Configuring AWS Automatically
SailPoint provides CloudFormation templates to automate the creation of IAM roles and policies, a CloudTrail trail, and an S3 Bucket. Depending on your configuration preference and existing infrastructure, different templates are available.
Collecting Data from All AWS Accounts
SailPoint collects resources across all AWS Accounts in an organization in two steps: it first lists all AWS Accounts using the management account role with organization permissions, then assumes a role in each member account with the same role name and external ID.
SailPoint offers CloudFormation templates to create identical roles with minimum permissions in each member account, and creates the primary role in the management account with the minimum organization permissions for listing AWS accounts.
You will first enable inventory collection in all accounts. You can then choose to include activity data in your SailPoint tenant.
Collecting Resources from All AWS Accounts
The following process creates a role and policies with minimum privileges in the management account.
Create an in-line policy on the role for reading resource data from your AWS cloud.
To enable inventory collection in all accounts:
-
Follow the AWS directions to create a stack in the root management account where logs are captured.
-
Upload the appropriate cloud formation template:
 AWS accounts only
Copy
AWS accounts only
Copy{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources": {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName": {
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::874540850173:role/ciem_universal"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [
{
"PolicyName": "SailPointAWSPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:UpdateAccessKey",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DeleteLoginProfile",
"iam:AttachUserPolicy"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
} AWS accounts with Activity Insights
Copy
AWS accounts with Activity Insights
Copy{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources": {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName": {
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::874540850173:role/ciem_universal"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [
{
"PolicyName": "SailPointAWSPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:UpdateAccessKey",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DeleteLoginProfile",
"iam:AttachUserPolicy",
"cloudtrail:Get*",
"cloudtrail:Describe*",
"cloudtrail:List*",
"cloudtrail:LookupEvents"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
} AWS accounts with Agent Discovery
Copy
AWS accounts with Agent Discovery
Copy{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources": {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName": {
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::874540850173:role/ciem_universal"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [
{
"PolicyName": "SailPointAWSPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "*",
"Action": [
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:UpdateAccessKey",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DeleteLoginProfile",
"iam:AttachUserPolicy",
"bedrock:ListAgents",
"bedrock:GetAgent",
"bedrock:ListAgentActionGroups",
"bedrock:GetAgentActionGroup",
"bedrock:ListAgentKnowledgeBases",
"bedrock:GetAgentKnowledgeBase",
"bedrock:ListKnowledgeBases",
"bedrock:GetKnowledgeBase",
"bedrock:ListAgentAliases",
"bedrock:GetAgentAlias",
"bedrock:ListAgentVersions",
"bedrock:GetAgentVersion",
"bedrock:ListDataSources",
"bedrock:GetDataSource",
"bedrock:ListAgentCollaborators",
"bedrock:GetAgentCollaborator",
"kms:Decrypt",
"kms:GenerateDataKey",
"bedrock-agentcore:ListAgentRuntimes",
"bedrock-agentcore:GetAgentRuntime",
"bedrock-agentcore:ListAgentRuntimeEndpoints",
"bedrock-agentcore:GetAgentRuntimeEndpoint",
"bedrock-agentcore:ListAgentRuntimeVersions",
