Cross Account by Assume Roles
This scenario requires 4 conditions for user USER_A from account A to have permission X on resource RESOURCE_B from account B through role ASSUME_ROLE_B:
-
ASSUME_ROLE_B is defined in account B.
-
ASSUME_ROLE_B is attached to policy that gives permission X on RESOURCE_B.
-
USER_A should be a member of ASSUME_ROLE - a trusted entity of the role.
-
USER_A should have in account A, permission to assume ASSUME_ROLE_B in account B.
File Access Manager does not display this information in v8.2.
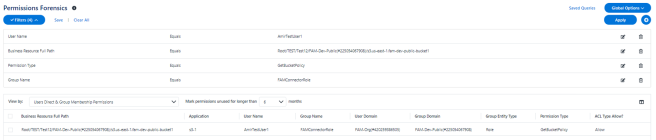
In the example above, the role “FAMConnectorRole” allows “GetBucketPolicy” on bucket “fam-dev-public-bucket1”. The role and the bucket, both belong to account “FAM-Dev-Public”. The role has a member user (trusted entity) “AmirTestUser1” from account “Fam-Org”.
If in account FAM-Org, “AmirTestUser1” has a policy which allows it to assume the role “FAMConnectorRole” in account “FAM-Dev-Public” (Not supported in File Access Manager view in v8.2) – The permission will be active.