Service Principal Accounts Management
Important
If you want to enable additional cloud governance features for your Entra Cloud Objects (for example,
To access resources that are secured by an Microsoft Entra ID tenant, the entity that requires access must be represented by a security principal. This requirement is true for both users (user principal) and applications (service principal). The security principal defines the access policy and permissions for the user/application in the Microsoft Entra ID tenant.
With this feature, the connector supports managing such Service Principals for enterprise applications as Accounts.
Note
To gauge the probability of compromised service principals (workload identities) accounts in your environment, refer to Risky Service Principal Alert Feature for more information.
Caution
Switching from Service Principal Group Management to Service Principal Account Management may invalidate previously created Service Principal Managed Attribute objects. Ensure a thorough review of configurations before making this change to avoid potential data issues in your environment.
Supported Operations
The following operations are supported for the Azure Service Principal:
|
Operations |
Service Principal |
|---|---|
|
Aggregation |
Yes |
|
Get Account |
Yes |
|
Create |
Yes |
|
Update |
Yes |
|
Enable and Disable Users |
Yes |
|
Add and Remove Entitlements
|
Yes |
Administrator Permissions
|
Purpose |
Type |
Permissions |
|---|---|---|
|
Aggregation of Service Principals |
Application |
Application.Read.All |
|
Create and Update Service Principals |
Application |
Application.ReadWrite.All |
|
Add and Remove Owners |
Application |
Application.ReadWrite.OwnedBy |
|
Add and Remove Application Roles for Service Principals |
Application |
AppRoleAssignment.ReadWrite.All |
|
Aggregation of Application Roles |
Application |
Application.Read.All |
|
Aggregation and Add/Remove Microsoft Entra ID Group and Roles for Service Principals |
|
Refer to Required Permissions. |
|
Aggregation and Add/Remove RBAC Roles for Service Principals |
|
Refer to Group Attributes for Azure Cloud Objects. |
|
Aggregation and Add/Remove PIM Azure Active and Microsoft Entra ID Roles for Service Principals |
|
|
|
Aggregation of Admin/User Consented Permissions for Service Principals |
Application |
DelegatedPermissionGrant.Read.All |
|
Add/Remove Admin Consented Delegated Permissions for Service Principals |
Application |
DelegatedPermissionGrant.ReadWrite.All |
|
Remove User Consented Delegated Permissions for Service Principals |
Application |
DelegatedPermissionGrant.ReadWrite.All |
Supported Schema Attributes
To aggregate service principal related information for the user during account aggregation, ensure that the service principal attributes are present in the account schema. For more information, refer to Service Principal as Accounts Attributes.
Supported Provisioning Attributes
To provision service principal related information, ensure that the attributes in Account Profile for Service Principal are present in your provisioning policy.
Configuring Microsoft Entra Service Principals as Accounts
-
Go to Feature Management.
-
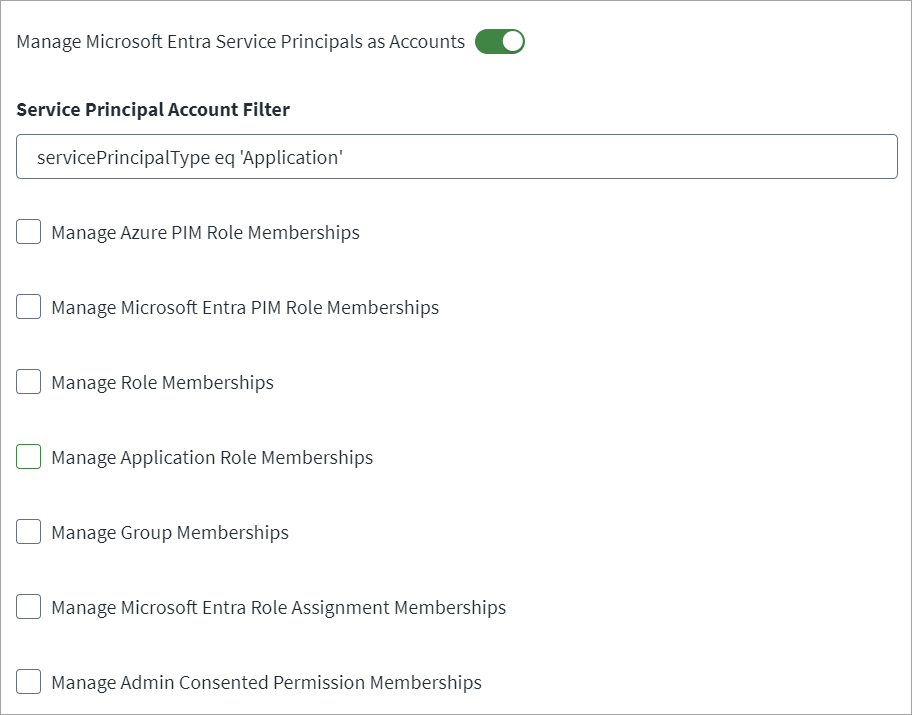
Select Manage Microsoft Entra Service Principals as Accounts to aggregate Azure Service Principals along with Users during the account aggregation process. By default, when this is enabled, entitlements are not fetched. You must select the entitlements you want to fetch from the available list. When this is turned off, you see a black X. If it is turned on, you see a blue ✔.
Note
To automate the process of adding Service Principal account attributes to the account schema during Account Schema configuration, select Include Attributes in Schema for managing azure Service Principal as account . For more information, refer to Service Principal as Accounts Attributes. -
In the Service Principal Account Filter field, enter filter statements to ensure only the correct Azure Service Principals are included in the aggregation process. The default filter is
servicePrincipalType eq 'Application'Note
Advanced queries are not supported.Example filters:
-
For a filter to match the Enterprise Application default view on the Azure portal use the following:
tags/Any(x: x eq 'WindowsAzureActiveDirectoryIntegratedApp')
-
-
Select the Manage Azure PIM Role Memberships checkbox to manage Azure PIM Active Role memberships for Service Principal.
-
Select the Manage Microsoft Entra PIM Role Memberships checkbox to manage Microsoft Entra ID PIM Active Role memberships for Service Principal.
-
Select the Manage Role Memberships checkbox to manage Directory Role memberships for Service Principal.
-
Select the Manage Application Role Memberships checkbox to manage Azure Application Role memberships for Service Principal.
-
Select the Manage Group Memberships checkbox to manage Microsoft Entra ID Group memberships for Service Principal.
-
Select the Manage Microsoft Entra Role Assignment Memberships checkbox to manage Azure Cloud Group memberships for Service Principals.
-
Select the Manage Admin Consented Permission Memberships checkbox to manage Azure admin consented permissions for Service Principals.
Note
This is for delegated permissions. -
Select Save.