"bedrock-agentcore:ListWorkloadIdentities",
"bedrock-agentcore:GetWorkloadIdentity",
"bedrock-agentcore:ListOauth2CredentialProviders",
"bedrock-agentcore:GetApiKeyCredentialProvider",
"bedrock-agentcore:ListApiKeyCredentialProviders",
"bedrock-agentcore:GetOauth2CredentialProvider"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
} AWS accounts with CEIM and Activity Insights
AWS accounts with CEIM and Activity Insights
 AWS Commercial
Copy
AWS Commercial
Copy{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources": {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName": {
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::874540850173:role/ciem_universal"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [
{
"PolicyName": "SailPointAWSPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "*",
"Action": [
"organizations:ListPoliciesForTarget",
"organizations:ListAccountsForParent",
"organizations:ListRoots",
"organizations:ListAccounts",
"organizations:ListTargetsForPolicy",
"organizations:DescribeOrganization",
"organizations:DescribeOrganizationalUnit",
"organizations:DescribeAccount",
"organizations:ListParents",
"organizations:ListOrganizationalUnitsForParent",
"organizations:DescribePolicy",
"organizations:ListPolicies",
"organizations:ListTagsForResource",
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:CreateGroup",
"iam:DeleteAccessKey",
"iam:AttachUserPolicy",
"iam:DeleteUserPolicy",
"iam:UpdateAccessKey",
"iam:AttachRolePolicy",
"iam:DeleteUser",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreatePolicy",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DetachRolePolicy",
"iam:DeleteSigningCertificate",
"iam:AttachGroupPolicy",
"iam:DeleteRolePolicy",
"iam:DetachGroupPolicy",
"iam:DetachUserPolicy",
"iam:DeleteLoginProfile",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudtrail:ListTags",
"cloudtrail:LookupEvents",
"cloudtrail:Get*",
"cloudtrail:Describe*",
"cloudtrail:List*",
"cloudwatch:Describe*",
"cloudwatch:ListTagsForResource",
"config:BatchGetAggregateResourceConfig",
"config:BatchGetResourceConfig",
"config:Deliver*",
"config:Describe*",
"config:Get*",
"config:List*",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeGlobalTable",
"dynamodb:DescribeTable",
"dynamodb:DescribeTimeToLive",
"dynamodb:ListBackups",
"dynamodb:ListGlobalTables",
"dynamodb:ListStreams",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:Describe*",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayMulticastDomains",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeTransitGateways",
"ec2:GetManagedPrefixListAssociations",
"ec2:GetManagedPrefixListEntries",
"ec2:GetTransitGatewayAttachmentPropagations",
"ec2:GetTransitGatewayMulticastDomainAssociations",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:GetTransitGatewayRouteTableAssociations",
"ec2:GetTransitGatewayRouteTablePropagations",
"elasticloadbalancing:Describe*",
"es:Describe*",
"es:ListDomainNames",
"es:ListElasticsearchInstanceTypeDetails",
"es:ListElasticsearchVersions",
"es:ListTags",
"events:Describe*",
"events:List*",
"events:TestEventPattern",
"kms:Describe*",
"kms:Get*",
"kms:List*",
"lambda:GetAccountSettings",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetLayerVersionPolicy",
"lambda:GetPolicy",
"lambda:List*",
"logs:Describe*",
"logs:ListTagsLogGroup",
"rds:Describe*",
"rds:DownloadDBLogFilePortion",
"rds:ListTagsForResource",
"s3:GetAccelerateConfiguration",
"s3:GetAccessPoint",
"s3:GetAccessPointPolicy",
"s3:GetAccessPointPolicyStatus",
"s3:GetAccountPublicAccessBlock",
"s3:GetAnalyticsConfiguration",
"s3:GetBucket*",
"s3:GetEncryptionConfiguration",
"s3:GetInventoryConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetMetricsConfiguration",
"s3:GetObjectAcl",
"s3:GetObjectVersionAcl",
"s3:GetReplicationConfiguration",
"s3:ListAccessPoints",
