generating the access token.
-
Enter the Client ID and accompanying Client Secret created in the SCIM 2.0 source.
-
Enter the Refresh Token used to generate an access token.
-
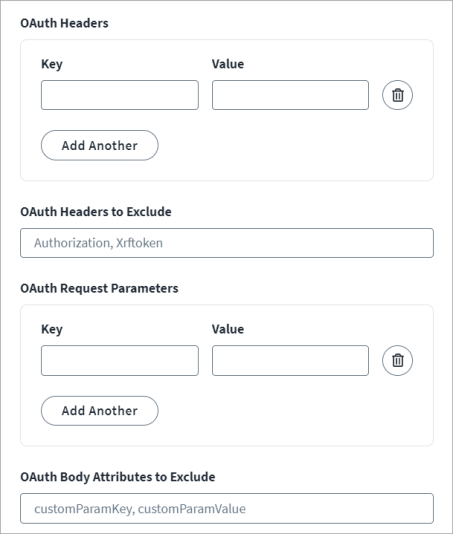
For OAuth Headers add the Key and Value pairs to set up the custom headers as part of the access token. The SCIM 2.0 SaaS source adheres to the generalized specifications of the OAuth 2.0 grant types. For some managed target systems, however, custom headers may be required to be part of the access token generation request. You can add the custom headers as an attribute. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Headers to Exclude. By default, an Authorization BASIC header with Base64-encoded client ID and client secret are a part of the access token generation request. Some managed target systems do not support this header. If there is no Authorization BASIC header required for such managed target systems, it can be excluded from the request.
-
Set the custom OAuth Request Parameters for the access token. For some managed target systems, custom request parameters may be required to be part of the access token generation request. You can add the custom request parameter as an attribute. For example, some managed target systems require explicit scope attributes in request parameters. In that case, add the scope as the key and value in OAuth Request Parameters. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Body Attributes to Exclude. To remove any of the standard request parameters that are not supported by managed systems access token generation requests, you must configure the request parameters to exclude them from the access token request.
-
Select Save.
Client Credentials
-
Enter the OAuth 2.0 Token URL for generating the access token.
-
Enter the Client ID and accompanying Client Secret created in the SCIM 2.0 source.
-
For OAuth Headers add the Key and Value pairs to set up the custom headers as part of the access token. The SCIM 2.0 SaaS source adheres to the generalized specifications of the OAuth 2.0 grant types. For some managed target systems, however, custom headers may be required to be part of the access token generation request. You can add the custom headers as an attribute. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Headers to Exclude. By default, an Authorization BASIC header with Base64-encoded client ID and client secret are a part of the access token generation request. Some managed target systems do not support this header. If there is no Authorization BASIC header required for such managed target systems, it can be excluded from the request.
-
Set the custom OAuth Request Parameters for the access token. For some managed target systems, custom request parameters may be required to be part of the access token generation request. You can add the custom request parameter as an attribute. For example, some managed target systems require explicit scope attributes in request parameters. In that case, add the scope as the key and value in OAuth Request Parameters. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Body Attributes to Exclude. To remove any of the standard request parameters that are not supported by managed systems access token generation requests, you must configure the request parameters to exclude them from the access token request.
-
Select Save.
JWT Grant
-
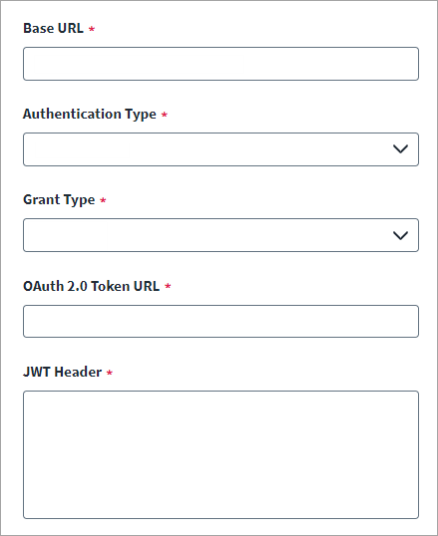
Enter the OAuth 2.0 Token URL for generating the access token.
-
Enter the JWT Header. You can add additional headers in JSON format if required. The header consists of the type of the token (JWT) and the signing algorithm being used.
For example, you can use:
{ "typ" : "JWT", "alg" : "RS256" }
-
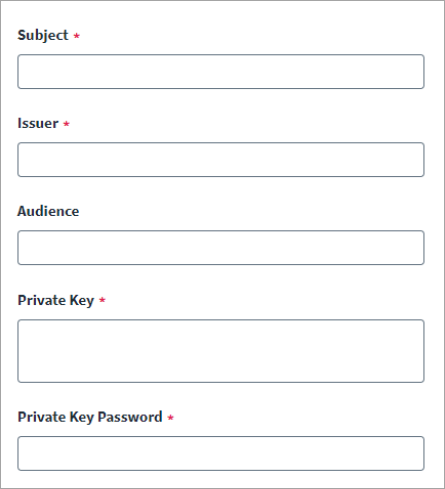
Enter the Subject.
-
Enter the Issuer.
-
Enter the Audience for authorization. This is the recipient for which the JWT is intended.
-
Enter the Private Keyand the Private Key Password.
-
For OAuth Headers add the Key and Value pairs to set up the custom headers as part of the access token. The SCIM 2.0 SaaS source adheres to the generalized specifications of the OAuth 2.0 grant types. For some managed target systems, however, custom headers may be required to be part of the access token generation request. You can add the custom headers as an attribute. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Headers to Exclude. By default, an Authorization BASIC header with Base64-encoded client ID and client secret are a part of the access token generation request. Some managed target systems do not support this header. If there is no Authorization BASIC header required for such managed target systems, it can be excluded from the request.
-
Set the custom OAuth Request Parameters for the access token. For some managed target systems, custom request parameters may be required to be part of the access token generation request. You can add the custom request parameter as an attribute. For example, some managed target systems require explicit scope attributes in request parameters. In that case, add the scope as the key and value in OAuth Request Parameters. Use the Add Another and Trash Bin buttons to add or remove fields.
-
Enter the OAuth Body Attributes to Exclude. To remove any of the standard request parameters that are not supported by managed systems access token generation requests, you must configure the request parameters to exclude them from the access token request.
-
Select Save.