Configuring Authentication Settings
To configure a direct connection between the Microsoft SharePoint Online source and SailPoint Identity Security Cloud, specify the authentication type and grant type.
Note
Microsoft recommends using JWT Certificate Credentials for authentication, as other grant types (Client Credentials, SAML Bearer Assertion, Refresh Token/Auth Code) are deprecated and will stop working after April 2, 2026. Use JWT Certificate Credentials for all new and existing source configurations.
The JWT Certificate Credentials method supports authentication based on a JWT assertion prepared from a certificate and private key.
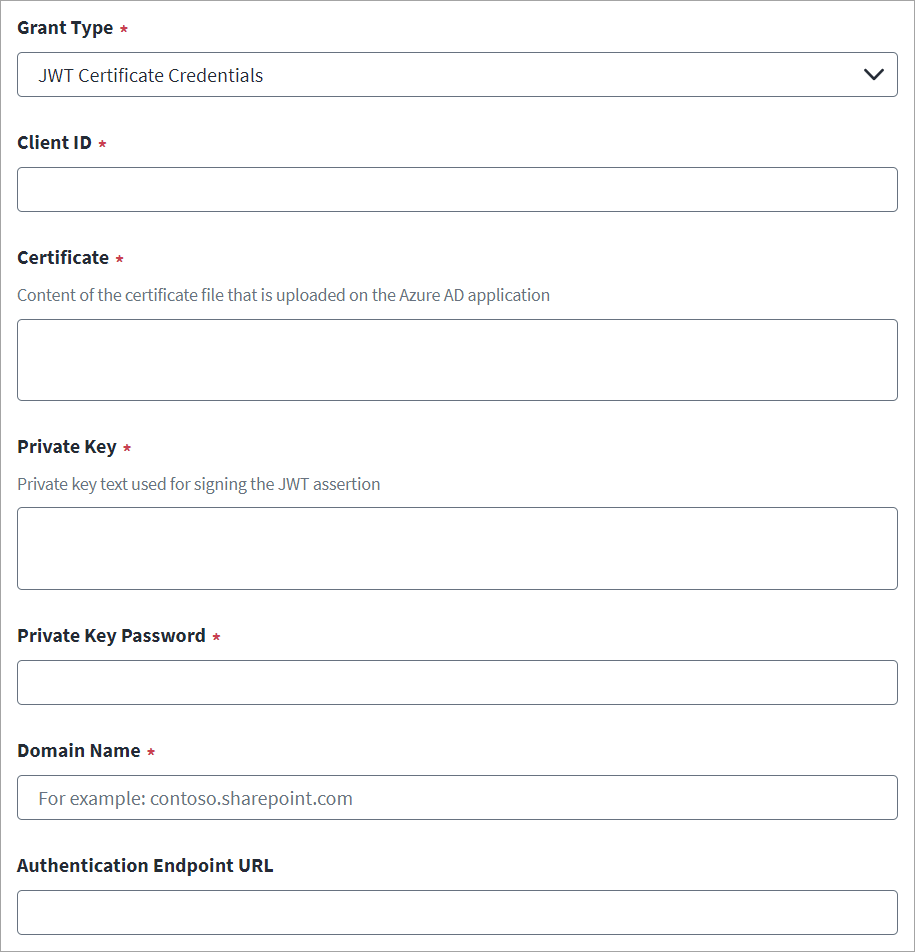
-
Select JWT Certificate Credentials from the Grant Type drop-down list.
-
Enter the Client ID of the source created on the SharePoint Online managed system. For more information, refer to Registering an Application Using the SharePoint Online Portal (Deprecated).
-
Enter the valid Certificate details of the source created on the SharePoint Online managed system.
-
Enter the valid Private Key text that is used to sign the JWT assertion and the corresponding Private Key Password. For more information, refer to Creating OAuth2.0 JWT Certificate Credentials (Recommended).
-
Enter the SharePoint Online Domain Name. For example,
contoso.sharepoint.com. -
In Authentication Endpoint URL, enter the URL that corresponds to the Microsoft Azure Active Directory authentication endpoint deployed on a national cloud.
For example, for the US government, enter
https://login.microsoftonline.us, or for China enterhttps://login.partner.microsoftonline.cn. -
Select Save.
Use the Client Credentials with the ID and Secret parameters.