"s3:ListAllMyBuckets",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTagsForResource",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListDeadLetterSourceQueues",
"sqs:ListQueueTags",
"sqs:ListQueues",
"tag:GetResources",
"tag:GetTagKeys",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
} AWS GovCloud
Copy
AWS GovCloud
Copy{
"AWSTemplateFormatVersion" : "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources" : {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName":
{
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws-us-gov:iam::229634586956:role/ciem_universal"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [ {
"PolicyName" : "SailPointAWSPolicy",
"PolicyDocument" : {
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Resource":"*",
"Action":[
"organizations:ListPoliciesForTarget",
"organizations:ListAccountsForParent",
"organizations:ListRoots",
"organizations:ListAccounts",
"organizations:ListTargetsForPolicy",
"organizations:DescribeOrganization",
"organizations:DescribeOrganizationalUnit",
"organizations:DescribeAccount",
"organizations:ListParents",
"organizations:ListOrganizationalUnitsForParent",
"organizations:DescribePolicy",
"organizations:ListPolicies",
"organizations:ListTagsForResource",
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:CreateGroup",
"iam:DeleteAccessKey",
"iam:AttachUserPolicy",
"iam:DeleteUserPolicy",
"iam:UpdateAccessKey",
"iam:AttachRolePolicy",
"iam:DeleteUser",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreatePolicy",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DetachRolePolicy",
"iam:DeleteSigningCertificate",
"iam:AttachGroupPolicy",
"iam:DeleteRolePolicy",
"iam:DetachGroupPolicy",
"iam:DetachUserPolicy",
"iam:DeleteLoginProfile",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudtrail:ListTags",
"cloudtrail:LookupEvents",
"cloudtrail:Get*",
"cloudtrail:Describe*",
"cloudtrail:List*",
"cloudwatch:Describe*",
"cloudwatch:ListTagsForResource",
"config:BatchGetAggregateResourceConfig",
"config:BatchGetResourceConfig",
"config:Deliver*",
"config:Describe*",
"config:Get*",
"config:List*",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeGlobalTable",
"dynamodb:DescribeTable",
"dynamodb:DescribeTimeToLive",
"dynamodb:ListBackups",
"dynamodb:ListGlobalTables",
"dynamodb:ListStreams",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:Describe*",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayMulticastDomains",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeTransitGateways",
"ec2:GetManagedPrefixListAssociations",
"ec2:GetManagedPrefixListEntries",
"ec2:GetTransitGatewayAttachmentPropagations",
"ec2:GetTransitGatewayMulticastDomainAssociations",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:GetTransitGatewayRouteTableAssociations",
"ec2:GetTransitGatewayRouteTablePropagations",
"elasticloadbalancing:Describe*",
"es:Describe*",
"es:ListDomainNames",
"es:ListElasticsearchInstanceTypeDetails",
"es:ListElasticsearchVersions",
"es:ListTags",
"events:Describe*",
"events:List*",
"events:TestEventPattern",
"kms:Describe*",
"kms:Get*",
"kms:List*",
"lambda:GetAccountSettings",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetLayerVersionPolicy",
"lambda:GetPolicy",
"lambda:List*",
"logs:Describe*",
"logs:ListTagsLogGroup",
"rds:Describe*",
"rds:DownloadDBLogFilePortion",
"rds:ListTagsForResource",
"s3:GetAccelerateConfiguration",
"s3:GetAccessPoint",
"s3:GetAccessPointPolicy",
"s3:GetAccessPointPolicyStatus",
"s3:GetAccountPublicAccessBlock",
"s3:GetAnalyticsConfiguration",
"s3:GetBucket*",
"s3:GetEncryptionConfiguration",
"s3:GetInventoryConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetMetricsConfiguration",
"s3:GetObjectAcl",
"s3:GetObjectVersionAcl",
"s3:GetReplicationConfiguration",
"s3:ListAccessPoints",
"s3:ListAllMyBuckets",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTagsForResource",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListDeadLetterSourceQueues",
"sqs:ListQueueTags",
"sqs:ListQueues",
