Additional Settings
This section contains the information that the source requires to configure the other required parameters. After you select Additional Settings the following page displays.
-
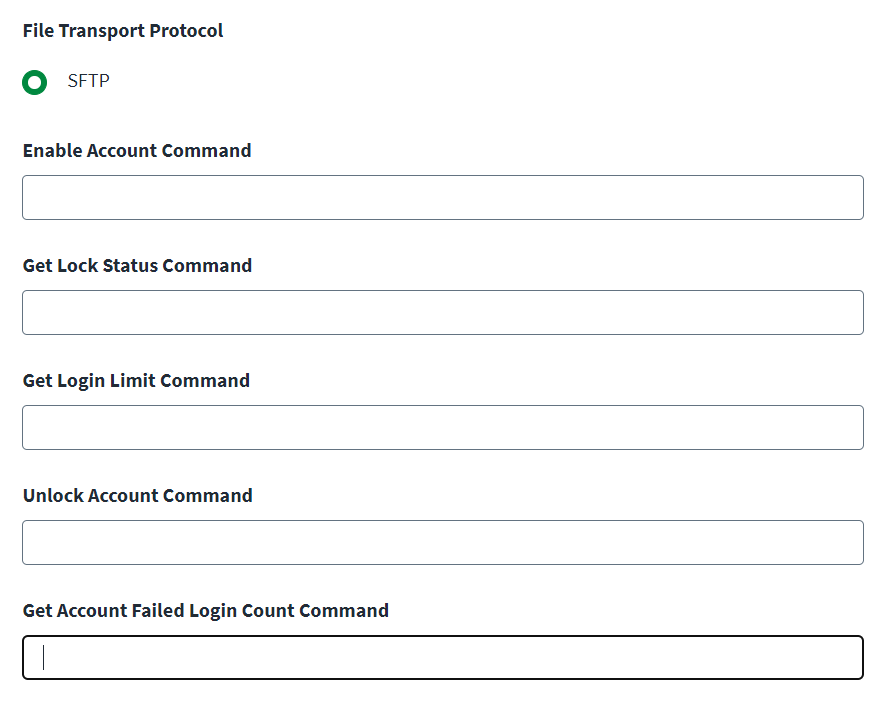
The Linux only supports the SFTP file transfer protocol used during aggregation.
-
Enter the command as follows to enable the account:
passwd -u
-
In the Get Lock Status Command field, set the command used to get the status of all locked user accounts.
Default:
pam_tally2 | awk '{print $1} {print $2}'
-
In the Get Login Limit Command field, set the command used to get the count limit of user logins.
Default:
cat /etc/pam.d/system-auth
-
In the Unlock Account Command, set the command used to unlock a user account.
Default:
pam_tally2 -u
-
In the Get Account Failed Login Count Command field, set the command used to obtain the count for failed login accounts.
Default:
pam_tally2
Note
The Linux source allows you to change the disable account attribute value to the usermod -s /bin/false command.
Disable Accounts Password Change
In the Linux source, you can deny change password operations for disabled accounts. You can reject the password change if the account is locked.
You can use the REST API to enable the denychangepassword attribute for a disabled account as follows:
POST <url>/api/source/update/<sourceID>
where:
-
<url>is the URL for the customer's Identity Security Cloud instance -
<sourceID>is the Source ID (number) obtained through the UI
In the body of the POST, use the form-data as follows:
-
Key –
connector_denyChangePasswordForDisabledAccount -
Value –
true