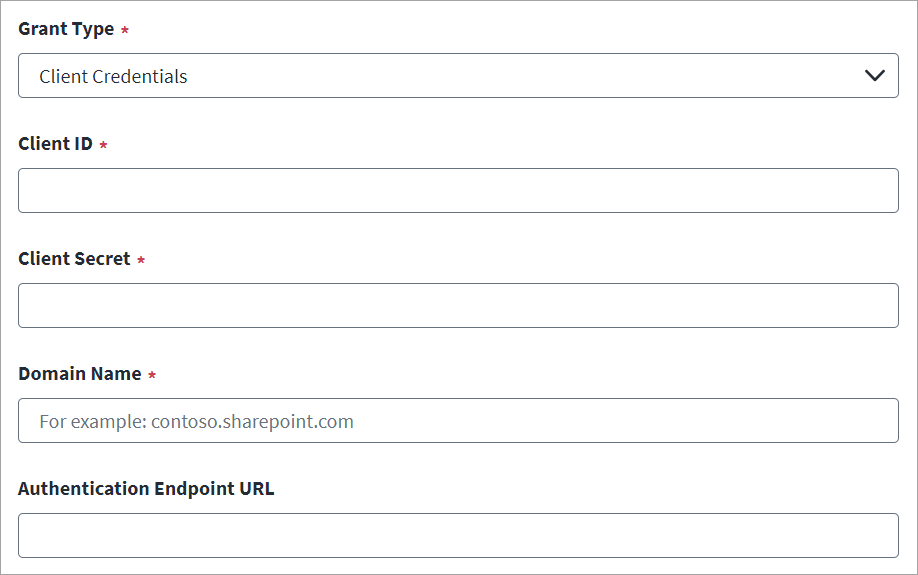
-
Select Client Credentials from the Grant Type drop-down list.
-
Enter the Client ID and Client Secret of the source created on the SharePoint Online managed system. For more information, refer to Registering an Application Using the SharePoint Online Portal (Deprecated).
-
Enter the SharePoint Online Domain Name. For example,
contoso.sharepoint.com. -
(Optional) In Authentication Endpoint URL, enter the URL that corresponds to the Microsoft Azure Active Directory authentication endpoint deployed on a national cloud.
For example, for the US government, enter
https://login.microsoftonline.us, or for China enterhttps://login.accesscontrol.chinacloudapi.cn. -
Select Save.
The Auth Code / Refresh Token grant type is a client credentials-based authentication protocol. In addition to client credentials, it uses a Refresh Token to authenticate.
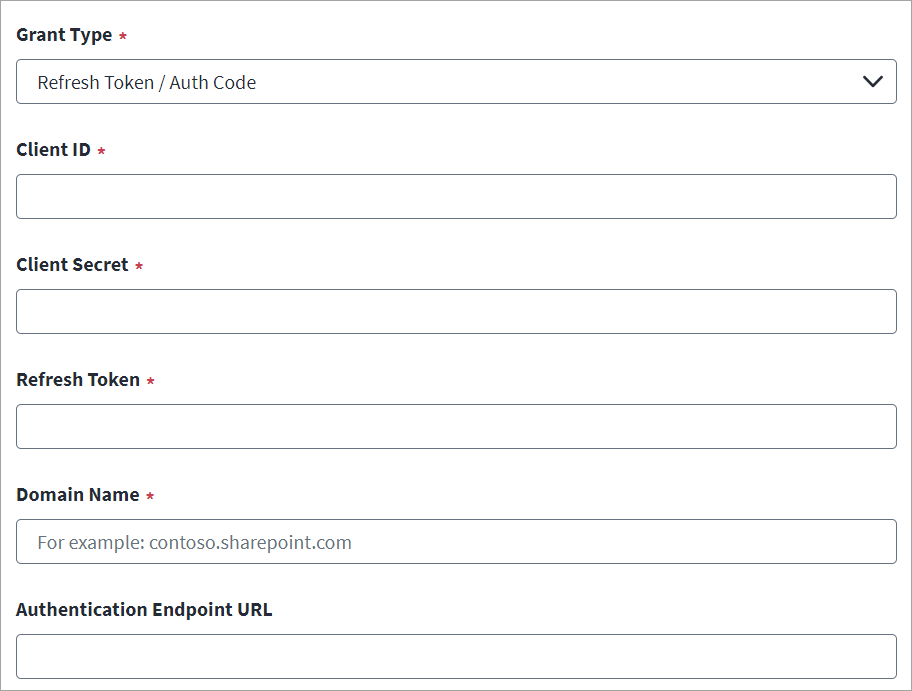
-
Select Refresh Token / Auth Code from the Grant Type drop-down list.
-
Enter the Client ID and Client Secret of the source created on the SharePoint Online managed system. For more information, refer to Registering an Application Using the SharePoint Online Portal (Deprecated).
-
Enter the valid Refresh Token obtained after registering the app with the Azure Active Directory Portal. For more information, refer to Generating a Refresh Token (Deprecated).
-
Enter the SharePoint Online Domain Name. For example,
contoso.sharepoint.com. -
In Authentication Endpoint URL, enter the URL that corresponds to the Microsoft Azure Active Directory authentication endpoint deployed on a national cloud.