"tag:GetResources",
"tag:GetTagKeys",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
} AWS accounts with CEIM, Activity Insights, and Agent Discovery
AWS accounts with CEIM, Activity Insights, and Agent Discovery
 AWS Commercial
Copy
AWS Commercial
Copy{
"AWSTemplateFormatVersion": "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources": {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName": {
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::874540850173:role/ciem_universal"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [
{
"PolicyName": "SailPointAWSPolicy",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": "*",
"Action": [
"organizations:ListPoliciesForTarget",
"organizations:ListAccountsForParent",
"organizations:ListRoots",
"organizations:ListAccounts",
"organizations:ListTargetsForPolicy",
"organizations:DescribeOrganization",
"organizations:DescribeOrganizationalUnit",
"organizations:DescribeAccount",
"organizations:ListParents",
"organizations:ListOrganizationalUnitsForParent",
"organizations:DescribePolicy",
"organizations:ListPolicies",
"organizations:ListTagsForResource",
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:CreateGroup",
"iam:DeleteAccessKey",
"iam:AttachUserPolicy",
"iam:DeleteUserPolicy",
"iam:UpdateAccessKey",
"iam:AttachRolePolicy",
"iam:DeleteUser",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreatePolicy",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DetachRolePolicy",
"iam:DeleteSigningCertificate",
"iam:AttachGroupPolicy",
"iam:DeleteRolePolicy",
"iam:DetachGroupPolicy",
"iam:DetachUserPolicy",
"iam:DeleteLoginProfile",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudtrail:ListTags",
"cloudtrail:LookupEvents",
"cloudtrail:Get*",
"cloudtrail:Describe*",
"cloudtrail:List*",
"cloudwatch:Describe*",
"cloudwatch:ListTagsForResource",
"config:BatchGetAggregateResourceConfig",
"config:BatchGetResourceConfig",
"config:Deliver*",
"config:Describe*",
"config:Get*",
"config:List*",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeGlobalTable",
"dynamodb:DescribeTable",
"dynamodb:DescribeTimeToLive",
"dynamodb:ListBackups",
"dynamodb:ListGlobalTables",
"dynamodb:ListStreams",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:Describe*",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayMulticastDomains",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeTransitGateways",
"ec2:GetManagedPrefixListAssociations",
"ec2:GetManagedPrefixListEntries",
"ec2:GetTransitGatewayAttachmentPropagations",
"ec2:GetTransitGatewayMulticastDomainAssociations",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:GetTransitGatewayRouteTableAssociations",
"ec2:GetTransitGatewayRouteTablePropagations",
"elasticloadbalancing:Describe*",
"es:Describe*",
"es:ListDomainNames",
"es:ListElasticsearchInstanceTypeDetails",
"es:ListElasticsearchVersions",
"es:ListTags",
"events:Describe*",
"events:List*",
"events:TestEventPattern",
"kms:Describe*",
"kms:Get*",
"kms:List*",
"lambda:GetAccountSettings",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetLayerVersionPolicy",
"lambda:GetPolicy",
"lambda:List*",
"logs:Describe*",
"logs:ListTagsLogGroup",
"rds:Describe*",
"rds:DownloadDBLogFilePortion",
"rds:ListTagsForResource",
"s3:GetAccelerateConfiguration",
"s3:GetAccessPoint",
"s3:GetAccessPointPolicy",
"s3:GetAccessPointPolicyStatus",
"s3:GetAccountPublicAccessBlock",
"s3:GetAnalyticsConfiguration",
"s3:GetBucket*",
"s3:GetEncryptionConfiguration",
"s3:GetInventoryConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetMetricsConfiguration",
"s3:GetObjectAcl",
"s3:GetObjectVersionAcl",
"s3:GetReplicationConfiguration",
"s3:ListAccessPoints",
"s3:ListAllMyBuckets",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTagsForResource",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListDeadLetterSourceQueues",
"sqs:ListQueueTags",
"sqs:ListQueues",
"tag:GetResources",
