Connection Settings
Provide the information required to connect to the Microsoft Entra ID instance based on the selected Grant Type for OAuth 2.0 authentication:
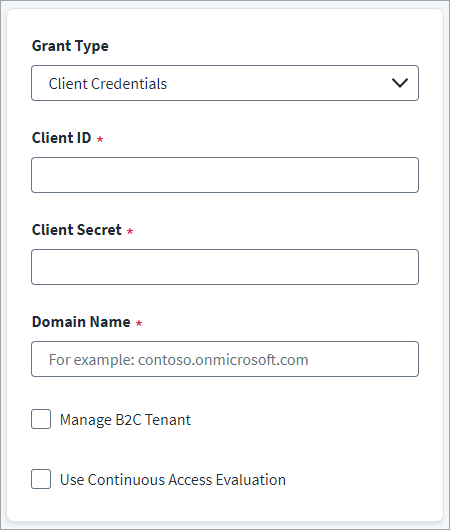
-
In the Client ID field, enter the Microsoft Entra ID API Client ID for OAuth2 authentication.
-
In the Client Secret field, enter the Microsoft Entra ID API Client Secret.
-
In the Domain Name field, enter the name of the Microsoft Entra ID domain to be managed. For example, contoso.onmicrosoft.com.
-
(Optional) Select the Manage B2C Tenant checkbox to manage identities in the Azure Active Directory B2C Tenant.
Note
Delta Aggregation is not applicable if the Manage B2C Tenant checkbox is selected. -
(Optional) Select the Use Continuous Access Evaluation checkbox to enable the connector to leverage the Microsoft Entra ID real-time enforcement of Conditional Access location and risk policies along with instant enforcement of token revocation events for an enterprise application (service principal).
-
Select Save.
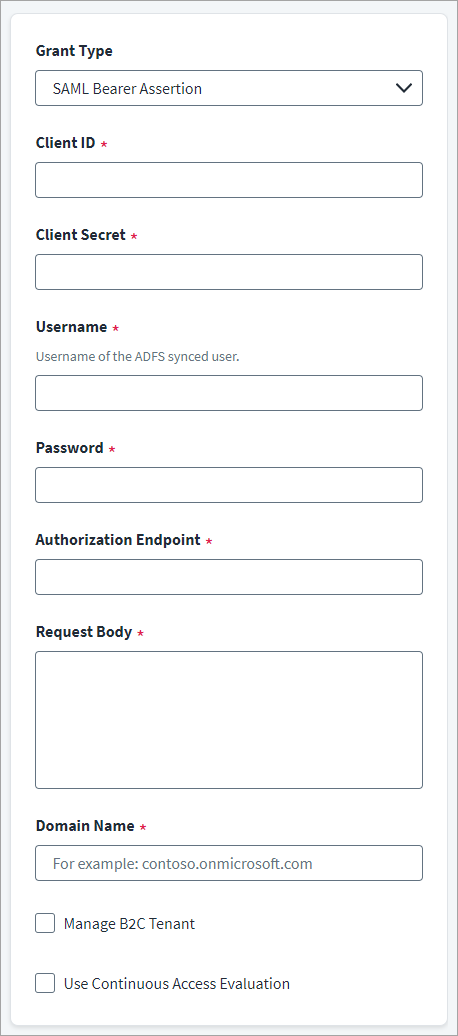
-
In the Client ID field, enter the Microsoft Entra ID API Client ID for OAuth2 authentication.
-
In the Client Secret field, enter the Microsoft Entra ID API Client Secret.
-
Enter the Username for authorization.
-
Enter the Password of the user for authorization.
-
In the Authorization Endpoint field, enter the endpoint URL of authorization server.
-
In the Request Body field, enter the request body for SAML assertion.
For more information on SAML Request Body, refer to SAML Request Body.
-
In the Domain Name field, enter the name of the Microsoft Entra ID domain to be managed. For example, contoso.onmicrosoft.com.
-
(Optional) Select Manage B2C Tenant checkbox to manage identities in the Azure Active Directory B2C Tenant.
Note
Delta Aggregation is not applicable if the Manage B2C Tenant checkbox is selected. -
(Optional) Select the Use Continuous Access Evaluation checkbox to enable the connector to leverage the Microsoft Entra ID real-time enforcement of Conditional Access location and risk policies along with instant enforcement of token revocation events for an enterprise application (service principal).