For example, for the US government, enter
https://login.microsoftonline.us, or for China enterhttps://login.partner.microsoftonline.cn. -
Select Save.
The SAML Bearer Assertion method is password-based user authentication with ADFS environment. SAML assertion issued by ADFS after authentication is used to get the access token from the Azure Active Directory.
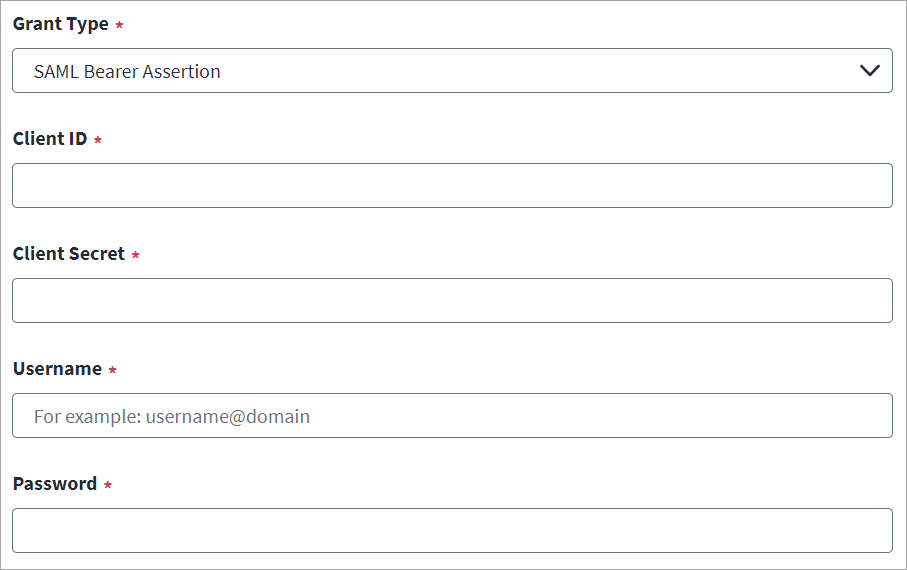
-
Select SAML Bearer Assertion from the Grant Type drop-down list.
-
Enter the Client ID and Client Secret of the source created on the SharePoint Online managed system. For more information, refer to Registering an Application Using the SharePoint Online Portal (Deprecated).
-
Enter the SAML Username and corresponding Password for SAML authorization.
-
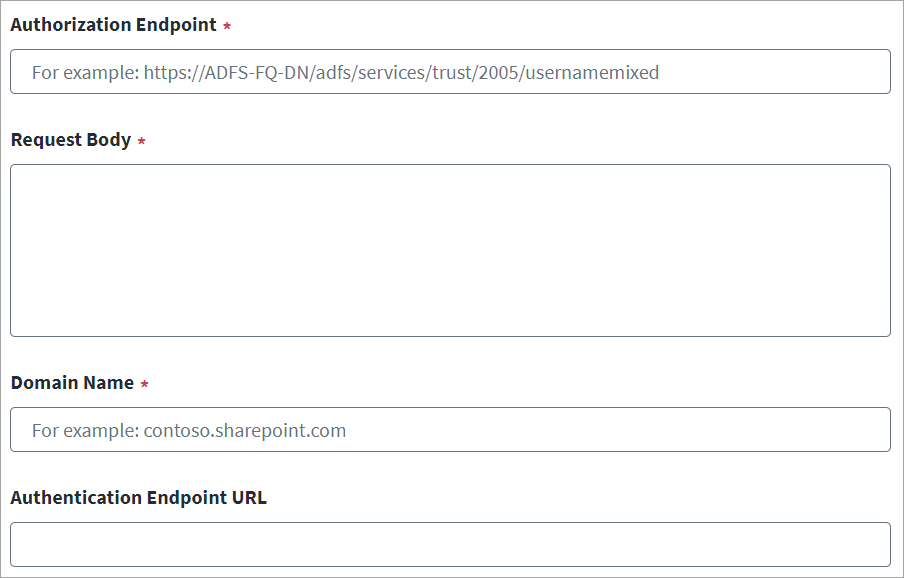
Enter the server URL for the Authorization Endpoint.
-
Enter the Request Body details for the SAML Bearer assertion.
-
Enter the SharePoint Online Domain Name. For example,
contoso.sharepoint.com. -
In Authentication Endpoint URL, enter the URL that corresponds to the Microsoft Azure Active Directory authentication endpoint deployed on a national cloud.
For example, for the US government, enter
https://login.microsoftonline.us, or for China enterhttps://login.partner.microsoftonline.cn. -
Select Save.