"tag:GetTagKeys",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy",
"bedrock:ListAgents",
"bedrock:GetAgent",
"bedrock:ListAgentActionGroups",
"bedrock:GetAgentActionGroup",
"bedrock:ListAgentKnowledgeBases",
"bedrock:GetAgentKnowledgeBase",
"bedrock:ListKnowledgeBases",
"bedrock:GetKnowledgeBase",
"bedrock:ListAgentAliases",
"bedrock:GetAgentAlias",
"bedrock:ListAgentVersions",
"bedrock:GetAgentVersion",
"bedrock:ListDataSources",
"bedrock:GetDataSource",
"bedrock:ListAgentCollaborators",
"bedrock:GetAgentCollaborator",
"kms:Decrypt",
"kms:GenerateDataKey",
"bedrock-agentcore:ListAgentRuntimes",
"bedrock-agentcore:GetAgentRuntime",
"bedrock-agentcore:ListAgentRuntimeEndpoints",
"bedrock-agentcore:GetAgentRuntimeEndpoint",
"bedrock-agentcore:ListAgentRuntimeVersions",
"bedrock-agentcore:ListWorkloadIdentities",
"bedrock-agentcore:GetWorkloadIdentity",
"bedrock-agentcore:ListOauth2CredentialProviders",
"bedrock-agentcore:GetApiKeyCredentialProvider",
"bedrock-agentcore:ListApiKeyCredentialProviders",
"bedrock-agentcore:GetOauth2CredentialProvider"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
} AWS GovCloud
AWS GovCloud
Note
Amazon Bedrock AgentCore agents are not supported in AWS GovCloud. For more information about the support of this regional service, refer to AWS Regions in the AWS documentation.Copy{
"AWSTemplateFormatVersion" : "2010-09-09",
"Parameters": {
"RoleName": {
"Default": "SailPointAWSRole",
"Description": "Role with this name will be created.",
"Type": "String"
},
"ExternalId": {
"Description": "Unique external ID needed for assuming role.",
"Type": "String"
},
"RolePolicyName": {
"Default": "SailPointAWSPolicy",
"Description": "Policy to allow SailPoint Role to read objects under the specified Cloud Trail Bucket.",
"Type": "String"
},
"BucketName": {
"Description": "Name of existing Bucket with CloudTrail logs.",
"Type": "String"
}
},
"Resources" : {
"SailPointAWSPolicy": {
"Type": "AWS::IAM::ManagedPolicy",
"DeletionPolicy": "Retain",
"Properties": {
"Description": "Policy for created for AWS Organizations",
"Path": "/",
"Roles": [
{
"Ref": "SailPointAWSRole"
}
],
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:GetBucketLocation",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
}
},
{
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "BucketName"
}
]
]
},
"*"
]
]
}
}
]
}
}
},
"SailPointAWSRole": {
"Type": "AWS::IAM::Role",
"DeletionPolicy": "Retain",
"Properties": {
"RoleName":
{
"Ref": "RoleName"
},
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": [
"arn:aws-us-gov:iam::229634586956:role/ciem_universal"
]
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": {
"Ref": "ExternalId"
}
}
}
}
]
},
"Policies": [ {
"PolicyName" : "SailPointAWSPolicy",
"PolicyDocument" : {
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Resource":"*",
"Action":[
"organizations:ListPoliciesForTarget",
"organizations:ListAccountsForParent",
"organizations:ListRoots",
"organizations:ListAccounts",
"organizations:ListTargetsForPolicy",
"organizations:DescribeOrganization",
"organizations:DescribeOrganizationalUnit",
"organizations:DescribeAccount",
"organizations:ListParents",
"organizations:ListOrganizationalUnitsForParent",
"organizations:DescribePolicy",
"organizations:ListPolicies",
"organizations:ListTagsForResource",
"iam:GetPolicyVersion",
"iam:ListServiceSpecificCredentials",
"iam:ListMFADevices",
"iam:ListSigningCertificates",
"iam:GetGroup",
"iam:ListSSHPublicKeys",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListAccessKeys",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"iam:ListRoles",
"iam:ListUserPolicies",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListAccountAliases",
"iam:ListUsers",
"iam:ListGroups",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GetLoginProfile",
"iam:ListEntitiesForPolicy",
"iam:GetAccessKeyLastUsed",
"iam:ListUserTags",
"iam:ListRoleTags",
"iam:ListPolicyTags",
"iam:UpdateLoginProfile",
"iam:CreateGroup",