-
Select Save.
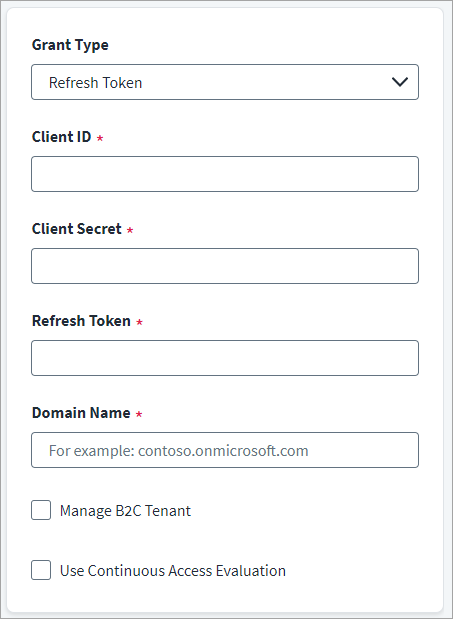
-
In the Client ID field, enter the Microsoft Entra ID API Client ID for OAuth2 authentication.
-
In the Client Secret field, enter the Microsoft Entra ID API Client Secret.
-
Enter the valid Refresh Token.
-
In the Domain Name field, enter the name of the Microsoft Entra ID domain to be managed. For example, contoso.onmicrosoft.com.
-
(Optional) Select Manage B2C Tenant checkbox to manage identities in the Azure Active Directory B2C Tenant.
Note
Delta Aggregation is not applicable if the Manage B2C Tenant checkbox is selected. -
(Optional) Select the Use Continuous Access Evaluation checkbox to enable the connector to leverage the Microsoft Entra ID real-time enforcement of Conditional Access location and risk policies along with instant enforcement of token revocation events for an enterprise application (service principal).
-
Select Save.
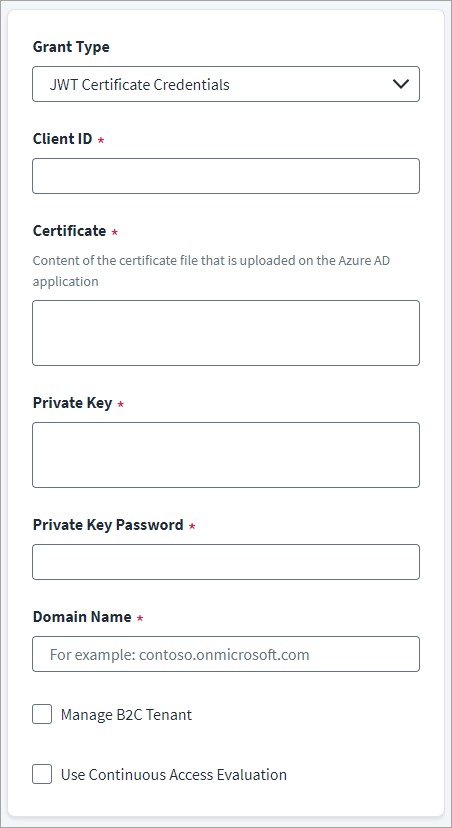
-
In the Client ID field, enter the Microsoft Entra ID API Client ID for OAuth2 authentication.
-
In the Certificate field, provide the unique alpha-numeric value of certificate used to sign the JWT assertion.
-
Enter the Private Key text used for encrypting the JWT assertion.
-
Enter the Private Key Password that is used for decrypting the private key.
-
In the Domain Name field, enter the name of the Microsoft Entra ID domain to be managed. For example, contoso.onmicrosoft.com.
-
(Optional) Select Manage B2C Tenant checkbox to manage identities in the Azure Active Directory B2C Tenant.
Note
Delta Aggregation is not applicable if the Manage B2C Tenant checkbox is selected. -
(Optional) Select the Use Continuous Access Evaluation checkbox to enable the connector to leverage the Microsoft Entra ID real-time enforcement of Conditional Access location and risk policies along with instant enforcement of token revocation events for an enterprise application (service principal).
-
Select Save.