"iam:DeleteAccessKey",
"iam:AttachUserPolicy",
"iam:DeleteUserPolicy",
"iam:UpdateAccessKey",
"iam:AttachRolePolicy",
"iam:DeleteUser",
"iam:CreateUser",
"iam:CreateAccessKey",
"iam:CreatePolicy",
"iam:CreateLoginProfile",
"iam:RemoveUserFromGroup",
"iam:AddUserToGroup",
"iam:DetachRolePolicy",
"iam:DeleteSigningCertificate",
"iam:AttachGroupPolicy",
"iam:DeleteRolePolicy",
"iam:DetachGroupPolicy",
"iam:DetachUserPolicy",
"iam:DeleteLoginProfile",
"cloudtrail:DescribeTrails",
"cloudtrail:GetEventSelectors",
"cloudtrail:GetTrailStatus",
"cloudtrail:ListTags",
"cloudtrail:LookupEvents",
"cloudtrail:Get*",
"cloudtrail:Describe*",
"cloudtrail:List*",
"cloudwatch:Describe*",
"cloudwatch:ListTagsForResource",
"config:BatchGetAggregateResourceConfig",
"config:BatchGetResourceConfig",
"config:Deliver*",
"config:Describe*",
"config:Get*",
"config:List*",
"dynamodb:DescribeContinuousBackups",
"dynamodb:DescribeGlobalTable",
"dynamodb:DescribeTable",
"dynamodb:DescribeTimeToLive",
"dynamodb:ListBackups",
"dynamodb:ListGlobalTables",
"dynamodb:ListStreams",
"dynamodb:ListTables",
"dynamodb:ListTagsOfResource",
"ec2:Describe*",
"ec2:DescribeTransitGatewayAttachments",
"ec2:DescribeTransitGatewayMulticastDomains",
"ec2:DescribeTransitGatewayPeeringAttachments",
"ec2:DescribeTransitGatewayRouteTables",
"ec2:DescribeTransitGatewayVpcAttachments",
"ec2:DescribeTransitGateways",
"ec2:GetManagedPrefixListAssociations",
"ec2:GetManagedPrefixListEntries",
"ec2:GetTransitGatewayAttachmentPropagations",
"ec2:GetTransitGatewayMulticastDomainAssociations",
"ec2:GetTransitGatewayPrefixListReferences",
"ec2:GetTransitGatewayRouteTableAssociations",
"ec2:GetTransitGatewayRouteTablePropagations",
"elasticloadbalancing:Describe*",
"es:Describe*",
"es:ListDomainNames",
"es:ListElasticsearchInstanceTypeDetails",
"es:ListElasticsearchVersions",
"es:ListTags",
"events:Describe*",
"events:List*",
"events:TestEventPattern",
"kms:Describe*",
"kms:Get*",
"kms:List*",
"lambda:GetAccountSettings",
"lambda:GetFunctionConfiguration",
"lambda:GetFunctionEventInvokeConfig",
"lambda:GetLayerVersionPolicy",
"lambda:GetPolicy",
"lambda:List*",
"logs:Describe*",
"logs:ListTagsLogGroup",
"rds:Describe*",
"rds:DownloadDBLogFilePortion",
"rds:ListTagsForResource",
"s3:GetAccelerateConfiguration",
"s3:GetAccessPoint",
"s3:GetAccessPointPolicy",
"s3:GetAccessPointPolicyStatus",
"s3:GetAccountPublicAccessBlock",
"s3:GetAnalyticsConfiguration",
"s3:GetBucket*",
"s3:GetEncryptionConfiguration",
"s3:GetInventoryConfiguration",
"s3:GetLifecycleConfiguration",
"s3:GetMetricsConfiguration",
"s3:GetObjectAcl",
"s3:GetObjectVersionAcl",
"s3:GetReplicationConfiguration",
"s3:ListAccessPoints",
"s3:ListAllMyBuckets",
"sns:GetTopicAttributes",
"sns:ListSubscriptions",
"sns:ListSubscriptionsByTopic",
"sns:ListTagsForResource",
"sns:ListTopics",
"sqs:GetQueueAttributes",
"sqs:ListDeadLetterSourceQueues",
"sqs:ListQueueTags",
"sqs:ListQueues",
"tag:GetResources",
"tag:GetTagKeys",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy",
"bedrock:ListAgents",
"bedrock:GetAgent",
"bedrock:ListAgentActionGroups",
"bedrock:GetAgentActionGroup",
"bedrock:ListAgentKnowledgeBases",
"bedrock:GetAgentKnowledgeBase",
"bedrock:ListKnowledgeBases",
"bedrock:GetKnowledgeBase",
"bedrock:ListAgentAliases",
"bedrock:GetAgentAlias",
"bedrock:ListAgentVersions",
"bedrock:GetAgentVersion",
"bedrock:ListDataSources",
"bedrock:GetDataSource",
"bedrock:ListAgentCollaborators",
"bedrock:GetAgentCollaborator",
"kms:Decrypt",
"kms:GenerateDataKey"
]
}
]
}
}
],
"Path": "/"
}
}
},
"Outputs": {
"SailPointAWSRoleARN": {
"Description": "SailPoint AWS Role ARN",
"Value": {
"Fn::GetAtt": [
"SailPointAWSRole",
"Arn"
]
}
},
"SailPointAWSRoleExternalId": {
"Description": "SailPoint AWS Role External ID",
"Value": {
"Ref": "ExternalId"
}
}
}
Important
You must verify your configuration before connecting your source. The following section provides verification steps.
Verifying Your AWS Configuration
When you have finished connecting your AWS accounts, you must verify that the configuration was successful. To verify your configuration:
-
In the AWS Console IAM service, select Roles.
-
Search for the IAM role created by CloudFormation. Select the role and save its name and ARN. For example,
arn:aws:iam::xxxxxxxxxxxx:role/SailPointAWSRole -
Select the Trust Relationships tab and confirm the principal displays:
874540850173for Commercial accounts229634586956for GovCloud accounts -
Select Policies and search for the IAM role created by CloudFormation. For example,
SailPointAWSRole -
Select Permissions and verify the bucket name in the JSON.
-
Ensure the policy allows
s3:GetBucketLocationands3:ListBucketactions on the CloudTrail bucket, and thes3:GetObjectaction on the S3 bucket contents.
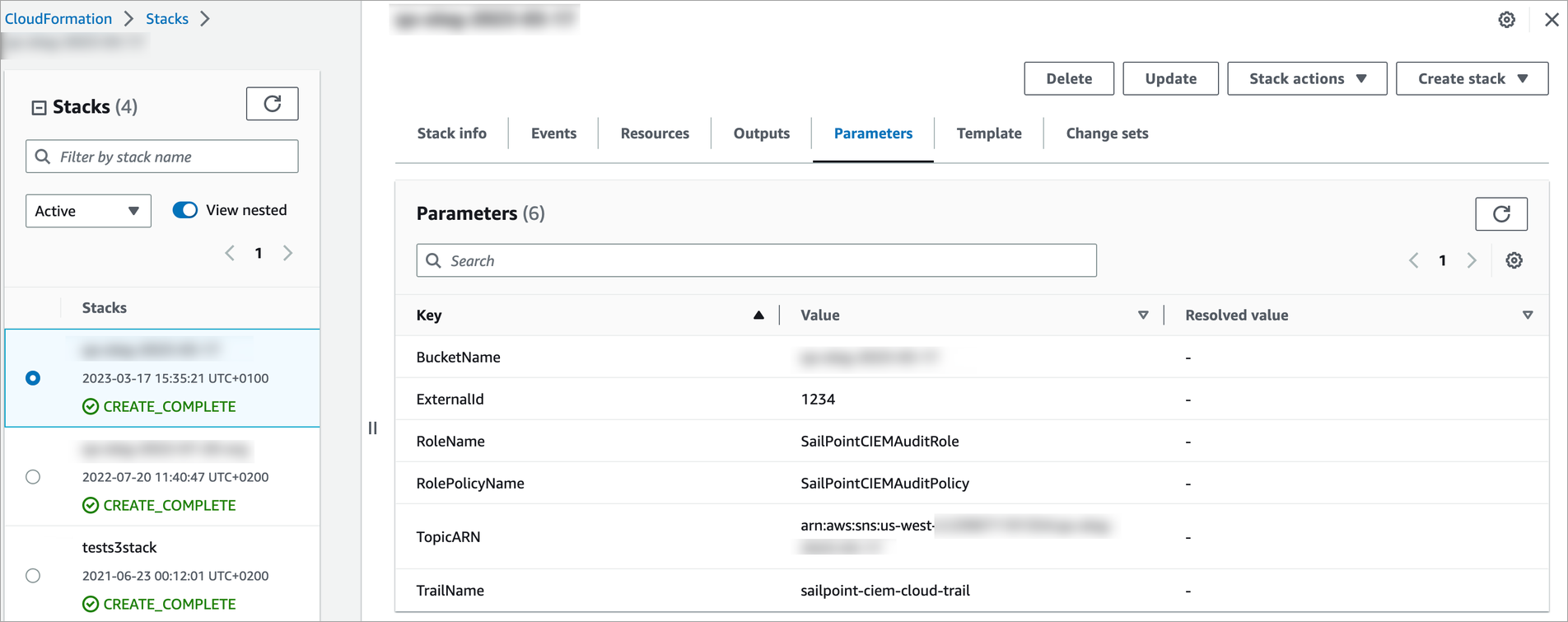
Viewing a Summary of the Details
-
Go to CloudFormation > Stacks, and select the stack.
-
Select the Parameters tab to view the key values for your configuration.